Lecture 1 1. 2. Introduction Basic Security Concepts
41 Slides489.50 KB

Lecture 1 1. 2. Introduction Basic Security Concepts

What is Cyber Security? Highly Technical People, processes, and technology Legislation and Regulation Risk management
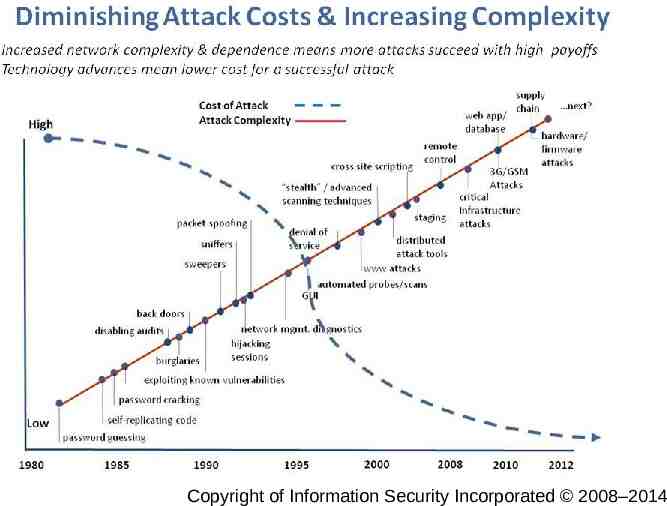
Lecture 1 Copyright CSCE of Information 522 - Farkas Security Incorporated 2008–2014 3

What Can I Do? 4
Class Information Class Homepage: https://cse.sc.edu/ farkas/csce522/csce522.htm Instructor: Csilla Farkas Office: Horizon II, 2253 Office Hours: Tuesday 11:45 am – 1:15 pm, Thursday 2:30 – 4:00 pm, or by appointment E-mail: [email protected] Lecture 1 CSCE 522 - Farkas 5
Teaching Assistant Theppatorn Rhujittawiwat, Office hours: Tuesdays and Thursdays 4:30 – 6:00 pm or by appointment Office location: Horizon II, 1215 Email: [email protected] Lecture 1 CSCE 522 - Farkas 6

Text Books Charles P. Pfleeger and Shari Lawrence Pfleeger, Security in Computing (5th Edition) (Hardcover), Prentice Hall PTR; ISBN: 9780134085043 Handouts Lecture 1 CSCE 522 - Farkas 7

Course Objective Understanding of Information Security Industry Academics Managerial Technical Leadership and Communication DEFENSE! Lecture 1 CSCE 522 - Farkas 8

TENTATIVE SCHEDULE Basic security concepts Cryptography, Secret Key Cryptography, Public Key Identification and Authentication, key-distribution centers, Kerberos Security Policies -- Discretionary Access Control, Mandatory Access Control Access control -- Role-Based, Provisional, and Logic-Based Access Control The Inference Problem Network and Internet Security, E-mail security, User Safety Program Security -- Viruses, Worms, etc. Firewalls Intrusion Detection, Fault tolerance and recovery Information Warfare Security Administration, Economic impact of cyber attacks Lecture 1 CSCE 522 - Farkas 9
Assignments Quizzes: quizzes on the previous class’ materials will be given randomly. Apogee students’ quizzes will be handled via email. Homework assignments: there will be several homework assignments during the semester. Homework should be individual work! There will be a late submission penalty of 20%/day after the due date. Cutoff date for the assignments is one week after due date. Lecture 1 CSCE 522 - Farkas 10

Assignments Group Project: group project to enable students to investigate security threats in currently evolving technologies. Exams: two closed book tests will cover the course material. Final exam is accumulative. Lecture 1 CSCE 522 - Farkas 11

Grading Quizzes: 10% Homework assignments: 15% Project : 20% Midterm: 25% Final exam: 30% Grades: 90 A , 85 B 90, 80 B 85, 75 C 80, 65 C 75, 60 D 65, 50 D 60, F 50 Graduate & Honors students must perform additional assignments to receive full credit. Lecture 1 CSCE 522 - Farkas 12

