Complying with HIPAA and HITECH Security Planning Susan Lincke
90 Slides789.01 KB

Complying with HIPAA and HITECH Security Planning Susan Lincke

Security Planning: An Applied Approach 02/22/2024 2 Objectives: Students shall be able to: Define HIPAA, Privacy Rule, Security Rule, CE, PHI. Define threat, vulnerability, threat agent Describe what Privacy Rule covers at a high level Describe what Security Rule covers at a high level Describe the difference between Required and Addressable for the Security Rule.

Security Planning: An Applied Approach 02/22/2024 3 HIPAA Introduced by Senators Edward Kennedy & Nancy Kassebaum; passed 1996 Portability: Workers can continue health care between different employers Group insurance cannot reject, not renew, or charge higher premiums of certain individuals Simplify administration by creating a health care transaction standard Accountability: Penalties for non-compliance Tax provisions

Security Planning: An Applied Approach 02/22/2024 4 HIPAA Titles Title 1: Health Care Insurance Access, Portability, and Renewability Title 2: Preventing Health Care Fraud & Abuse, Administrative Simplification, Medical Liability Reform Title 3: Tax-related Health Provisions Standardizes medical savings accounts Title 4: Application and Enforcement of Group Health Insurance Requirements Title 5: Revenue Offsets Defines how employers can deduct company-owned life insurance premiums from income tax

Security Planning: An Applied Approach 02/22/2024 5 Title 2 Has Three Rules Transactions, Code Sets, and Identifiers: Standards for electronic transmission Electronic Data Interchange: Standardized records for health care transactions The Privacy Rule: Standard for Privacy of Individually Identifiable Health Information The Security Rule: Security Standard for electronic patient health

Security Planning: An Applied Approach 02/22/2024 6 Reasons for Legislation Records of patients or insurance claims made publicly available by accident Email reminder to take Prozac sent to 600 (not blind cc’d) Woman fired from job after positive review but expensive illness 35% of Fortune 500 companies admitted checking medical records before hiring or promoting People avoid using insurance when they have AIDS, cancer, STD, substance abuse or mental illness

Security Planning: An Applied Approach 02/22/2024 7 Medical Identity Theft When a person’s name and other parts of his/her medical identity are stolen for the purpose of getting medical services and goods. Problems: Medical info is for wrong person Inaccurate health records Wrong diagnosis Fatal treatments Imposter claims health care Medical Insurance Fraud Inaccurate Credit History: Bills sent elsewhere

Security Planning: An Applied Approach 02/22/2024 8 Medical Identity Thieves: Who can commit this crime? Computer hackers Members of organized crime rings Health care providers (doctor’s, dentists, hospital employees) 2003: An employee at a cancer center stole the identity of a center patient. The identity thief was sentenced to 16 mos. In prison and ordered to pay restitution. 2006: A desk clerk at a Florida clinic stole the health info of over 1,000 patients. The clerk sold the data to another person. That person used the information to submit 2.8M in fraudulent Medicare claims to the U.S. government.

Security Planning: An Applied Approach 02/22/2024 9 Business Challenges Facing the Health Care Industry Hospital computer systems contain notes from hospital employees and primary care physicians. Health Insurance Companies collect and compile patient data from different providers. Organizations MUST maintain the security of computer systems that hold health data.

Security Planning: An Applied Approach 02/22/2024 10 Health Care Organization Covered Entities (CE) Health plan (e.g., HMO, PPO) Standard bills/records Health care Clearinghouse Standard bills/records Nonstandard bills/records Health Care Provider (e.g., doctor, hospital)

Security Planning: An Applied Approach 02/22/2024 11 Health Care Organization Business Associates (BA) Works Accounting Covered Entities (CE) Health plan for Performs: Claims Processing Transcription Billing Data Analysis Independent organization Work involves health info Not bank or post office Health care Clearinghouse Health Care Provider

Security Planning: An Applied Approach 02/22/2024 12 Business Associates (BA) Must also be responsible with PHI Accreditation Accounting Ac L eg al Legal Department Actuarial in g t n c ou & Consulting Adm in Ma istra nag tion em en t & ce n a Fin Not Business Associates Janitorial Electrical Phone Vending Copy Mail Room Conduit: Mail Financial Institution: Banks Bank

Security Planning: An Applied Approach 02/22/2024 13 Protected Health Information (PHI) Health Information Relates to Physical or Mental health or past/present/ future payment Identifiers Name SSN city or county zip code phone or fax medical record # fingerprint If YOU had AIDS, how could such identifiers Identify you? Individually Identifiable Health Information Created or maintained by CE or BA Protected Health Information (PHI) Covered by HIPAA & HITECH

