A Progress Report on the CVE Initiative Robert Martin Steven Christey
52 Slides5.31 MB

A Progress Report on the CVE Initiative Robert Martin Steven Christey David Baker The MITRE Corporation June 27, 2002

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

Many Motivations for Getting on top of Vulnerabilities CERT/CC Incidents Reported http://www.theregister.co.uk/content/53/24244.html http://www.cert.org/advisories/CA-2002-06.html 120000 Projected based on Q1 2002 actual reported incidents 100000 80000 60000 40000 20000 http://www.baselinemag.com/article/0,3658,s 1867&a 23195,00.asp 2002 2001 2000 1999 1998 1997 http://www.eweek.com/article/0,3658,s 701&a 23193,00.asp 1996 1995 1994 1993 1992 1991 1990 1989 1988 0 MITRE

Vulnerabilities Have Been Found in Almost Every Type of Commercial Software There Is Mail Servers 1st Up Mail Server All-Mail ALMail32 Avirt Mail Server Becky! Internet Mail CWMail Domino Mail Server Exchange Server Hotmail Internet Anywhere Mail Server ITHouse Mail Server Microsoft Exchange Pegasus Mail Sendmail Security Software ACE/Server BlackICE Agent BlackICE Defender Certificate Server CProxy Server ETrust Intrusion Detection GateKeeper InterScan VirusWall Kerberos 5 Norton AntiVirus PGP SiteMinder Tripwire Sample of Vulnerabilities Announced in 1999 & 2000 Web servers & tools Domino HTTP Server IIS NCSA Web Server Sawmill WebTrends Log Analyzer Internet AFS Apache BIND CGI Cron IMAP Routers 3220-H DSL Router 650-ST ISDN Router Ascend Routers Cisco Routers R-series routers Network Applications BackOffice Meeting Maker NetMeeting DBMSs Access DB2 Universal Database FileMaker Pro MSQL Oracle Desktop Applications Acrobat Clip Art Excel FrameMaker Internet Explorer Napster client Notes Client Novell client Office Outlook PowerPoint Project Quake R5 Client StarOffice Timbuktu Pro Word Works Workshop Development Tools ClearCase ColdFusion Flash Frontpage GNU Emacs JRun WebLogic Server Visual Basic Visual Studio Operating Systems AIX BeOS BSD/OS DG/UX FreeBSD HP-UX IRIX Linux MacOS Runtime for Java MPE/iX NetWare OpenBSD Palm OS Red Hat Security-Enhanced Linux Solaris SunOS Ultrix Windows 2000 Windows 95 Windows 98 Windows ME Windows NT Firewalls Firewall-1 Gauntlet Firewall PIX Firewall Raptor Firewall SOHO Firewall MITRE

Difficult to Integrate Information on Vulnerabilities and Exposures Security Advisories Priority Lists ? Vulnerability Scanners ? Research ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? Software Vendor Patches Intrusion Detection Systems ? Incident Response & Reporting Vulnerability Web Sites & Databases MITRE

The adoption of CVE Names by the Security Finding and sharing vulnerability information has Community is starting to Problem, address this problem been difficult: The Same Different Names Organization Name CERT CyberSafe ISS AXENT Bugtraq BindView Cisco IBM ERS CERIAS NAI CA-96.06.cgi example code Network: HTTP ‘phf’ Attack http-cgi-phf phf CGI allows remote command execution PHF Attacks – Fun and games for the whole family #107 – cgi-phf #3200 – WWW phf attack Vulnerability in NCSA/Apache Example Code http escshellcmd #10004 - WWW phf check Along with the new rule, “Whoever finds it, gets a CVE name for it” Which has been caused by the rule, “Whoever finds it, names it” MITRE

The CVE List provides a path for integrating information on Vulnerabilities and Exposures Security Advisories Priority Lists Vulnerability Scanners Software Vendor Patches CVE-1999-0067 Intrusion Detection Systems Incident Response & Reporting Research Vulnerability Web Sites & Databases MITRE

