BRK2258 Keep your OneDrive and SharePoint Content Safe Navjot Virk
46 Slides2.96 MB

BRK2258 Keep your OneDrive and SharePoint Content Safe Navjot Virk Principal Group Program Manager
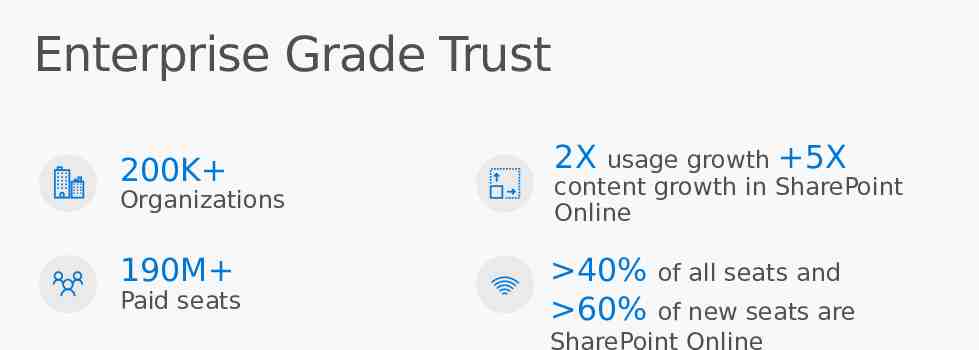
Enterprise Grade Trust 200K 2X 190M 40% 60% Organizations Paid seats usage growth 5X content growth in SharePoint Online of all seats and of new seats are SharePoint Online

Guiding principles Your data remains yours Secure and compliant cloud platform No security without usability Customizable for your needs
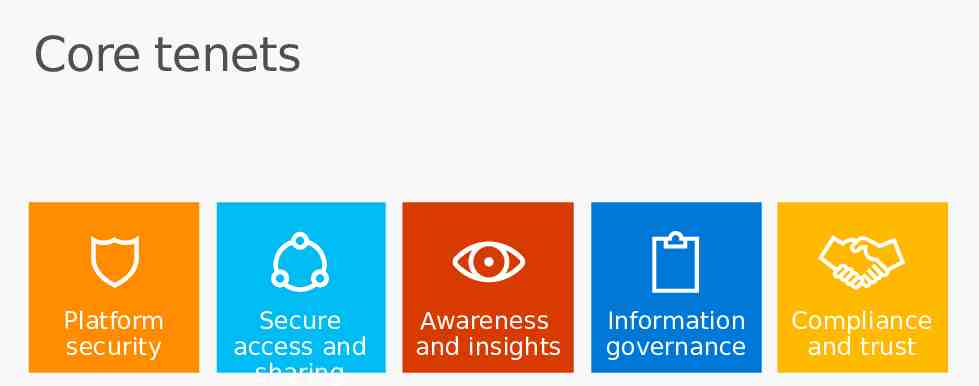
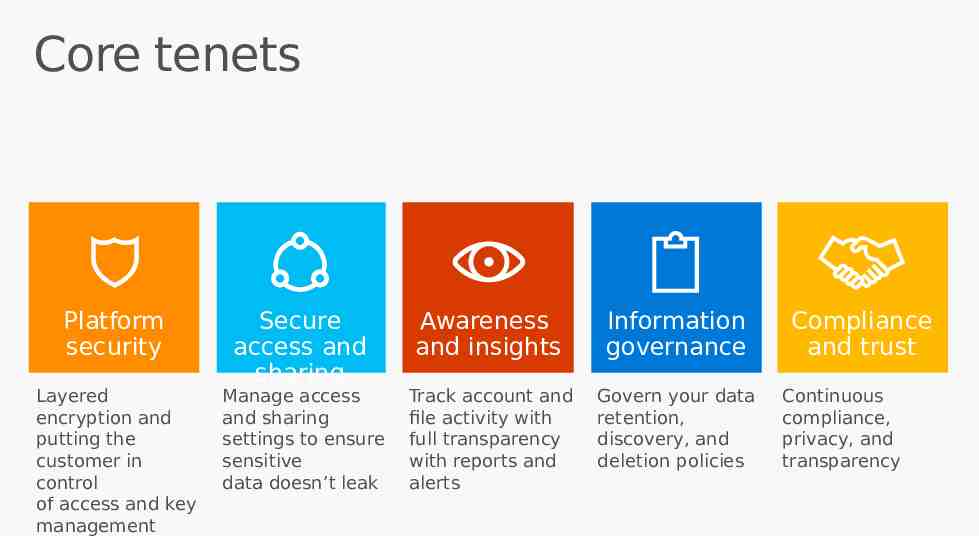
Core tenets Platform security Secure access and sharing Awareness and insights Information governance Compliance and trust