Reading Assignment Reading assignments for this class: Pfleeger: Ch 1 Reading assignments for next class: Pfleeger: Ch 2 Lecture 1 CSCE 522 - Farkas 13

Security Objectives Confidentiality: prevent/detect/deter improper disclosure of information Integrity: prevent/detect/deter improper modification of information Availability: prevent/detect/deter improper denial of access to services Lecture 1 CSCE 522 - Farkas 14

Military Example Confidentiality: target coordinates of a missile should not be improperly disclosed Integrity: target coordinates of missile should be correct Availability: missile should fire when proper command is issued Lecture 1 CSCE 522 - Farkas 15

Commercial Example Confidentiality: patient’s medical information should not be improperly disclosed Integrity: patient’s medical information should be correct Availability: patient’s medical information can be accessed when needed for treatment Lecture 1 CSCE 522 - Farkas 16

Fourth Objective Securing computing resources: prevent/detect/deter improper use of computing resources Hardware Software Data Network Lecture 1 CSCE 522 - Farkas 17

Question 1: What is the trade off between the security objectives? a) b) c) d) Confidentiality reduces integrity because secret data is higher quality Integrity requires that the data is kept in an isolated location and cannot be accessed Increased confidentiality may reduce availability Confidential and correct data has high trade off availability Lecture 1 CSCE 522 - Farkas 18

Achieving Security Organizational Goals Why to invest in security protection? Policy What to protect? Mechanism How to protect? Assurance How good is the protection? Lecture 1 CSCE 522 - Farkas 19
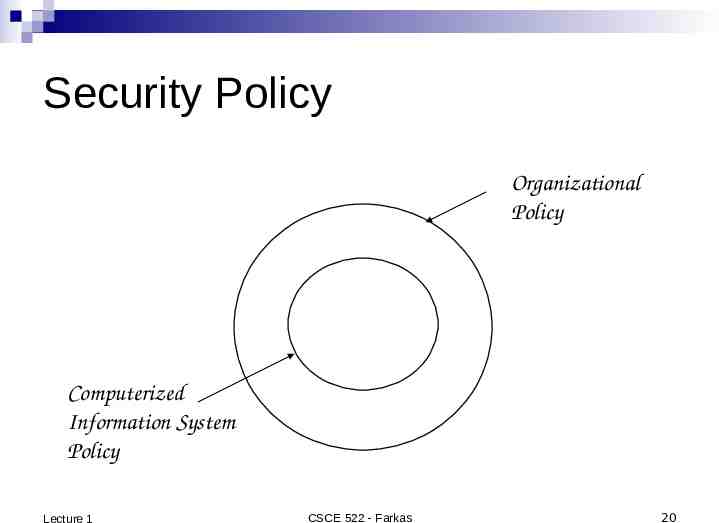
Security Policy Organizational Policy Computerized Information System Policy Lecture 1 CSCE 522 - Farkas 20

Question 2: Why do we need to fit the security policy into the organizational policy? a) b) c) d) Because the management would not pay for it otherwise Because security policy should support and protect organizational goals Because this will make the implementation easier Because it is mandated by law and regulation Lecture 1 CSCE 522 - Farkas 21

Security Mechanism Prevention Detection Tolerance/Recovery Lecture 1 CSCE 522 - Farkas 22

Security by Obscurity Hide inner working of the system Bad idea! Vendor independent open standard Widespread computer knowledge Lecture 1 CSCE 522 - Farkas 23