FBI/SANS Institute 2001 Top Twenty uses CVE names yet another step down the policy road All CVE-names Unix Windows Note 2. CVE Numbers You’ll find references to CVE (Common Vulnerabilities and Exposures) numbers accompanying each vulnerability. You may also see CAN numbers. CAN numbers are candidates for CVE entries that are not yet fully verified. For more data on the Award-winning CVE project, see http://cve.mitre.org. In the General Vulnerabilities section, the CVE numbers listed are examples of Some of the vulnerabilities that are covered by each listed item. Those CVE lists are not meant to be all-inclusive. However, for the Windows and Unix Vulnerabilities, the CVE numbers reflect the top Priority vulnerabilities that should be checked for each item. http://www.sans.org/top20.htm MITRE

CVE is Even Being Used to to Compare and Contrast products or the vulnerabilities they do or don’t find. Tables from Network Computing Article “To Catch a THIEF” (8/20/2001) by talking about the vulnerabilities they do or do not have. Ad from SC Magazine (April 2002) MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

0 An international security community activity led by MITRE focused on developing a list that provides common names for publicly known information security vulnerabilities and exposures. 0 Key tenets – One name for one vulnerability or exposure – One standardized description for each vulnerability or exposure – Existence as a dictionary rather than a database – Publicly accessible for review or download from the Internet – Industry participation in open forum (editorial board) 0 The CVE list and information about the CVE effort are available on the CVE web site at [cve.mitre.org] 22 vo 23 te ap d pr o o 1 n, ve 00 4 d e -1 50 nt 5 0 0 ri ne und es, w er 24 /m a 1 on na 9 b th ly ein si g s, The Common Vulnerabilities and Exposures (CVE) Initiative MITRE

The CVE Strategy 4. Establish CVE in vendor fix-it sites and update mechanisms Commercial S/W Products Unreviewed Update and Fix Sites & Update Mechanisms Bugtraqs, Mailing lists, Hacker sites Discovery Policy Reviewed Advisories CERT, CIAC, Vendor advisories 1. Inject Candidate numbers into advisories Security Products Scanners, Intrusion Detection, Vulnerability Databases 2. Establish CVE at security product level in order to . time Methodologies Purchasing Requirements Education 3. enable CVE to permeate the policy level. MITRE

Example: CVE helping to make Detailed Product Comparisons Tables from Network Computing Article “To Catch a THIEF” (8/20/2001) Network Computing Article “Vulnerability Assessment Scanners” (1/8/2001) MITRE

CVE email Lists have an International readership Representing 2200 registered email subscribers - 51 plus (11 countries) - 11 to 50 registered (39 countries) - 1 to 10 registered (71 countries) MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

Where the CVE List comes from ISS, SecurityFocus, New Submissions Neohapsis, NIPC 150–500 per/month CyberNotes AXENT, BindView, Harris, Cisco, CERIAS, Hiverworld, SecurityFocus, ISS, NAI, Symantec, Nessus New Vulnerabilities Vulnerability Databases CVE Content Team Vulnerability Databases Candidates in New Alerts & Advisories 5–15 per/month Legacy Submissions 8400 ——— —— 563 1,100 2,500 dups 3,900 info study 900 CVE Candidates 2419 Yes Yes Yes 4 Editorial Board CVE List 2223 MITRE

4500 4000 Status (as of June 26, 2002) 2223 entries 2419 candidates Sep-99 Oct-99 Nov-99 Dec-99 Jan-00 Feb-00 Mar-00 Apr-00 May-00 Jun-00 Jul-00 Aug-00 Sep-00 Oct-00 Nov-00 Dec-00 Jan-01 Feb-01 Mar-01 Apr-01 May-01 Jun-01 Jul-01 Aug-01 Sep-01 Oct-01 Nov-01 Dec-01 Jan-02 Feb-02 Mar-02 Apr-02 May-02 Jun-02 CVE Growth 5000 Candidates CVE Entries 3500 3000 2500 2000 1500 1000 500 0 MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

Identifying Known Vulnerabilities: The CVE Submission Stage 0 Sources provide MITRE with their lists of all known vulnerabilities 0 MITRE’s CVE Content Team processes submissions Conversion Convert items in database/tool to submission format Assign temporary ID’s to each submission Matching Find most similar submissions, candidates, and entries based on keywords Refinement Combine all matched submissions into groups Use each group to create candidates MITRE