Security Planning: An Applied Approach 02/22/2024 14 Treatment, Payment & Health Care Operations (TPO) Treatment Payment Provision & coordination of health care among health care providers, including referral Any activities involved in compensation for health care: billing, determining coverage or eligibility analyzing services Health Care Operations Administrative functions related to health care: financial or legal or quality improvement, training, certification, case mgmt, business planning

Security Planning: An Applied Approach 02/22/2024 15 HIPAA Standard Transactions Health plan (e.g., HMO, PPO) Enrollment or Disenrollment into Health Plan Health Plan Premium Payment Health Plan Eligibility Inquiry Certification & Authorization of Referral Health Care Claim Health Care Claim Status Request Health Care Claim Payment Plan Sponsor (Employer) Certification & Authorization of Referral Health Care Provider (e.g., doctor, hospital)

Security Planning: An Applied Approach 02/22/2024 16 Criminal Penalties for HIPAA Penalty Up to 50K Imprisonment Up to one year Offense Wrongful disclosure of individually identifiable health information Up to 100K Up to 5 years committed under false pretenses Up to 500K Up to 10 years with intent to sell, achieve personal gain, or cause malicious harm Then consider bad press, state audit, state law penalties, lost claims,

Security Planning: An Applied Approach 02/22/2024 17 HITECH: Health Information Technology for Economic and Clinical Health Act (2009) Breach Notification Rule: Introduced notification requirements Specifies how CE/BA should notify individuals and agencies if a breach of information occurs Patients need to be notified within 60 days (unless law enforcement investigation) Patient notification shall include description of what happened, date of the breach and its discovery type of information that was breached, steps the clients should take to protect themselves, and actions the CE is taking to investigate the breach, mitigate existing problems, and prevent new ones.

Security Planning: An Applied Approach 02/22/2024 18 HITECH Act (2009) HITECH Category Each Violation Max Per Year 120- 30,113 30,133 Violation is due to reasonable cause 1,205 60,226 120,452 CE/BA demonstrated willful neglect but corrected violation 12,045- 60,226 301,130 CE/BA demonstrated willful neglect and took no corrective action within 30 days 60,226-1.8 million 1.8 Million CE/BA exercised reasonable diligence but did not learn about violation Penalties are prohibited if problem is corrected within 30 days and no willful neglect Penalties pay for enforcement and redress for harm caused

Security Planning: An Applied Approach 02/22/2024 19 Breach Notification Laws The Oregonian, May 2006 In one of Oregon’s largest security breaches, Providence Health System disclosed that a burglar stole unencrypted medical records on 365,000 patients kept on disks and tapes left overnight in an employee’s van State Laws, called Breach Notification Laws require CEs to notify patients when their PHI has been breached If data is encrypted and laptop is lost, notification is not required This often applies to any industry that uses personal information, such as Social Security Numbers

Security Planning: An Applied Approach 02/22/2024 20 The Genetic Information Nondiscrimination Act of 2008 Protects against some types of genetic testing discrimination: Insurance companies can’t make eligibility decision based on genetic testing results. Insurance companies can’t base cost of premiums on genetic testing results. Employers can’t hire, fire or make job decisions based on the use genetic testing. Employers/Health Insurance Plans can not requiring genetic testing.
Security Planning: An Applied Approach 02/22/2024 21 The HIPAA Privacy Rule

Security Planning: An Applied Approach 02/22/2024 22 Privacy Rule: Develop Policies CE/BAs shall: Develop policies, procedures, and standards for how it will adhere to Privacy Rule. How will CE/BA: use and disclose PHI? protect patient rights? Regularly review policies and procedures Update policies when new requirements emerge Monitor that policies/procedures are consistently applied throughout the organization

Security Planning: An Applied Approach 02/22/2024 23 Privacy Rule: No NonHealth Usage of PHI The National Law Journal, May 30, 1994 A banker who also served on his county’s health board cross-referenced customer accounts with patient Information. He called due the mortgages of anyone suffering from cancer. Health information is not to be used for nonhealth purposes, unless an individual gives explicit permission

Security Planning: An Applied Approach 02/22/2024 24 Privacy Rule: Need-to-Know Access Washington Post, March 1, 1995 The 13-year-old daughter of a hospital employee took a list of patients’ names and phone numbers from the hospital when visiting her mother at work. As a joke, she contacted patients and told them they were diagnosed with HIV. CE/BA Employees should have access only to what is absolutely required as part of their jobs. What individuals should have access to PHI? What categories of PHI should individuals have access to? What conditions are required for access? How will Business Associates & Trading Partners be informed and controlled?

