Illinois Municipal Treasurer’s Association PCI Compliance
14 Slides618.28 KB

Illinois Municipal Treasurer’s Association PCI Compliance – Best Practices June 2021 NCR Confidential

Agenda Introductions PCI Partner PCI Compliance Program Continuous Monitoring Employee Training Payment Methods Key Practice Points Tools and References

Introductions Frank Napolitano, PMP, PMI-ASP, CSM, Government Relationship Manager Alok Kumar, M.Sc., MBA, CISSP, CEH - Retail and Payments CISO Dr. John Reynolds, D.Sc. Cybersecurity, CISSP – Sr Security Architect About NCR, for over 135 years NCR has been a leader in cashiering and point of sale systems. NCR is a payment processor serving government agencies across the country including municipalities, counties and state agencies. NCR is proud to serve the City of Springfield and many other clients through the Illinois ePAY program. NCR is certified as a PCI Level 1 Service Provider.

PCI Partner The Qualified Security Assessor (QSA) is a data security firm that is qualified by the PCI Council to perform on-site PCI Data Security Standard assessments. They are your Trusted Advisor! For the PCI-DSS Audit The Assessor will: 4 Verify all technical information given by merchant or service provider Use independent judgment to confirm the standard has been met Provide support and guidance during the compliance process Be onsite for the duration of the assessment as required Adhere to the PCI Data Security Standard Assessment Procedures Validate the scope of the assessment Evaluate compensating controls Produce the final Report on Compliance NCR Confidential

