2016 State of Vulnerability Exploits Amol Sarwate Director of
28 Slides2.69 MB

2016 State of Vulnerability Exploits Amol Sarwate Director of Vulnerability Labs, Qualys Inc.

Agenda Vulnerabilities, Exploits, Exploit Kits 2016 Trends Apply
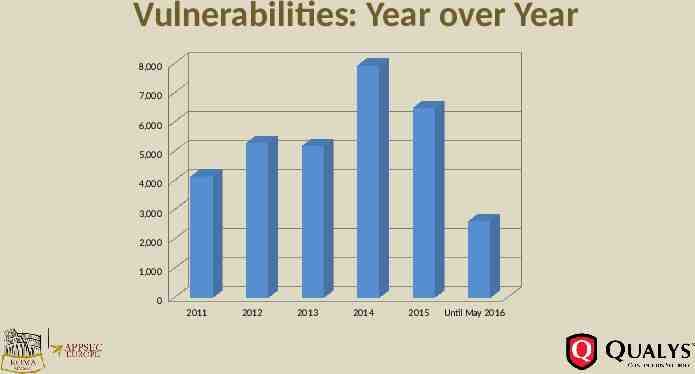
Vulnerabilities: Year over Year 8,000 7,000 6,000 5,000 4,000 3,000 2,000 1,000 0 2011 2012 2013 2014 2015 Until May 2016

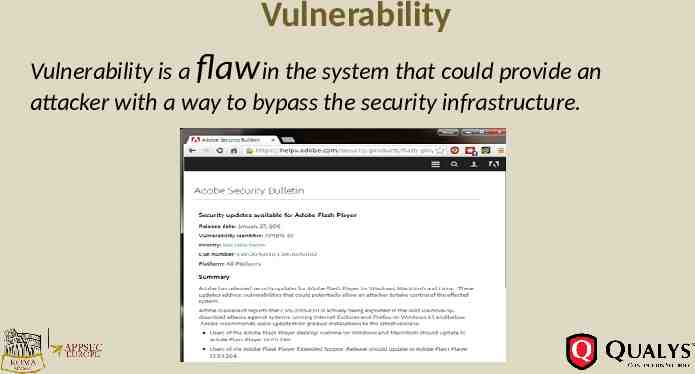
Vulnerability Vulnerability is a flaw in the system that could provide an attacker with a way to bypass the security infrastructure.
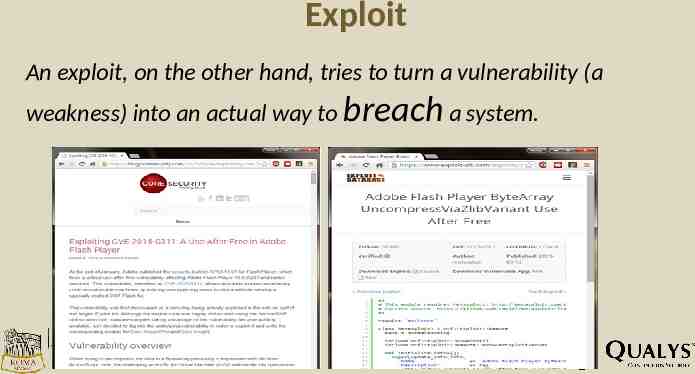
Exploit An exploit, on the other hand, tries to turn a vulnerability (a weakness) into an actual way to breach a system.
Exploit Frameworks Examples An exploit, on the other hand, tries to turn a vulnerability (a weakness) into an actual way to breach a system.

Exploit Kit Exploit kits are toolkits that are used for the purpose of spreading malware. They automate the exploitation of mostly client-side vulnerabilities, come with pre-written exploit code and the kit user does not need to have experience in Vulnerabilities or Exploits.

