Cybersecurity and Criminal Justice Brian K. Payne, PhD Vice
88 Slides3.46 MB

Cybersecurity and Criminal Justice Brian K. Payne, PhD Vice Provost Department of Sociology and Criminal Justice Old Dominion University This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Criminal Justice and Cybersecurity After completing this module, students will be able to: Discuss the impact that cyber technology has on individuals’ experiences with crime and victimization. Describe the role of cybersecurity in defining definitions of appropriate and inappropriate behavior. Describe the role of the criminal justice system in cybercrime cases. Identify common types of cybercrimes and theories explaining them. Explain how the discipline of criminal justice addresses cybercrime. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Criminal Justice and Cybersecurity The Discipline of Criminal Justice and Cybersecurity Types of cybercrime The criminal justice system and cybercrime This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity 1. Conceptualizing cybercrime 6. 2. Explaining cyber offending and victimization Expanding the field of digital forensics 7. Determining interventions 3. Identifying guardianship activities 8. 4. Measuring victimization and offending Developing, researching, and understanding cyber law 9. Seeking NSA Designation 5. Developing future employees This material is based upon work supported by the National Science Foundation under Grant No. 1723635. 10. Conducting interdisciplinary research.

The Discipline of Criminal Justice and Cybersecurity – Conceptualizing Cybercrime What is cybercrime? Legal definition – cyber-related behavior that is against the law - Defined as illegal - No legal defense or justification - Offenders can be punished Sociological definition – cyber-related behavior society describes as wrong, regardless of legality This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Conceptualizing Cybercrime Many cybercrimes are traditional crimes that are committed differently than they were in the past Fraud Embezzlement Bullying Others are new types of crimes Distributed denial of service attacks Unauthorized access This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Conceptualizing Cybercrime Myths about cybercrime Most cybercriminals are skilled hackers. Cybercrime can be prevented with virus protection software. Virtually all cybercrimes occur because of technological problems with software or hardware. The criminal justice system has primary responsibility for preventing and responding to cybercrime. Cybercriminals tend to have higher IQs than the general population. When caught, cybercriminals rarely go to prison. Cybercrime is different from white-collar crime. Cybercrime is always bad. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Conceptualizing Cybercrime Functions of cybercrime Warning light about problems. Social change Boundary maintenance (help to understand rules) Community integration (some would say that Russia’s behaviors in 2016 election brought Democrats together) These functions apply to all types of crime (Durkheim) Would you make cybercrime go away if you could? This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Explaining Cyber Offending and Victimization Several criminological studies explore causes of cyber offending/victimization: Self-control – several studies show offenders and victims have low self-controls Neutralization theory – research shows offenders justify behavior before committing the crimes: -denial of victim (victim deserves it) -denial of injury (no one is hurt) -appeal to higher loyalties (doing it for broader group, like Anonymous) -condemnation of condemners (“officials” commit crime too) -claims of future patronage (will purchase pirated software later) -digital rights management software defiance (frustration with digital rights software) Others to be discussed below including learning theory, routine activities theory, and subcultural theory. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Identifying Guardianship Activities Hinduja and Kooi applied principles of situational crime prevention to cybersecurity. Situational crime prevention focuses on guardianship strategies that consider the context surrounding various crimes. The focus is on the crime, not the offender. This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Target hardening Access control Removing/deflecting offenders Controlling facilitators Entry/exist screening Formal surveillance Surveillance by employees Natural surveillance Target removal Removing temptations Denying benefits Rule setting

