Integrating security into modern software development: A workflow
55 Slides8.16 MB

Integrating security into modern software development: A workflow study Lucas Charles Secure Software Engineer @ GitLab about.gitlab.com 1
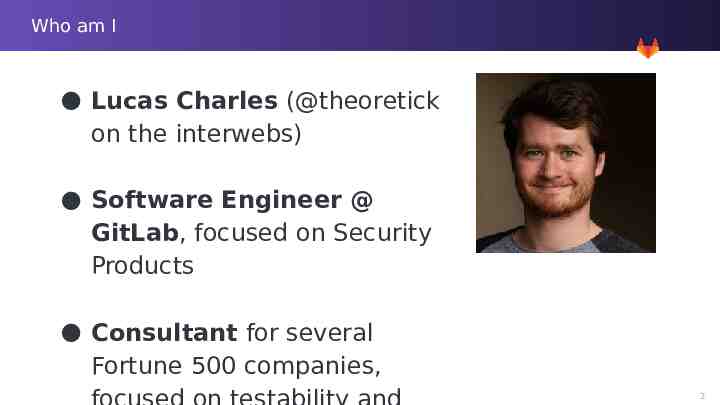
Who am I Lucas Charles (@theoretick on the interwebs) Software Engineer @ GitLab, focused on Security Products Consultant for several Fortune 500 companies, 2
What I care about Tooling 3

What I care about Tooling Collaboration 4

What I care about Tooling Collaboration Transparency 5
Why I care about these things Results! Happiness! ᕕ( ᐛ )ᕗ 6