PCI Compliance Program Does IMTA follow NIST RMF Information Security Program guidelines? SP800-37, 39, 53, 53A, 18, 137A (Continuous Monitoring) Card Brands - Specific questions about compliance validation levels and what you must do to validate should be directed to your acquiring financial institution or payment card brand. – See references Implementing the PCI Data Security Standard starts with scoping. This process involves identifying all system components that are located within or connected to the cardholder data environment (such an environment is comprised of people, processes, and technology that handle cardholder data or sensitive authentication data). Scoping is an annual process and must occur prior to the annual assessment. Merchants and other entities must identify all locations and flows of cardholder data to ensure all applicable system components are included in scope for the PCI Data Security Standard. 5 NCR Confidential
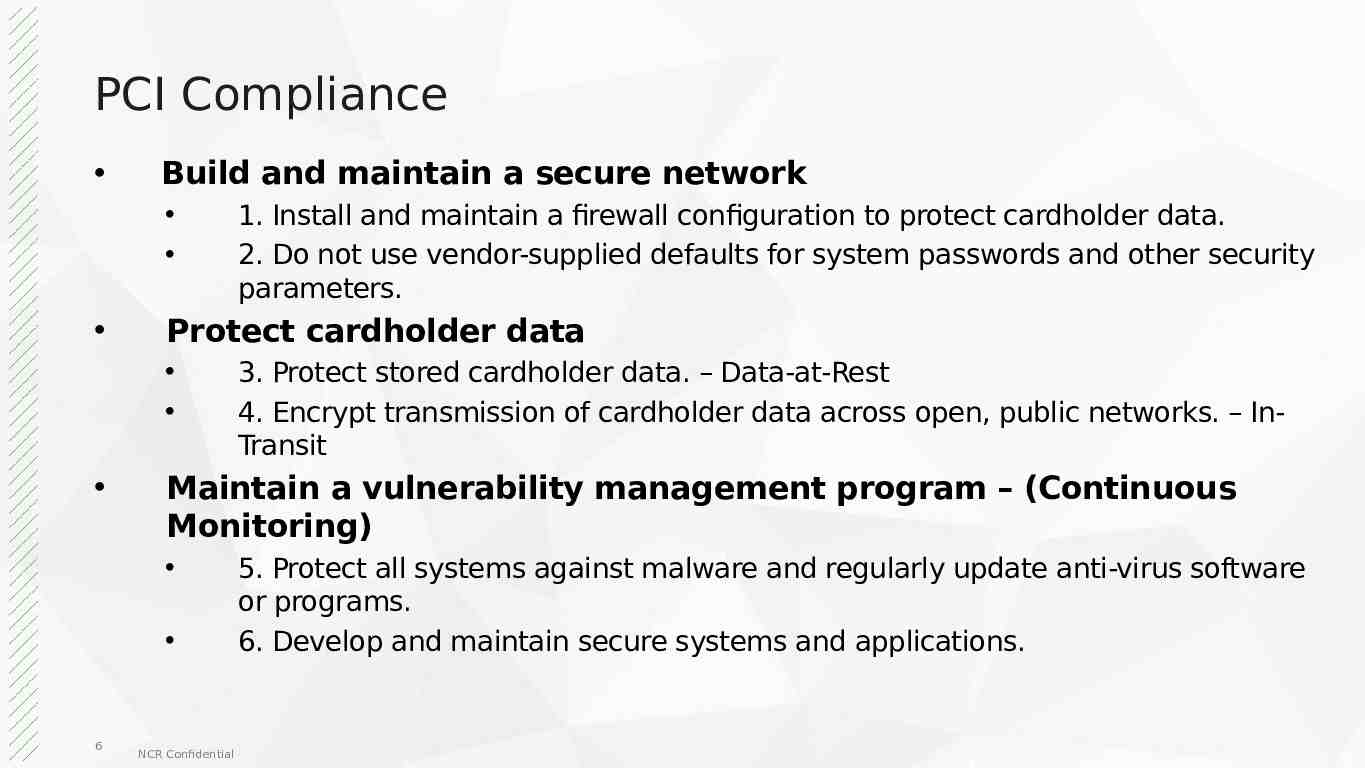
