Working Group 6: Secure Hardware and Software – Security by
16 Slides1,005.41 KB

Working Group 6: Secure Hardware and Software – Security by Design Presentation of Final Report (Deliverable 1) March 16, 2016 Joel Molinoff, Co-Chair (CBS) Brian Scarpelli, Co-Chair (ACT The App Association)

WG 6 Objectives Develop recommendations and best practices to enhance the security of hardware and software in the core public communications network Develop voluntary mechanisms to demonstrate success of recommendations/best practices 2

WG 6 Deliverables March 2016 – Security best practices recommendations September 2016 – Recommend voluntary attestation framework 3
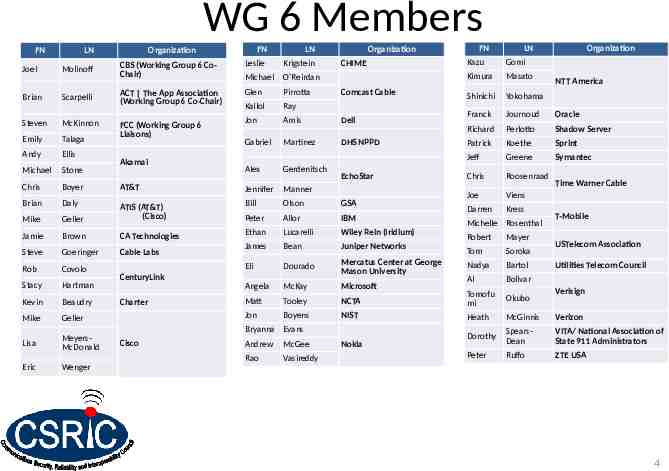
WG 6 Members FN Joel FN LN CBS (Working Group 6 CoChair) Leslie Krigstein Michael O’Reirdan ACT The App Association (Working Group 6 Co-Chair) Glen Pirrotta Kallol Ray Jon Amis Dell Gabriel Martinez DHS NPPD Alex Gerdenitsch LN Molinoff Organization Comcast Cable Brian Scarpelli Steven McKinnon Emily Talaga Andy Ellis Michael Stone Chris Boyer AT&T Jennifer Manner Brian Daly Bill Olson GSA Mike Geller ATIS (AT&T) (Cisco) Peter Allor IBM Jamie Brown CA Technologies Ethan Lucarelli Wiley Rein (Iridium) James Bean Juniper Networks Eli Dourado Mercatus Center at George Mason University Steve Goeringer Rob Covolo Stacy Hartman Kevin Beaudry Mike Geller Lisa MeyersMcDonald Eric Wenger FCC (Working Group 6 Liaisons) Akamai Cable Labs CenturyLink Charter EchoStar LN Organization Kazu Gomi Kimura Masato Shinichi Yokohama Franck Journoud Oracle Richard Perlotto Shadow Server Patrick Koethe Sprint Jeff Greene Symantec Chris Roosenraad Joe Viens Darren Kress Michelle Rosenthal Robert Mayer Tom Soroka Nadya Bartol Al Bolivar NTT America Time Warner Cable T-Mobile USTelecom Association Utilities Telecom Council Angela McKay Microsoft Matt Tooley NCTA Tomofu mi Okubo Jon Boyens NIST Heath McGinnis Verizon Dorothy SpearsDean VITA/ National Association of State 911 Administrators Peter Ruffo ZTE USA Bryanna Evans Cisco FN Organization CHIME Andrew McGee Rao Vasireddy Nokia Verisign 4

Background Recognizing the advantages of building security in to hardware and software (rather than retrofitting), FCC has urged industry to examine security by design practices for core network equipment CSRIC IV’s WG 4 Final Report, Cybersecurity Risk Management and Best Practices, provides baseline/model for approach 5
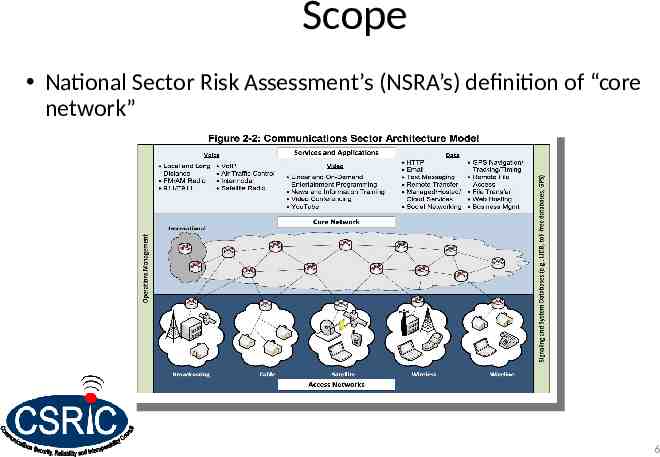
Scope National Sector Risk Assessment’s (NSRA’s) definition of “core network” 6

Scope Report addresses best practices for service providers seeking to manage cybersecurity risks associated with technology obtained from third party vendors, suppliers, and/or integrators for use in their core networks. WG 6 leveraged the NIST Cybersecurity Framework to provide recommendations that can be adopted by communications sector stakeholders to improve security-by-design practices. 7

Findings A rich body of information exists to help companies evaluate and manage cybersecurity risk, and the development of security-bydesign principles. 8

Findings Given the diverse type and functions of vendors and suppliers serving core network providers, any risk management recommendations are at a macro level and process-based, so as to allow for their extensibility and utility across technologies and services. 9

Findings WG 6 has completed an assessment (based on the NIST Cybersecurity Framework) of measures that a communications sector member should utilize to review security-bydesign protections with vendors and suppliers. 10

