PARIS & Identity Theft JESSICA BRINKS I P L O C AT O R S P E C I A
23 Slides905.56 KB

PARIS & Identity Theft JESSICA BRINKS I P L O C AT O R S P E C I A L I S T M I C H I G A N D E PA R T M E N T O F H E A LT H & H U M A N S E R V I C E S O F F I C E O F I N S P E C T O R G E N E R A L , I N V E S T I G AT I V E A N A LY T I C S U N I T

Identity Theft Defined The theft or misuse of an individual’s personal identifying information, which may include name, date of birth, social security number, and other identifying factors
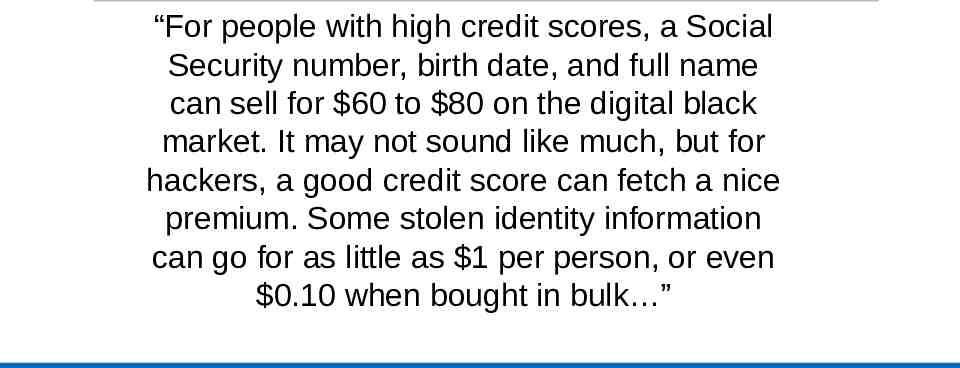
“For people with high credit scores, a Social Security number, birth date, and full name can sell for 60 to 80 on the digital black market. It may not sound like much, but for hackers, a good credit score can fetch a nice premium. Some stolen identity information can go for as little as 1 per person, or even 0.10 when bought in bulk ”