PCI Compliance Build and maintain a secure network Protect cardholder data 3. Protect stored cardholder data. – Data-at-Rest 4. Encrypt transmission of cardholder data across open, public networks. – InTransit Maintain a vulnerability management program – (Continuous Monitoring) 6 1. Install and maintain a firewall configuration to protect cardholder data. 2. Do not use vendor-supplied defaults for system passwords and other security parameters. NCR Confidential 5. Protect all systems against malware and regularly update anti-virus software or programs. 6. Develop and maintain secure systems and applications.
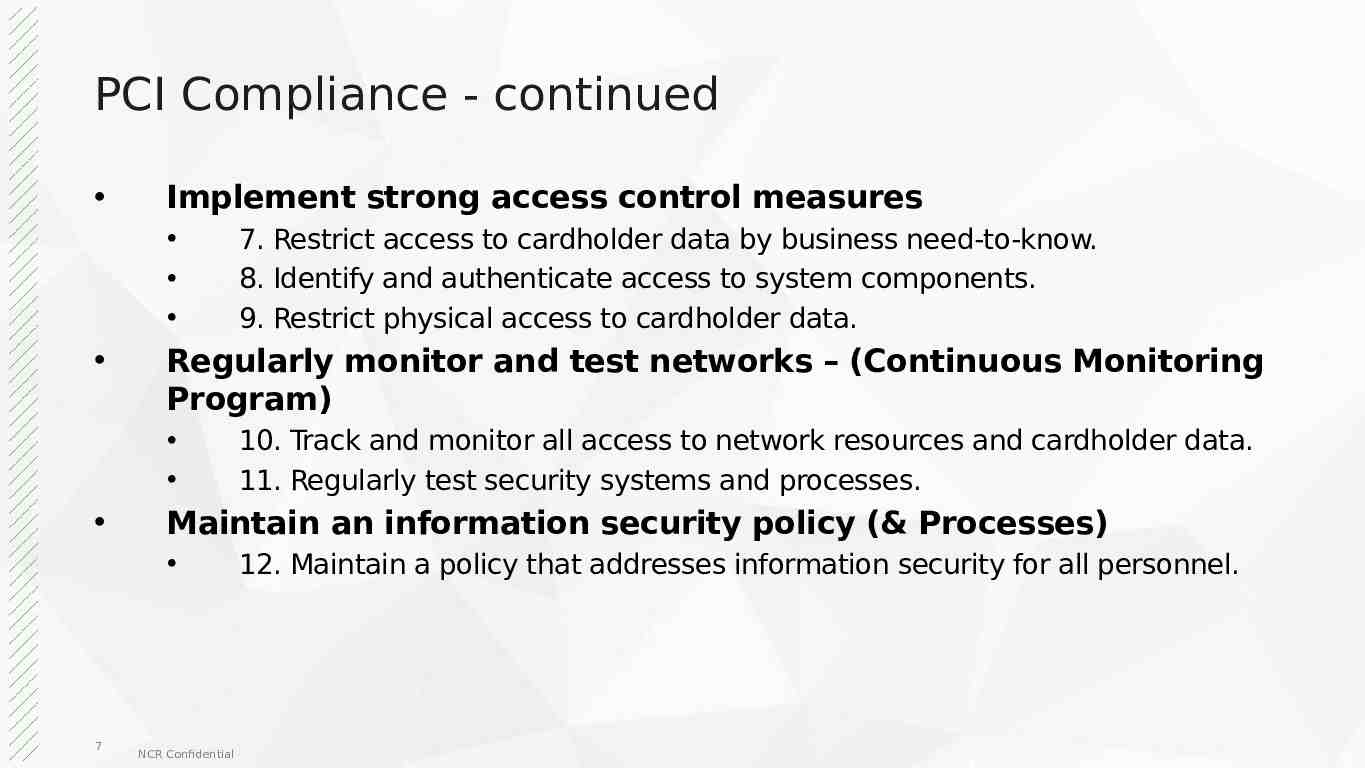
PCI Compliance - continued Implement strong access control measures Regularly monitor and test networks – (Continuous Monitoring Program) 10. Track and monitor all access to network resources and cardholder data. 11. Regularly test security systems and processes. Maintain an information security policy (& Processes) 7 7. Restrict access to cardholder data by business need-to-know. 8. Identify and authenticate access to system components. 