The Discipline of Criminal Justice and Cybersecurity – Measuring Cyber Offending and Victimization Criminologists measure offending and victimization through: -Using reports to government agencies (e.g., Internet Crime Complaint Center) advantage: accessible, data available over time, disadvantage: “dark figure” of cyber crime (unreported crime) -Conducting self-report surveys advantage: address dark figure of crime disadvantage: validity, hard to conduct Criminologists help to demonstrate pervasiveness of cyber offenses This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Developing Future Employees With appropriate coursework, criminal justice graduates can enter cyber careers related to NICE framework. Oversee and govern -- “Provides leadership, management, direction, or development and advocacy so the organization may effectively conduct cybersecurity work.” Collect and operate – analogous to counterintelligence Cybercrime majors integrating CJ and technology majors have been developed. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Expanding Field of Digital Forensics Digital forensics – field that was borne, in part, out of criminal justice. Experts define it as: “The use of scientifically derived and proven methods toward the preservation, collection, validation, identification, analysis, interpretation, documentation and presentation of digital evidence derived from digital sources for the purpose of facilitating or furthering the reconstruction of events found to be criminal, or helping to anticipate unauthorized actions shown to be disruptive to planned operations.” Criminal justice has been identified as one of three social sciences (Sociology and Psychology being the other two) that would create competencies for the growing field of digital forensics. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Determining Interventions Criminal justice researchers study: Appropriate punishments Should offenders be sent to prison? When on probation, how do you limit computer access for cyber offenders? Does punishment prevent future misconduct? Appropriate prevention strategies Do “warnings” stop hackers? Who uses virus protections? Appropriate policies and laws This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Developing, Researching, and Understanding Cyber Law Law – form of social control proscribing penalties for violations Criminal law – proscribes criminal punishment, viewed as crimes against the state. punishments – prison/jail, probation, fine, etc. Civil law – proscribes monetary and injunctive penalties, viewed as crimes against individuals or organizations. (lawsuits) penalties – financial and administrative (cease/desist) Regulatory law – proscribes regulations enforced by administrative bodies at state or federal level penalties – financial and administrative (cease/desist) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Developing, Researching, and Understanding Cyber Law Cyber law – form of social control regulating cyber technologies Brenner (2012) describes intersection of cyber and criminal laws: Hacking laws regulate against the unauthorized access of a computer. Federal malware laws make it illegal to intentionally damage with malicious malware. Cybercrimes against property laws include theft, cyber bank theft, theft of trade secrets, and other laws Cybercrimes against persons laws include cyber harassment, cyber stalking, and cyber threats laws. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Seeking NSA designation To receive cyber operations designation, must approach cybersecurity from interdisciplinary perspective. Combining CJ with other disciplines does this. Certain topics that must be addressed (like cyber law) can be addressed in criminal justice courses that are part of a cybersecurity program. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Discipline of Criminal Justice and Cybersecurity – Conducting Interdisciplinary Research How criminal justice researchers study cybercrime Surveys Students Members of public Professionals Analysis of existing records Reviews of web forums Field research Experiments Studies of students This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Opportunities exist to have criminal justice researchers work more closely with researchers from computer science, engineering, information technology, psychology, business, philosophy, and other disciplines that make up the interdisciplinary field of cybersecurity.

Types of Cybercrime Hacking Cyber Attack Cyber Bullying This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Cyber Fraud Child Pornography Cyber Terrorism Digital Piracy

For each offense type, consider 1. What are specific varieties? 2. What patterns have been identified for the offenses? 3. Who engages in these offenses? 4. Why do they commit the crimes? 5. How would other disciplines (information technology, business, philosophy, engineering, and computer science) address each type? This material is based upon work supported by the National Science Foundation under Grant No. 1723635.
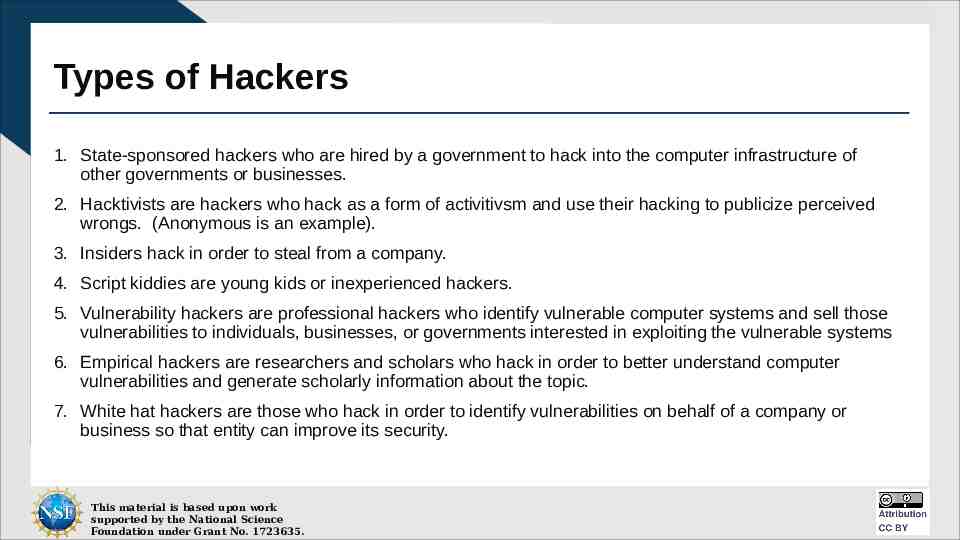
Types of Hackers 1. State-sponsored hackers who are hired by a government to hack into the computer infrastructure of other governments or businesses. 2. Hacktivists are hackers who hack as a form of activitivsm and use their hacking to publicize perceived wrongs. (Anonymous is an example). 3. Insiders hack in order to steal from a company. 4. Script kiddies are young kids or inexperienced hackers. 5. Vulnerability hackers are professional hackers who identify vulnerable computer systems and sell those vulnerabilities to individuals, businesses, or governments interested in exploiting the vulnerable systems 6. Empirical hackers are researchers and scholars who hack in order to better understand computer vulnerabilities and generate scholarly information about the topic. 7. White hat hackers are those who hack in order to identify vulnerabilities on behalf of a company or business so that entity can improve its security. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