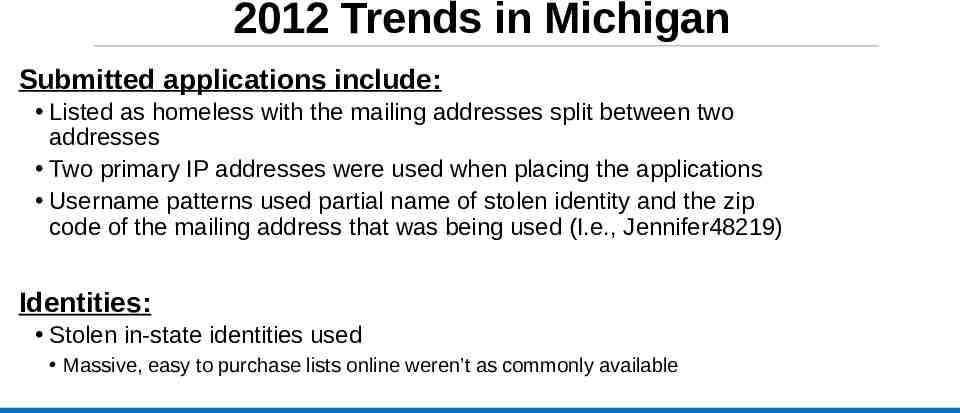
2012 Trends in Michigan Submitted applications include: Listed as homeless with the mailing addresses split between two addresses Two primary IP addresses were used when placing the applications Username patterns used partial name of stolen identity and the zip code of the mailing address that was being used (I.e., Jennifer48219) Identities: Stolen in-state identities used Massive, easy to purchase lists online weren’t as commonly available
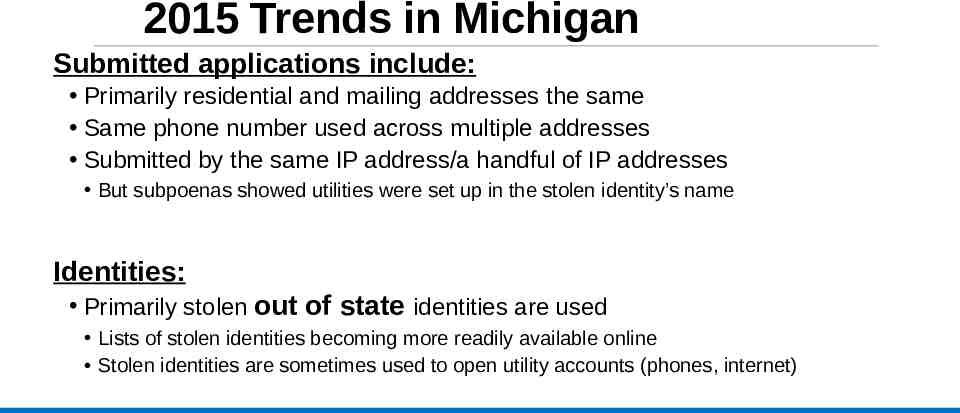
2015 Trends in Michigan Submitted applications include: Primarily residential and mailing addresses the same Same phone number used across multiple addresses Submitted by the same