Security by Legislation Instruct users how to behave Not good enough! Important Only enhance security Targets only some of the security problems Lecture 1 CSCE 522 - Farkas 24
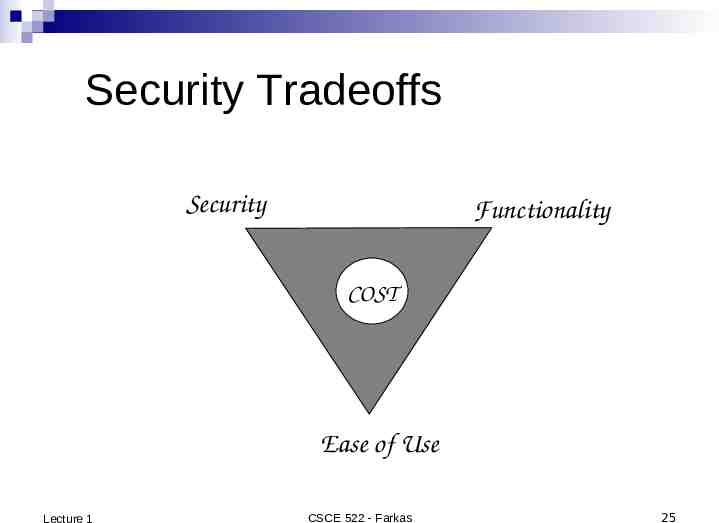
Security Tradeoffs Security Functionality COST Ease of Use Lecture 1 CSCE 522 - Farkas 25

Threat, Vulnerability, Risk Threat: potential occurrence that can have an Lecture 1 undesired effect on the system Vulnerability: characteristics of the system that makes is possible for a threat to potentially occur Attack: action of malicious intruder that exploits vulnerabilities of the system to cause a threat to occur Risk: measure of the possibility of security breaches and severity of the damage CSCE 522 - Farkas 26

Types of Threats (1) Errors of users Natural/man-made/machine disasters Dishonest insider Disgruntled insider Outsiders Lecture 1 CSCE 522 - Farkas 27

Types of Threats (2) Disclosure threat – dissemination of unauthorized information Integrity threat – incorrect modification of information Denial of service threat – access to a system resource is blocked Lecture 1 CSCE 522 - Farkas 28

Types of Attacks (1) Interruption – an asset is destroyed, unavailable or unusable (availability) Interception – unauthorized party gains access to an asset (confidentiality) Modification – unauthorized party tampers with asset (integrity) Fabrication – unauthorized party inserts counterfeit object into the system (authenticity) Denial – person denies taking an action (authenticity) Lecture 1 CSCE 522 - Farkas 29

Types of Attacks (2) Passive attacks: Eavesdropping Monitoring Active attacks: Masquerade – one entity pretends to be a different entity Replay – passive capture of information and its retransmission Modification of messages – legitimate message is altered Denial of service – prevents normal use of resources Lecture 1 CSCE 522 - Farkas 30

Computer Crime Any crime that involves computers or aided by the use of computers U.S. Federal Bureau of Investigation: reports uniform crime statistics Lecture 1 CSCE 522 - Farkas 31

Malicious Attacks Method: skills, knowledge, tools, information, etc. Opportunity: time and access Motive: reason to perform the action How can defense influence these aspects of attacks? Lecture 1 CSCE 522 - Farkas 32

Computer Criminals Amateurs: regular users, who exploit the vulnerabilities of the computer system Motivation: easy access to vulnerable resources Crackers: attempt to access computing facilities for which they do not have the authorization Motivation: enjoy challenge, curiosity Career criminals: professionals who understand the computer system and its vulnerabilities Motivation: personal gain (e.g., financial) Lecture 1 CSCE 522 - Farkas 33

Methods of Defense Prevent: block attack Deter: make the attack harder Deflect: make other targets more attractive Detect: identify misuse Tolerate: function under attack Recover: restore to correct state Lecture 1 CSCE 522 - Farkas 34

Information Security Planning Organization Analysis Risk management Mitigation approaches and their costs Security policy Implementation and testing Security training and awareness Lecture 1 CSCE 522 - Farkas 35