Security Planning: An Applied Approach 02/22/2024 25 Privacy Rule: Protections against Marketing Boston Globe, August 1, 2000 A patient at Brigham and Women’s Hospital in Boston learned that employees had accessed her medical record more than 200 times. CE must obtain permission before sending any marketing materials, with limited exceptions

Security Planning: An Applied Approach 02/22/2024 26 Privacy Rule: Establish Privacy Safeguards Required Shut or locked doors Keep voice down Clear desk policy Privacy curtains Password protection Auto screen savers Locked cabinets Paper shredders Not Required Soundproof rooms Redesign office space Private hospital rooms (semiprivate ok) OK for doctors to talk to nurses at nurse stations Safeguards should be REASONABLE

Security Planning: An Applied Approach 02/22/2024 27 Privacy Rule: Employee Training & Accountability New York Times, Jan. 19, 2002 Eli Lilly and Co. inadvertently revealed over 600 patient e-mail addresses when it sent an all message to every individual registered to receive reminders about taking Prozac. Each CE organization shall name one person who is accountable for Privacy Rule compliance Each employee, volunteer, contractor shall be trained in privacy policies and procedures Full and Part-time
Security Planning: An Applied Approach 02/22/2024 28 Privacy Rule: Individual Privacy Rights Patients have the right to: See or obtain copies of medical information (except for psychotherapy notes) Request correction to health record Receive a Notice of Privacy Practices Request restrictions as to who can see PHI Request specific method of contact for sake of privacy Know who has accessed PHI File a complaint if their rights have been violated Allow and withdraw authorizations for use and disclosure CE must: Respond to requests within 30 days May extend delay with notice for another 30 days Keep records of how PHI is disclosed

Security Planning: An Applied Approach 02/22/2024 29 Notice of Privacy Practices Privacy Requirements: NPP must be available when asked for NPP must be displayed prominently in the office Health Plan must provide upon enrollment Health Provider must provide on first service delivery Both must request written acknowledgment of receipt of NPP After change, revised NPP must be issued to clients within 60 days Electronic Requirements (if web page): Must be displayed prominently on web page Must be emailed to customers after a change in NPP

Security Planning: An Applied Approach 02/22/2024 30 Required & Permitted Disclosures Required Disclosure: Patient (or personal representative, e.g., parent, next of kin) Office of Civil Rights Enforcement: Investigates potential violations to Privacy Rule Permitted Disclosure: Minimum-Necessary PHI may be disclosed without authorization for: judicial proceedings, coroner/funeral, organ donation, approved research, military-related situations, governmentprovided benefits, worker’s compensation, domestic violence or abuse, some law enforcement activities ID must be verified by proof of identity/badge and documentation

Security Planning: An Applied Approach 02/22/2024 31 More Disclosures Routine Disclosure Disclosures that happen periodically should be addressed in policies, procedures, forms E.g.: Referral to another provider, school immunization, report communicable disease, medical transcription, births, deaths & other vital statistics Non-routine Disclosure CEs shall have reasonable criteria to review requests for non-routine PHI disclosures E.g., Research disclosures Incidental Disclosure CEs shall have reasonable safeguards E.g. Patient overhears advice given to another patient Accidental Disclosure Computer is stolen with PHI Disclosures must be tracked for six years

Security Planning: An Applied Approach 02/22/2024 32 Disclosures Requiring Authorization Research project (special conditions may allow) Person outside health care system Employer However, employer may require authorization for drug test before hiring Other insurance companies Health care provider not involved in patient’s health care Insurance company not paying patient’s claims Lawyer Patient should get copy of authorization

Security Planning: An Applied Approach 02/22/2024 33 Sample Authorization Form Disclosure Authorization Form Description of Information: Patient making authorized disclosure Person receiving information: Purpose of the disclosure: Authorization Expiration Date: Patient Signature Date: A form to revoke authorization must be completed to terminate authorization. Must be retained by CE for 6 years

Security Planning: An Applied Approach 02/22/2024 34 Implementing ‘Minimum Necessary’ Minimum necessary: Just enough info to accomplish the main purpose E.g., Send prescription for glasses to optician, not medical history Data Classification Sensitivity of information Type of treatment required Questions to Answer What parts of record can each user type access? How will we constrain access to implement view?

Security Planning: An Applied Approach 02/22/2024 35 Business Associate Contract (BAC) CEs must request BA to sign a BAC: BA will not disclose PHI BA is liable for damage due to disclosure or misuse BA will use safeguards to prevent misuse BA will report any security incident or violation of agreement BA will destroy or protect PHI upon termination of contract CE can terminate contract if violation occurs CE will provide BA copies of policies, procedures and materials for safeguarding Etc. BAs are equally liable as CEs, under HITECH Act

Security Planning: An Applied Approach 02/22/2024 36 HITECH: Health Information Technology for Economic and Clinical Health Act (2009) BA’s must follow the HIPAA Security Rule. BA’s are held to the same standard as CE’s. Health & Human Services (HHS) can: require BA’s to comply with HIPAA. enforce penalties on noncompliant BA’s.

