Homeland Security: The Past, Present, and Future Trends Young B.
61 Slides2.44 MB

Homeland Security: The Past, Present, and Future Trends Young B. Choi Dept. of CIS & MS James Madison University 1
Homeland Security 2

Agenda Introduction Homeland Security History of Homeland Security Major Players JMU IIIA and GMU CIPP – James Madison University IIIA – George Mason University CIPP Major Research Areas of Homeland Security Information Analysis Homeland Security Related Resources Funding Sources for Homeland Security Research Conclusions References 3

Homeland Security: The Past, Present, and Future Trends Abstract This presentation reviews the past, present, and future trends of Homeland Security. The research activities of relevant research organizations including the IIIA (Institute for Infrastructure and Information Assurance) of James Madison University and the CIPP (Critical Infrastructure Protection Program) of George Mason University are introduced. The annual Homeland Security Symposium and current technical trends based on the analysis of presented research papers will be identified. Outstanding and emerging research issues of Homeland Security will be proposed and discussed. 4

Introduction Homeland Security Poster This is a great conversation piece. Black and white and photos of Red Dog, Little Dog, Little Wound, Red Cloud and American Horse and in back John Bridgeman Dated 1880. Price: 3.50 5

Homeland Security Definition: Wikipedia – The term homeland security refers to the broad national effort by all levels of government to protect its territory from hazards, both internal and external, natural and man-made. The term is most often used in the United States; elsewhere, national security has more usage. The term is also used to refer to the United States Department of Homeland Security itself [1]. 6

History of Homeland Security 1st Century – The Sicarii Zealots; Assasins; Herod the Great 5th Century – Attila The Hun 1095-1099 – First Crusade 13th Century – Ghengis Khan 15th Century – Torquemoda 1793-1794 – Reign of Terror 1972 – The Munich Massacre 2001 – 9/11 (September 11 Attacks) 7
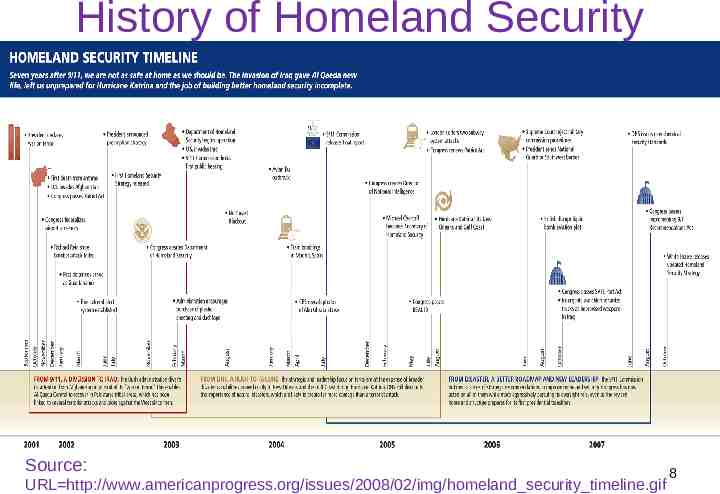
History of Homeland Security Source: URL http://www.americanprogress.org/issues/2008/02/img/homeland security timeline.gif 8

Major Players Federal Agencies Universities State and Local Agencies Industry Military 9

Federal Agencies Federal Agencies – U.S Department of Homeland Security A government agency created in 2003 to handle immigration and other security-related matters. http://www.dhs.gov – The Federal Facilities Council (FFC) Established in 1953 as the Federal Construction Council. It operates under the auspices of the Board on Infrastructure and the Constructed Environment (BICE) of the National Research Council, the principal operating agency of the National Academies and the National Academy of Engineering. Mission – Identify and advance technologies, processes, and management practices that improve the performance of federal facilities over their entire life-cycle, from planning to disposal. http://www7.nationalacademies.org/ffc/ 10

Federal Agencies: DHS Homeland Security Act of 2002 – November 25, 2002 – Officially created by the Homeland Security Act of 2002, this mega agency is charged with preventing and deterring terrorist attacks and protecting against and responding to threats and hazards to the nation. The DHS – Mission: We will lead the unified national effort to secure America. We will prevent and deter terrorist attacks and protect against and respond to threats and hazards to the nation. We will ensure safe and secure borders, welcome lawful immigrations and visitors, and promote the free-flow of commerce. 11