Candidate Stage: Assignment CAN-YYYY-NNNN B:1 C:1 17 19 Assign new number (CAN-YYYY-NNNN) YYYY is the year in which the number was assigned; NNNN is a counter for that year To Source A ftp-pasv CAN-YYYY-NNNN iis-dos CAN-1999-1234 A:2 ftp-pasv CAN-1999-1234 B:3 524 Backmap To Source B 17 CAN-YYYY-NNNN 524 CAN-1999-1234 To Source C 19 CAN-YYYY-NNNN A:1 iis-dos Backmap: internal ID’s mapped to candidate names, sent back to provider Submissions removed MITRE

Candidate Reservation Process Researcher / Vendor Request Candidate CAN-YYYY-NNNN Request candidate from CNA Provide candidate number to vendor and other parties Include candidate number in initial public announcement Notify MITRE of announcement Perform due diligence to avoid duplicate or incorrect candidates Follow responsible disclosure practices to increase confidence in correctness of the candidate Candidate Numbering Authority CAN POOL Obtain pool of candidate numbers from MITRE Define requirements for researchers to obtain a candidate Assign correct number of candidate numbers (follow content decisions) Ensure candidate is shared across all parties Do not use candidates in “competitive” fashion MITRE 400 CANs reserved Primary CNA Accessible to researchers and vendors Educate CNA about content decisions Update CVE web site when candidate is publicly announced Track potential abuses Reserving and coordinating CANs requires a process change for all parties. MITRE

Many organizations are reserving CVE names and using them in their alerts and advisories To-date, CVE names have been included in initial advisories from: ISS X-Force IBM Rain Forest Puppy @stake BindView HP CERT/CC SGI COMPAQ Microsoft Ernst & Young eEye CISCO Rapid 7 NSFOCUS Sanctum SecurityFocus Red Hat VIGILANTe Apache Apple http://www.redhat.com/support/errata/RHSA-2001-150.html assigned CAN-2001-0869 to this issue. MITRE

Candidate Stage: Proposal Through Final Decision CAN-YYYY-NNNN Proposal Modification Clustering (date of discovery, OS, service type, etc.) Published on CVE web site Editorial Board members vote on candidate ACCEPT, MODIFY, REVIEWING, NOOP (No Opinion), RECAST (change level of abstraction), REJECT Add references, change description Change level of abstraction Significant changes may require another round of voting Interim Decision ACCEPT or REJECT (Requires sufficient votes) At least 2 weeks after initial proposal 4 days for last-minute feedback Final Decision ACCEPT or REJECT Convert CAN-YYYY-NNNN to CVE-YYYY-NNNN Report final voting record Create new CVE version MITRE

Entry Stage CVE-YYYY-NNNN Publication Publish new CVE version and difference report Modification Minor modifications Add references Change description Reassessment New information may force a re-examination of the entry Level of abstraction may need to be changed May be a duplicate May not be a problem after all Deprecation May need to “delete” an existing entry (e.g. duplicate entries) But, some products may still use this number Register the “deletion” but keep entry available for review MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

Content Decisions 0 Explicit guidelines for content of CVE entries – Ensure and publicize consistency within CVE – Provide “lessons learned” for researchers – Document differences between vulnerability “views” 0 Three basic types – Inclusion: What goes into CVE? What doesn’t, and why? – Level of Abstraction: One or many entries for similar issues? – Format: How are CVE entries formatted? 0 Difficult to document – “[It’s] like trying to grasp wet corn starch” (Board member) Incomplete information is the bane of consistency - and content decisions! MITRE

Example Content Decision: SF-LOC (Software Flaws/Lines of Code) Create separate entries for problems in the same program that are of different types, or that appear in different software versions. 0 Older versions of this CD distinguished between problems of the same type – “Split-by-default” approach generated “too many” candidates – Also “unfair” to vendors with source code or detailed reports – Once produced 8 candidates where other tools and databases would have created only 1 vulnerability record 0 Affected by amount of available information – Especially source code and exploit details 0 For all candidates affected by SF-LOC, see: – http://cve.mitre.org/cgi-bin/cvekey.cgi?keyword CD:SF-LOC MITRE