State-sponsored hackers Some may target other nations or businesses in other nations Russia reportedly has spent 300 million hiring 1,000 hackers to target 100 countries. China has also been identified as a nation using similar tactics Sony breach by North Korea Related to cyber warfare (discussed below) Nations may pay hackers to test vulnerabilities US Digital Service held “Hack the Pentagon” in February 2017 Charlton, C. (2017). Russia spends 250m every year employing 1,000 state-sponsored hackers. Retrieved from https://www.thesun.co.uk/news/2579702/russia-hackingbudget-250-million-cyber-attack/ This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Hacktivists Combines the terms hacking and political activism Hacking that is done for political reasons. Varieties Virtual blockade – visiting a website and creating excessive traffic to limit access to the website. - Swarming – simultaneously visit website to cause collapse e-mail bombs/ping attacks – sending thousands of emails simultanesouly to target Web hacking/computer breakins – damaging or defacing (like PETA throwing paint on people wearing fur. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Empirical Hackers Two researchers showed how a car could be hacked in July 2015 1.4 million automobiles recalled Research labs set up separate from organization’s network to research hacking (honeypots) Students can be “empirical hackers” but must follow instructor’s guidelines. Must not hack outside of approved virtual environment that is removed from the organization or the government’s network. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Insiders An example of white-collar crime (discussed earlier) Insiders are seen as one of the biggest threats to a company’s computer security. Many inside hacks traced to recently fired employees. Other factors: Introversion Ethical flexibility Reduced loyalty Entitlement (Studies cited by Shaw et al.) Businesses may not report: Fear of losing public confidence Costs too much to get involved with the justice process Don’t want to expose vulnerabilities May not know the hack occurred This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Script Kiddies Least sophisticated Acts committed out of boredom and thrill seeking Don’t do as much damage as other hackers Younger than other hackers Seek acceptance from the hacking subculture, but experienced hackers have little respect for them This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Vulnerability Hackers Aka White Hat Hackers and ethical hackers Synack held a challenge – paid 30,000 as highest reward for exposing hacking vulnerabilities Called bug bounties This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Should we teach “ethical hacking”? Benefits Understand hacking Understand hackers Disadvantages Learn how to commit crimes Pike (2013) cites research showing that “both white-hat and black-hat hackers understand the consequences of illegal hacking, however, college students do not”

Who are the Hackers? Tend to be: Younger Caucasian White Males High school educated International in scope When females involved, frequently in groups This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Why do they hack? Subcultural explanations – individuals are part of a technology subculture that rewards behaviors. White hat/vulnerability hackers – legal and financial rewards Cybercriminals – to create harm or unfairly gain advantage Defcon – annual conference for hackers. Learning theory – individuals learn how to hack and why to hack. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

