CompTIA Security+ Study Guide (SY0-501) Chapter 7: Host, Data, and
12 Slides181.70 KB

CompTIA Security Study Guide (SY0-501) Chapter 7: Host, Data, and Application Security

Chapter 7: Host, Data, and Application Security Explain threat actor types and attributes Explain the impact associated with types of vulnerabilities Explain the security implications of embedded systems Summarize secure application development and deployment concepts

Threat Actors and Attributes Script kiddies Hacktivist Organized crime Nation-states/APT Insiders Competitors

Use of Open Source Intelligence ThreatCrowd OpenPhish OSINT framework Shodan

Types of Vulnerabilities Configuration issues User issues Zero-day exploits Other issues
Embedded Systems Security IoT: Internet of Things

Application Vulnerabilities Input vulnerabilities Memory vulnerabilities
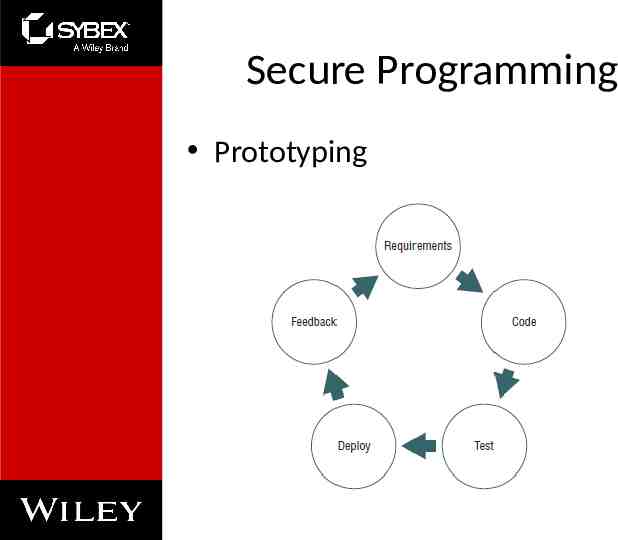
Secure Programming Prototyping

Specific Types of Software Testing Unit testing Integration testing System testing User acceptance testing Regression testing

Patch Management Hotfix Patch Service pack
Database Tier Models One-tier model Two-tier model Three-tier model
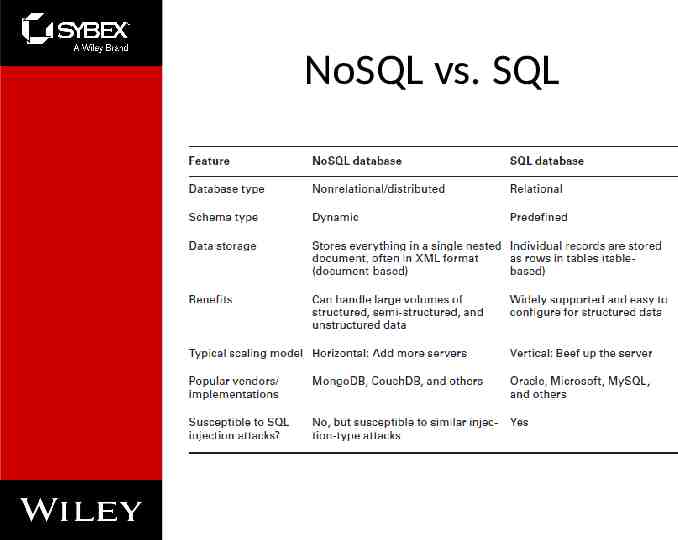
NoSQL vs. SQL