Physical and logical security Encryption at rest and in transit PLATFORM SECURITY Putting the customer at ease and in control Customer lockbox Bring your own key

Physical security Limited datacenter access Restricted to essential personnel only Multiple factors of authentication including smart cards and biometrics On-premise security officers, motion sensors, video surveillance Intrusion detection alerts include anomalous activity by datacenter engineers Fault-tolerant and highly-available Data is stored in at least two datacenters within your region Mitigates the impact of a natural disaster or service-impacting outage Protects data integrity and availability while respecting regional data locality

Logical security Built in protection Built in antivirus and antispam protection Advanced threat protection to safeguard against external threats Operational Security Automation of configuration, operations, and deployment Administrator access to your files is strictly controlled. A combination of port scanning, perimeter vulnerability scanning, and intrusion detection prevent or detect any malicious access. Customer Lockbox Cyber Crime Prevention Unit Dedicated threat management teams to anticipate, prevent, and mitigate malicious access.

Encryption at rest and in transit Encryption in transit Encrypted in transit between client and service and within service data centers Volume encryption at rest BitLocker encryption protects drives where content is stored Per-file encryption at rest Contents of each file encrypted with a unique key Large files are stored in parts with a unique key per par File contents and encryption key are stored separately

Customer encryption Azure Rights Management (Azure RMS) Use Azure RMS to encrypt your secret data before uploading Works across phones, tablets, and PCs Information protected both within and outside organization Key management options By default, Azure RMS generates and manages key Coming soon – you have complete control over your tenant key
Customer lockbox No standing access to customer content Engineer accounts have no access to content Engineers do not use service account credentials to perform tasks Intrusion detection monitors content access and service account use Customer approval for any access to their content Access granted only after approval Time bound access only All activity logged and available for auditing
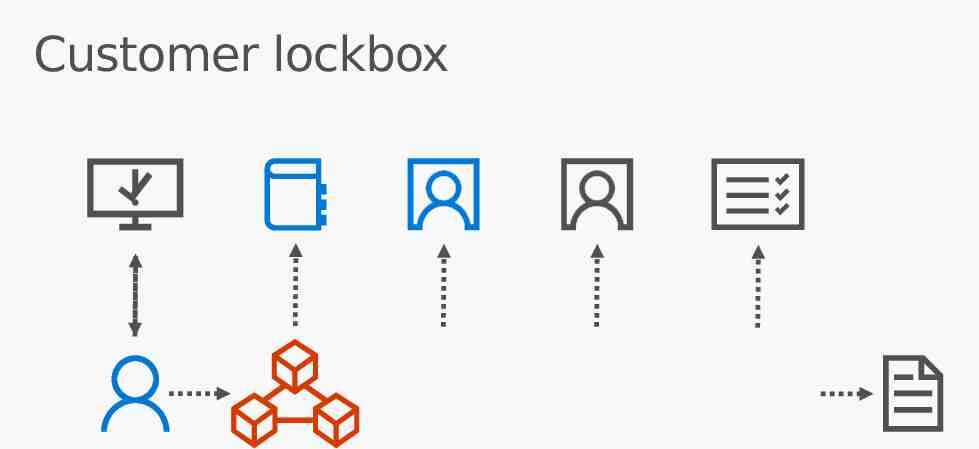
Customer lockbox