Federal Agencies: DHS Directorates of the Department of Homeland Security – Border and Transportation Security (BTS) – Emergency Preparedness and Response – Science and Technology – Information Assurance and Infrastructure Protection 12
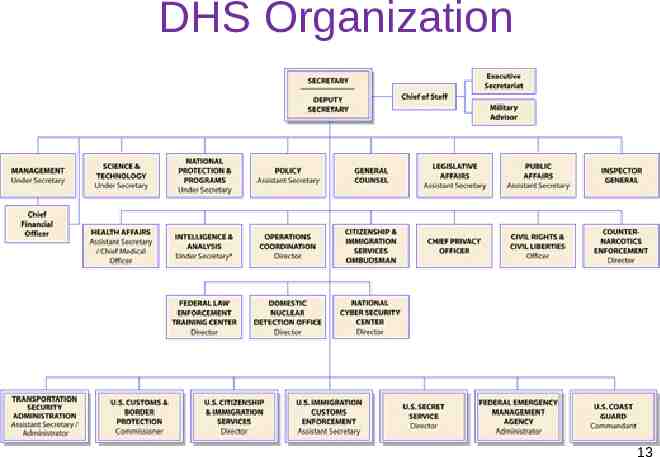
DHS Organization 13

Military Military – Air Force Intelligence – Army Intelligence – Marine Corps Intelligence – Navy Intelligence Center for Contemporary Conflict http://www.ccc.nps.navy.mil/rsepResources/homel and.asp#journals – Coast Guard Intelligence 14

JMU IIIA and GMU CIPP Universities – James Madison University IIIA – George Mason University CIPP – “Centers of Excellence” Program University of Southern California (Nov. 2003) Texas A&M University (Apr. 2004) University of Minnesota (Apr. 2004) University of Maryland (Jan. 2005) Johns Hopkins University (Dec. 2005) 15

Universities – DHS Scholars and Fellows Program Disaster Mitigation Emergency Response Prevention through the Use of Technology 16

Mission and Vision – A leader in Computer Security – One of the original seven Centers of Academic Excellence for Information Security Education by the National Security – In 2001, successfully competed for a grant through the Commonwealth Technology Research Fund to establish the Commonwealth Information Security – The Mission Facilitate development, coordination, integration and funding of activities and capabilities of James Madison University to enhance information and critical infrastructure assurance at the federal, state and local levels. – The Vision A society strengthened and enriched by increasingly dependable infrastructures fostered by a strong university role in leadership, interdisciplinary education, research and problem-solving . 17
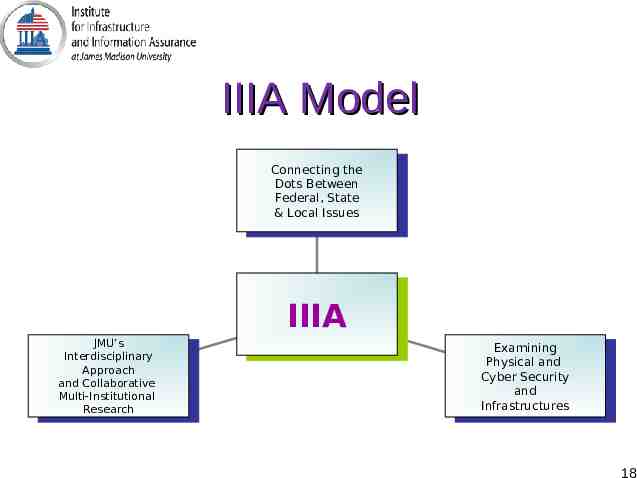
IIIA Model Connecting the Connecting the Dots Between Dots Between Federal, State Federal, State && Local Issues Local Issues JMU’s JMU’s Interdisciplinary Interdisciplinary Approach Approach and Collaborative and Collaborative Multi-Institutional Multi-Institutional Research Research IIIA IIIA Examining Examining Physical and Physical and Cyber Security Cyber Security and and Infrastructures Infrastructures 18
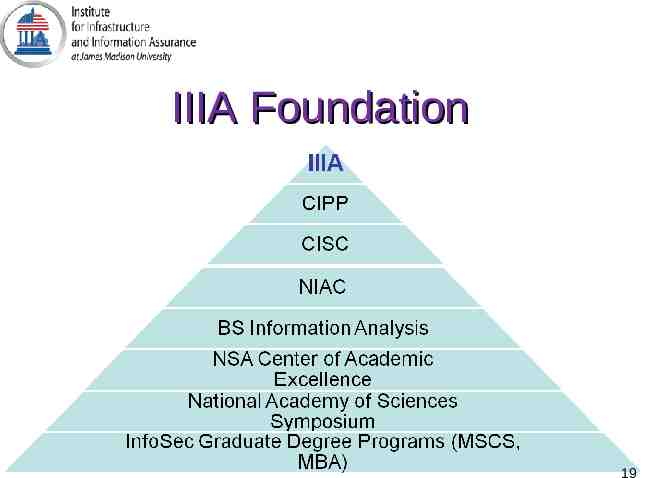
IIIA Foundation 19