SF-LOC Examples CAN-2000-0686 Auction Weaver CGI script 1.03 and earlier allows remote attackers to read arbitrary files via a . (dot dot) attack in the fromfile parameter. 2 failure points CAN-2000-0687 Auction Weaver CGI script 1.03 and earlier allows remote attackers to read arbitrary files via a . (dot dot) attack in the catdir parameter. CAN-2000-0971 Avirt Mail 4.0 and 4.2 allows remote attackers to cause a denial of service and possibly execute arbitrary commands via a long "RCPT TO" or "MAIL FROM" command. 2 failure points CAN-2001-0019 Arrowpoint (aka Cisco Content Services, or CSS) allows local users to cause a denial of service via a long argument to the “show script,” “clear script,” “show archive,” “clear archive,” “show log,” or “clear log” commands. CAN-2001-0020 Directory traversal vulnerability in Arrowpoint (aka Cisco Content Services, or CSS) allows local unprivileged users to read arbitrary files via a . (dot dot) attack 6 failure points 0 CAN-2001-0019 is clearly different than CAN-2001-0020 – But a single patch fixes both problems 0 CAN-2001-0019 could be 1, 2, or 6 vulnerabilities MITRE

Why CAN-2001-0019 Could Identify 1, 2, or 6 Vulnerabilities 0 3 different source code scenarios 0 Without actual source, can’t be sure which scenario is true 0 Even with source, there are different ways of counting 0 Multiple format string problems are especially difficult to distinguish strcpy(arg, long input); if (strcmp(cmd, "show") 0) { process show command(arg); } elsif (strcmp(cmd, "clear") 0) { process show command(arg); } if (strcmp(cmd, "show") 0) { strcpy(str, long input); process show command(str); } elsif (strcmp(cmd, "clear") 0) { strcpy(str, long input); process clear command(str); } if (strcmp(cmd, "show") 0) { if (strcmp(arg1, "script") 0) { strcpy(str, long input); show script(str); } elsif (strcmp(arg1, "archive") 0) { strcpy(str, long input); show archive(str); } elsif (strcmp(arg1, "log") 0) { strcpy(str, long input); show log(str); } } elsif (strcmp(cmd, "clear") 0) { if (strcmp(arg1, "script") 0) { strcpy(str, long input); show script(str); } elsif (strcmp(arg1, "archive") 0) { strcpy(str, long input); show archive(str); } elsif (strcmp(arg1, "log") 0) { strcpy(str, long input); show log(str); } } MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

CVE Editorial Board 0 Includes mostly technical representatives from 35 different organizations including researchers, tool vendors, response teams, and end users 0 Reviews and approves CVE entries 0 Discusses issues related to CVE maintenance 0 Holds monthly meetings (face- to-face or phone) 0 Maintains publicly viewable mailing list archives [cve.mitre.org/board/archives] [cve.mitre.org/board/boardmembers.html] MITRE

Editorial Board Roles, Tasks, and Qualifications 0 0 0 0 0 0 0 0 Minimum Expectations Tasks for All Members Technical Member Tasks Liaison Tasks Advocate Tasks Emeritus Tasks Recognition of Former Members Roles for MITRE [cve.mitre.org/board/edroles.html] MITRE

CVE Senior Advisory Council Objectives and Roles .The CVE Council is established to ensure that the CVE program receives the sponsorship, including funding and guidance, required to maximize the effectiveness of this program . Council Roles 0 Act as a catalyst for CVE and related activities. 0 Assure funding for the core CVE activity over the 0 0 0 0 0 long term including outreach to Government organizations and agencies. Discuss community needs and possible new CVE services. Promote the adoption of CVE at the strategic level. Business planning & prioritization. Discuss CVE and related security policy implications for the Federal Government. Identify CVE related materials & resources for use by Government CIOs and senior managers. MITRE