Demo – Lockbox
Bring your own key Customer-managed “master key” Master key is used to encrypt/decrypt per-file encryption keys If it is removed or access is revoked, SharePoint Online can no longer decrypt your content Does not limit/restrict SharePoint Online functionality when enabled You control the master key You upload it to Azure Key Vault and grant access to the Office 365 service You can remove it or revoke access to it at any time
Conditional access policies SECURE ACCESS AND SHARING Access to the right data by the right people Sharing controls
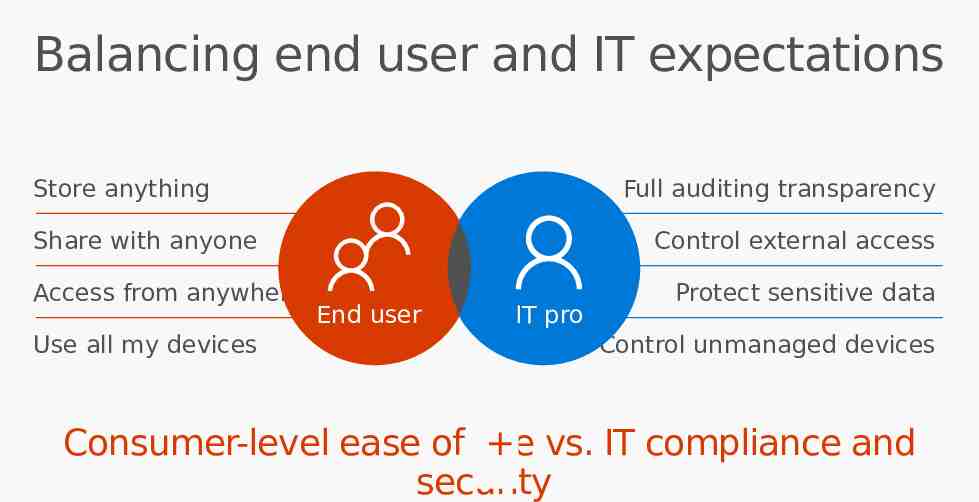