Security Planning: An Applied Approach 02/22/2024 37 Violation of HIPAA Privacy Rule: WTHR Investigation Leads to Record 2.25M HIPAA Settlement, Indianapolis, IN, 2006: Reported that CVS was “throwing sensitive personal information in the trash” (e.g.: unredacted pill bottles, prescription instruction sheets, pharmacy receipts with credit card information and health insurance account numbers. After this, other CVS pharmacies were investigated and it was found that they also were improperly disposing of PHI. In the settlement CVS was required to: Create an information security program to protect personal information. Requires that they get an independent audit every 2 years until 2029. Pay 2.25 million to settle claims. CVS agreed to: Implement a security plan that complies with HIPAA’s Privacy Rule. Protect information during disposal. Develop employee training programs.

Security Planning: An Applied Approach 02/22/2024 38 Patient Record Obfuscation: De-identification de-identified records: not considered PHI: risk of re-identification must be statistically very small can be processed for research, public health and healthcare operations; not subject to breach status Information that must be removed includes: names (individual, employer and family members), geographical information (excluding state or permissible zip code manipulation), dates, contact information, social security and other account numbers, vehicle and device IDs, IP addresses, biometric or facial images, etc.

Security Planning: An Applied Approach 02/22/2024 39 Patient Record Obfuscation: Limited Data Set Re-identification method may use randomly-generated codes and code translation to re-identify a patient from a de-identified record. The algorithm cannot be guessably reversible; the mechanism to translate codes should be carefully controlled on a minimumnecessary basis. Limited data set: de-identified file with no guessable method of reversal. Advantage of limited data set: less opportunity for breach. When CE shares a limited data set with a BA, the CE must contract with the BA: the permissible uses of the limited data set limit the distribution of this data

Security Planning: An Applied Approach 02/22/2024 40 The HIPAA Security Rule Information Systems

Security Planning: An Applied Approach 02/22/2024 41 Security Rule Enforces Privacy Rule on Computers Privacy Rule With or w/o computer Protect PHI Security Rule With computer Protect EPHI Minimum Necessary Authentication & Access Control Accounting of Disclosures Unique Login Credentials Authentication Track modifications to EPHI: Who did what when?

Security Planning: An Applied Approach 02/22/2024 42 Security Vocabulary Asset: Diamonds Threat: Theft Vulnerability: Open door or windows Threat agent: Burglar Owner: Those accountable or who value the asset Risk: Danger to assets

Security Planning: An Applied Approach 02/22/2024 43 Security Rule Assures

Security Planning: An Applied Approach 02/22/2024 44 Security Services Authentication Access Control Data confidentiality Data integrity Data backup & recovery Nonrepudiation Cannot say it wasn’t you who sent or received data Risk Management

Security Planning: An Applied Approach 02/22/2024 45 Risk Management Risk assessment Policy & Procedures Maintenance Security Program Enforcement Audit logs, vulnerability assessments, audit for procedure adherence and control effectiveness Patches are applied to software Data is available, confidential, & integrity is protected

Security Planning: An Applied Approach 02/22/2024 46 Security Rule Standards Comprehensive Technology Neutral Administrative Controls Security Rule Small or Large Physical Controls Technical Controls Scalable Look to Best Practices for Technology Answers e.g. NIST Security Rule

Security Planning: An Applied Approach 02/22/2024 47 Three Areas of Safeguards Administrative: Administrative policies, procedures, and actions to implement and maintain security controls to protect EPHI, including risk mgmt, access control, contingency plans, incident response. Security Rule Physical: Protection of the physical access to terminals, laptops, servers, backup disks, memory, including viewing, access, maintenance and disposal. Technical: Protection using technology tools to protect EPHI, including logs, encryption, authentication

Security Planning: An Applied Approach 02/22/2024 48 Policies & Procedures Policies and Procedures MUST BE: Retained for 6 years after date of creation or last effect Available to workers responsible for them Must be updated regularly accommodating changes in environment & operations

Security Planning: An Applied Approach 02/22/2024 49 Security Rule Standard This is recommended Address this in some way Implement equivalent alternative measure . If it doesn’t apply, document well why not DO IT! We do this instead: .