Findings Service providers should establish upfront which party will be responsible for managing risks associated with the operation of the technology. The approach may vary depending upon the circumstances. 11
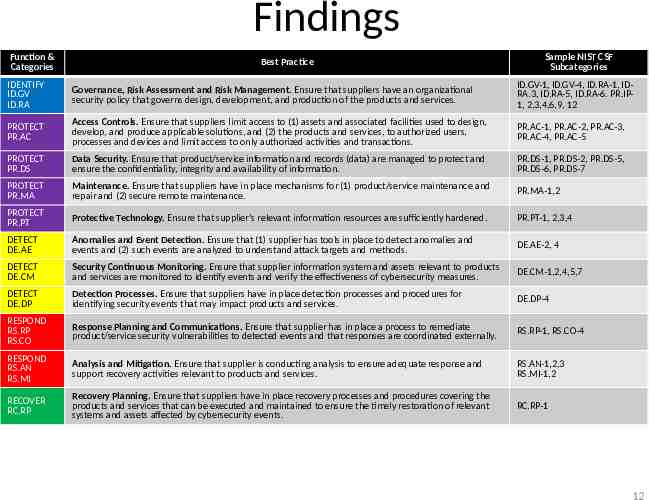
Findings Function & Categories Best Practice Sample NIST CSF Subcategories IDENTIFY ID.GV ID.RA Governance, Risk Assessment and Risk Management. Ensure that suppliers have an organizational security policy that governs design, development, and production of the products and services. ID.GV-1, ID.GV-4, ID.RA-1, IDRA.3, ID.RA-5, ID.RA-6. PR.IP1, 2,3,4,6,9, 12 PROTECT PR.AC Access Controls. Ensure that suppliers limit access to (1) assets and associated facilities used to design, develop, and produce applicable solutions, and (2) the products and services, to authorized users, processes and devices and limit access to only authorized activities and transactions. PR.AC-1, PR.AC-2, PR.AC-3, PR.AC-4, PR.AC-5 PROTECT PR.DS Data Security. Ensure that product/service information and records (data) are managed to protect and ensure the confidentiality, integrity and availability of information. PR.DS-1, PR.DS-2, PR.DS-5, PR.DS-6, PR.DS-7 PROTECT PR.MA Maintenance. Ensure that suppliers have in place mechanisms for (1) product/service maintenance and repair and (2) secure remote maintenance. PR.MA-1,2 PROTECT PR.PT Protective Technology. Ensure that supplier’s relevant information resources are sufficiently hardened. PR.PT-1, 2,3,4 DETECT DE.AE Anomalies and Event Detection. Ensure that (1) supplier has tools in place to detect anomalies and events and (2) such events are analyzed to understand attack targets and methods. DE.AE-2, 4 DETECT DE.CM Security Continuous Monitoring. Ensure that supplier information system and assets relevant to products and services are monitored to identify events and verify the effectiveness of cybersecurity measures. DE.CM-1,2,4,5,7 DETECT DE.DP Detection Processes. Ensure that suppliers have in place detection processes and procedures for identifying security events that may impact products and services. DE.DP-4 RESPOND RS.RP RS.CO Response Planning and Communications. Ensure that supplier has in place a process to remediate product/service security vulnerabilities to detected events and that responses are coordinated externally. RS.RP-1, RS.CO-4 RESPOND RS.AN RS.MI Analysis and Mitigation. Ensure that supplier is conducting analysis to ensure adequate response and support recovery activities relevant to products and services. RS.AN-1,2,3 RS.MI-1,2 RECOVER RC.RP Recovery Planning. Ensure that suppliers have in place recovery processes and procedures covering the products and services that can be executed and maintained to ensure the timely restoration of relevant systems and assets affected by cybersecurity events. RC.RP-1 12

Recommendations Communications sector members should use the best practices detailed in this report as a reference for working with vendors and suppliers to reduce cybersecurity risk within the core network. 13

Recommendations Public-private coordination and collaboration in advancing security-by-design should be encouraged and enabled in order to avoid inconsistencies in approaches to security-bydesign and to ensure increased intelligence sharing. Information sharing about supplier risk between government and industry is recommended. 14
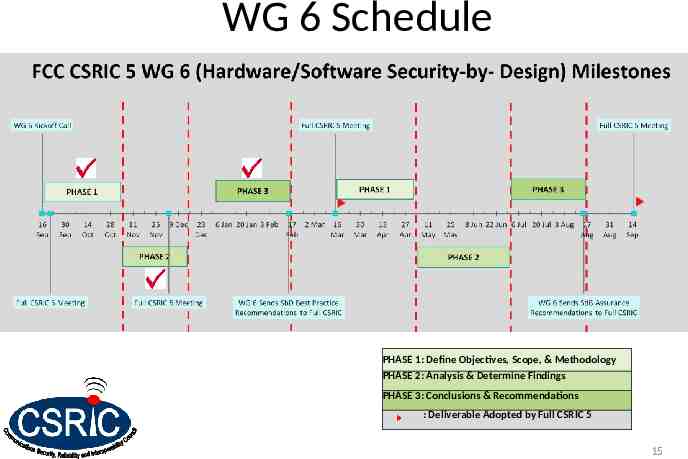
WG 6 Schedule PHASE 1: Define Objectives, Scope, & Methodology PHASE 2: Analysis & Determine Findings PHASE 3: Conclusions & Recommendations : Deliverable Adopted by Full CSRIC 5 15

Next Steps Shift WG focus to 2nd deliverable (develop voluntary mechanisms to demonstrate success of recommendations/best practices) Continue bi-weekly conference calls Provide periodic status updates to Steering Committee and Council 16