The Problem: A landscape overview 7
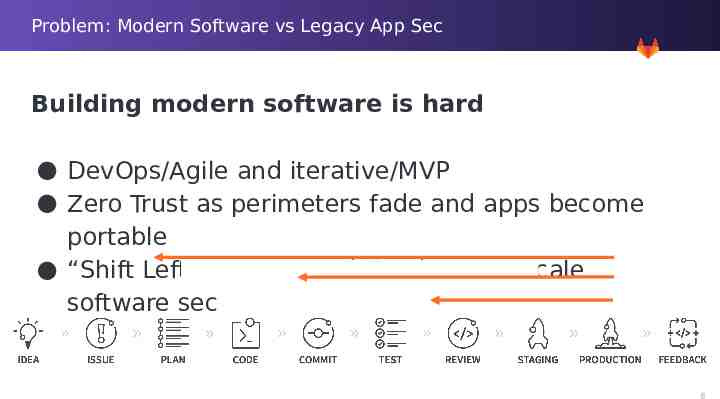
Problem: Modern Software vs Legacy App Sec Building modern software is hard DevOps/Agile and iterative/MVP Zero Trust as perimeters fade and apps become portable “Shift Left” security and the desire to scale software sec 8
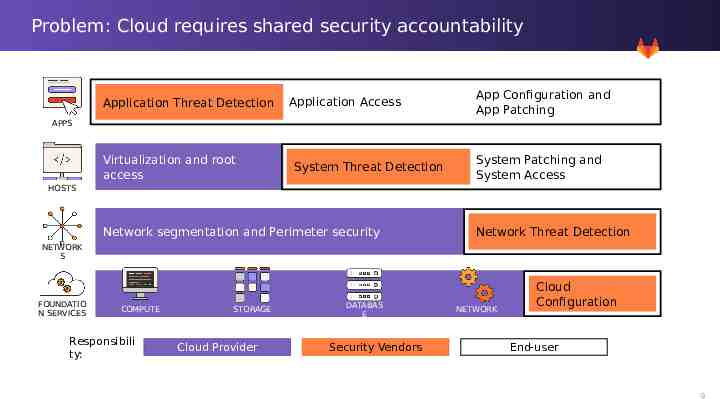
Problem: Cloud requires shared security accountability Application Threat Detection Application Access App Configuration and App Patching APPS Virtualization and root access System Threat Detection System Patching and System Access HOSTS Network segmentation and Perimeter security Network Threat Detection NETWORK S FOUNDATIO N SERVICES COMPUTE Responsibili ty: STORAGE Cloud Provider DATABAS E Security Vendors NETWORK Cloud Configuration End-user 9
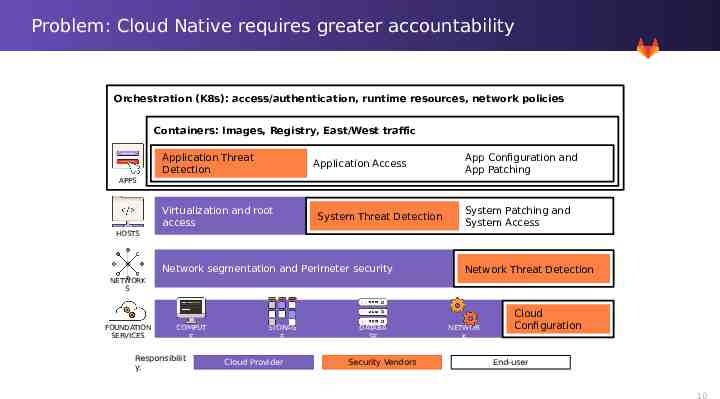
Problem: Cloud Native requires greater accountability Orchestration (K8s): access/authentication, runtime resources, network policies Containers: Images, Registry, East/West traffic Application Threat Detection Application Access App Configuration and App Patching APPS Virtualization and root access System Threat Detection System Patching and System Access HOSTS Network segmentation and Perimeter security Network Threat Detection NETWORK S FOUNDATION SERVICES COMPUT E Responsibilit y: STORAG E Cloud Provider DATABA SE Security Vendors NETWOR K Cloud Configuration End-user 10
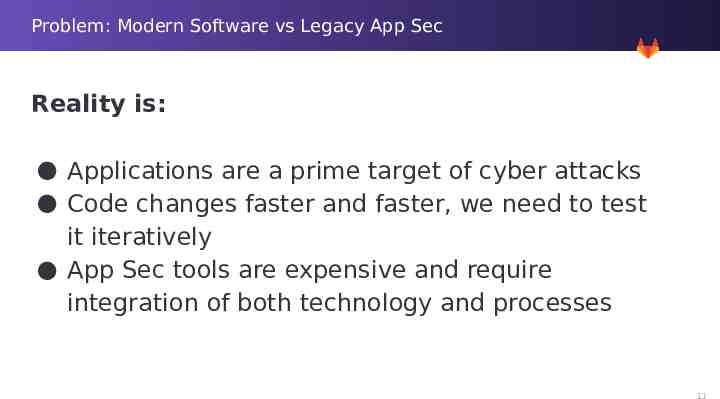
Problem: Modern Software vs Legacy App Sec Reality is: Applications are a prime target of cyber attacks Code changes faster and faster, we need to test it iteratively App Sec tools are expensive and require integration of both technology and processes 11

Problem: Rapid Iteration Iterative development is incongruent with “test everything” security flows 12