Security Planning: An Applied Approach 02/22/2024 50 Administrative: Security Mgmt Process Risk Analysis: Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the CIA of EPHI held by the CE. R Risk Mgmt: Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with the Security Rule R Sanction Policy: Apply appropriate penalties against workforce members who fail to comply with the entity’s security policies and procedures R Info System Activity Review: Implement procedures to regularly review records of IS activity, such as audit logs, access reports, and security incident tracking reports R

Security Planning: An Applied Approach 02/22/2024 51 Security Mgmt Implications We will need an IT person to regularly check logs to be sure our system was not broken into The Sanction policy basically requires we all sign a confidentiality agreement and if someone breaks the rule, they could be fired. Risk assessment must be ‘accurate and thorough’ – that will be a challenge! And all are Rs Security Mgmt Process

Security Planning: An Applied Approach 02/22/2024 52 Administrative: Workforce Security Authorization and/or Supervision: Implement procedures A for the authorization and/or supervision of workforce members who work with EPHI or in locations where it might be accessed Workforce Clearance Procedure: Implement procedures to determine that the access of a workforce member to EPHI is appropriate A Termination Procedures: Implement procedures for terminating access to EPHI when the employment of a workforce member ends A

Security Planning: An Applied Approach 02/22/2024 53 Workforce Security Implications They are asking for checks and balances with supervision or authorization .We must have procedures to allocate authorization, periodically check authorization, and procedures to terminate someone Workforce Security We are a three person operation, can we get away with not doing this? Must we document our situation? These are As.

Security Planning: An Applied Approach 02/22/2024 54 Administrative: Information Access Mgmt Isolating Health Care Clearinghouse (CH) Function: If a health care CH is part of a larger organization, the CH operation must implement policies and procedures that protect the EPHI of the CH from unauthorized access by the larger organization R Access Authorization: Implement policies and procedure for granting access to EPHI – e.g., through access to a workstation, transaction, program, process, or other mechanism A Access Establishment & Modification: Implement policies and procedures that, based upon the entity’s access authorization policies, establish, document, review, and modify a user’s right of access to a workstation, transaction, program or process. A

Security Planning: An Applied Approach 02/22/2024 55 Info Access Mgmt Implications Isn’t this the same as the previous rule? It is an implementation: We must define a data owner for each major process .And then our IT people must define how they will grant access based upon the data owner’s decisions. Info Access Mgmt

Security Planning: An Applied Approach 02/22/2024 56 Administrative: Security Awareness & Training Security Reminders: Provide periodic security updates to members of the workforce A Protection from Malicious Software: Implement procedures for guarding against, detecting, and reporting malicious software A Login Monitoring: Implement procedures for monitoring login attempts and reporting discrepancies A Password Mgmt: Implement procedures for creating, changing and safeguarding passwords A What do you think these mean?

Security Planning: An Applied Approach 02/22/2024 57 Administrative: Contingency Plan Data Backup Plan: Establish and implement procedures to create and maintain retrievable exact copies of EPHI Disaster Recovery Plan: Establish procedures to restore any loss of data Emergency Mode Operation Plan: The emergency mode operation plan requires CEs to establish procedures to enable continuation of critical business processes, while maintaining the security of EPHI while operating in emergency mode Testing & Revision Procedure: Implement procedures for periodic testing and revision of contingency plans. Applications & Data Criticality Analysis: Assess the relative criticality of specific applications and data in support of other contingency plan components. R R R A A

Security Planning: An Applied Approach 02/22/2024 58 Administrative: One-Line Safeguards Assigned Security Responsibility: Identify the security R official who is responsible for the development and implementation of the policies and procedures required by this rule for the entity. Security Incident Procedures: Implement policies & procedures to address security incidents. Identify and respond to suspected or known security incidents; mitigate harmful effects of security incidents that are known to the CE; and document security incidents and their outcomes. R

Security Planning: An Applied Approach 02/22/2024 59 Administrative: More One-Line Safeguards Evaluation: Perform a periodic technical and nontechical evaluation, based initially upon the standards implemented under this rule and subsequently, in response to environmental or operations changes affecting the security of EPHI, that establishes the extent to which an entity’s security policies and procedures meet the requirements of this subpart R BA Contracts and Other Arrangements: A BA [may] create, receive, maintain, or transmit EPHI on the CE’s behalf only if the CE obtains satisfactory assurances that the BA will appropriately safeguard the information. R

Security Planning: An Applied Approach 02/22/2024 60 Info Access Mgmt Implications According to Evaluation, we must self-test or be certified on a regular basis, to be sure we follow the Security Rule That makes sense when technology changes, but I guess we have to do it periodically as well, since the world changes. We need to know who, what, when, where, why for incident response. Evaluation Who shall we name as our Security Manager?

Security Planning: An Applied Approach 02/22/2024 61 Physical Safeguards: Facility Access Controls Facility Access Controls: Implement policies and procedures to limit physical access to electronic info systems and areas where sensitive paper documents are stored and any facilities in which they are housed, while ensuring authorized access Contingency Operations Facility Security Plan Access Control & Validation Procedures Maintenance Records A A A A

Security Planning: An Applied Approach 02/22/2024 62 Physical Safeguards: Facility Access Control How will physical access be restricted to sensitive paper documents, terminals, server, backup copies, laptops, contingency operations in copy, view, or modify forms? How are visitors controlled from accessing PHI/EPHI? When repairs occur (to facility or systems) how will PHI/EPHI be safeguarded?

