IS 483 Information Systems Management James Nowotarski 1 May 2003
75 Slides261.50 KB

IS 483 Information Systems Management James Nowotarski 1 May 2003

Today’s Objectives Deepen understanding of service level agreements (SLA) Understand fundamentals of operations management Understand primary approaches to end user training

Today’s agenda Topic Duration Recap last week 15 minutes Operations management 60 minutes *** Break 15 minutes Operations management 45 minutes Quiz 15 minutes Assignment 3 5 minutes End user training 30 minutes

Today’s agenda Topic Duration Recap last week 15 minutes Operations management 60 minutes *** Break 15 minutes Operations management 45 minutes Quiz 15 minutes Assignment 3 5 minutes End user training 30 minutes

Importance of business focus in network solutions Computer Associates and others have pointed out the importance of business focus when providing network solutions Some of today’s key business drivers Globalization Mobile enterprise Lower cost/Increased capability Security threats 24/7/365 availability Increased reach and content of today’s applications

Network management architecture Source: Cisco

Network Management Functions Fault management Configuration management Accounting management Performance management Security management Source: International Standards Organization (ISO)

Management of Systems Environments Users Internal SLA External SLA SLA Vendors Systems Management Network Mgmt Server Mgmt etc. IT Service Management Developers

Service Level Agreements Service Provider Service User Internal IT network group End user group (i.e., business unit) External Vendor End user group -- IT network group coordinates Type of SLA

Service Level Agreements Table of Contents Dates (start, expiration) Types of services provided Service measures Roles/Responsibilities (provider, consumer) Resources needed and/or costs charged Reporting mechanism Signatures

Service Level Agreements Disciplines Service Types Availability Performance Management Reliability Response time Configuration Management Application versions & enhancements Accounting Management Reporting procedure Fault Management Incident management, e.g., database failure workstation failure Security Management Recovery Management Backup Recovery Capacity Planning Online Systems Output handling Batch Systems Schedule execution

Trends Overall: Network infrastructure more intelligent Data/Voice convergence – Examples: VoIP, unified messaging Exponential growth in # of managed elements – Used to be 1 element per 8000 subscriber lines – Now closer to 1:1, will soon be M:1 subscriber due to new technologies (ATM, SONET), complexity Security – File sharing and Instant Messaging (IM) software routinely subvert firewalls Business continuity Rich media Web services Network attached storage

Trends (cont.) Mobile/Wireless – Five years ago, mobile users were 5 percent of the population – Now, upwards of 50 percent might be mobile part of the time – Security issues: IEEE working on IEEE 802.11i to be released in 2003 – Security is #1; coverage, ubiquity and quality of service (QoS) fall under #2 – “Our enterprise customers are now supplying WLANs as a strategic part of their networks . . . With the proliferation of WLAN technology, customers have become increasingly concerned about security and interoperability . . . it’s important to maintain real interoperability across many vendors, not just one or two” (Gary Berzack, CEO of Tribeca Technologies, wireless solution provider, CRN, 3/31/03)
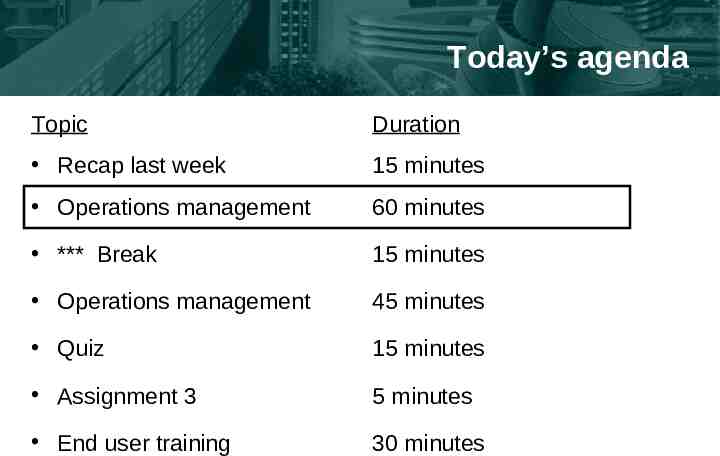
Today’s agenda Topic Duration Recap last week 15 minutes Operations management 60 minutes *** Break 15 minutes Operations management 45 minutes Quiz 15 minutes Assignment 3 5 minutes End user training 30 minutes

Operations Management - What is it? Operations Management is the planning and management of . . . Computer hardware (servers, workstations, etc.) Communications lines and equipment (hubs, routers, switches, gateways, etc.) Software (applications, system software, utilities) Data centers (control rooms, console operations, libraries, backup, etc.) Disaster recovery - detailed procedures/processes for recovering data and applications Security (firewalls, intrusion detection, user authentication, etc.) Personnel for the above (e.g., operators, programmers, technicians, etc.)