How do various disciplines address hacking? Information technology Business Harm done to businesses Unauthorized access by insiders How to create a business that responds to hacking Philosophy Engineering Computer Science Criminal Justice This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Adversary Class Skills Maliciousness Motivation Method script kiddies, newbies, novices very low low boredom, thrill seeking download and run already-written hacking scripts known as "toolkits" hacktivists, political activists low moderate promotion of a political cause engage in denial of service attacks or defacement of rival cause sites cyber punks, crashers, thugs low moderate prestige, personal gain, thrill seeking write own scripts, engage in malicious acts, brag about exploits insiders, user malcontents moderate high disgruntlement, personal gain, revenge uses insider privileges to attack current or former employers coders, writers high moderate power, prestige, revenge, respect write scripts and automated tools used by newbies, serve as mentor white hat hackers, old guard, sneakers high very low intellectual gain, ethics, respect non-malicious hacking to help others and test new programming black hat hackers, professionals, elite very high very high personal gain, greed, revenge sophisticated attacks by criminals/thieves; may be 'guns for hire' or involved in organized crime cyber terrorists very high very high ideology, politics, espionage state-sponsored, well funded cyber attacks against enemy nations This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Cyber Attacks Efforts to harm, modify, destroy, or take over a cyber technology. Strategies have evolved over time. This is why you spend so much money on virus protection. Malware malicious software. While discussed separately from hacking, some hackers might hack in order to attack. Wikimedia (2009). Bones DOS Trojan. Retrieved October 14, 2018 from https://commons.wikimedia.org/w/index.php?search BONES dos trojan&tit le Special%3ASearch&profile default&fulltext 1#/media/File:Bones DOS Trojan.jpg This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Attack Types Subtypes Description viruses file infectors, system/boot record infectors, macros self-replicating program that replicates through infected files; attached to an existing program worms mass mailing via botnets, network aware self-replicating program that replicates through networks or email; no user interaction required trojans remote access, data destruction program made to appear benign that serves a malicious purpose buffer overflows stack-based overflows, heap-based overflows process that gains control or crashes another process via buffer overflowing denial of service host (resource hogs, crasher), network (TCP, UDP, ICMP flooding), distributed attack that prevents legitimate users from accessing a host of network network attacks spoofing, web/email phishing, session hijacking, wireless WEP cracking, web application attacks attack based on manipulating network protocols, against users or networks physical attacks basic, energy weapon (HERF gun, EMP/T bomb, LERF), Van Eck attacks based on damaging the physical components of a network or computer guessing (brute force, dictionary attacks), exploiting implementation attacks aimed at acquiring a password or login credential packet sniffing, host mapping, security scanning, port scanning, OS fingerprinting attacks in which no damage is carried out, but information is gathered by attacker password attacks information gathering This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Additional varieties Ransomware – install malware that holds computer or system hostage until ransom is paid anonymously. Web defacement – hacking into computer system and defacing a website. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Who engages in cyber attacks? Similar to hackers Most have limited technical skills/knowledge Those with significant skills/knowledge tend to form social networks with one another Do not report having college education (may be hiding identities) “operate within a collegial subculture that encourages information sharing and values innovation and skill” (Holt et al., 2012). This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Why do individuals engage in cyber attacks? Motives are tied to different types of attacks. Defacement – often politically motivated. Denial of service – might be political or economic. Worms or viruses – might be created to show knowledge. Ransomware – done for economic reasons, clearly tied to Routine Activities Theory This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

How do other disciplines view cyber attacks? Information Technology Protecting information Encouraging individuals to protect selves Business Protecting businesses Developing computer security businesses Philosophy Questions laws and policies used Explores privacy rights This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Engineering Securing networks and systems Focus on critical infrastructure Computer Science Creating malware and virus software Criminal Justice

Cyber Fraud Fraud – using deception to steal items Cyber fraud – using cyber technologies to deceive individuals and steal from them. Different from robbery in many ways: No force used Larger economic losses No physical contact necessary to complete the crime No weapon used, especially in cyber fraud unless you consider technology to be a weapon. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Varieties of Cyber Fraud Internet fraud Auction fraud (driving up bids) Crime in online sales (not delivering, overcharging, counterfeit goods) Email fraud and scams Phishing – mass emails Work-at-home scam emails Lottery scams Romance scams (sweetheart scams) Catfishing Extortion Theft Nigerian Fraud (419 frauds) Identity theft Technology schemes (contacting and offering tech. help) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Patterns surrounding cyber fraud International in scope Contrepreneurial crime – some frauds appear to be legitimate businesses, but are illegitimate and designed to commit crime Trust violations are central Target many victims simultaneously Significant technical knowledge not required In 2016, nearly 300,000 complaints received by FBIs Internet Crime Complaint Center, with losses totaling 1.3 billion. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Top 10 States by Number of Reported Cybercrime Victims Internet Crime Complaint Center (IC3). (2016). Internet Crime Report. Retrieved October 14, 2018 from https://pdf.ic3.gov/2016 IC3Report.pdf This material is based upon work supported by the National Science Foundation under Grant No. 1723635. https://pdf.ic3.gov/ 2016 IC3Report.pdf

Top 10 States by Losses to Internet Crime Internet Crime Complaint Center (IC3). (2016). Internet Crime Report. Retrieved October 14, 2018 from https://pdf.ic3.gov/2016 IC3Report.pdf This material is based upon work supported by the National Science Foundation under Grant No. 1723635. https://pdf.ic3.gov/2016 IC3Report.pdf

Who engages in cyber fraud? Many scams are in groups. Nigerian advanced fee frauds: Called 419 frauds in reference to Nigeria’s legal code regulating against fraud Can originate from anywhere but many come from Nigeria Promise money in exchange for payment *Osuofia (2006). I Go Chop Your Dollar [Music Video].Retrieved October 14, 2018, from https://www.youtube.com/watch?v D YjvC4ndzM This material is based upon work supported by the National Science Foundation under Grant No. 1723635. I Go Chop Your Dollars* song: "419 is just a game, you are the losers, we are the winners. White people are greedy, I can say they are greedy White men, I will eat your dollars, will take your money and disappear. 419 is just a game, we are the masters, you are the losers." Signs of scams Poorly written Misspelled words Claims of monetary rewards Email comes out of nowhere Claims of legitimacy Claims of urgency