Security Planning: An Applied Approach 02/22/2024 63 Physical Safeguards: Workstations Workstation Use: Implement policies and R procedures that specify the proper functions to be performed, the manner in which those functions are to be performed, and the physical attributes of the surroundings of a specific workstation or class of workstation that can be used to access EPHI Workstation Security: Implement physical R safeguards for all workstations that can be used to access EPHI, to restrict access to authorized users

Security Planning: An Applied Approach 02/22/2024 64 Workstation Use and Security What functions will be performed on which workstations? How will workstation access be limited when the user leaves their station? How will theft of laptops be prevented? How will the workstations be positioned? What other physical safeguards (locked rooms, hoods) will be implemented to prevent shoulder surfing?

Security Planning: An Applied Approach 02/22/2024 65 Physical Safeguards: Device & Media Controls Device and Media Controls: Implement policies and procedures that govern the receipt and removal of hardware and electronic media and devices that contain EPHI into and out of a worksite or facility, and the movement of these items within the worksite or facility. Disposal Media Reuse Accountability Data Backup and Storage R R A A

Security Planning: An Applied Approach 02/22/2024 66 Device & Media Controls How will media be erased or damaged before disposal or reuse? Reformatting disk is not adequate, even for reuse How, when and where has EPHI been moved or transferred? Documentation is necessary How is a backup made and where/how stored?

Security Planning: An Applied Approach 02/22/2024 67 Technical Safeguards: Access Control Access Control: Implement technical policies and procedures for electronic info systems that maintain EPHI. These policies and procedures should contain access protocols that will establish and enforce the entity’s other access policies, and allow access only to those persons or software programs that have been granted access rights Unique User Identification R Emergency Access Procedure R Automatic Logoff Encryption and Decryption A A

Security Planning: An Applied Approach 02/22/2024 68 Technical Safeguards: Access Control How is each user uniquely identified to the system? How does authentication occur? In an emergency, what backup methods are used for authentication? How does automatic logoff occur after a period of inactivity? Which data is encrypted in storage and/or transmission?

Security Planning: An Applied Approach 02/22/2024 69 Technical Safeguards: Transmission Security Transmission Security: Implement technical security measures to guard against unauthorized access to EPHI that is being transmitted over an electronic communications network Integrity Controls A Encryption A

Security Planning: An Applied Approach 02/22/2024 70 Technical Safeguards: Transmission Security How are we sure that data is not modified or lost during transmission? What encryption techniques are used to protect the security of EPHI transmitted over a public network?

Security Planning: An Applied Approach 02/22/2024 71 Other Technical Safeguards Audit Controls: Implement hardware, software, and/or R procedural mechanisms that record and examine activity in information systems that contain or use EPHI Integrity: Implement policies and procedures to protect EPHI at rest, meaning stored on organizational systems and applications, from improper alteration or destruction. A Person or Entity Authentication: Implement procedures to verify that a person or entity seeking access to EPHI is the one claimed R

Security Planning: An Applied Approach 02/22/2024 72 Other Technical Safeguards For which devices will the logs be monitored? What log events should be archived for security purposes? How will potential attacks found in logs be recorded, reported, and acted upon? What techniques will be used to ensure stored data has not been modified (hashes, message digests?) What authentication mechanisms will be used to assure that approved entities (people or systems) are accessing EPHI?

Security Planning: An Applied Approach 02/22/2024 73 Question An example of a vulnerability is 1. Theft 2. Burglar 3. Open door 4. Diamonds

Security Planning: An Applied Approach 02/22/2024 74 Question 1. 2. 3. 4. Protected Health Information is: SSN, medical information Name, SSN, medical information Name, address, SSN, phone, medical information Medical information stored in a computer

Security Planning: An Applied Approach 02/22/2024 75 Question The Security Rule requires that: 1. Logs are monitored 2. An intrusion detection system is implemented 3. Cabinets containing PHI must be locked 4. Walls must be soundproof and all terminals outside of waiting room

Security Planning: An Applied Approach 02/22/2024 76 Question The Privacy Rule requires that: 1. Logs are monitored 2. An intrusion detection system is implemented 3. Cabinets containing PHI must be locked 4. Walls must be soundproof and all terminals outside of the waiting room

Security Planning: An Applied Approach 02/22/2024 77 Question The Addressable option for the Security Rule means: 1. Smaller organizations need not implement if they can justify it would be too expensive 2. HIPAA discusses alternative means to accomplish this, and the organization must select one 3. The CE must document how they accomplish this provision 4. This provision must be implemented or addressed in some way, although alternative implementations are allowed