Balancing end user and IT expectations Store anything Full auditing transparency Share with anyone Access from anywhere Use all my devices Control external access End user IT pro Protect sensitive data Control unmanaged devices Consumer-level ease of use vs. IT compliance and security
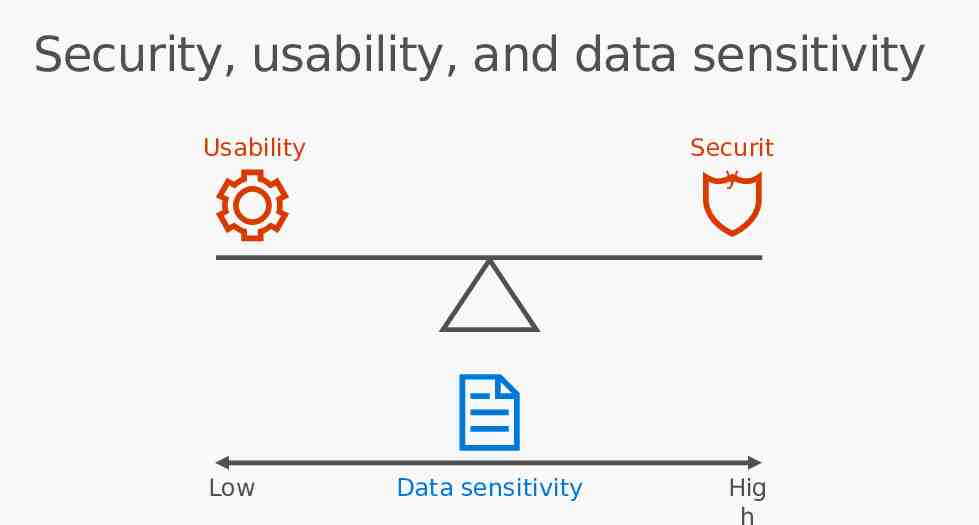
Security, usability, and data sensitivity Usability Low Securit y Data sensitivity Hig h
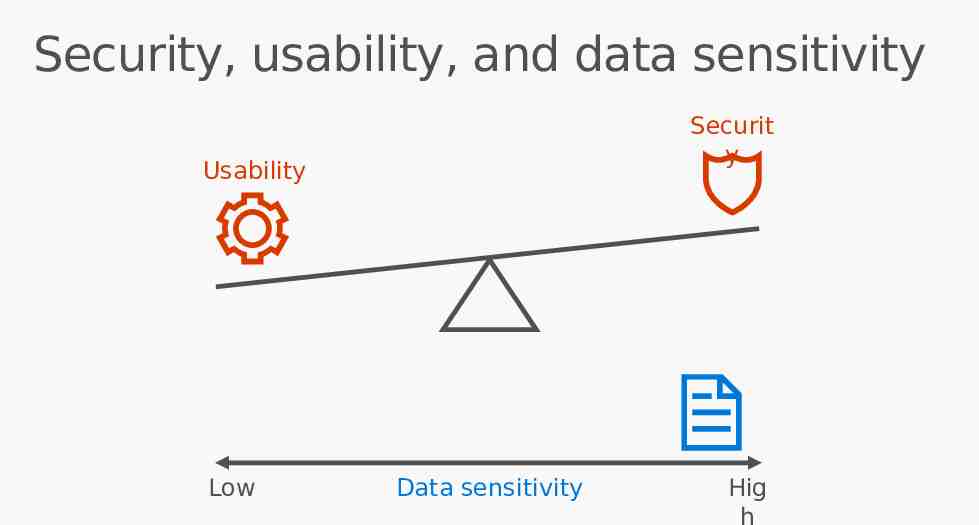
Security, usability, and data sensitivity Securit y Usability Low Data sensitivity Hig h
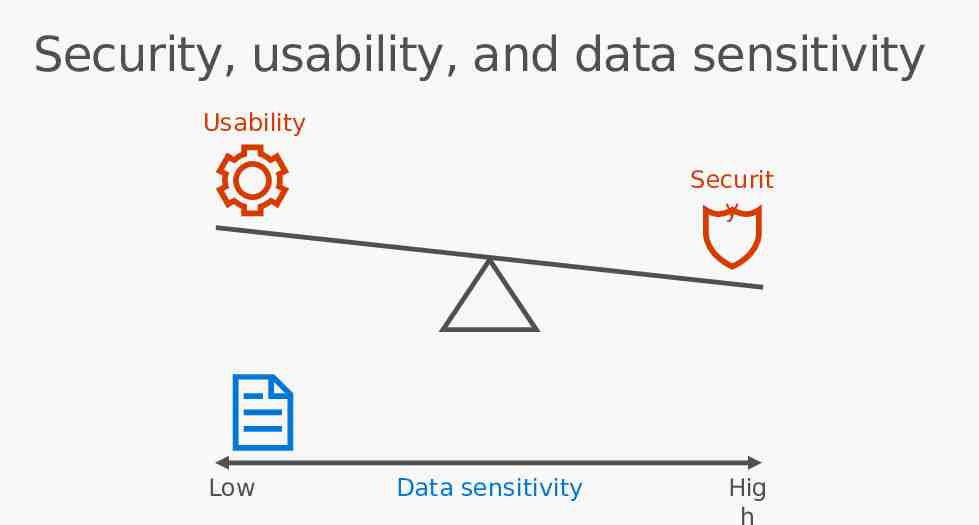
Security, usability, and data sensitivity Usability Securit y Low Data sensitivity Hig h