Why do individuals commit cyber fraud? Routine activities theory, crime occurs when three things are present: 1. Absence of capable guardian 2. Presence of motivated offender 3. Vulnerable target (Cohen and Felson) The Internet has increased number of motivated offenders and vulnerable targets, with cyberspace being difficult to guard. Fraud is actually easy to commit Self-control Some studies show that cyber fraud victims have low levels of self-control, suggesting they might be more impulsive than non-victims. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

How do other disciplines view cyber fraud? Information Technology Business Philosophy Engineering Computer Science Criminal Justice This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Digital Piracy Illegally copying/using digital media that is protected by copyright. Music, television shows, movies, ebooks, software photos, etc. Nearly 32 billion in TV/Movie revenue lost from piracy in 2017. 191 billion visits to online piracy sites in 2016. This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Top 10 Most Pirated Movies of 2017 Thor Ragnarok Shape of Water Jumanji: Welcome to the Jungle Bright Blade Runner 2049 Murder on the Orient Express Downsizing Geostorm Justice League Coco (PCMAG.COM, 2018).

Digital Piracy Prevention Digital Rights Management (DRM) strategies developed. Digital rights management technologies developed to: Prevent unauthorized access Restrict use of product to intended use Deterrence by making hit hard to misuse product Detection identified unapproved use. Digital rights management systems include: Content identification (watermarks/digital fingerprints) Encryption-translates plain text to random/coded data Decryption –translates encrypted data to data that can be understood. Licensing – contracts specifying appropriate use This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Explaining Digital Piracy Widespread perception that no one is hurt from piracy exists. Piracy is easy to commit. Belief that punishment is rare. Research by Higgins found that low self-control interacts with values and rational decision making to increase the likelihood of committing digital piracy. Higgins’ question: You are taking a class that requires a lot of computer homework. The class is important to your success in your major because other classes use the same material, so you want to learn the material and make a good grade in the class. You have all of the computer programs that you need for the class EXCEPT for one. So, you go to the bookstore to purchase the software; however, you cannot afford it. Others in the class have told you that they own the program and would be willing to burn a copy for you. What is the likelihood that you would take the software under these circumstances? This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Who engages in digital piracy? Age – younger more likely Those who perceive external or internal Gender – females less likely rewards more likely to commit Computer self efficacy – “small but significant effect” Different from computer skills, refers to belief in ability to use computers This material is based upon work supported by the National Science Foundation under Grant No. 1723635. digital piracy

How do other disciplines view cyber fraud? Information Technology Business Philosophy Engineering Computer Science Criminal Justice Panas and Ninni conclude that electronic file sharing can be seen “as a consequence of technological innovation”? Explain why the authors reach this conclusion and how technological innovation changed the way users define right and wrong. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Cyber bullying Bullying activities using digital media/technologies Girls believed to be more involved in cyber bullying than traditional bullying. Occurs over the life course (even in the workplace) Estimated that one in four youth experience cyber bullying This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Types of cyber bullying Verbal aggression Relational aggression (spreading rumors) Sexting Flaming Outing Masquerading Exclusion This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Here is one girl’s story: https://www.girlshealth.gov/bullying /whatis/sexting.html

Patterns surrounding cyber bullying Hard to detect Persistent Permanent Uses different mediums Email Internet SMS/Text messages Social media This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Different from traditional bullying: Can be anonymous Technical Cyber bullies feel less remorse than traditional bullies because they don’t see the victim’s reactions. (Peebles, 2014). Larger audience for cyber bullying https://www.ncbi.nlm.nih.gov/pmc/articles/P MC4276384/

Who engages in cyber bullying? Cyber Bullies Younger Have been victims of cyber bullying Also commit traditional bullying This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Cyber Victims Internet dependence Do not feel popular Have committed cyber bullying Infrequently commit traditional bullying but have been victims of traditional bullying

Why do individuals commit cyber bullying? Power – maintain status and reputation Affiliation – to be a part of a group Anger – targeted towards a victim Fun – some enjoy doing these acts Some have talked about the “joy of violence” referring to the pleasure some get out of hurting others. Is it possible that, for some bullies, there is a “joy of cyber bullying”? If so, how does technology promote this “joy”? This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