IP address/a handful of IP addresses But subpoenas showed utilities were set up in the stolen identity’s name Identities: Primarily stolen out of state identities are used Lists of stolen identities becoming more readily available online Stolen identities are sometimes used to open utility accounts (phones, internet)
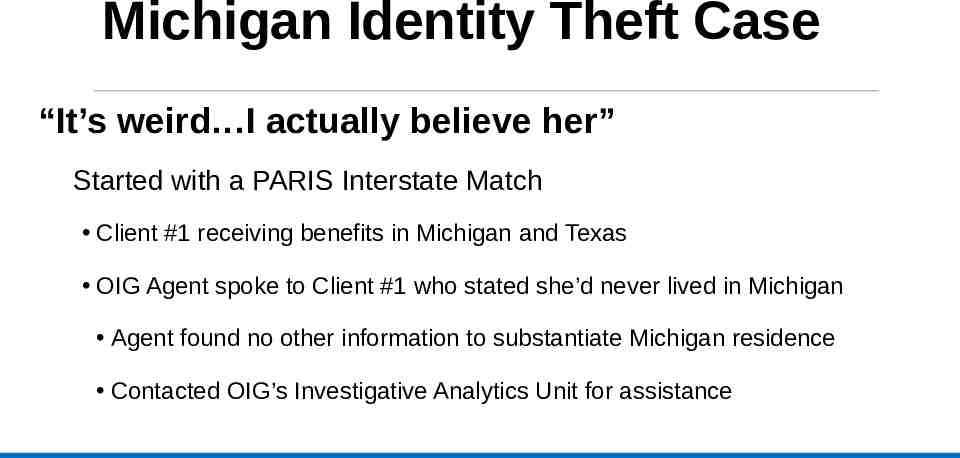
Michigan Identity Theft Case “It’s weird I actually believe her” Started with a PARIS Interstate Match Client #1 receiving benefits in Michigan and Texas OIG Agent spoke to Client #1 who stated she’d never lived in Michigan Agent found no other information to substantiate Michigan residence Contacted OIG’s Investigative Analytics Unit for assistance
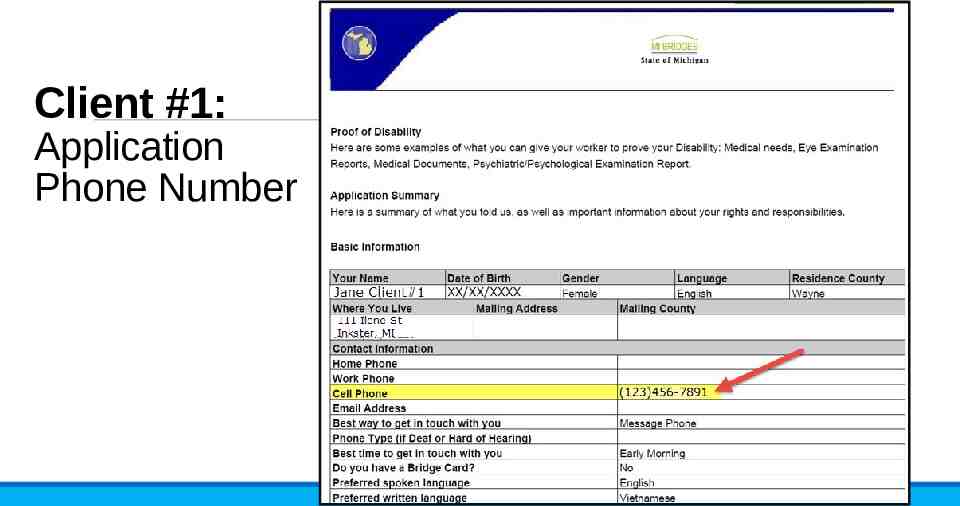
Client #1: Application Phone Number