Strategic Attributes Emphasize applied research Provide services to faculty for proposal and project development Coordinate student-facultystaff research teams Enlist interdisciplinary, product- driven approach and agile organization Implement strategic alliances quickly Connect physical and cyber security and assurance Develop software Simulate and test networks Produce quality, deliverablebased grant and contract products on time Perform community service Maintain and expand outstanding political support and linkages Advance curriculum development Develop risk assessment tools Leverage longstanding degree programs 20

Strategic Alliances – Private and Non-Profit 21

Strategic Alliances – Education and Government 22

Critical Infrastructure Protection Project Core Research Areas Health Infrastructure Avian Flu Pandemic Disaster Preparedness and Response Modeling, Simulation & Visualization Information Analysis Education Community Resilience Alternative Energy Green IT 23
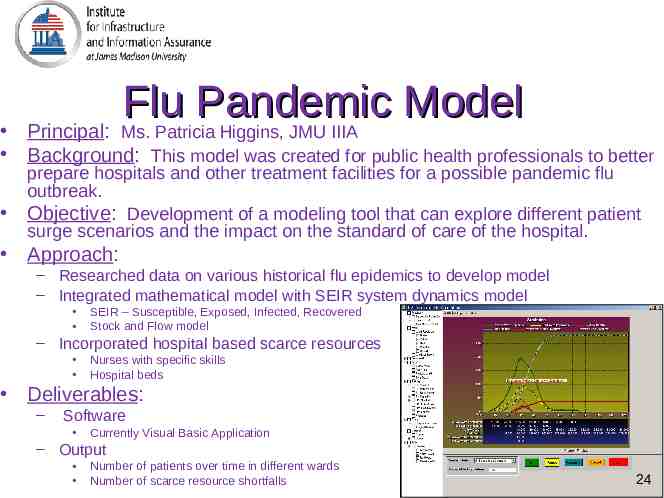
Flu Pandemic Model Principal: Ms. Patricia Higgins, JMU IIIA Background: This model was created for public health professionals to better prepare hospitals and other treatment facilities for a possible pandemic flu outbreak. Objective: Development of a modeling tool that can explore different patient surge scenarios and the impact on the standard of care of the hospital. Approach: – Researched data on various historical flu epidemics to develop model – Integrated mathematical model with SEIR system dynamics model SEIR – Susceptible, Exposed, Infected, Recovered Stock and Flow model – Incorporated hospital based scarce resources Nurses with specific skills Hospital beds Deliverables: – Software Currently Visual Basic Application – Output Number of patients over time in different wards Number of scarce resource shortfalls 24

BS Information Analysis Department: Integrated Science and Technology Program Scope: Prepares graduates to apply the principles of information analysis, synthesis and data mining to problems in national, international or business intelligence settings. Knowledge & Skills: – Identify, formulate, analyze and solve complex, real-world problems – Access and critically analyze data from multiple sources – Use computer-based and mathematical tools to effectively analyze and display information Three-tiered Approach: – Social/Political/Cultural Understanding – Advanced Critical Thinking – Tools and Technology Concentrations: – National Security – Competitive Analysis Carrier Library 25

2008 - Newly Funded Research WMD Training for Community Emergency Responders – Dr. Ronald Raab, JMU/ISAT Engineering Development of RFID Disaster Bracelet System – Dr. Anthony Teate, JMU/ISAT Hosting a Cyber Defense Competition – Drs. Brett Tjaden and Houssain Heydari, JMU/CS Computerized Constructive Cartography and Communication Center for Pandemic Prediction and Response – Dr. Lincoln Gray, JMU/HHS Improving the Efficiency of Energy End-Use – Dr. Tony Chen, JMU/ISAT 26

WMD Training for Community Emergency Responders Principal: Dr. Ronald Raab, JMU Integrated Science and Technology Background: Weapons of Mass Destruction (WMD) Standardized Awareness Training (AWR-160) is a FEMA/DHS course that standardizes the minimum WMD awareness level learning objectives that shall be included in all federal, state and local jurisdictions. Objective: This course establishes a common baseline to ensure nationwide consistency in WMD education and training for first responders. Approach: The course will be taught to all fire and rescue personnel in the city of Harrisonburg and the county of Rockingham. Delivery of the course for the city of Harrisonburg will be done for each of the three shifts, which consists of 4 engine companies and one truck company. Deliverables: – Training for 11 companies with 3 shifts with a total of 70 personnel 27