How do other disciplines view cyber fraud? Information Technology Business Philosophy Engineering Computer Science Criminal Justice This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Child Pornography Internet described as “principal medium for distribution” of child pornography (Quayle and Taylor) Computers allow Production Storage Distribution Contact with potential victims Contact with other pedophiles (Quayle and Taylor) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Patterns surrounding child pornography One study found that nearly 245,000 U.S. computers shared 120,418 child pornography files on a peer-to-peer site. (Wolak et al., 2014). Over 80% shared relatively few files or participated for a short period. Less than 1% “made high annual contributions to the number of known CP files available on the network (100 or more files)” Three types of child sex offenders: Those who collect Internet pornography Those who engage in contact offenses Those who engage in contact offenses and pornography (Henshaw et al.) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Who engages in Internet child pornography? Male dominated offense Predominantly Caucasian Compared to other child sexual abusers: More psychological difficulties in adulthood Few prior convictions for sexual offenses Less like to commit new offenses after conviction (Webb et al., 2007) Higher amount of depression and interpersonal deficits, and lowers aggression and dominance scores (Magaletta et al., 2014) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Why do offenders collect/view child pornography? Technology exacerbated problem. Made it easy to find material online Provided opportunities for offenders to “meet” other pedophiles online and feel less isolated about their behaviors. Made it easy to distribute materials online This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

How do other disciplines view child pornography? Information Technology Business This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Philosophy Engineering Computer Science Criminal Justice

Internet Sex Crimes Revenge porn This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Sexual blackmail Sexting Prostitution

Revenge Porn Sharing intimate photos online without permission AKA nonconsensual pornography Done to embarrass former partner Recognizing it’s not a “perfect solution,” one legal expert argues that victims can sue on basis of copyright violations (Levendowski) Only recently criminalized (38 states and DC have laws as of 2018) https://www.cybercivilrights.org/revenge-porn-laws/ This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Sexual Blackmail Finding compromising photos/videos and threatening to publish unless paid In 2011, Internet Crime Complaint Center received 50 complaints Many targeted physicians This material is based upon work supported by the National Science Foundation under Grant No. 1723635. “the IC3 has received over 50 complaints reporting extortion emails targeting professionals, mainly physicians. Victims were told complaints had been filed against them and posted online, claiming they were facing prison for sexual indecency. Also posted were the victims' names, addresses, telephone numbers, and email addresses. The victims were told ‘these types of comments will destroy your reputation and are permanently archived on search engine sites; you will lose thousands of dollars in revenue with a bad reputation.’ Victims were also told the sender could ‘convince the people who posted the comments to remove the’; however, the removal fee was 250 USD.”

Sexting Sending photos/videos/comments of sexual nature Pew (2009) study: 4% of teens with cell phones have sent sexual photos 15% of teens with cell phones have received them Older teens and teens who pay own phone bills more likely to sext Survey of 352 undergraduate students: Nearly two-thirds sent or received sexual message Males more likely to sext casually Half reported positive sexual/emotional consequences and one-tenth reported negative consequences. (Druin et al. 2017) Illegality depends on context Communicating to minor Communicating photos/videos of minor This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Online Prostitution Internet technology has changed the way prostitution crimes are committed. Number of participants has grown, and some former “street” prostitutes have turned to online marketing. Online prostitutes engage in less risky behavior than “street” workers Marketing is relatively easy and inexpensive Easy to evade law enforcement This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Who engages in Internet sex crimes? Sexual blackmail Perpetrated as scams by cyber offenders Revenge porn – tied to some type of relationship Prostitutes: Online prostitutes arrested: average age is 28, 61% are white, 11% are black Study of 685 sex workers found the 41% had a college degree (Cunningham/Kendall) Clients of prostitutes Average age of 43, 80% white (Cunningham/Kendall) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Patterns Surrounding Internet Sex Crimes Internet technology: Helps prostitutes “(a) reach large numbers of potential clients with informative advertising, (b) build reputations for high-quality service, and (c) employ screening methods to reduce the risk of discovery” (Cunningham/Kendall) Provides new strategy for communication in form of sexting “Weapon of emotional and reputational destruction” in revenge porn (Calvert) This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Why do individuals engage in Internet sex crimes? Typically, sex crimes are about power and not sex. In Internet sex crimes, power may play a role. Patriarchal theory has been used to understand sex crimes in general. Women are viewed as property who are owned (or can be ‘bought’ by men) Structural features make it harder for women to enter certain occupations. “Sexual commerce provides a patriarchal right of access to women's bodies, thus perpetuating women's subordination to men” (Gerassi, 2015). How does the Internet perpetrate a patriarchal society? This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