9. Restrict physical access to cardholder data. NCR Confidential 12. Maintain a policy that addresses information security for all personnel.
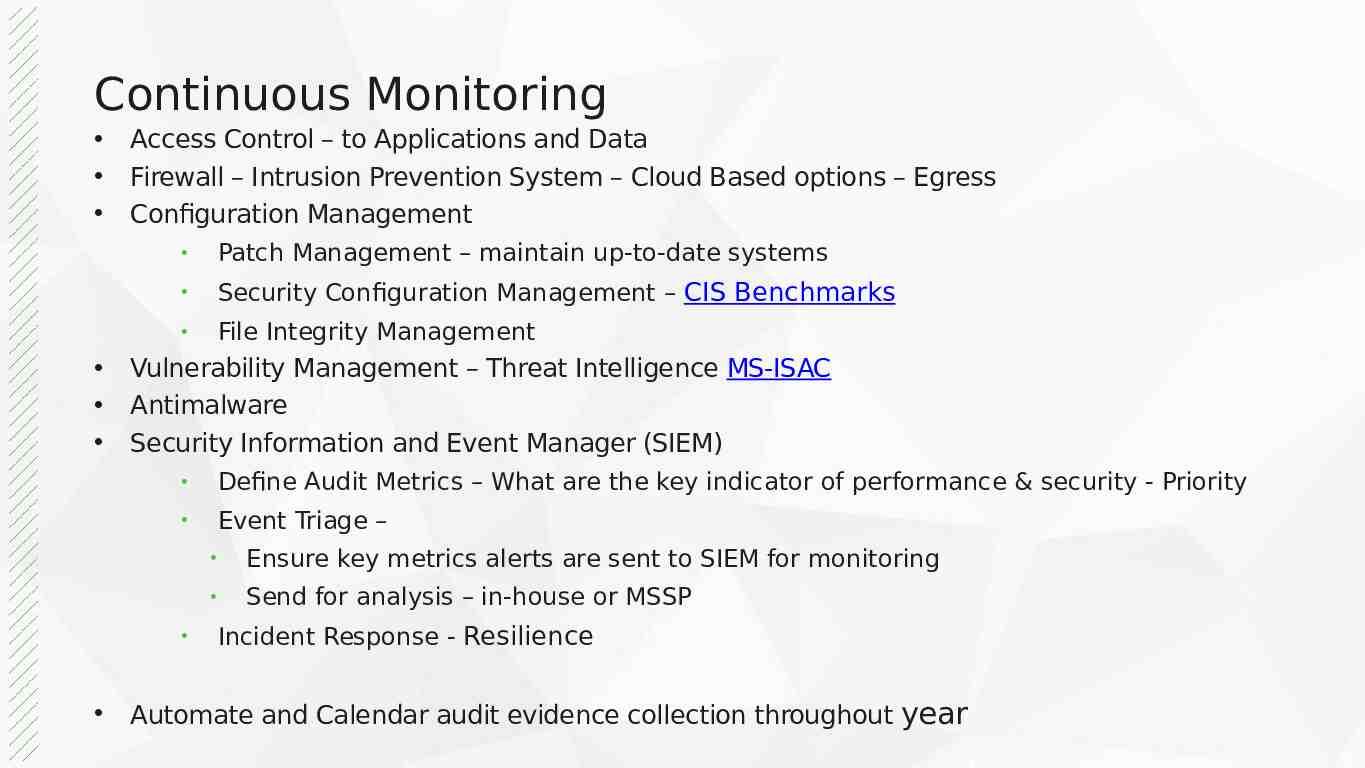
Continuous Monitoring Access Control – to Applications and Data Firewall – Intrusion Prevention System – Cloud Based options – Egress Configuration Management Patch Management – maintain up-to-date systems Security Configuration Management – CIS Benchmarks File Integrity Management Vulnerability Management – Threat Intelligence MS-ISAC Antimalware Security Information and Event Manager (SIEM) Define Audit Metrics – What are the key indicator of performance & security - Priority Event Triage – Ensure key metrics alerts are sent to SIEM for monitoring Send for analysis – in-house or MSSP Incident Response - Resilience Automate and Calendar audit evidence collection throughout year