RFID Hurricane Bracelet System Development Principal: Dr. Anthony A. Teate, JMU Integrated Science and Technology Background: According to FEMA, Hurricane Katrina displaced more than 330,000 families. Of these, over 182,000 victims moved into shelters across more than 20 states. Many of these individuals experienced considerable delays in ability to contact/reunite with their family members. Objective: Research and final prototype development of Radio Frequency Identification (RFID) bracelet and tracking system with application to locating large numbers of individuals after a natural disaster. Approach: – Develop and test “Missing Persons” aspect of DIBS software – Develop and test an interface with a secure login that allows authorities to locate a person’s identification data – Create a secure web-based application which allows family members to retrieve one another’s contact information Deliverables: – Proposal in response to SBIR opportunities – Seek early stage investment from Angel Investors 28

Hosting a Cyber Defense Competition Principals: Dr. Brett Tjaden, Dr. Houssain Heydari, JMU Computer Science Background: Cyber Defense competitions are important and challenging opportunities for participants to test their information security knowledge and skills in a realistic environment. JMU has participated in the Collegiate Cyber Defense Competition last year and plans to participate in the next competition. We would benefit from hosting a cyber-defense competition at JMU. Objective: To develop the capability and host a Cyber Defense Competition at JMU in Fall 2008. Approach: – – – – Develop a team packet of relevant rules, guidelines, and schedule Build the contest scenario Acquire and configure network and virtual machines Prepare participating faculty and students to participate and administer the competition Deliverables: – Actual cyber defense competition for JMU students, prospective students, and possibly local or regional businesses – Lessons learned from competition 29
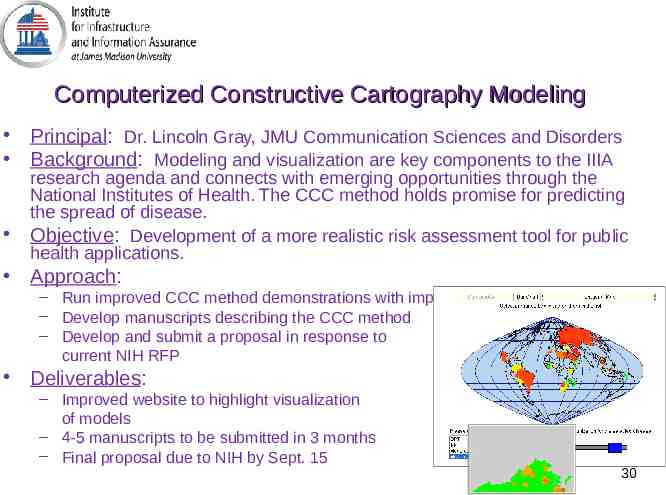
Computerized Constructive Cartography Modeling Principal: Dr. Lincoln Gray, JMU Communication Sciences and Disorders Background: Modeling and visualization are key components to the IIIA research agenda and connects with emerging opportunities through the National Institutes of Health. The CCC method holds promise for predicting the spread of disease. Objective: Development of a more realistic risk assessment tool for public health applications. Approach: – Run improved CCC method demonstrations with improved visualizations – Develop manuscripts describing the CCC method – Develop and submit a proposal in response to current NIH RFP Deliverables: – Improved website to highlight visualization of models – 4-5 manuscripts to be submitted in 3 months – Final proposal due to NIH by Sept. 15 30

Efficient End-Use for Energy Principal: Dr. Tony Chen, JMU Integrated Science and Technology Background: – America’s security is threatened by dependence on foreign oil and fragile infrastructure (i.e. Trans-Alaska Pipeline System). – Most cost-effective option to replace imported fossil fuels is to use less energy – Latest efficient technologies estimated to save U.S. 300 billion/year overall Objectives: – Assessment of the current status of customer implementation of energy monitoring systems – Evaluation of their effect on end-user behavior in conserving energy Approach: – Monitor, collect and analyze data from all participants in a local power company’s Demand Response and Green Power Rate Programs – Students will work with Dominion Virginia Power company to assess and implement these two programs in the Central Shenandoah Valley Deliverables: – Monthly progress reports – Final report on research results 31

2008 Symposium Partner: National Academy of Sciences Theme: To foster the development of public-private partnerships, IIIA’s 3rd annual homeland security research symposium illuminated successful collaboration between industry and government at the local, regional and national levels. Keynote Speakers: – Congressman Dutch Ruppersberger, MD-2 Win the satellite war in space Cyber security a top priority – Assistant Secretary of the Private Sector Office for DHS, Alfonso Martinez-Fonts Vice Provost John Noftsinger with IIIA Fellow Dennis Barlow Public-private collaboration invested 5 million for more than a 2.5 billion return on investment to improve transportation of consumer goods from Canada to U.S. through Detroit. 32

