Cyber Security Jobs
14 Slides4.38 MB

Cyber Security Jobs

The Importance of Cyber Security With respect to IT, security plays a crucial role in protecting company resources from unauthorized access. A company’s priority should always be the protection of sensitive information, making professions within the field of security more critical and sought after. 2 Everyday Cyber attacks are becoming more common and more damaging.
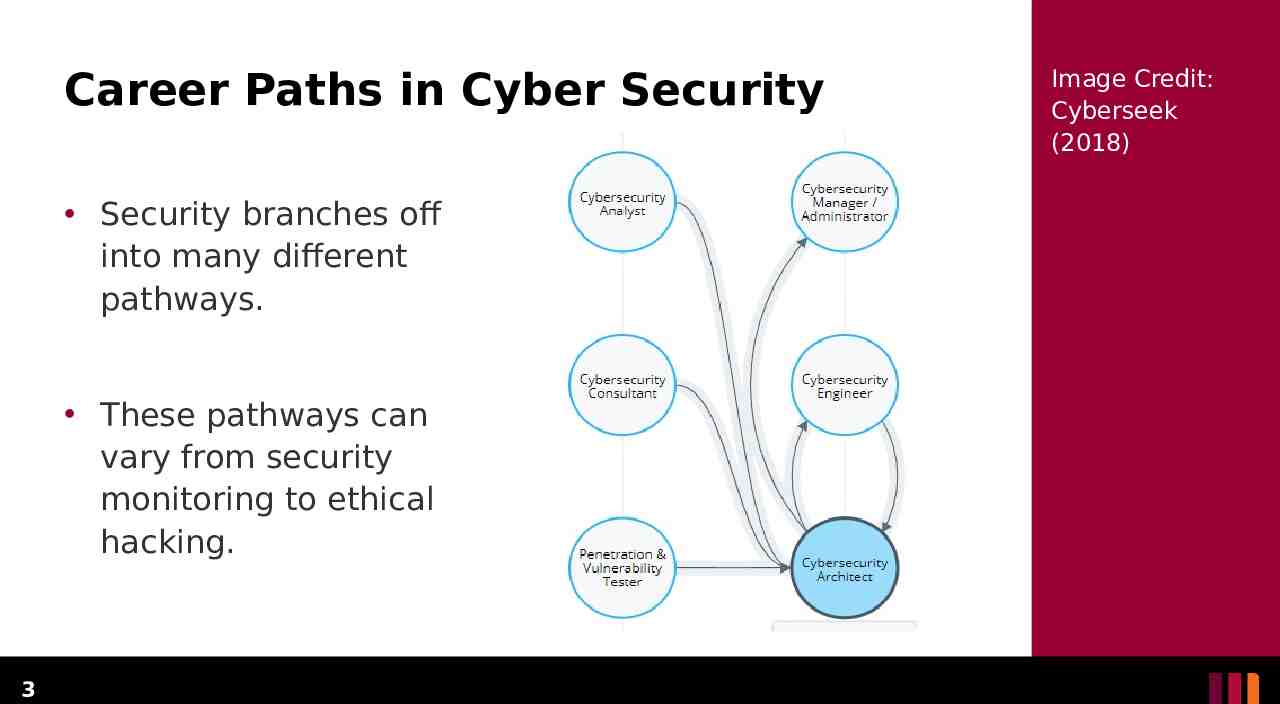
Career Paths in Cyber Security Security branches off into many different pathways. These pathways can vary from security monitoring to ethical hacking. 3 Image Credit: Cyberseek (2018)

Career Paths in Cyber Security The primary areas of concern consist of the following: Security Analyst Penetration Tester Bounty Hunters Security Architect Application Security Engineer 4 There are many more security positions and it is important to find the one that interests you.

Security Analyst Security analysts play a key role in keeping an organization’s sensitive information secure. They will often spend a lot of their time monitoring network activities within the company, checking for any suspicious activities that may result in malicious attacks. When an attack does occur, security analyst have a role in mitigating those attacks. 5

Penetration Tester The responsibilities of a Penetration Tester involve finding any vulnerabilities or exploits with a given a target. These targets could be Networks, Web Applications, Desktop, etc. The goal of finding vulnerabilities enables companies to create plans to mitigate those vulnerabilities which in turn can prevent a risk of an attack. 6 Penetration Testers are also called “ethical hackers” as they use their talents in hacking to secure organizations.

Bug Bounty Hunter Bug Bounty Hunters are essentially like Penetration testers, where their role is to find vulnerabilities. However, their job revolves around completing bug bounty programs on their own time rather then being hired as an employee. This program involves companies setting out rewards to individuals that are successful in finding a vulnerability. 7

Bug Bounty Hunter Continued This program is also set out to the public where anyone could part take in the program. Sites like HackerOne provide an easy way to find companies with the bug bounty program. Companies that are involved with HackerOne include: Android, Buzzfeed, Facebook, etc. 8

Security Architect Security Architects are responsible for designing, testing, and implementing security systems within an organization’s network. They often will review current security systems where they will make recommendation on new solutions to implement or upgrade. 9

Application Security Engineer Application Security Engineers assist in helping secure software applications that are developed and offered by organizations to consumers or employees. This position is more on the coding side of IT as they are expected to review code of a software product. Being an application security engineer you will also use penetration testing techniques to find vulnerabilities. 10

Application Security Engineer vs Penetration Tester This position can be very similar to that of a Penetration Tester. The difference is the Penetration Tester tests an entire environment, while the Application Security Engineer test single software products. 11

Skills for Cyber Security Careers Skills we generally would see in these positions include: 12 Communication Skills Security Principles Team Work Risk Analysis Problem Solving Skills Network Protocols Programming Skills Intrusion Detection Ethical Hacking Scripting Remember, there are a lot of ways to get into cyber security. A lot of people come from both technical and non-technical disciplines.

References 13 (2018). Retrieved from Cyberseek: https://www.cyberseek.org/pathway.html (2019). Retrieved from Forbes: https://www.forbes.com/sites/forbestechcouncil/2019/02/22/want-to-learn-codingcheck-out-these-resources-recommended-by-tech-experts/#1f568a065d6f (2019). Retrieved from Tech Target: https://searchsecurity.techtarget.com/definition/penetration-testing (2020). Retrieved from HackerOne: https://www.hackerone.com/branding GMERCYU. (2020). Retrieved from GMERCYU: https://www.gmercyu.edu/academics/learn/cs-cis-it-difference Khuspe, S. (2020). Retrieved from Cyberprime: https://cyberprime.net/getting-startedwith-web-application-penetration-testing/

References Continued 14 O'Hara, K. (2019). Retrieved from Monster: https://www.monster.com/career-advice/article/future-of-Cyber Security-jobs Perrin, J. (2016). Retrieved from https://www.le-vpn.com/last-mcafee-security-report-orhow-everyone-can-easily-become-a-cybercriminal/ Sobers, R. (2020). Retrieved from Varonis: https://www.varonis.com/blog/Cyber Security-careers/ Zhang, E. (2019). Retrieved from Digital Guardian: https://digitalguardian.com/blog/what-security-analyst-responsibilities-qualificationsand-more (2020). Retrieved from Penta: https://www.penta.ie/services/it-architects/