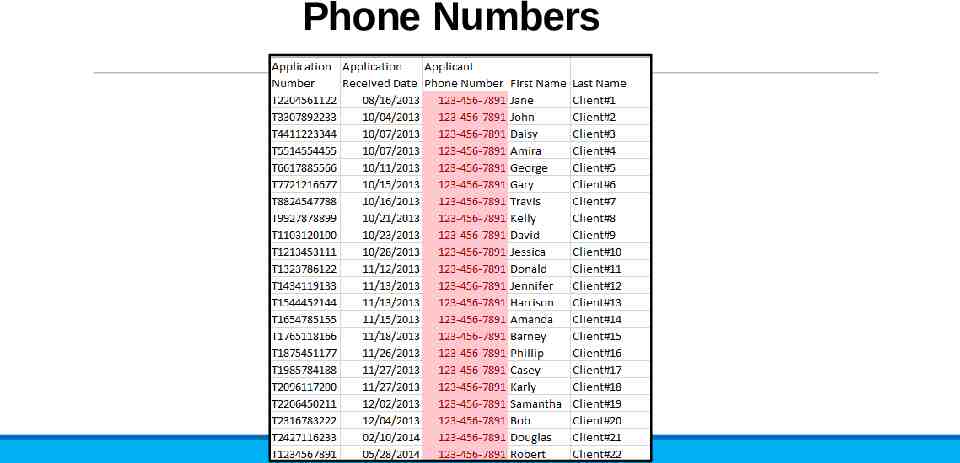
Phone Numbers
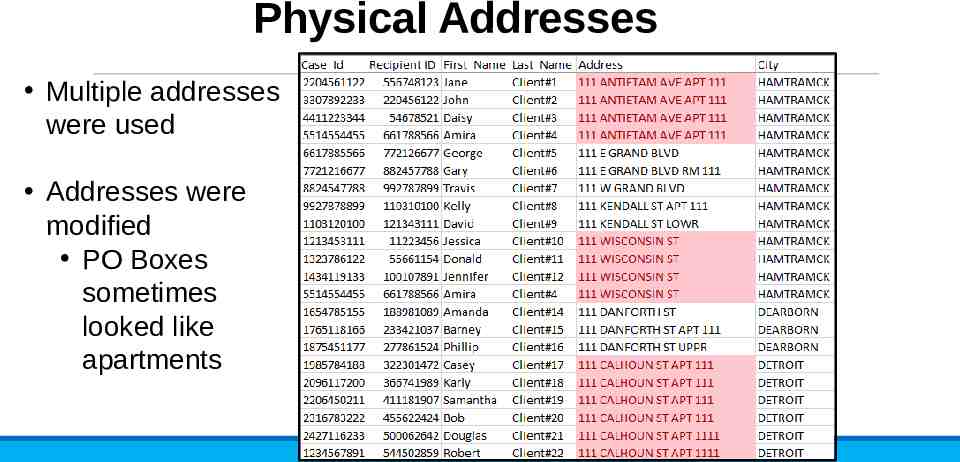
Physical Addresses Multiple addresses were used Addresses were modified PO Boxes sometimes looked like apartments
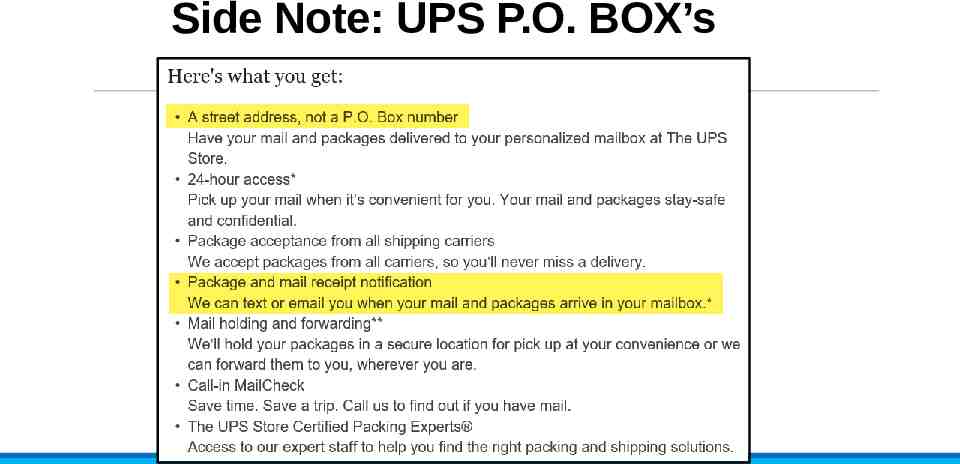
Side Note: UPS P.O. BOX’s
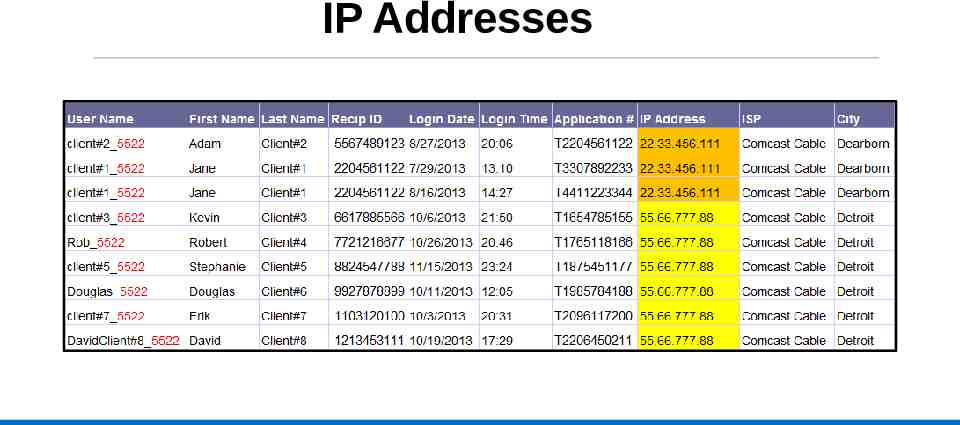
IP Addresses
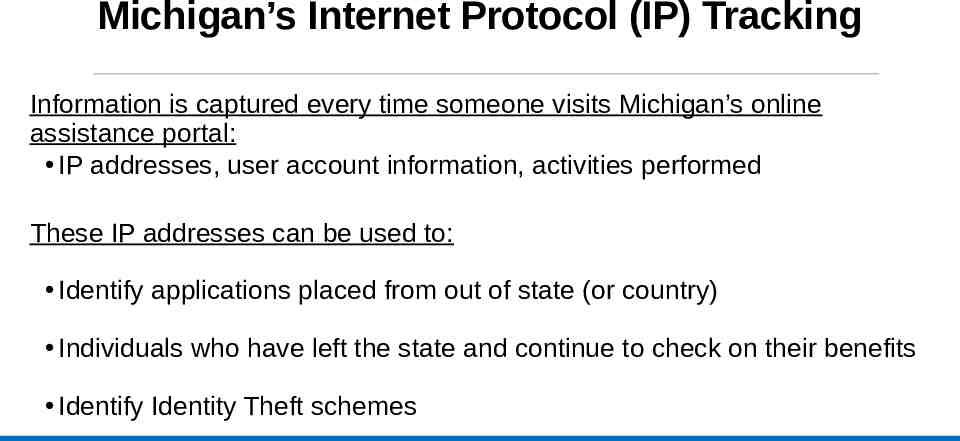
Michigan’s Internet Protocol (IP) Tracking Information is captured every time someone visits Michigan’s online assistance portal: IP addresses, user account information, activities performed These IP addresses can be used to: Identify applications placed from out of state (or country) Individuals who have left the state and continue to check on their benefits Identify Identity Theft schemes
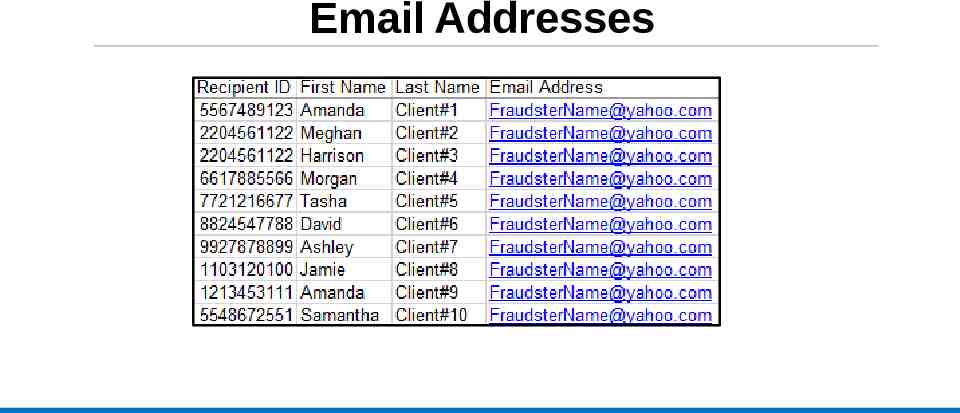
Email Addresses