Collaboration: Security and developer teams still fail to communicate Security and developer teams still fail to communicate 13
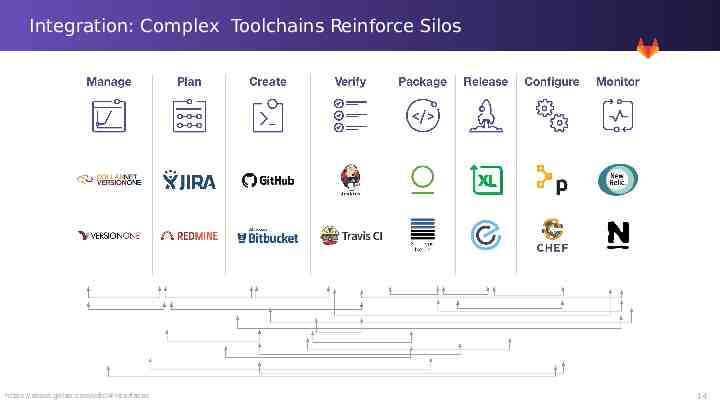
Integration: Complex Toolchains Reinforce Silos https://about.gitlab.com/sdlc/#interfaces 14
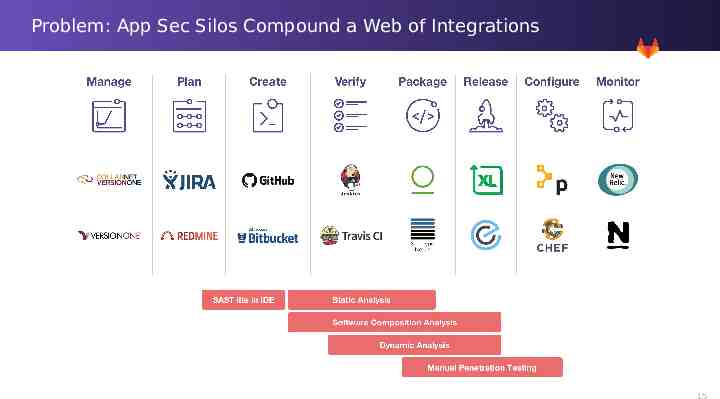
Problem: App Sec Silos Compound a Web of Integrations 15
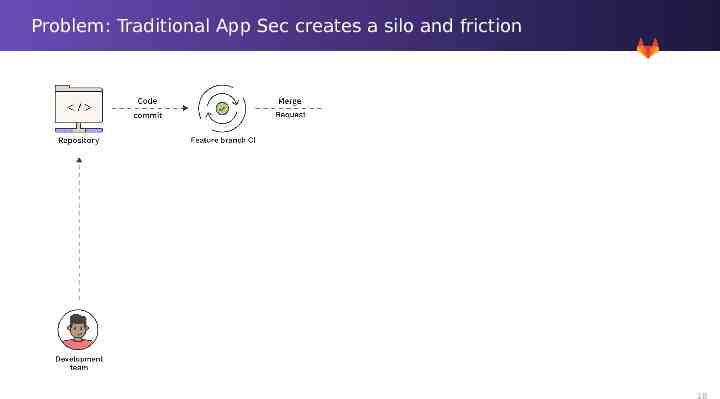
Problem: Traditional App Sec creates a silo and friction 16
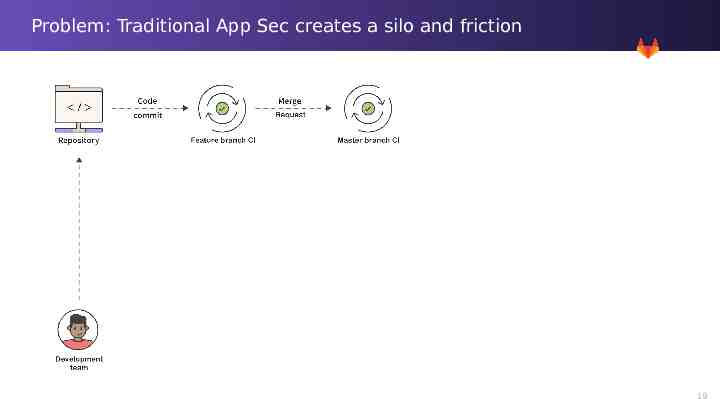
Problem: Traditional App Sec creates a silo and friction 17
Problem: Traditional App Sec creates a silo and friction 18
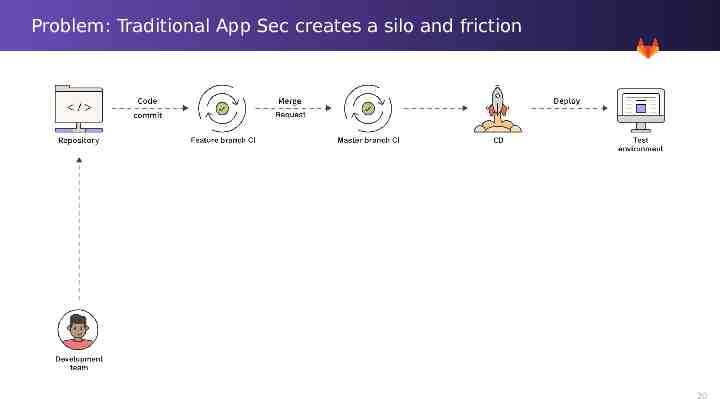
Problem: Traditional App Sec creates a silo and friction 19
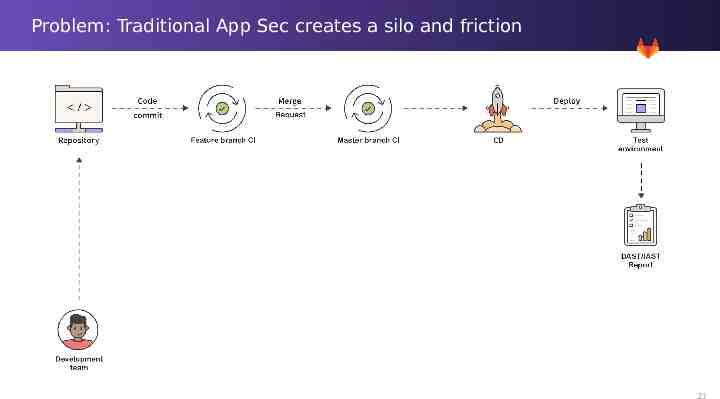
Problem: Traditional App Sec creates a silo and friction 20
Problem: Traditional App Sec creates a silo and friction 21
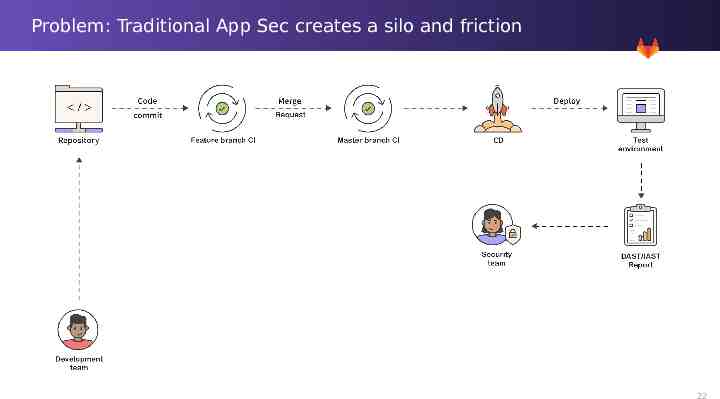
Problem: Traditional App Sec creates a silo and friction 22
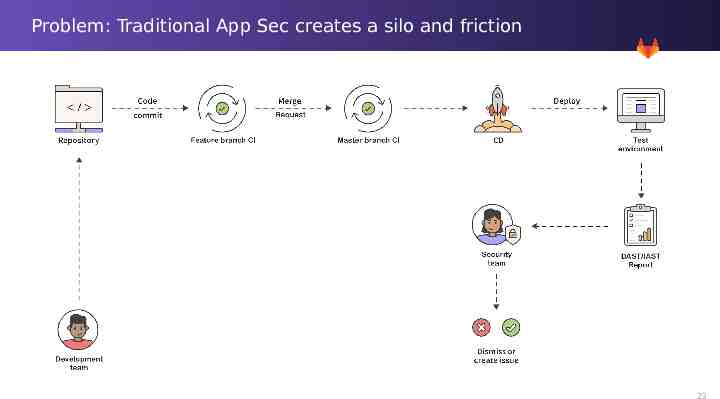