CVE Senior Advisory Council Members Co-Chairs: 0 John Gilligan, CIO of the USAF, and Co-chair of the Architecture/Interoperability Committee of the CIO Council 0 Sallie McDonald, GSA Assistant Commissioner Office of Info Assurance and Critical Infrastructure Protection 0 0 0 0 0 0 0 0 0 Participating Organizations Department of the Treasury Department of Energy Department of Labor Department of Health and Human Services Internal Revenue Service National Institute of Standards and Technology Critical Infrastructure Assurance Office National Infrastructure Protection Center Office of Management and Budget GSA ASD/C3I DISA Air Force NSA Intelligence Community NASA MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

What does CVE-compatible mean? 0 CVE-compatible means that a tool, database, web site, or security service can “speak CVE” and correlate data with other CVE-compatible items 0 CVE-compatible means it meets the following requirements: – Can find items by CVE name (CVE searchable) – Includes CVE name in output for each item (CVE output) – Explain the CVE functionality in their item’s documentation (CVE documentation) – Provided MITRE with “vulnerability” item mappings to validate the accuracy of the product or services CVE entries – Makes a good faith effort to keep mappings accurate [cve.mitre.org/compatible/requirements.html] MITRE

New CVE Compatibility Procedure (as of 18 June 2002) 0 Consists of two parts (phase 1 and phase 2): – Phase 1 - Compliance Declaration Item listed on Compatibility page and quote posted if given – Phase 2 - Compliance Questionnaire Submitted response is evaluated by MITRE Upon concurrence with Questionnaire: – Questionnaire response put on CVE site & mapping accuracy evaluated Upon completion of mapping accuracy evaluation – Use of the CVE-Compatible logo granted – Vendor free to refer to product or service as CVE-Compatible 0 Status: – Draft questionnaire developed/tested (takes 3 days to do) – “sample” questionnaire using CVE Web site created as example – alpha- & beta-tests conducted with MITRE/Editorial Board Also discussed at length with 30 organizations w/positive responses – Revised Compatibility pages to support new processes MITRE

Examples of CVE-compatible items: The ICAT Metabase 08.13.01 Government Computer News CVE-names http://icat.nist.gov MITRE

Where CVE-compatible Items Have Come From and Where the New Ones Are Coming From 2, 2 3, 3 E-Soft Inc. 1 Item 1, 5 SecurityWatch.Com 1 Item 2, 2 China National Computer Software & Technology Service Corporation FuJian RongJi Software Development Company,Ltd NSFOCUS Information Technology Co., Ltd Tsinghua UnisNet Ltd. Venus Information Technology Inc. 9 Items 1, 1 13, 30 2, 2 Red Hat Inc. 2 Items 37 Organizations, 59 Items Advanced Research Corporation ArcSight, Inc. Application Security, Inc. BindView Corporation CERIAS, Purdue University CERT/CC Cisco Systems, Inc. Citadel Security Software, Inc. eEye Digital Security Enterasys Networks, Inc. Entercept SECURITY TECHNOLOGIES ESecurityOnline Foundstone, Inc. Harris Corporation ISS - Internet Security Systems, Inc. KaVaDo Inc. LURHQ Company NCircle Network Security NetiQ Corporation Network Associates Inc. Network Security Systems, Inc. NFR Security, Inc. NIST Qualys, Inc. Recourse Technologies, Inc. SAINT Corporation Sanctum Inc. The SANS Institute SecureInfo Corporation SecurityFocus Snort.Org SpiDYNAMICS Strongbox Security Inc. Symantec Corporation Tiger Testing Inc. Tivoli Systems, Inc. UCDavis Computer Security Laboratory VIGILANTe.Com, Inc. 1, 7 EsCERT-UPC 1 Item 1 N-Stalker, Inc. 1 Item 2, 2 1, 1 E*MAZE Networks S.P.A. 1 Item Alliance Qualité Logiciel Cert-IST INTRANODE Software Technologies INTRINsec The Nessus Project 5 Items INZEN CO., Ltd. NetSecure Technology, Inc. Penta Security Systems, Inc. SecureSoft, Inc. Wins Technet Co., Ltd. 1, 1 nSecure Software (P) Ltd. 9 Items 1 Item Shake Communications Pty Ltd 1 Item (as of 25 June 2002) MITRE
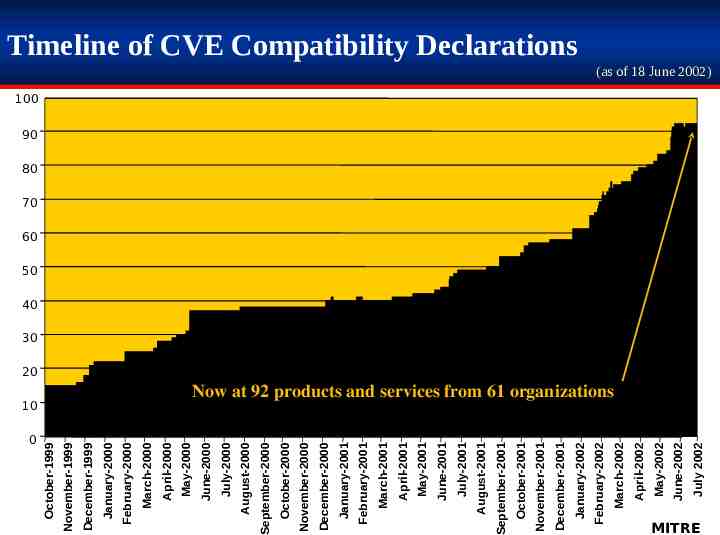
0 July 2002 June-2002 May-2002 April-2002 March-2002 February-2002 January-2002 December-2001 November-2001 October-2001 September-2001 August-2001 July-2001 June-2001 May-2001 April-2001 March-2001 February-2001 January-2001 December-2000 November-2000 October-2000 September-2000 August-2000 July-2000 June-2000 10 May-2000 April-2000 March-2000 February-2000 January-2000 December-1999 November-1999 October-1999 Timeline of CVE Compatibility Declarations (as of 18 June 2002) 100 90 80 70 60 50 40 30 20 Now at 92 products and services from 61 organizations MITRE

