Marilyn Prosch, Ph.D., CIPP Arizona State University
10 Slides1.73 MB

Marilyn Prosch, Ph.D., CIPP Arizona State University
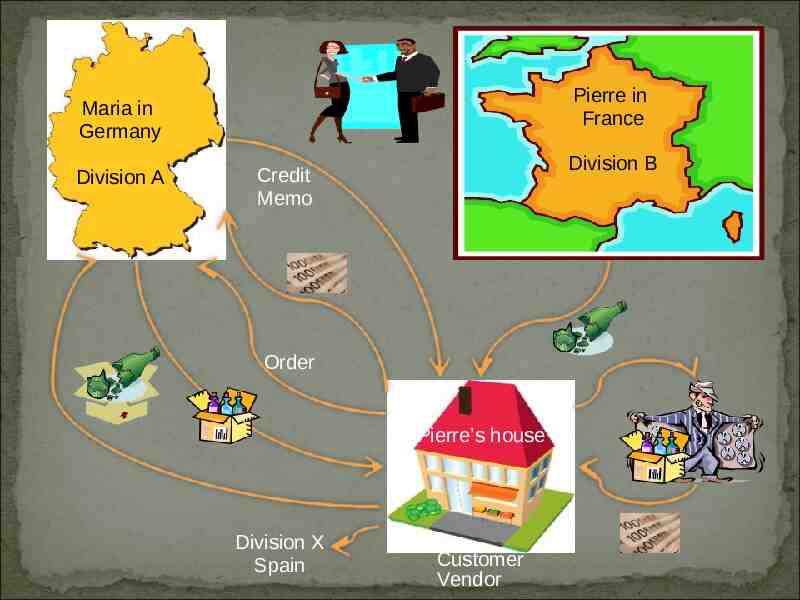
Pierre in France Maria in Germany Division A Division B Credit Memo Order Pierre’s house Division X Spain Customer Vendor

Multiple Divisions Multiple Countries Internal Audit will likely want to transfer employee data into a central repository
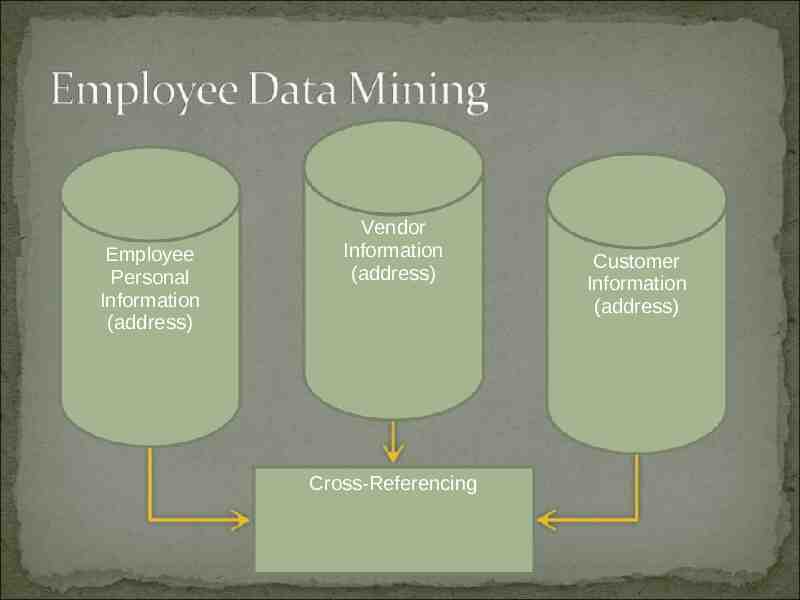
Employee Personal Information (address) Vendor Information (address) Cross-Referencing Customer Information (address)

Pierre’s house 2000-2007 Address 1 Pierre’s house 2008 Address 2 Anjuli’s house 2008 Address 1
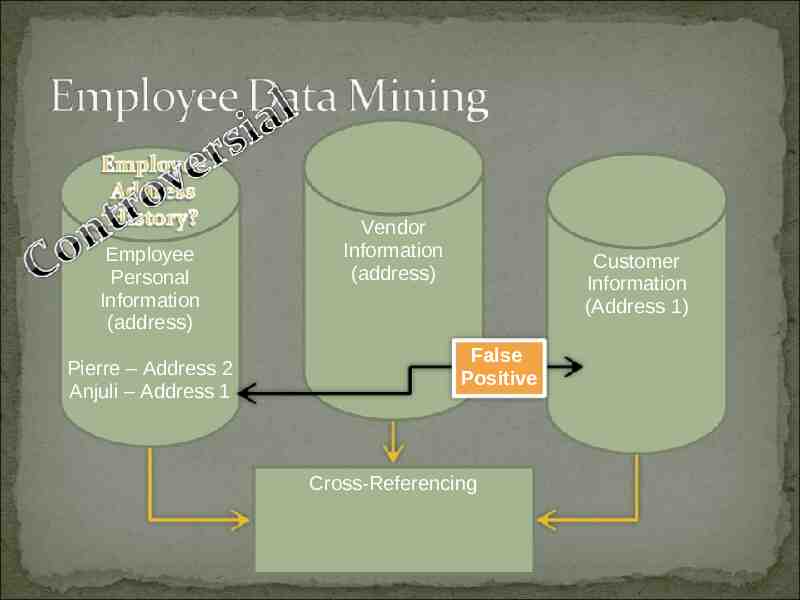
Employee Personal Information (address) Pierre – Address 2 Anjuli – Address 1 Vendor Information (address) Customer Information (Address 1) False Positive Cross-Referencing

EU law, until recently, restricted the transfer of personal data to countries not on the short list of those deemed to have adequate protections in place. US is not considered “adequate” EU data protection authorities have just amended the rules for overseas data transfers. The Article 29 Working Party has created Binding Corporate Rules (BCRs) that will allow companies to send data within an organization, but outside EU borders and into countries whose data protection standards the European Commission has not found adequate.

“In determining reasonableness, considerations include the breadth of the information collected, the extent of the intrusion, whether the collection and use relates to a specific investigation or whether it is an ongoing surveillance program of the employer implemented on the off chance that it might find something. Canadian law is in general not friendly to intrusive ongoing monitoring that is not incident or investigation based but might rather be characterized as a “fishing expedition.” It would come down to the employer’s situation, the demonstrated necessity for the program etc and proportionality vis a vis the employer’s needs and the employee’s right to privacy.”

One would need to ask questions such as: Would the database and data matching include all employees or is it more targeted Will there be any sensitive personal information involved Is the program likely to be effective in achieving its stated purpose? Conflict of interest/fraud detection – is there another less privacy intrusive way to monitor Is it the data matching ongoing or a one off or annual program? Is the program incident related? Incident activated? Is it reasonable and proportionate given the employer needs and purposes.

Descriptive research: What are companies actually doing? Are they aware of the issues? If so, how are they handling these issues? Are they using some kind of data masking during these processes? Normative research: How can we build privacy protection into processes? o o o o Data tagging and masking Data replication (logging) Security around possession and handling Data life and destruction techniques (poison pills)