Problem: Traditional App Sec creates a silo and friction 23
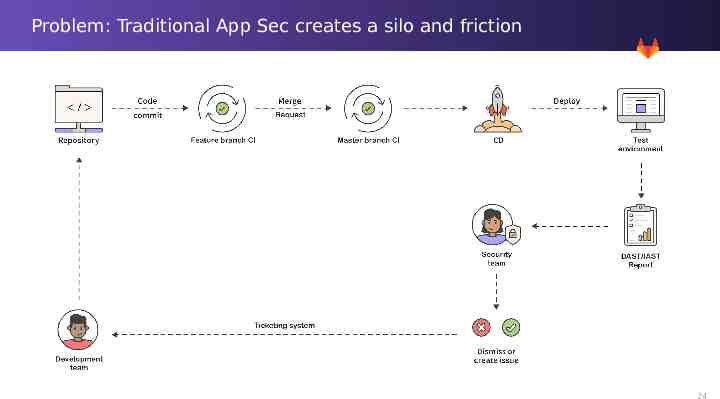
Problem: Traditional App Sec creates a silo and friction 24
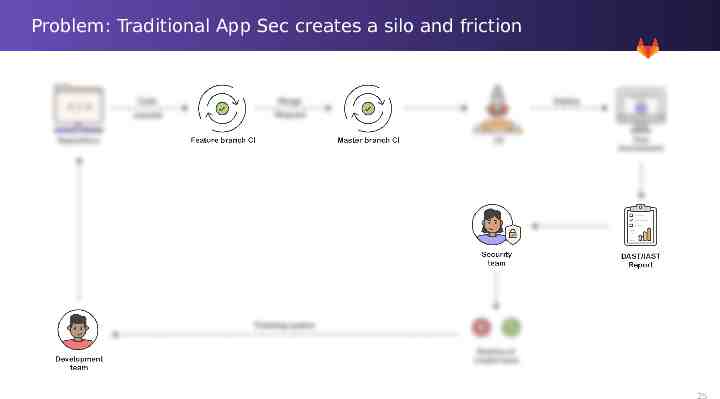
Problem: Traditional App Sec creates a silo and friction 25
Problem - Security and developer teams still fail to communicate “Despite the enterprise benefits of adopting a DevOps culture, the majority of IT leaders polled believe communication between IT security and software development teams must improve greatly to achieve success.” “Part of the challenge is believed to be — despite enthusiasm for DevOps, which has seen 81% of organisations already implement or currently work on projects — nearly half of respondents (46%) have only partially developed their DevOps strategy. IT leaders polled confirmed that enhancing IT security is more of a priority (46%) in DevOps than any other factor.” Source: Devops Online survey results from Trend Micro 2019 https://www.devopsonline.co.uk/security-and-developer-teams-still-failing-to-communicate-says-report/ 26