Employee Training The Secret Key to Success Annual Security Awareness Training NCR Confidential At least a monthly touchpoint – Email Blast, Fun Team Building Gathering, Industry Organization Webinar Annual Role-based Training 9 Everyone’s Awareness and Due Care practice Specialized focus on each Role involved with CHD

Payment Methods Point of Sale (POS), In Person - Card Present Devices should face payer, payer should be in control of their card Web Payments, Online & Auto Pay Telephone Payment, made over phone to a live agent Higher Risk, should be avoided Interactive Voice Response (IVR), Pay by Phone 1 0 Should not store full payment card details – Encryption/tokenization/obfuscation NCR Confidential Similar to a telephone payment, but employees do not receive payment card details

Key Payments Practice Points Employees should not handle or have direct access to payment card details, such as full card numbers, CVV numbers or PIN Numbers Credit Card numbers must be masked. The maximum number of digits that can be displayed or stored are the first six and last four digits of the card Any stored payment information should be encrypted/tokenized/obfuscated 1 1 Credit Card Point of Sale (POS) devices should be customer facing Best practice is establishing a trusted relationship with your payment processor to securely process and store consumer payments data. ITMA maintains Transaction Number to reduce attack surface NCR Confidential
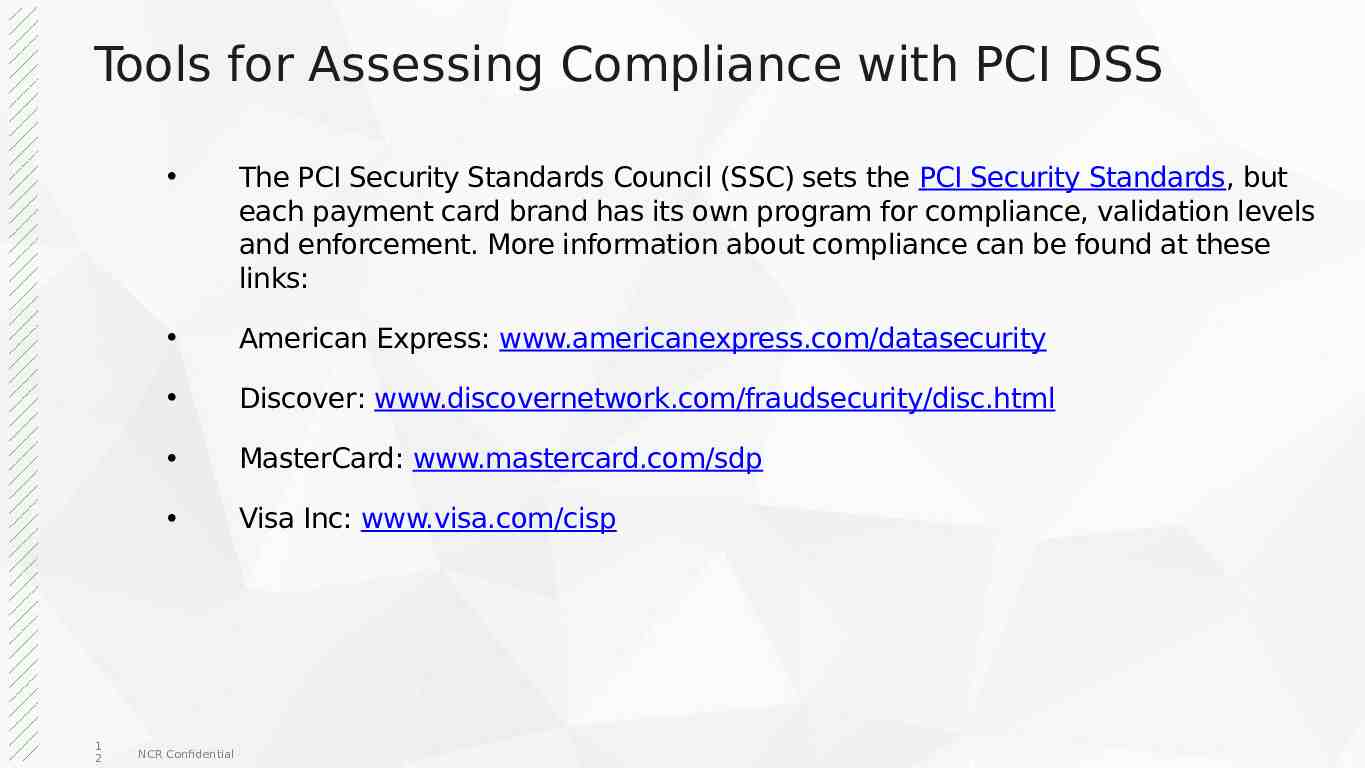
Tools for Assessing Compliance with PCI DSS 1 2 The PCI Security Standards Council (SSC) sets the PCI Security Standards, but each payment card brand has its own program for compliance, validation levels and enforcement. More information about compliance can be found at these links: American Express: www.americanexpress.com/datasecurity Discover: www.discovernetwork.com/fraudsecurity/disc.html MasterCard: www.mastercard.com/sdp Visa Inc: www.visa.com/cisp NCR Confidential
Merchant References 1 3 https://www.pcisecuritystandards.org/merchants/ https://www.mastercard.us/en-us/business/overview/safety-and-security/security-recommendations/site-data-prot ection-PCI/merchants-need-to-know.html PCI Compliance Keeping Customer Data Safe Visa - Verify your Compliance Validation Level Official PCI Security Standards Council Site - Verify PCI Compliance, Download Data Security and Credit Card Secur ity Standards Small Merchant Guide to Safe Payments.pdf (pcisecuritystandards.org) - Contains good baseline information, terminology definitions and tips https://www.pcisecuritystandards.org/document library https://www.mastercard.us/en-us/business/overview/safety-and-security/security-recommendations/site-data-prot ection-PCI/merchants-need-to-know.html https://www.cisecurity.org/cis-benchmarks/ NCR Confidential

THANK YOU 1 4 NCR Confidential