Risk Management Lecture 1 CSCE 522 - Farkas 36
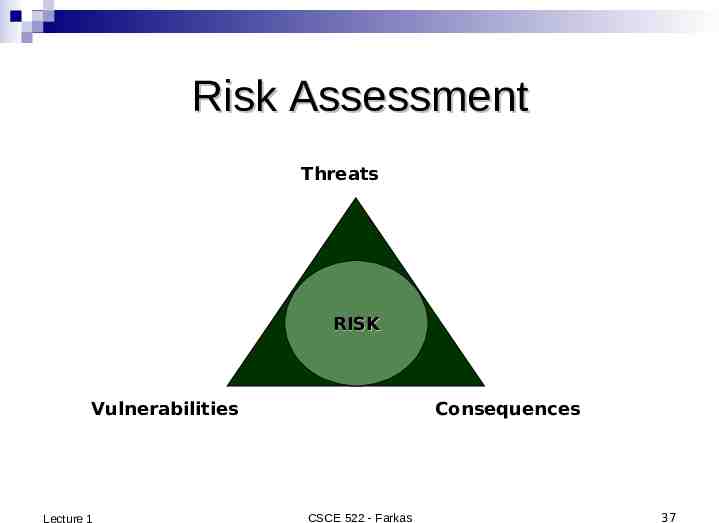
Risk Assessment Threats RISK Vulnerabilities Lecture 1 Consequences CSCE 522 - Farkas 37
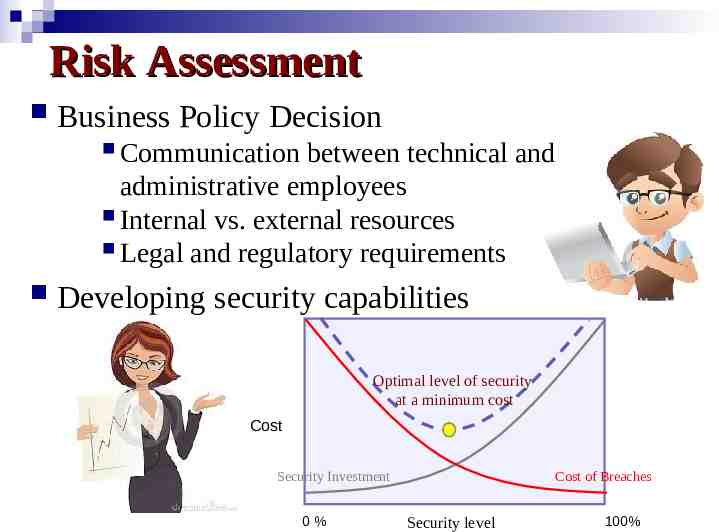
Risk Assessment Business Policy Decision Communication between technical and administrative employees Internal vs. external resources Legal and regulatory requirements Developing security capabilities Optimal level of security at a minimum cost Cost Security Investment 0% Cost of Breaches Security level 100%

Real Cost of Cyber Attack Damage of the target may not reflect the real amount of damage Services may rely on the attacked service, causing a cascading and escalating damage Need: support for decision makers to – Evaluate risk and consequences of cyber attacks – Support methods to prevent, deter, and mitigate consequences of attacks Lecture 1 CSCE 522 - Farkas 39
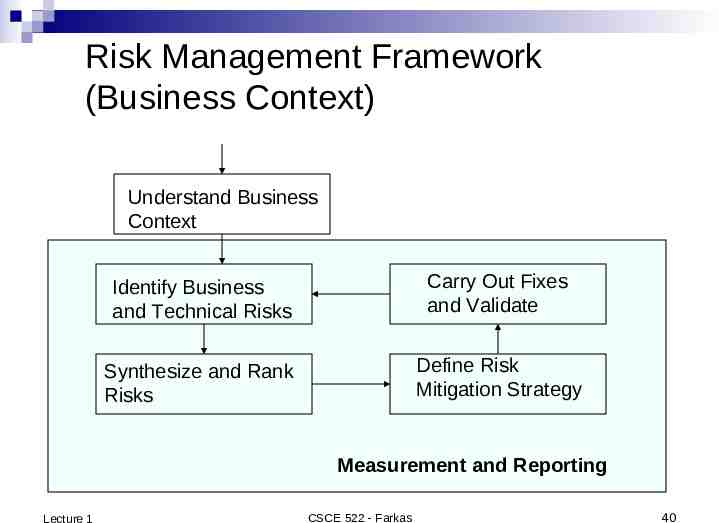
Risk Management Framework (Business Context) Understand Business Context Identify Business and Technical Risks Carry Out Fixes and Validate Synthesize and Rank Risks Define Risk Mitigation Strategy Measurement and Reporting Lecture 1 CSCE 522 - Farkas 40

Next Class Cryptography The science and study of secret writing Lecture 1 CSCE 522 - Farkas 41