Solving the bigger problem 27

Shifting further left Workflows must target both teams (because shift left is a fundamental shift for companies) Security must be empowering, not blocking Dev must be engaged in security 28

Shifting further left - Workflows must target both teams Workflows must target both teams because shift left is a fundamental shift for companies; Proactive security: Security vulnerabilities reported directly to accountable developers Security teams do less tracking and triage and focus their skills. Minimal context switching for embraceable workflow. Ability to test every code change. 29

Shifting further left - Empowering security paradigm Increase Awareness Support decision makers, not replace them Augment, dont block 30
Shifting further left - Developer engagement in security Avoid warning fatigue Shift both when scans occur and who performs them The way we achieve this is by running our security scans before merge 31
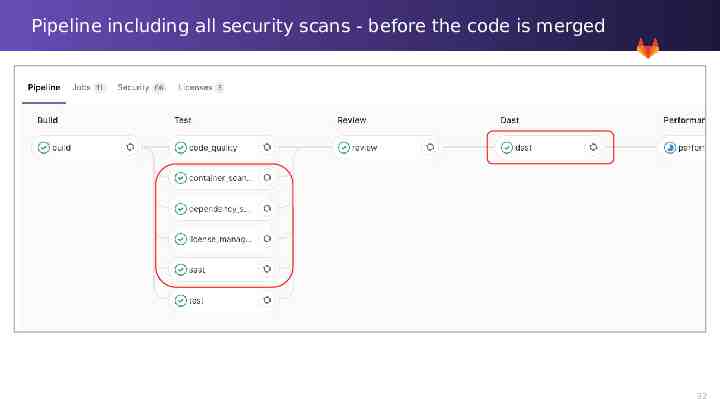
Pipeline including all security scans - before the code is merged 32