Conditional access pivots 5 Key Pivots of Control USER DEVICE APPLICATION LOCATION DATA SENSITIVITY

Users, device and applications Manage Users AAD to manage users and groups Enforce strong passwords Multi factor authentication Conditional access based on users and groups Revoke suspicious user sessions Manage device and application access Integrated device and app management through Microsoft InTune Prevent or downgrade access on unmanaged and non-compliant devices Control apps and their level of access on both managed and unmanaged devices Integration with other EMM providers such as MobileIron, AirWatch etc.

Location and data sensitivity Manage location of access Restrict access to specific IP ranges Automatically revoke access when user moves to untrusted location Manage access to sensitive data Office 365 Data Loss Prevention (DLP) policies protect sensitive data Prevent sharing of sensitive data with external users or within the organization
Sharing controls Manage external sharing in your organization Restrict who can share with whom Control what data can be shared with external users Restrict what external users can do

Demo – Secure Access and Sharing
Auditing Reporting AWARENESS Alerting AND INSIGHTS Full transparency and insight into your users and data
Auditing and reporting Auditing Every user action recorded for full audit trail Custom alerts to get notified when a specific event occurs Office 365 Management Activity API to export audit logs Reporting Full usage dashboard to monitor all Office 365 services Tenant level and per user reporting

Demo – Auditing and Reporting

Demo – Session Revocation

Data retention policies INFORMATION GOVERNANCE Ensuring you can manage your data lifecycle and discovery eDiscovery and legal hold
Data retention Meet your organizational or industry compliance requirements Set global retention policies on all content in Office 365 or granular policies on specific users or content Granular content policies based on custom tags, last modified date, or created date Preserve and delete content on customized schedule

Demo – Retention Policies

eDiscovery and legal hold Find, preserve, analyze, and package data for legal investigation Delegate control to specialists such as a compliance officers or HR Single experience for searching and preserving across Office 365 No user action is required, all process performed in the
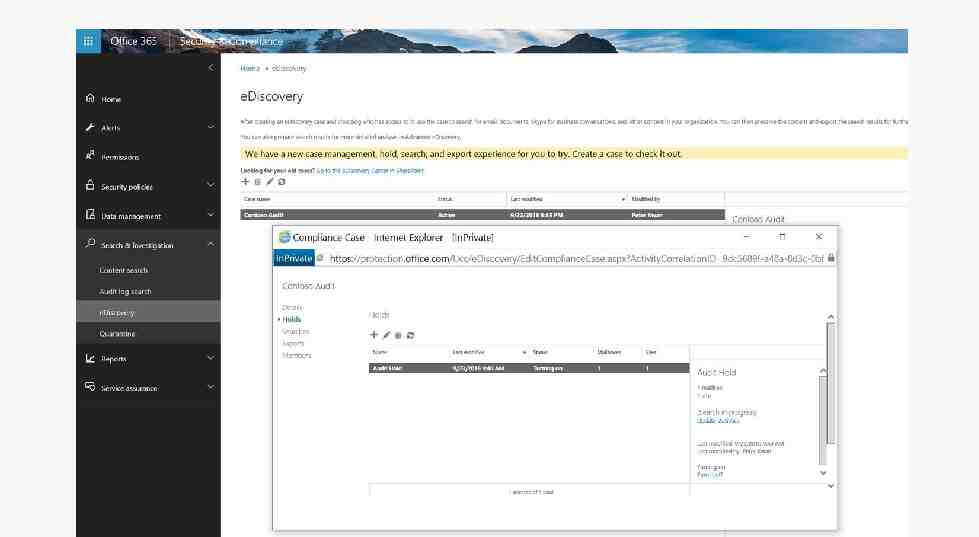
Proactive continuous compliance COMPLIANCE AND TRUST Privacy and transparency

Proactive and continuous compliance Independent validation of security practices Assessment of whether Office 365 complies with regulatory and security standards Dedicated engineering team for compliance and standards within Office 365 Internal compliance framework includes over 900 controls that map to external standards Product teams leverage internal controls to build functionality that respects regulatory constraints Compliance is a fundamental service offering We pursue accreditation as part of our holistic approach to security and privacy We implement features that help your organization remain compliant Largest compliance portfolio in the industry