Several Parts of the Federal Government Have Called for the Use of CVE and CVE-Compatible products Furthermore, preference should be given to products that are Compatible with the Common Vulnerabilities and Exposures (CVE) list. . Federal departments and agencies should 1. give substantial consideration to . [CVE-compatible] products and services. 2. periodically monitor their systems for applicable vulnerabilities listed in . CVE 3. use [CVE] in their descriptions and communications of vulnerabilities http://www.acq.osd.mil/dsb/tfreports.htm http://csrc.nist.gov/publications/drafts/Use of the CVE.PDF MITRE

Outline for: A Progress Report on the CVE Initiative 0 0 0 0 0 0 0 0 Motivation Implementing CVE The CVE List Candidates Content Decisions The Editorial Board and Advisory Council CVE Compatibility Challenges and Opportunities MITRE

Challenge: Improving the Naming Scheme 0 Some benefits with the current naming scheme – Compact – Candidate/entry status encoded within the name – Most CAN-YYYY-NNNN will become CVE-YYYY-NNNN – Removes debate about what a “good” name is 0 Some issues – Changing a CAN to a CVE incurs maintenance costs – Differences not obvious to casual users – Year segment can be misunderstood as year of discovery – Name is not atomic in most search engines, thus difficult to find – Maximum 10,000 candidates per year (CAN-10K problem) 0 Once public, names must not disappear without explanation – Deprecated entries, rejected candidates. even typos – Mappings from old to new names Any change to the CVE naming scheme will impact many users. MITRE

Managing the Scope of the CVE List 0 What issues should be included? – Exposures (CD:DEFINITION) e.g., running finger Highly controversial topic before CVE was even public – Beta software (CD:EX-BETA) – Online services / ASPs (CD:EX-ONLINE-SVC) – Client-side DoS (CD:EX-CLIENT-DOS) – Vague vendor advisories (CD:VAGUE) 0 Malicious code (viruses, Trojans) 0 Configuration problems – Challenges in abstraction 0 0 0 0 Default passwords: 1 CVE, or hundreds? – Blurry lines between policy, security, and environment Large-scale analyses, e.g. PROTOS Voting: how much confidence is needed for official CVE entries? Timeliness: Fast and noisy or slow and stable? Intrusion events that do not map to vulnerabilities MITRE