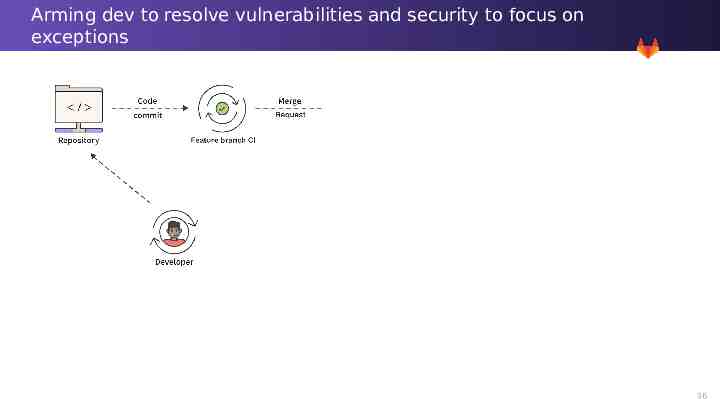
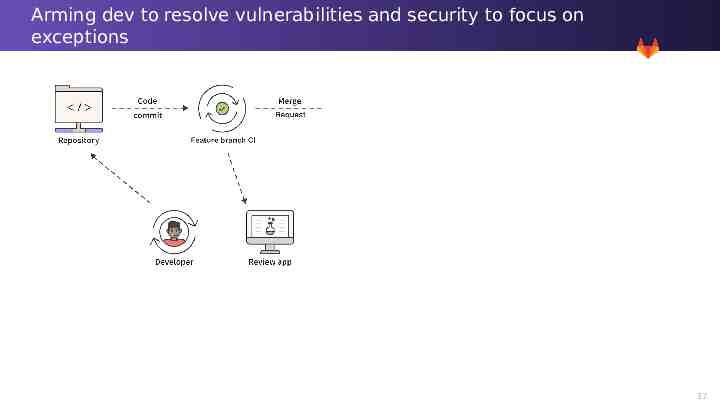
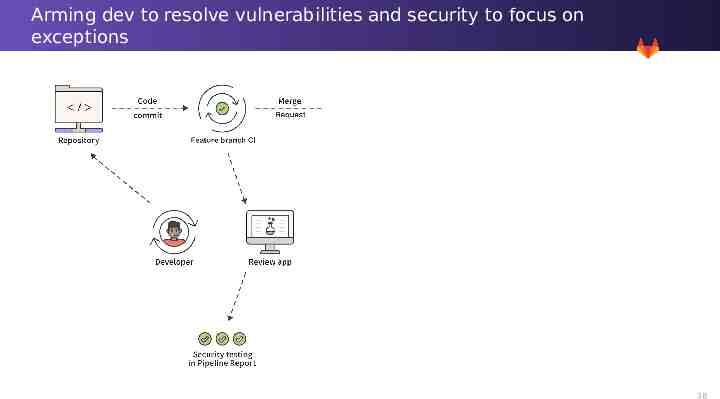
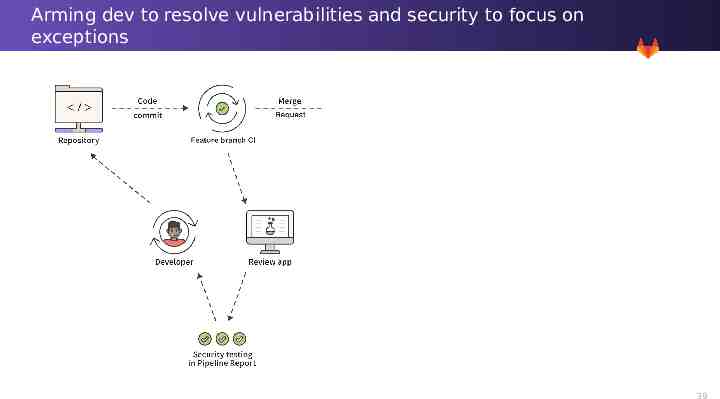
Arming dev to resolve vulnerabilities and security to focus on exceptions 33