Where Operations Management Fits Example: IT functional alignment is organizing IT personnel by primary tasks Director - IS/IT Manager, Systems Development Manager, Application Maintenance Manager, Computer Operations

Where Operations Management Fits 4B revenue company 400 person IT shop, 70M Director - CIO Director, IS Planning Enterprise Arch Security S/W Evaluation Director, Software Engineering Developers Development tools Director, Business Technology Business analysts Program managers Data warehouse Manager, Production Operations Help desk Application support Manager, Administration Director, Technical Services Network PC technicians

Operations Management - Who Cares? Key Objectives Cost Containment – Typical IT budget breakdown: .57 data center operations .33 systems and programming .10 admin and training Reliability – Problems are very visible Adaptability – Extend existing functions – Take on new jobs Benefits Realization – Improve quality of service – Revenue generating opportunities

Operations Management - What is it? Operations Management is the planning and management of . . . Computer hardware (servers, workstations, etc.) Communications lines and equipment (hubs, routers, switches, gateways, etc.) Software (applications, system software, utilities) Data centers (control rooms, console operations, libraries, backup, etc.) Disaster recovery - detailed procedures/processes for recovering data and applications Security (firewalls, intrusion detection, user authentication, etc.) Personnel for the above (e.g., operators, programmers, technicians, etc.)

Data Centers Data Center Functions 1. 2. 3. 4. 5. Console monitoring Input/Output control Manual media distribution Backups Production coordination

Data Center Functions Console monitoring Monitor and ensure acceptable performance of: – – – – servers databases networks applications Detect and correct problems Shut down components for servicing

Data Center Functions Input/Output Control Compare calculated control numbers on input to actuals to ensure integrity Compare output control numbers to input control numbers to ensure integrity

Data Center Functions Manual Media Distribution Distribute non-electronic media, e.g., reports Done on ad-hoc or scheduled basis to agreed standards of delivery

Data Center Functions Backup Make and control copies and backups of: – – – – databases logs software utilities Transfer backups to offsite storage facilities For crucial/sensitive items, maintain backups at several sites Enable retrieval of backups for recovery purposes

Data Center Functions Production Coordination Schedule and run production processes – applications – utilities – backups Coordinate with stakeholders on outages, problems, changes, etc.

Data Center Set-Up Managerial Considerations Evaluation of user expectations Use of vendors Proximity issues Measures and controls Procure needed human resources Define test plan Physical security Buy vs. lease the facility

Data Center Set-Up Technical Considerations Location of the data center (access to needed resources) Power issues Fire suppression Telephone-company connectivity Cable management Cooling system Security/Backup procedures

Data Center Set-Up Technical Considerations Location of the data center (access to needed resources) Power issues Fire suppression Telephone-company connectivity Cable management Cooling system Security/Backup procedures

Fire Suppression Q. Which of the following methods of suppressing a fire in a data center is the MOST effective and environmentally friendly? a. b. c. d. Halon gas Wet-pipe sprinklers Dry-pipe sprinklers Carbon dioxide

Fire Suppression Q. Which of the following methods of suppressing a fire in a data center is the MOST effective and environmentally friendly? a. b. c. d. Halon gas Wet-pipe sprinklers Dry-pipe sprinklers Carbon dioxide Explanation: Water sprinklers, with an automatic power shut-off system, are accepted as efficient because they can be set to automatic release without threat to life and water is environmentally friendly. Sprinklers must be dry-pipe to prevent the risk of leakage. Halon is efficient and effective as it does not threaten human life, and therefore can be set to automatic release, but it is environmentally damaging and very expensive. Water is an acceptable medium but the pipes should be empty to avoid leakage, so a full system is not a viable option. Carbon dioxide is accepted as an environmentally acceptable gas, but it is less efficient as it cannot be set to automatic release in a staffed site because it threatens life.

