Applications of Feather-Weight Virtual Machines (FVMs) Hadi Salimi
16 Slides115.65 KB

Applications of Feather-Weight Virtual Machines (FVMs) Hadi Salimi Distributed Systems Lab, School of Computer Engineering, Iran University of Science and Technology, [email protected]

Motivation Fault-tolerant and intrusion-tolerant systems The ability to test-drive un-trusted programs in a realistic environment No need to keep permanent damages. Virtualization need is a perfect fit to meet this

Requirements Such trial operations need to be invoked frequently. Invoking a virtual execution environment must be extremely low-overhead The FVM project aims at developing an OS level virtualization technique on Microsoft Windows.

OS-Level Virtualization Virtualization is to partition lower-level system resources to present multiple operating environments at a higher level. Normally OS-level virtualization means partitioning system resources at the system call interface. The key idea behind FVM is name-space virtualization.

OS-Level Virtualization (Cont.) The OS-level virtualization is not a new idea. In recent years there are already many projects on the Linux/FreeBSD platform, like FreeBSD Jail, Linux Vserver, Virtuozzo and Alcatraz Not many attempts have been tried on the Microsoft Windows platform.

FVM Challenges System call interception Namespace Copy IPC isolation on write confinement Single instance restriction

System call interception Different from Linux platform, Windows hides too many secrets. The system service calls are not officially and fully documented, especially those for handing window and messages. Special interception methods are required in order to change function call's entry point.
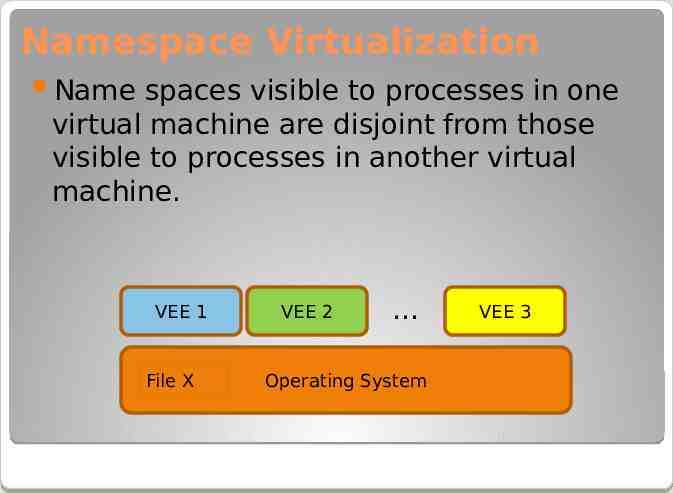
Namespace Virtualization Name spaces visible to processes in one virtual machine are disjoint from those visible to processes in another virtual machine. VEE 1 File X VEE 2 Operating System VEE 3

Namespace isolation There are various kinds of name spaces on Windows platform, such as files, registries (configurations), kernel objects, win32 services (daemon processes) and others. Name space virtualization should identify all these names spaces and their corresponding system service calls. Basically, most system calls taking a resource name as an input parameter should be intercepted.

Copy-on-Write To avoid unnecessary duplication of common system resources, FVM adopts a copy-on-write mechanism. This means an FVM virtual machine shares the system resources with the host machine by default, and gets a local resource copy before it attempts to modify the host copy.

Copy on write The "write" access to system resource from a process in a virtual machine will result at the resource being duplicated into the virtual machine's local space, if it has not been duplicated before. The "write" access here includes write, delete, rename, as well as the read access when sharing is not allowed.

IPC confinement In order to achieve a proper degree of isolation, inter-process communication (IPC) must be confined In addition to standard IPC mechanisms like synchronization object, socket, named pipe, there are also quite a few Windowsspecific IPC mechanisms like window message, DDE, COM, clipboard, etc.

Single instance restriction Windows is initially designed under the consumption that only one interactive user can use any desktop applications at the same time. Therefore, many applications allow only one instance of application to start at one time

FVM Applications Mobile code security. Mobile code refers to programs that come into an end user's computer over the network and start to execute Running email clients and Web browsers like Microsoft Internet Explorer and Outlook inside an FVM virtual machine can guarantee that, malicious code coming through these applications cannot damage the host machine and connected network.

FVM Applications (Cont.) Shared binary service The shared binary server architecture is widely used in the UNIX world. User machines typically mount binary files exported by a central binary server onto local directories, and execute them directly on the local machine.
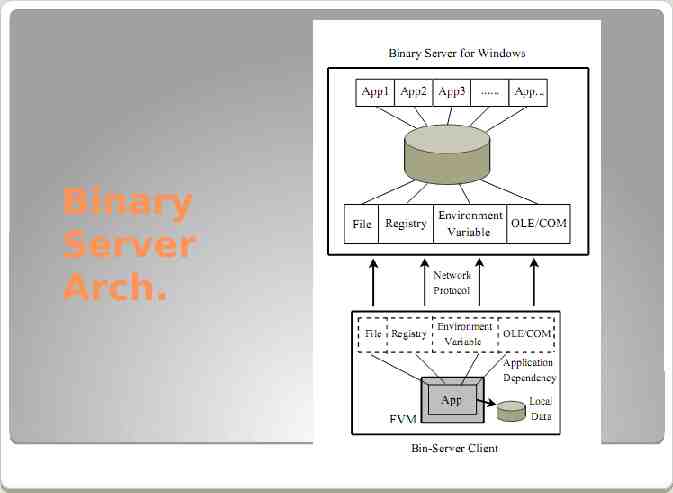
Binary Server Arch.