Initial Findings Over 120 recipients were found to be linked via a combination of: Phone numbers Email addresses IP addresses Physical addresses MI Bridges Username patterns

PARIS Matches Of the 120 recipients, many matched on the PARIS Interstate Match: Alaska California District of Columbia Florida New Jersey New Mexico North Carolina Ohio Pennsylvania Texas Vermont

A Joint Operation Partnered with: USDA-OIG United States Department of Agriculture-Office of Inspector General AUSA Assistant United States Attorney

Findings of the Search Warrant List of 700 identities Names DOBs SSNs State of residence Employment information Banking information Background checks EBT cards

The Damages 300 Food Assistance applications using stolen identities 518,000 in Total Fraud
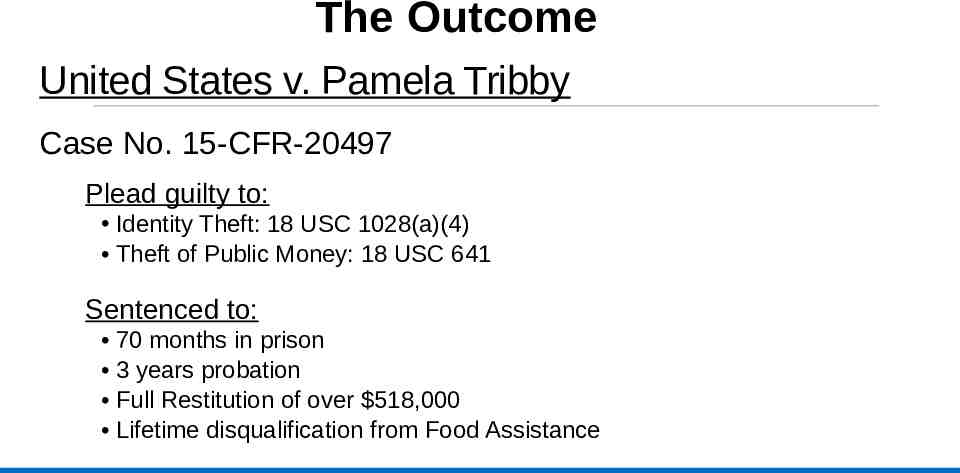
The Outcome United States v. Pamela Tribby Case No. 15-CFR-20497 Plead guilty to: Identity Theft: 18 USC 1028(a)(4) Theft of Public Money: 18 USC 641 Sentenced to: 70 months in prison 3 years probation Full Restitution of over 518,000 Lifetime disqualification from Food Assistance

Current Trends in Michigan Submitted applications include: Random residential addresses with groupings of the same mailing addresses Groupings of the same phone number across multiple addresses Groupings submitted by the same IP address IP addresses may show a proxy server or VPN When applications get approved, cases ride until they are closed fraudulently, or up for recertification. No recertifications are completed and cases close. Identities are reused 3-6 months later to reapply. Identities: Primarily stolen out of state identities are used Smaller chance of in-state identities being used as these are typically caught by wage matches, or the individual may already have an open assistance case Stolen identities are being used to open utility accounts (phones, internet)

PARIS and Identity Theft Stolen out of state identities are common: If the individual is on assistance in the other state, you’ll likely see a PARIS match You now have a contact point in the other state, which means it’s easier to contact your victim Stolen identities may be used for many things, including opening utilities. Public record data may show both fraudster and victim information
PARIS With a Twist Fraudster traveling between two states to buy Michigan identities to open SNAP cases in State 2 Using PARIS data, Michigan OIG identified additional identities being used in State 2 Multiple Michigan identities were used at the same address in State 2 Michigan OIG is currently assisting State 2 to apprehend Fraudster
Jessica Brinks IP Locator Specialist Michigan Department of Health & Human Services Office of Inspector General, Investigative Analytics Unit [email protected]