A Word on Security According to the 2002 CSI/FBI Computer Crime and Security Survey, more than 90% of the study's 503 respondents (mainly Fortune 500 corporations and government agencies) reported detecting a computer system security breach within the last year, with the average annual financial loss reported at about 5 million. - Application Development Trends, Oct. 2002

A Word on Security “Before, [small businesses] first looked at getting their site up with us quickly, then at high-availability services and lastly at security. Now they’re more concerned about their site being compromised, so security is taking precedence over things such as high availability” - Steve Mann, director of network and security engineering at NaviSite, Andover, Mass, Computer Reseller News, 10/14/2002

A Word on Security Bringing together the various departments of a company -- HR, MIS, legal, etc. -- to develop and enforce policies is essential to tackling the security problem. You evaluate, you write the policies, you educate the employees and you put the enforcement technology in place, and then you start again every month of every quarter. It’s just doing due diligence. - Computer Reseller News, 10/14/2002

A Word on Security “Transaction theft and application exploits are where we see things moving . . . vendors introducing more comprehensive securitymanagement products (Symantec, SAS, IBM). . . Despite the growing sophistication and comprehensiveness of security management systems, IT professionals will face tough integration tasks for years to come . . . no single product addresses the many areas that need attention, including improved usability and forensics” - Information Week, 7 October 2002

Security Web Site http://www.infosyssec.com/

Disaster Recovery Planning Primary Objective Enable an organization to survive a disaster and to continue normal business operations. Specific Goals Assess existing vulnerabilities Implement disaster avoidance and prevention procedures Develop comprehensive plan to enable organization to react appropriately and in a timely manner if disaster strikes

Disaster Recovery Planning vs. Business Continuity Business Continuity Disaster recovery Business resumption and recovery (workplace to rebuild systems and the business) Crisis management (how executives respond to and make decisions during a crisis)

Business Continuity Project Team Departments Involved Real estate and facilities Security Human resources Information systems Communications Technology, planning, and development Audit department oversees process

Disaster Recovery Planning What is meant by this statement? Disaster recovery planning is not a two-month project, neither is it a project that once completed, you can forget about. An effective recovery plan is a live recovery plan. - Computing and Network Services (CNS)

Disaster Recovery Planning Key Success Factors Continuous process, not a discrete process Involves IT and the business units Essential that required resources (personnel, capital, expenses) are available during development and ongoing maintenance of the program

Disaster Recovery Planning Two out of five enterprises that experience a disaster, such as a terrorist attack or an extreme force of nature, go out of business within five years. Need to immediately begin developing and testing businesscontinuity plans and seeking disaster-recovery services. - Gartner Group, Sept. 2001

Disaster Recovery Planning The most critical data storage device in an enterprise -the mainframe -- is typically overlooked during disaster recovery planning. That's according to mainframe security maven Ronn H. Baily, who made the observation during a recent briefing at the White House. "Mainframe computers are less secure now than they were just seven to 10 years ago,“ Baily said, "and mainframe systems, by and large, are very vulnerable to unauthorized access, misuse and attack.“ - Application Development Trends, Oct. 2002

Operations Management - How to Improve Approaches to Meeting Objectives Centralize resources Automate operations Replace/Streamline legacy applications Outsource Continuous process improvement

Operations Management - How to improve Centralize resources Locate resources in same physical location(s) Can reduce support costs without jeopardizing service levels Enables greater standardization of processes Enables continual streamlining of operations processes

Operations Management - How to improve Automate Operations Partial or full (“lights out”) automation of data center functions Example: Automatic response to console messages (80% of messages can be handled this way) Example: Intelligently manage data center assets (e.g., servers) through software that can summon capacity as needed – – – IBM’s Project eLiza HP’s Adaptive Management Platform Sun’s N1 Computer operators going way of telephone operators Implications for data center managers: – – – Focus more on business issues than technical issues Plan more than react Focus on customer service

Operations Management - How to improve Replace/Streamline Legacy Applications Upgrade to minimize human intervention Replace with higher-quality, more reliable, more adaptable components

Operations Management - How to improve Outsource Third party handles computer operations, network operations, application maintenance, and/or other IS functions Typically for a specified period of time, e.g., 10 years Leads to lower costs and frees up IS personnel to focus on more strategic projects Recent variation: Application Service Providers (ASPs) IS departments can underbid outsourcers, if they are doing a good job

Operations Management - How to improve Continuous Process Improvement Plan Act Do Check

Operations Management - How to Improve Metrics are required to determine whether goals are being met Example Objective: Student arrives at class on time Metric: ? Target Value: ?