How do other disciplines view Internet sex crimes? Information Technology Business Philosophy Engineering Computer Science Criminal Justice This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Cyber Terrorism/Cyber War Cyberterror -- “using computer technology to engage in terrorist activity” (Brenner, 2007, p. 386). Cyberwar—”Conduct of military operations by virtual means” (Brenner, 2007, p. 401). Information warfare – using information to harm others Martin Libicki identifies these types in What is Information Warfare: Psychological (propaganda) Command and control (infrastructure) Electronic (change flow of electrons/information) Hacker warfare (stealing information) Economic information warfare – using information to harm economy Cyber warfare seen as a type of information warfare This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Patterns surrounding cyber terrorism Harm is similar to harm from crime, but “harms are inflicted for very different reasons” (Brenner, 2007). Goal is demoralization through cyber technology Three categories Weapon of mass destruction – computers could harm critical infrastructure Weapon of mass distraction – manipulate population psychologically Weapon of mass disruption – “undermine a civilian populace’s faith in the stability and reliability of essential infrastructure” (Brenner, 2007). - Make the population think that a system is compromised when it is not. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Who engages in cyber terrorism? Nation-states Domestic terrorism United States Air Force mission is to fly, fight and win.in air, space and cyberspace. https://www.pexels.com/photo/aircraftformation-diamond-airplanes-66872/ This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Why do individuals/groups commit cyber terroristic acts? Political motives – to gain power Economic changes Social changes (Gordon and Ford) This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Appeal of Cyberterrorism Cheaper than other types of terrorism Anonymous Large number of targets Remote capabilities from afar Media coverage (Weimann, 2004)

How do other disciplines view cyber terror? Information Technology Business Philosophy Engineering Computer Science Criminal Justice This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Case Study In 2017, the House Intelligence Committee learned that Russian agents purchased Facebook and Twitters ads seemingly trying to influence the 2016 presidential election. One ad is here. “We basically have the brightest minds of our tech community here and Russia was able to weaponize your platforms to divide us, to dupe us and to discredit democracy.” –Rep. Jackie Spier. Does this constitute cyberwar? Discuss both sides of the argument and the ethical, political, and business ramifications of calling it cyberwar. Shane, S. (2017, November 01). These Are the Ads Russia Bought on Facebook in 2016. Retrieved October 14, 2018, from https://www.nytimes.com/2017/11/01/us/politics/russia-2016-election-facebook.html This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The Criminal Justice System and Cybercrime Three components of the criminal justice system Police Enforce law Maintain order Community Service This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Courts Adjudicate the law Guilt or innocence Protect rights of accused Corrections Apply the law Deterrence Rehabilitation Incapacitation Retribution

The police and cybercrime Much of the cyber law enforcement done in federal and state units, though local police may get involved. In larger departments, different police respond to different types of cybercrime (e.g., cyber fraud versus child pornography) Tools have been developed to help all police officers gather electronic data COFEE – Computer Online Forensic Evidence Extractor is a configured jump drive that police officers can use to gather the forensic evidence in the field. DF investigators can then use the jump drive to search for the evidence collected by the officer. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Police and Cybercrime: Federal Law Enforcement Federal Bureau of Investigation (FBI) – lead agency Cyber Division at FBI Headquarters Cyber Action Team Internet Crimes Complaint Center Computer Crimes Task Forces (partner with DoD and DHS, and state/local) National Cyber Forensics and Training Alliance Department of Homeland Security Immigration and Customs Enforcement (ICE) – support “cross-border” invests. Cybercrimes Centers (C3) Cyber Crimes Unit Child Exploitation Investigations Unit Computer Forensics Unit Secret Service Electronic Crimes Task Forces Cyber Intelligence Section National Computer Forensics Institute This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Police and Cybercrime Reactive – police are notified about incident and respond. Proactive – police actively search for cyber offending. Electronic audits Undercover stings - Easier in digital world Identity is concealed (anyone could be the undercover officer) Less danger Interactions can be recorded Can target larger pool of potential offenders Can do an international investigation without traveling This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Police and cybercrime Challenges with digital forensics Diversity of information agents need to know about Amount of data that needs to be searched is enormous Evidence seizure varies across case types Balancing privacy with amount of information needed Cyber offenders adjust to changing investigation techniques Additional challenges Training Jurisdictional issues Victims don’t report victimization immediately This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