Homeland Security Textbook Understanding Homeland Security: Policy, Perspectives, and Paradoxes Dr. John B. Noftsinger, Kenneth F. Newbold, Jack Wheeler [2] Comprehensive exploration of the history of terrorism, the Department of Homeland Security, public policy issues, information analysis, critical infrastructure protection, risk communication, border & transportation security, and future trends. May 2007 33

Overview One of the first texts analyzing the historical, social, psychological, technological, and political aspects that form the broad arena of homeland defense and security. Foreword: Sec. John O. Marsh, Jr. Publication: May 2007 Publisher: Palgrave Macmillan Pages: 232 34

Table of Contents The Nature of the Threat (Historical Underpinnings) What is Homeland Security? Public Policy Issues (Security vs. Privacy) Information/Intelligence Analysis Critical Infrastructure Protection and Information Security Risk Communication, Psychological Management, and Disaster Preparedness Transportation and Border Security Issues Future Implications: Imagination, Integration, and Improvisation 35

About the Book Each chapter begins with a hypothetical “Table Top Scenario” Chapters conclude with a “Case Study”-examination of issues discussed within the text Provides a new expanded definition of terrorism Areas of Emphasis – – – – – – – Bureaucratic and legislative initiatives Critical infrastructure protection Information/cyber security Public health Border and transportation security Intelligence collection and dissemination Balancing Security and Privacy Rights 36

Innovative Approach 37

Forecasting the Future Fighting the Last War Need for Education and Research Opportunities for Business Innovation: A National Imperative 38

Three “I’s” of the Future Imagination Integration Improvisation 39

Endorsements "To illuminate Homeland Security is an ambitious undertaking in a world where the topic often generates more heat than light. Through integration of governmental, business and academic perspectives, the authors succeed in providing the reader with a vital framework for understanding. I know of no other single source that provides students and policy makers with such a thorough, yet eminently readable volume." --Gregory Saathoff MD, Executive Director, Critical Incident Analysis Group (CIAG), University of Virginia School of Medicine "Finally, a comprehensive and coherent textbook for the homeland security arena. The authors have undertaken a complex subject matter and distilled it into a presentable format that will have great utility from the classroom to the boardroom. The balancing and integration of subjects that impact public and private sector organizations as well as academia provide the instructor and student with a unique text that will also serve as a ready reference long after the class has concluded." --Paul M. Maniscalco, MPA, Gilmore National Terrorism Commission, Chairman, Threat Reassessment Panel and State and Local Response Panel 40

Customer Reviews Amazon.com Customer Reviews – 'A Fine Effort for a Little Book' This short, little paperback covers the basics, even though it uses a broadened or widened definition of terrorism (e.g., socially motivated, incites fear). Historical details are kept to a minimum. Organizational issues closely follow the governmental dictum about how homeland security ought to be organized. The tabletop exercises at the end of each chapter are good. – 'A must read for students of homeland security, concerned citizens, and policymakers.‘ "Understanding Homeland Security" is a comprehensive examination of the past, present, and future of homeland security. “Understanding Homeland Security" is well designed, very readable, and is an important read for anyone interested in homeland security. 41

George Mason University CIPP George Mason University School of Law Center for Infrastructure Protection (CIPP) Nationally and internationally recognized as a leading facilitator and provider of infrastructure protection programs that help secure and defend the United States and its allies. Mission – Integrates law, policy, and technology to conduct comprehensive infrastructure protection, resiliency, and security research relevant to U.S. and international security. – Provides critical infrastructure stakeholders with valuable analysis of the cyber, physical, human, and economic frameworks of the United States’ critical infrastructures. 42

George Mason University CIPP Core Functions of Mission Facilitate basic and applied multi-disciplinary research in critical infrastructure protection, resiliency, and security and defense issues, identifying policy and operational gaps not adequately covered elsewhere; Provide timely and focused research, analysis, recommendations, and follow-on activities; Provide a forum where stakeholders – all levels of government, industry, academia, and the private sector, both domestic and international – share insights, seek solutions to problems, interact with other experts, gain access to decision-makers, bring about corrective action, and receive recognition for their work; Convene critical communities for collective action, especially in areas where such coordination would not otherwise occur; Encourage sensible security by balancing aspects of national security, homeland defense, and disaster response with concepts of federalism, economic efficiency, globalism, and personal freedoms; Collect knowledge about CIP issues, practices, and developments that will facilitate research, policy making, and private action; Collect, integrate, and analyze knowledge about CIP in this University, among academic, public, and private-sector organizations in this Nation, and among our allies; Perform outreach activities and facilitate information exchange and outreach among stakeholders; 43