Compliance Certification s

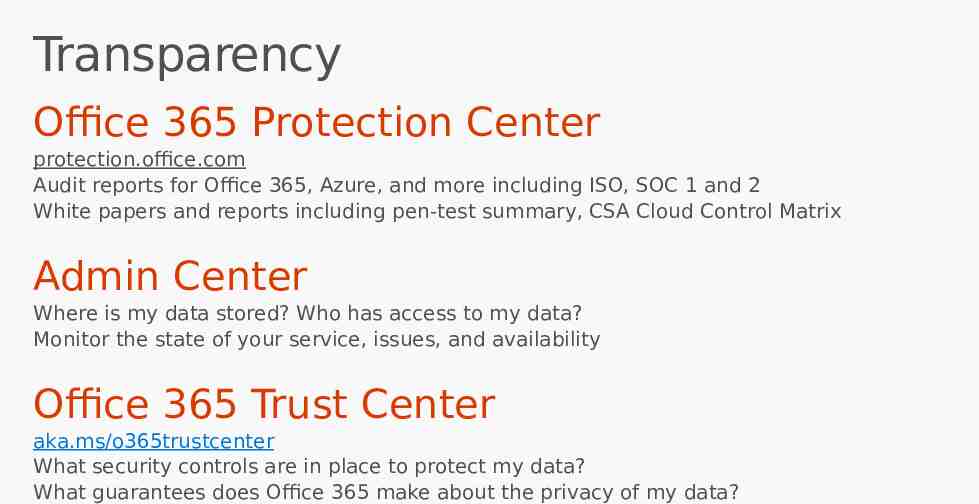
Transparency Office 365 Protection Center protection.office.com Audit reports for Office 365, Azure, and more including ISO, SOC 1 and 2 White papers and reports including pen-test summary, CSA Cloud Control Matrix Admin Center Where is my data stored? Who has access to my data? Monitor the state of your service, issues, and availability Office 365 Trust Center aka.ms/o365trustcenter What security controls are in place to protect my data? What guarantees does Office 365 make about the privacy of my data?
Privacy Custody, not ownership You are the owner; Microsoft is the “custodian” or “processor” of your data If you leave the service, you can take your data with you We do not mine your data for advertising purposes Security for the sake of privacy The privacy of your data is the driving force behind our security measures SharePoint sites and libraries are set to “private” by default OneDrive are not shared until the user explicitly takes a sharing action Transparency about law enforcement requests Redirect government requests to customer whenever possible

Summary
Core tenets Platform security Layered encryption and putting the customer in control of access and key management Secure access and sharing Manage access and sharing settings to ensure sensitive data doesn’t leak Awareness and insights Information governance Track account and file activity with full transparency with reports and alerts Govern your data retention, discovery, and deletion policies Compliance and trust Continuous compliance, privacy, and transparency