Arming dev to resolve vulnerabilities and security to focus on exceptions 34
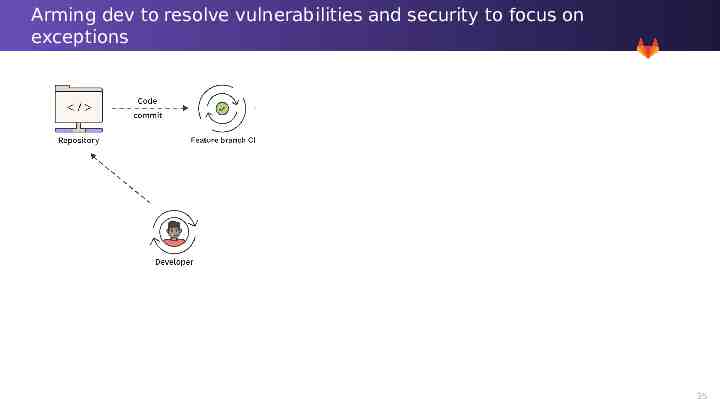
Arming dev to resolve vulnerabilities and security to focus on exceptions 35
Arming dev to resolve vulnerabilities and security to focus on exceptions 36
Arming dev to resolve vulnerabilities and security to focus on exceptions 37
Arming dev to resolve vulnerabilities and security to focus on exceptions 38
Arming dev to resolve vulnerabilities and security to focus on exceptions 39
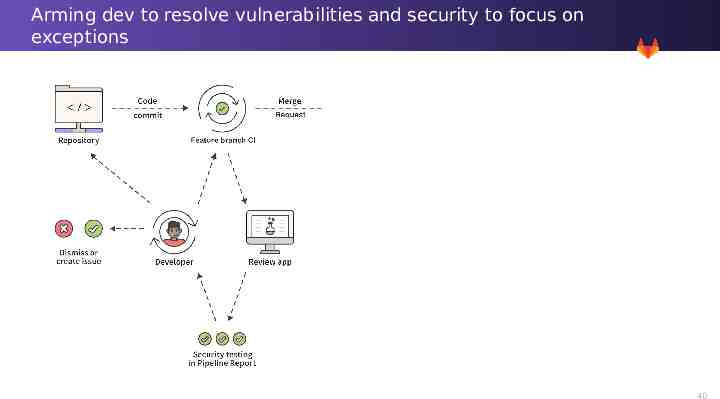
Arming dev to resolve vulnerabilities and security to focus on exceptions 40
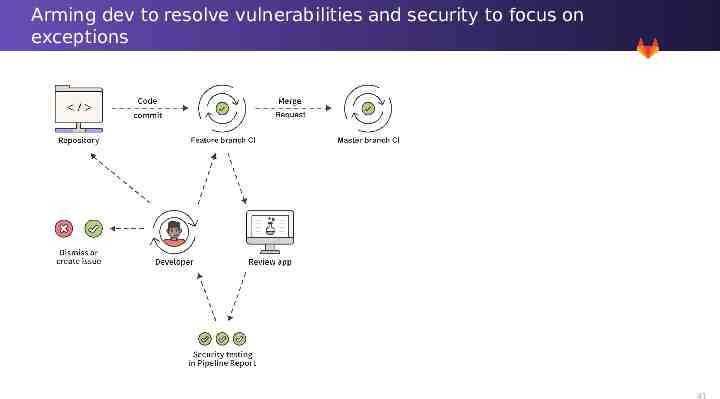
Arming dev to resolve vulnerabilities and security to focus on exceptions 41
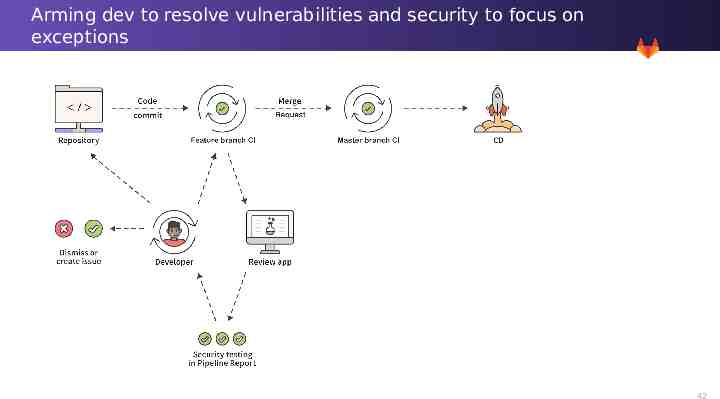
Arming dev to resolve vulnerabilities and security to focus on exceptions 42
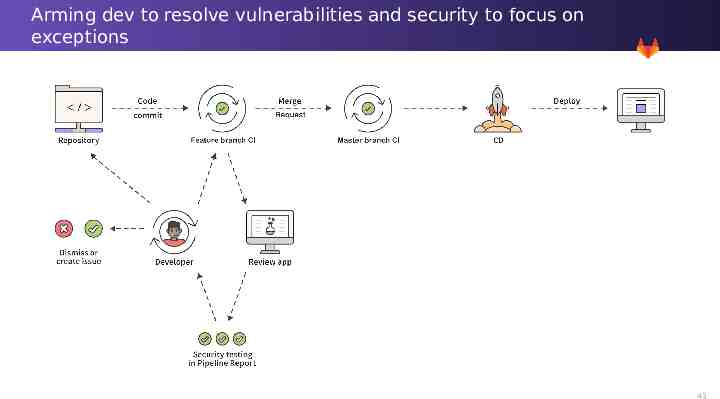
Arming dev to resolve vulnerabilities and security to focus on exceptions 43
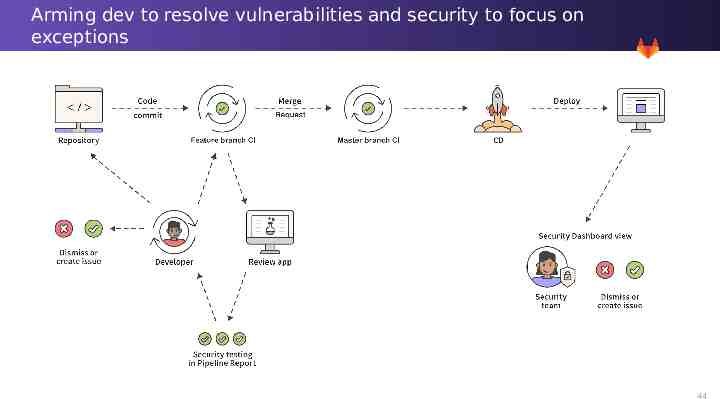
Arming dev to resolve vulnerabilities and security to focus on exceptions 44
Arming dev to resolve vulnerabilities and security to focus on exceptions 45
Advantage of this approach Contextual 46

Advantage of this approach Contextual Congruent with DevOps processes 47

Advantage of this approach Contextual Congruent with DevOps processes Integrated with DevOps tools 48

Advantage of this approach Contextual Congruent with DevOps processes Integrated with DevOps tools Efficient and automated 49

Security as an Outcome not a Department “Your most important security product won’t be a security product .” CISO of VMWare 50

Where can we go from here? 51
Tightening the feedback loop Security Approvals in Merge Requests: https://gitlab.com/gitlab-org/gitlab-ee/issues/9928 Show on dashboard when security tests are not ran: https://gitlab.com/gitlab-org/gitlab-ee/issues/7521 Forbid remote push if commit contains secrets: https://gitlab.com/gitlab-org/gitlab-ee/issues/8792 https://gitlab.com/groups/gitlab-org/-/epics/634 52
Roadmap https://about.gitlab.com/direction/secure/#upcoming-releases 53

Thank You Lucas Charles @theoretick - [email protected] Slides: http://bit.ly/OSCONSecWorkflow Whitepaper: http://bit.ly/OSCONSecWorkflowWhitepaper 54
Rate today ’s session Session page on conference website O’Reilly Events App