George Mason University CIPP Core Functions of Mission Present formal programs for training and education, including professional development of current and future leaders in the field; Produce research papers and periodic publications that are recognized domestically and internationally as that of an independent, credible authority; Open avenues for the development of mutually beneficial international relationships; Provide subject matter expertise and skilled, cost-effective administrative and logistical support in the development and execution of preparedness exercises and simulations; Evaluate cross-government agency activities; Using Mason’s pre-eminence in law and economics, evaluate homeland security activities from a market-economy perspective; and Stimulate innovation and invention in CIP by analyzing the issues from an independent perspective. 44
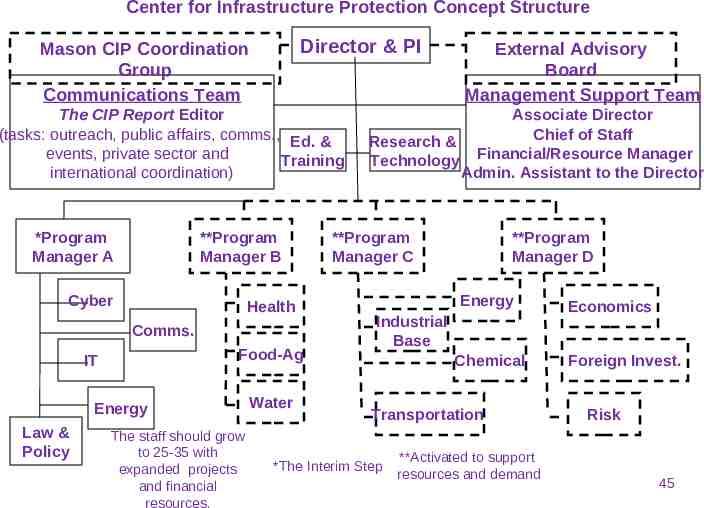
Center for Infrastructure Protection Concept Structure Director & PI Mason CIP Coordination Group Communications Team The CIP Report Editor (tasks: outreach, public affairs, comms., Ed. & events, private sector and Training international coordination) *Program Manager A **Program Manager B Cyber Health Comms. Food-Ag IT Energy Law & Policy The staff should grow to 25-35 with expanded projects and financial resources. Water External Advisory Board Management Support Team Associate Director Chief of Staff Research & Technology Financial/Resource Manager Admin. Assistant to the Director **Program Manager C **Program Manager D Energy Industrial Base Chemical Transportation *The Interim Step **Activated to support resources and demand Economics Foreign Invest. Risk 45
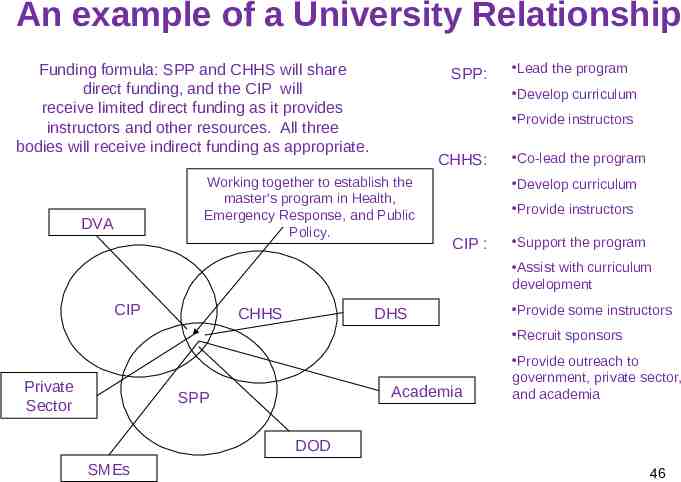
An example of a University Relationship Funding formula: SPP and CHHS will share direct funding, and the CIP will receive limited direct funding as it provides instructors and other resources. All three bodies will receive indirect funding as appropriate. SPP: Develop curriculum Provide instructors CHHS: Working together to establish the master’s program in Health, Emergency Response, and Public Policy. DVA Lead the program Co-lead the program Develop curriculum Provide instructors CIP : Support the program Assist with curriculum development CIP CHHS DHS Provide some instructors Recruit sponsors Private Sector Academia SPP Provide outreach to government, private sector, and academia DOD SMEs 46

State and Local Agencies State and Local Agencies – Office of State and Local Government Coordination and Preparedness (OSLGCP) 2005 Jurisdiction of The Office for Domestic Preparedness (ODP) – The Homeland Security Grant Program (HSGP) Establishment of The Offices of Community Preparedness, and State and Local Government Coordination 47

Industry Industry – To lead the effort of engaging business, DHS created the Homeland Security Advanced Research Projects Agency (HSARPA) as the clearing house and coordinating body for these activities. – The DHS has also actively sought “innovative and unique” concepts and technologies from the private sector by issuing unsolicited proposals from businesses for the purpose s of contracting. 48