Security Planning: An Applied Approach 02/22/2024 78 Summary HIPAA protects Protected Health information (PHI) Applicable to Covered Entities and their Business Associates In General: Privacy Rule covers Need-to-know, Disclosures, Notice of Privacy Practice, non-electronic privacy Security Rule covers Administrative, Physical and Technical Safeguards HITECH increases penalties for non-compliance HIPAA is an example of state-of-the-art Privacy and Security regulation Most of each chapter of this book is required for HIPAA

Security Planning: An Applied Approach 02/22/2024 79 Jamie Ramon MD Doctor Chris Ramon RD Dietician Terry Licensed Practicing Nurse HEALTH FIRST CASE STUDY Complying with HIPAA and HITECH Pat Software Consultant

Security Planning: An Applied Approach 02/22/2024 80 Case Study and Homework 1. Develop a procedure of how disclosures will work. 2. Create a prototype form for the Disclosure Authorization and Tracking 3. Develop evil user stories and security stories pertaining to disclosures. Add them to the Health First Database Security Plan. 4. Develop test case(s) to test your security stories. Add them to the Health First Database Security Plan 5. Reiterate through these steps as new ideas form. Note: This is an example of a simple procedure (numbered steps of actions to take).

Security Planning: An Applied Approach 02/22/2024 81 Step 1: Develop a Bullet-Proof Procedure Against Fraud Can you prepare a procedure that is nearly 100% social engineering fool-proof? A procedure is a numbered step-by-step description of what an employee shall do when confronted with a request for Disclosure. Write the procedure and add it to the Security Plan. Add your finalized form after your procedure.

Security Planning: An Applied Approach 02/22/2024 82 Step 2: Develop form for Disclosure authorization & tracking A manual disclosure form must be computerized for the database. What administrative security controls should be added to this form to ensure social engineering did not occur?

Security Planning: An Applied Approach 02/22/2024 83 (Step 2) Creating A Form Patient Appointment Date 9/5/2010 Doctor J. Ramon Time Patient name (Last, First): Patient AM 8:00 8:15 Stuart, John Winfrey, Oprah 8:30 8:45 9:00 9:15 Sub mit 9:30 To develop a form, you may use PowerPoint or Word or other tools Professional software development tools: Visual Studios, etc.

Security Planning: An Applied Approach 02/22/2024 84 Disclosure Types to Accommodate Required Disclosure: Patients and the Office of Civil Rights Enforcement are allowed to request patient medical information. Permitted Disclosure: PHI may be disclosed without authorization for: judicial proceedings, coroner/funeral, organ donation, approved research, militaryrelated situations, government-provided benefits, worker’s compensation, and domestic violence or abuse. For these types of disclosures, ID must be verified by proof of identity/badge and documentation, and the minimum necessary information should be provided. Routine Disclosure: These periodic disclosures include: referral to another provider, school immunization, communicable disease report, and medical transcription. These disclosures should be addressed by defining detailed procedures and forms.

Security Planning: An Applied Approach 02/22/2024 85 Step 3: Develop Evil User Stories & Security Stories Evil User Stories As a criminal hacker, I access local databases through a mobile laptop onsite. Security Stories As a security administrator, I ensure local area networks have high quality recent encryption with strong security logins As a criminal hacker, I social engineer As an employee, I do not follow links an email contact, then attack using a or open attachments from anyone social engineering attack. other than fellow known employees. As a criminal hacker, I install malware ? on logged in machines that are left unattended. As a criminal hacker, I take notes ? from logged in machines with proprietary information on them.