Applicability of CVE to IDS CVE 0 Vulnerabilities and exposures IDSes 0 Exploits, detects, decodes, anomalies, reconnaissance, probes, scans, malware. 0 System states 0 Events 0 0 0 0 0 0 0 0 0 0 Atomic entities Easier to classify Tools less varied Similar levels of granularity Easier to match across tools Hybrid entities Harder to classify Tools more varied Multiple levels of granularity Harder to match across tools 0 Many public databases 0 One public “database” 0 Known and provable 0 Bad cut-and-paste between vulnerabilities signatures, scans for incorrect vulnerability reports MITRE

CIEL (Common Intrusion Event List) 0 Standardize names for IDS events – Use lessons learned from CVE – Handle multiple levels of abstraction – Ease of use – Independent of the methods used to detect the event 0 Past Activities (2001) – Draft CIEL with almost 40 high-level entries created by MITRE Effectively a draft taxonomy Too complex Did not achieve exhaustiveness and mutual exclusiveness 0 CIEL Working Group – First meeting in March 2001 – Part of the CVE Editorial Board – Structure, membership, and process TBD 0 Current CIEL – Names formed from attributes MITRE

CVE in Incident Handling 0 Current Activity Summaries 0 0 0 0 – Which vulnerabilities are being actively exploited? Incident Reports – CVE clarifies which vulnerability was exploited Simplifies data collection from multiple sources Share incident data across teams Share data across language barriers MITRE

Responsible Disclosure and CVE: A Case Study 0 CVE analysis includes distinguishing between similar issues 0 Reporters who reserve CVE candidates must follow good disclosure practices to minimize errors 0 When reporter and vendor do not work closely together – Multiple CVE’s assigned to the same issue reporter describes symptom, vendor describes the problem – Inaccurate, incomplete, or unverified reports 0 When vendors do not acknowledge the vulnerability – Less likely that the Editorial Board will accept a candidate – Too resource-intensive to verify every report 0 When vendors do not include sufficient details in advisories – Can be difficult to tell which vulnerability was fixed – Change logs can be vague – Even credits aren’t always enough! – Source diffs (when available) may be insufficient MITRE

The CVE Strategy: Where are we? 4. Establish CVE in vendor fix-it sites and update mechanisms Adding CVE names broached with 13 groups. Commercial S/W Products Unreviewed Update and Fix Sites & Update Mechanisms Bugtraqs, Mailing lists, Hacker sites Discovery Policy Reviewed Advisories CERT, CIAC, Vendor advisories Security Products Scanners, Intrusion Detection, Vulnerability Databases 1. Inject CVE Names into advisories CVE names have been included in initial advisories from ISS XForce, Rain Forest Puppy, IBM, @stake, BindView, CERT/CC, HP, SGI, COMPAQ, Microsoft, Ernst & Young, eEye, CISCO, Rapid 7, NSFOCUS, Sanctum, SecurityFocus, VIGILANTe, Red Hat, Apache, and Apple. (as of 18 June 2002) 2. Establish CVE at security product level in order to . 2223 CVE Entries -- 2419 Candidates. 92 CVE-compatible products from 61 groups. 54 more from 27 others in “the works”. time Methodologies Purchasing Requirements Education 3. enable CVE to permeate the policy level. SANS / FBI Top 20 uses CVE names Network Computing IDS & Scanner Comparisons included CVE Draft NIST Rec. calls for use of CVE DSB Report calls for CVE compatibility Network World IDS Comparison included CVE coverage MITRE

Progress in a Nutshell 400 CANs Reserved Security Advisories Broached w/ 13 vendors SANS Top 20 Priority Lists Scanner Comparisons Software Vendor Patches Vulnerability Scanners Intrusion Detection Systems CIEL Incident Response & Reporting Research Cassandra FIRST Vulnerability Web Sites & Databases ICAT MITRE

For More Information CVE web site http://cve.mitre.org MITRE

MITRE