Major Research Areas of HS Homeland Security Research Areas with Codes [3] 01 Explosives Detection, Mitigation and Response 02 Social, Behavioral, and Economic Sciences 03 Risk and Decision Sciences 04 Human Factors Aspects of Technology 05 Chemical Threats and Countermeasures 06 Biological Threats and Countermeasures 07 Food and Agriculture Security 08 Transportation Security 09 Border Security 10 Immigration Studies 11 Maritime and Port Security 12 Infrastructure Protection 13 Natural Disasters and Related Geophysical Studies 14 Emergency Preparedness and Response 15 Communications and Interoperability 16 Advanced Data Analysis and Visualization 49

Intelligence Analysis Intelligence – The process, which produces a product through a series of six steps (Richelson 1999, 8) Collection of data Processing this information Integration with other data Analysis of what has been assembled Evolution of the data Interpretation by the analyst(s) – Information analysis (IA) and the use of intelligence is not only practical in combating terrorism, but is also utilized in law enforcement; disaster planning and response; competitive analysis; and strategic planning 50
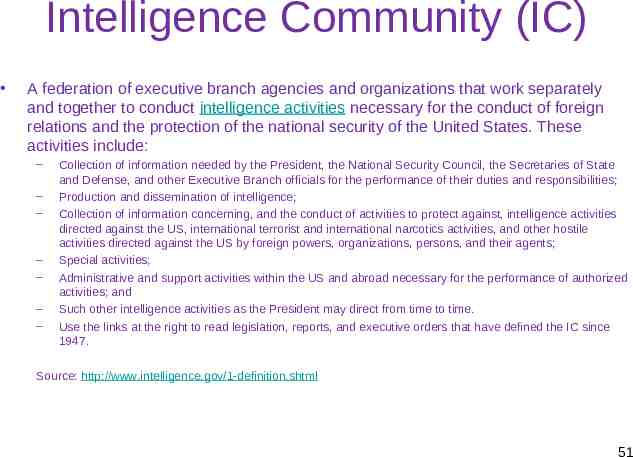
Intelligence Community (IC) A federation of executive branch agencies and organizations that work separately and together to conduct intelligence activities necessary for the conduct of foreign relations and the protection of the national security of the United States. These activities include: – – – – – – – Collection of information needed by the President, the National Security Council, the Secretaries of State and Defense, and other Executive Branch officials for the performance of their duties and responsibilities; Production and dissemination of intelligence; Collection of information concerning, and the conduct of activities to protect against, intelligence activities directed against the US, international terrorist and international narcotics activities, and other hostile activities directed against the US by foreign powers, organizations, persons, and their agents; Special activities; Administrative and support activities within the US and abroad necessary for the performance of authorized activities; and Such other intelligence activities as the President may direct from time to time. Use the links at the right to read legislation, reports, and executive orders that have defined the IC since 1947. Source: http://www.intelligence.gov/1-definition.shtml 51
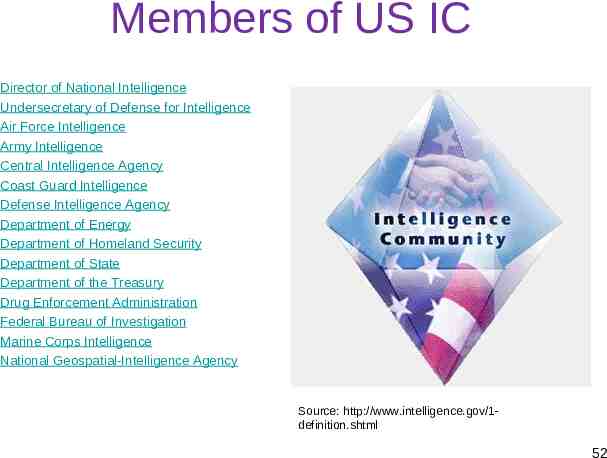
Members of US IC Director of National Intelligence Undersecretary of Defense for Intelligence Air Force Intelligence Army Intelligence Central Intelligence Agency Coast Guard Intelligence Defense Intelligence Agency Department of Energy Department of Homeland Security Department of State Department of the Treasury Drug Enforcement Administration Federal Bureau of Investigation Marine Corps Intelligence National Geospatial-Intelligence Agency National Reconnaissance Office National Security Agency Navy Intelligence Source: http://www.intelligence.gov/1definition.shtml 52