The courts and cybercrime Actors Judge Prosecutor Defense Attorney Defendant Witnesses – lay, expert, professional Similar to other types of crime, when cases are prosecuted, cyber offenders are more likely to plead guilty than go to trial. Challenges Determining appropriate charges For cases that go to trial, technical evidence may confuse jurors Determining actual losses can be hard. Because cases are rarely prosecuted, defense will argue sentence is “unusual” Cases take a long time to prosecute. Victims (companies) may not be willing to participate This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Corrections and cybercrime When convicted, vast majority go to jail or prison (more than 90%) Recent research shows male offenders receive longer prison sentences than female cyber offenders. Sanctions justified on deterrent ideals, but few studies have shown deterrent value of long prison sentences This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Recent Study on Sentences Given to Cyber Offenders Male Prison/Jail Yes No 100 (92.6) 8 (7.4) Female 9 (90.0) 1 (10.0) U.S. Prison/Jail Yes No Foreign 74 (89.2) 9 (10.8) 34 (97.1) 1(2.9)) 6 (7.2) 77 (72.6) 6 (17.1) 29 (82.9) 4 (40.0) 6 (60.0) Restitution Yes No 38 (45.8) 45 (54.2) 9 (25.7) 25 (75.3) 0 (0.0) 10 (100.0) Probation Yes No 7 (8.4) 76 (91.6) 0 (0.0) 35 (100.0) 8 (9.6) 75 (90.4) 0 (0.0) 35 (100.0) Fine Fine Yes No Restitution Yes No Probation Yes No Community Service Yes No 10 (9.3) 98 (90.7) 43 (39.8) 65 (60.2) 7 (6.5) 101 (93.5) 8 (7.4) 110 (92.6) This material is based upon work supported by the National Science Foundation under Grant No. 1723635. 2 (20.0) 8 (80.0) 0 (0.0) 10 (100.0) Yes No Community Service Yes No

Corrections and cybercrime For probation officers, issues arise: Need training for investigations Need guidance in determining conditions of release (whether offenders can have access to computers) Different supervision strategies might be used for cyber offenders Need hardware and software (and training) to search offenders’ computers This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Sample Conditions of Probation for Cyber Offenders No Internet or Electronic Bulletin Board (BBS) access. Provide telephone / Internet service provider billing records monthly. Disclose all online accounts, including user-names and passwords. No access to modem or other connective device. No use of encryption technology or software designed to delete computer log files. Require the use of filtering software. This material is based upon work supported by the National Science Foundation under Grant No. 1723635. Use of activity tracking and reporting software. Computer search / inspection condition. Provide a software/hardware audit at onset of case. No new hardware/software added to the computer without officer authorization. No computer use or access at any location. No use of any device capable of accessing the Internet or an online service

Class Exercise – Sentencing Cyber Offenders SAN DIEGO – ****** was sentenced in federal court today to ****** for his involvement in a conspiracy to steal and misuse mortgage customers’ sensitive personal information. ****** was charged along with ******** with conspiracy to commit wire fraud and computer hacking. ****** was also charged with aggravated identity theft. All four defendants have pleaded guilty. According to charging and sentencing documents, between 2011 and 2014, ***** and his coconspirators were part of a Tijuana-based conspiracy that hacked the computer servers of major U.S. mortgage brokers, stole over 4,200 customers’ mortgage applications, and then used the victims’ social security numbers, addresses, dates of birth and personal information to open unauthorized lines of credit and take over and drain victims’ retirement and brokerage accounts. For example, according to **** plea agreement, he identified multiple victims’ brokerage accounts and fraudulently took control of the victims’ accounts by first calling the brokerage companies and providing the victims’ personal identification information, and then changing the victims’ passwords and contact information. Once he and his codefendants gained control of the accounts, members of the conspiracy wired funds from the victims’ brokerage accounts to coconspirators’ U.S. bank accounts in the San Diego and Calexico areas. Several of these wires were over 20,000 and 30,000 each. What sentence would you give the offender? Explain how you arrived at that decision. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.

Class Exercise – Sentencing Cyber Offenders Earlier today, *****, an Italian citizen, was sentenced by United States District Judge Nicholas G. Garaufis following his conviction by a federal jury in Brooklyn of one count of computer intrusion. The defendant was sentenced to the statutory maximum sentence of **** of imprisonment, a **** fine, and **** of supervised release following incarceration. The Court also directed the forfeiture of the defendant’s botnet, the infrastructure used to manage and run the botnet (including computers, command-and-control servers, and domains), and the backdoor that the defendant installed on victim computers worldwide. The sentence was announced by Bridget M. Rohde, Acting United States Attorney for the Eastern District of New York, and William F. Sweeney, Jr., Assistant Director-in-Charge, Federal Bureau of Investigation, New York Field Office (FBI). As proven at trial, ***** spread malicious software onto computer servers in the United States and around the world and thereby covertly hacked into them. ******’s scheme specifically targeted a type of computer server that companies and individuals typically use for large-scale data storage and transfer. ****** obtained control over the servers and the sensitive data and files they contained. ******* also created an exclusive backdoor that enabled him to access the data and computing power of those servers in perpetuity. In so doing, ****** created a botnet. A botnet is a network of computers (such as servers) infected with malicious software without the true owners’ knowledge or permission; a hacker can remotely control and use a botnet for malicious purposes. What sentence would you give this offender? Explain how you arrived at that decision. This material is based upon work supported by the National Science Foundation under Grant No. 1723635.