Security Planning: An Applied Approach 02/22/2024 86 (Step 3) Add stories to Health First Database Security Plan Evil User Story Section: Patient Management As a busy nurse, I sometimes do not provide all required information or enter incorrect information Corresponding Security Story Test Case # and Name As a database system, I ensure Test case 1: Create that all required fields are Patient Information included and that some fields are checked for type (zip, phone) and accurate options (sex, insurance)
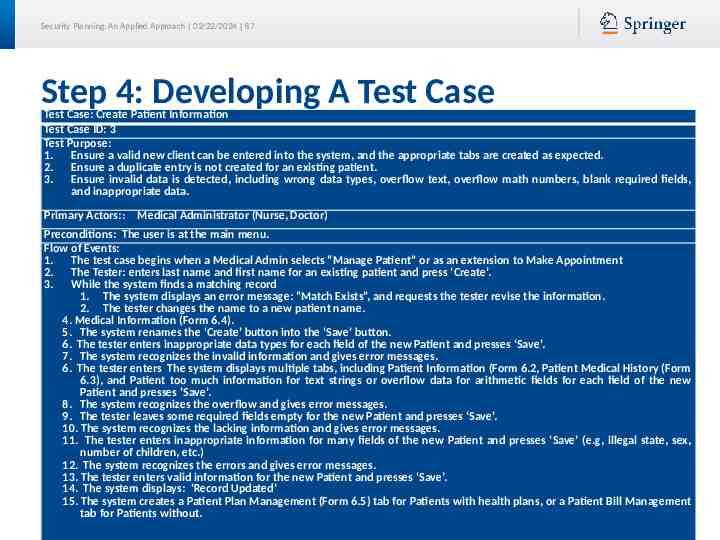
Security Planning: An Applied Approach 02/22/2024 87 Step 4: Developing A Test Case Test Case: Create Patient Information Test Case ID: 3 Test Purpose: 1. Ensure a valid new client can be entered into the system, and the appropriate tabs are created as expected. 2. Ensure a duplicate entry is not created for an existing patient. 3. Ensure invalid data is detected, including wrong data types, overflow text, overflow math numbers, blank required fields, and inappropriate data. Primary Actors:: Medical Administrator (Nurse, Doctor) Preconditions: The user is at the main menu. Flow of Events: 1. The test case begins when a Medical Admin selects “Manage Patient” or as an extension to Make Appointment 2. The Tester: enters last name and first name for an existing patient and press ‘Create’. 3. While the system finds a matching record 1. The system displays an error message: “Match Exists”, and requests the tester revise the information. 2. The tester changes the name to a new patient name. 4. Medical Information (Form 6.4). 5. The system renames the ‘Create’ button into the ‘Save’ button. 6. The tester enters inappropriate data types for each field of the new Patient and presses ‘Save’. 7. The system recognizes the invalid information and gives error messages. 6. The tester enters The system displays multiple tabs, including Patient Information (Form 6.2, Patient Medical History (Form 6.3), and Patient too much information for text strings or overflow data for arithmetic fields for each field of the new Patient and presses ‘Save’. 8. The system recognizes the overflow and gives error messages. 9. The tester leaves some required fields empty for the new Patient and presses ‘Save’. 10. The system recognizes the lacking information and gives error messages. 11. The tester enters inappropriate information for many fields of the new Patient and presses ‘Save’ (e.g, illegal state, sex, number of children, etc.) 12. The system recognizes the errors and gives error messages. 13. The tester enters valid information for the new Patient and presses ‘Save’. 14. The system displays: ‘Record Updated’ 15. The system creates a Patient Plan Management (Form 6.5) tab for Patients with health plans, or a Patient Bill Management tab for Patients without.

Security Planning: An Applied Approach 02/22/2024 88 (Step 4) Developing a Test Case Test Case Example Test Case Notes Test Case: Create Patient Information Test Case: Verb Adjective Noun Test Case ID: 3 Test Purpose: This lists the security goals of the test Test Purpose: Ensure a valid new client can be entered into the system, and the appropriate tabs are created as expected. Ensure a duplicate entry is not created for an existing patient. Ensure invalid data is detected, including wrong data types, overflow text, overflow math numbers, blank required fields, and inappropriate data. Primary Actors: Medical Administrator (Nurse, Doctor) Preconditions: The user is at the main menu. Primary Actors: Who logically executes the use case (but not necessarily the test case). Preconditions: How do we get to this test?

Security Planning: An Applied Approach 02/22/2024 89 (Step 4) Developing a Test Case Test Case Example Test Case Notes Flow of Events: 1. The test case begins when a Medical Admin selects “Manage Patient” or as an extension to Make Appointment 2. The Tester: enters last name and first name for an existing patient and press ‘Create’. 3. While the system finds a matching record Medical Information (Form 6.4). 1. The system displays an error message: “Match Exists”, and requests the tester revise the information. 2. The tester changes the name to a new patient name. 4. The system renames the ‘Create’ button into the ‘Save’ button. 5. The tester enters inappropriate data types for each field of the new Patient and presses ‘Save’. 6. The system recognizes the invalid information and gives error messages. 7. The tester enters The system displays multiple tabs, including Patient Information (Form 6.2, Patient Medical History (Form 6.3), and Patient too much information for text strings or overflow data for arithmetic fields for each field of the new Patient and presses ‘Save’. Start with Flow of Events 1. The test case begins when 2. The tester 3. The system 4. The tester 5. The system

Security Planning: An Applied Approach 02/22/2024 90 Case Study and Homework 1. Develop a procedure of how disclosures will work. 2. Create a prototype form for the Disclosure Authorization and Tracking 3. Develop evil user stories and security stories pertaining to disclosures. Add them to the Health First Database Security Plan. 4. Develop test case(s) to test your security stories. Add them to the Health First Database Security Plan 5. Reiterate through these steps as new ideas form. Note: This is an example of a simple procedure (numbered steps of actions to take).