Small Group Discussion Identify metrics and targets for each of the SLA service types below: Performance? Reliability (outages)? Security management? Incident management (i.e., responding to problems)? Schedule execution (i.e., batch runs)?

Trend: ROI Optimization Many companies refocusing their technology spending on solutions that consolidate and optimize existing infrastructure and squeeze out a better return on investment Example: GM now runs on 80 Lotus Notes servers instead of 300 and has halved the array of software products used to run operations

Trend: Increased Need for Storage Management email proliferation explosion of multimedia content business continuity – multiple copies of data on the network trend to network attached storage

Trend: Automatic Systems Management Managing IT in a way that’s pegged to a company’s demand for computing power Computer Associates IBM HP Microsoft

Today’s agenda Topic Duration Recap last week 15 minutes Operations management 60 minutes *** Break 15 minutes Operations management 45 minutes Quiz 15 minutes Assignment 3 5 minutes End user training 30 minutes

Today’s agenda Topic Duration Recap last week 15 minutes Operations management 60 minutes *** Break 15 minutes Operations management 45 minutes Quiz 15 minutes Assignment 3 5 minutes End user training 30 minutes

Today’s agenda Topic Duration Recap last week 15 minutes Operations management 60 minutes *** Break 15 minutes Operations management 45 minutes Quiz 15 minutes Assignment 3 5 minutes End user training 30 minutes

Business Process Reengineering (BPR) Use of technology to change specific business processes Typical goals: – Cost reduction – Time reduction – Increased quality of outcome Example: Ford reengineers purchasing/accounts payable, eliminating need for vendor invoices

Enterprise Resource Planning (ERP) Packaged application software to address common business functions Some customization through switches and parameters, but NO changes to core application Emphasis is on changing the business to what the ERP does, not on changing the ERP Tight integration among modules and data Rich functionality Process orientation: Streamline processes

BPR vs. ERP BPR ERP Business process impact Radically redesign process Use process imposed by package Software delivery approach Mostly custom Package Software upgrade responsibility Enterprise Vendor Biggest challenge Adoption by the enterprise Adoption by the enterprise

Human Resource Impacts of BPR and ERP Both BPR and ERP are high risk projects that frequently fail to live up to expectations Process Tech People Lack of visible leadership/sponsorship Lack of adequate training Lack of communication Death by 1000 initiatives New/Changed roles not implemented New/Changed incentives/rewards not implemented

End User Training Benefits Helps to overcome resistance to change Boosts productivity More knowledgeable and effective workers Drives down support costs – help desk support – support from colleagues Increases self-worth, confidence, morale, retention

End User Training Major Types of Training Third-Party Training Classes In-House Training Classes Traditional Self-Study Computer-Based Training Web-based training Video-based training (“highly animated cave paintings”)

Small Group Discussions List Advantages and Disadvantages of Each: Third-Party Training Classes In-House Training Classes Traditional Self-Study Computer-Based Training Web-based training Video-based training

End User Training Third-Party Training Classes Advantages Disadvantages

End User Training In-House Training Classes Advantages Disadvantages

End User Training Traditional Self-Study Advantages Disadvantages

End User Training Computer-Based Training Advantages Disadvantages

End User Training Web-Based Training Advantages Disadvantages

End User Training Video-Based Training Advantages Disadvantages

End User Training Other Types of Training eLearning Executive education Integrated performance support (e.g., online help) Management training Mentoring, coaching

User training and total cost of ownership call volume call complexity time

User training and total cost of ownership Increases total cost of ownership Not providing any training Providing training at the wrong time Providing ineffective training Replacing software with same level of functionality Providing functionality not required by user Decreases user productivity/ effectiveness Process-related, rather than application-specific training Additional software functionality (new or existing software) Increases user productivity/ effectiveness Providing FAQ’s from the help desk Training new users Source: Gartner Decreases total cost of ownership Retraining existing users on functionality they have forgotten

Training IT Training Emphasis Management training Customer service training Communication skills training (e.g., presentations, writing)

Training Questions for Discussion What is the relationship between end user training costs and graphical user interfaces (GUIs)? What is the impact of distributed systems on training of user support personnel (do they require more or less training)? Should an organization provide training in areas not directly applicable to a person’s job responsibilities (e.g., provide training on web page publishing)?

End of slides