Overview of Information Analysis The Intelligence Cycle – Planning and Direction Drawing up specific collection requirements – Collection Gathering of the raw data needed to produce finished intelligence – Processing Conversion of the vast amount of information collected to a form usable by analysts – All-Source Analysis and Production Conversion of basic information into finished intelligence – Dissemination Distribution of the finished intelligence to the consumers, the same policy makers, whose needs initiated the intelligence requirements 53

Overview of Information Analysis Security Clearance – Specifies a level of access given to certain information and is a status granted to individuals, typically members of the military and employees of governments and their contractors – Security Clearance Steps A detailed life story form Background check Full field investigation Special background investigation (SBI) Polygraph test of the candidate Adjudication: A review of all the materials from the prior steps, and a conclusion is reached where the individual is either given or denied the requested level of clearance Levels of Classification: Unclassified, Confidential, Secret, Top Secret 54

Overview of Information Analysis Role of Information Analysis in HS – Homeland Security is a relatively new area. – The future success of information analysis and preparation of intelligence depends on the ability of agencies to cooperate and share pertinent information to protect the nation’s interests. – One emerging issue of in the IC: The rising need for analysts as the existing workforce approaches retirement age. Current estimates: 20,000-25,000 analysts positions in the IC will be available – The other issue shaping the future of the IC is the need for increased translators of foreign languages. 55

Homeland Security Related Resources Conferences – Homeland Security 2008 AFCEA INTERNATIONAL (Armed Forces Communications and Electronics Association) AFCEA's 7th Annual Renowned Homeland Security Conference "Building on Progress.A Promising Future" February 27-28, 2008 Ronald Reagan International Trade Center Washington, D.C. http://www.afcea.org/events/homeland/08/home.asp – Homeland Security in Action Second Annual Conference and Showcase The Naval Postgraduate School, Monterey, California August 25-29, 2008 http://www.physics-math.com/ConferenceFolder/2008ConfHomePage 56

Homeland Security Related Resources – 7th Annual 2008 Homeland Security Conference Fall 2008 Albuquerque, New Mexico http://www.nmhsconference.org/index.html – 2009 IEEE International Conference on Technologies for Homeland Security (HST 2009) May 11 - 13, 2009 Westin Hotel - Waltham, MA – Greater Boston http://www.ieeehomelandsecurityconference.org/ – 2009 NRC/FFC and IIIA Homeland Security Symposium “Protecting Large Facility Complexes” Wednesday, May 13, 2009 Keck Center, National Academy of Sciences, Washington, D.C. 57

Homeland Security Related Resources Journals – Journal of Homeland Security and Emergency Management http://www.bepress.com/jhsem/ – Homeland Security Affairs http://www.hsaj.org/ – Homeland Defense Journal (magazine) http://www.homelanddefensejournal.com/hdl/ home.asp 58

Funding Sources for Homeland Security Research DOH DOD Major US IC member organizations 59

Conclusions The growth of Homeland Security in America – One of the most wide-sweeping bureaucratic movements in history. – For coordinated domestic preparedness efforts, improvements are necessary. – Understanding of key legislation, organizations, terms, and goals of HS is necessary. – More detailed research of many perspectives of HS should be pursued. 60

References [1] Homeland Security, URL http://en.wikipedia.org/wiki/Homeland Security [2] Understanding Homeland Security – Policy, Perspectives, and Paradoxes, John B. Noftsinger, Jr., Kenneth F. Newbold, Jr., and Jack K. Wheeler, Palgrave Macmillian, 2007. [3] Homeland Security Research Areas with Codes, URL http://www.orau.gov/DHSED/2008pages/ResearchAreaswithCodes.pdf [4] The CIP Report, Critical Infrastructure Protection Program, School of Law, George Mason University, Volume 7, Number 1, July 2008. http://cipp.gmu.edu/archive/cip report 7.1.pdf [5] 2008 Homeland Security Spring Research Symposium “Fostering Public Private Partnerships,” The National Academy of Sciences, Washington, D.C., May 22, 2008. http://www.jmu.edu/iiia/2008symposium/index.html [6] 2007 Homeland Security Spring Research Symposium “Cascading Infrastructure Failures: Avoidance and Response,” The National Academy of Sciences, Washington, D.C., May 16, 2007. (IIIA Publication 08-02) http://www.jmu.edu/iiia/webdocs/symposiums/2007%20Symposium%20Program.pdf [7] 2006 Homeland Security Spring Research Symposium “Homeland Security: Engaging the Frontiers,” The National Academy of Sciences, Washington, D.C., May 12, 2006. (IIIA Publication 07-02) [8] Toward an Organization for Software System Security Principles and Guidelines, IIIA Technical Paper 08-01, Samuel T. Redwine, Jr., James Madison University, 2008. http://www.jmu.edu/iiia/webdocs/Reports/SwA Principles Organization-sm.pdf 61