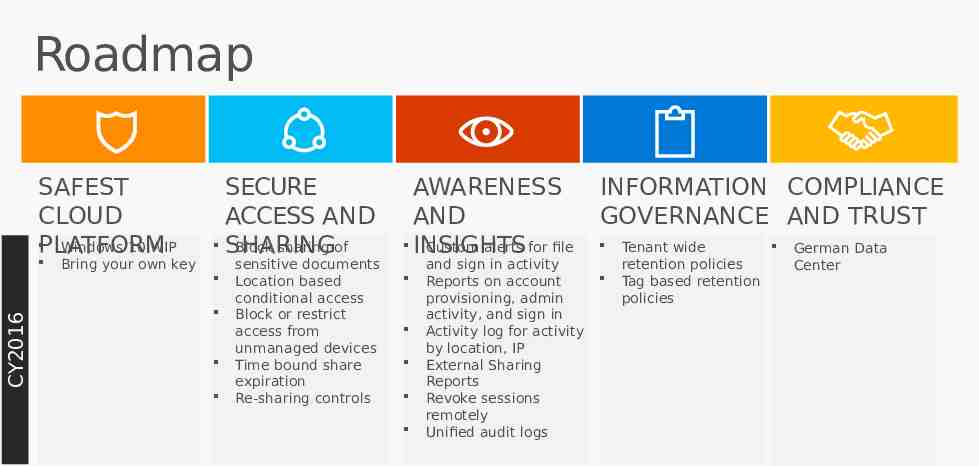
Roadmap SAFEST CLOUD PLATFORM Windows 10 WIP CY2016 Bring your own key SECURE ACCESS AND SHARING Block sharing of AWARENESS AND INSIGHTS Custom alerts for file sensitive documents Location based conditional access Block or restrict access from unmanaged devices Time bound share expiration Re-sharing controls and sign in activity Reports on account provisioning, admin activity, and sign in Activity log for activity by location, IP External Sharing Reports Revoke sessions remotely Unified audit logs INFORMATION COMPLIANCE GOVERNANCE AND TRUST Tenant wide retention policies Tag based retention policies German Data Center
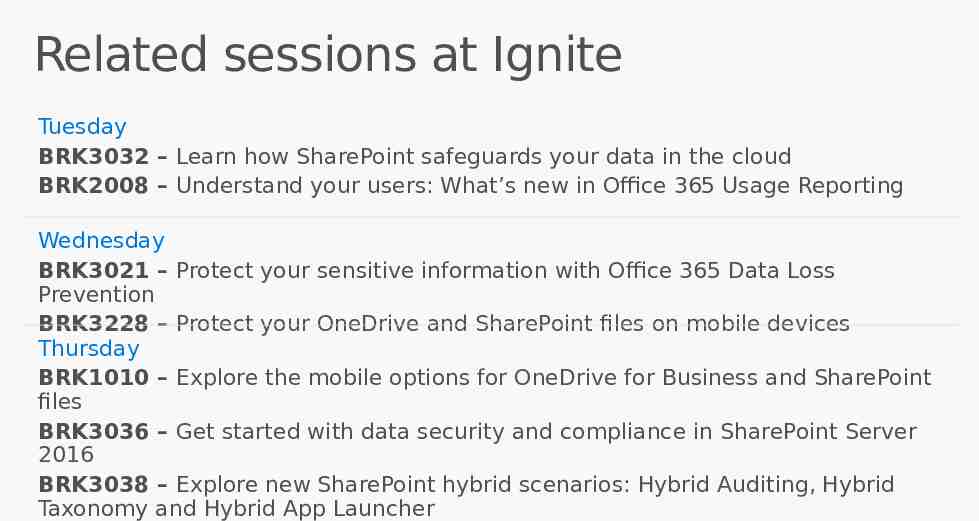
Related sessions at Ignite Tuesday BRK3032 – Learn how SharePoint safeguards your data in the cloud BRK2008 – Understand your users: What’s new in Office 365 Usage Reporting Wednesday BRK3021 – Protect your sensitive information with Office 365 Data Loss Prevention BRK3228 – Protect your OneDrive and SharePoint files on mobile devices Thursday BRK1010 – Explore the mobile options for OneDrive for Business and SharePoint files BRK3036 – Get started with data security and compliance in SharePoint Server 2016 BRK3038 – Explore new SharePoint hybrid scenarios: Hybrid Auditing, Hybrid Taxonomy and Hybrid App Launcher
Deploy, ramp-up on new services and onboard new users with Microsoft FastTrack: http://fasttrack.microsoft.c om/
Join the Microsoft Tech Community to collaborate, share, and learn from the experts: http://techcommunity.microsof t.com

Please evaluate this session Your feedback is important to us! From your PC or Tablet visit MyIgnite at http://myignite.microsoft.com From your phone download and use the Ignite Mobile App by scanning the QR code above or visiting https://aka.ms/ignite.mobileapp

2016 Microsoft Corporation. All rights reserved.