Exploit Kit Image: http://www.microsoft.com/security/portal/mmpc/threat/exploits.aspx
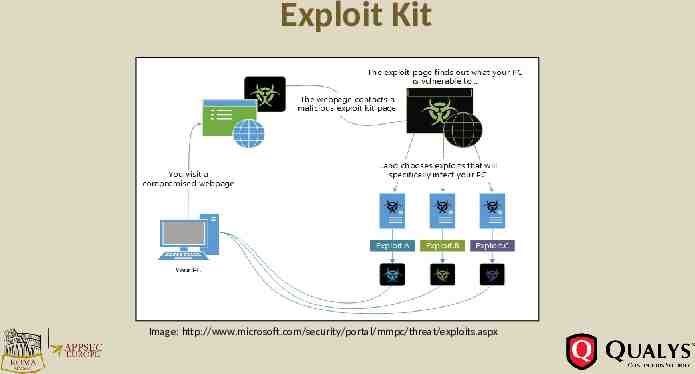
Exploit Kit

Exploit Kit Examples

Exploit Trends 2015-2016

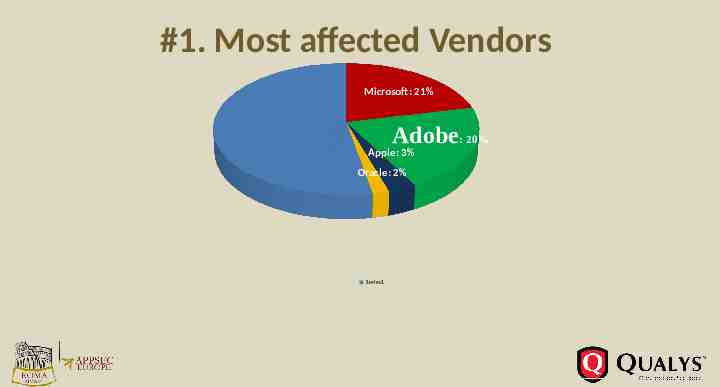
#1. Most affected Vendors Microsoft: 21% Adobe: 20% Apple: 3% Oracle: 2% Series1
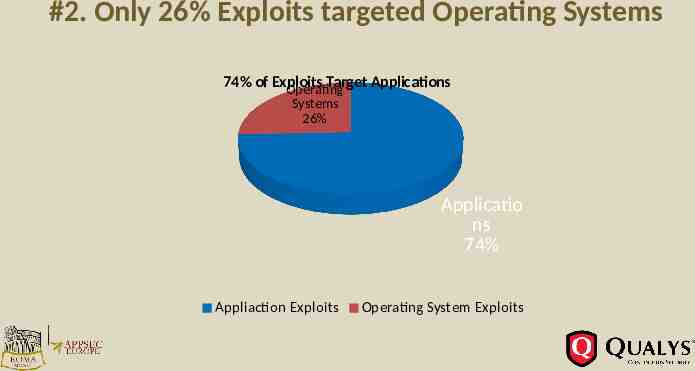
#2. Only 26% Exploits targeted Operating Systems 74% of Exploits Target Applications Operating Systems 26% Applicatio ns 74% Appliaction Exploits Operating System Exploits
Remote vs Local Exploits Requires Local Access Remotely Exploitable 15
#3. Remote vs Local Exploits 80% can be compromised Remotely Requires Local Access Remotely Exploitable (80%) Remote Local

Remote vs Local Exploits REMOTE LOCAL CVE-2015-0349: Adobe Flash Player APSB15-06 Multiple Remote Code Execution Vulnerabilities CVE-2015-2789: Foxit Reader CVE-2015-2789 Local Privilege Escalation Vulnerability CVE-2015-2545: Microsoft Office CVE-2015-2545 Remote Code Execution Vulnerability CVE-2015-2219: Lenovo System Update 'SUService.exe' CVE-2015-2219 Local Privilege Escalation CVE-2015-0014: Microsoft Windows CVE-2015-0014 Telnet Service Buffer Overflow Vulnerability CVE-2015-0002: Microsoft Windows CVE-2015-0002 Local Privilege Escalation Vulnerability Requires Local CVE-2015-1635: Microsoft Windows HTTP Protocol Stack CVE-2015-1635 Remote Code Access Execution CVE-2015-0003: Microsoft Windows Kernel 'Win32k.sys' CVE-2015-0003 Local Privilege Escalation CVE-2015-0273: PHP CVE-2015-0273 Use After Free Remote Code Execution Vulnerability CVE-2015-1515: SoftSphere DefenseWall Personal Firewall 'dwall.sys' Local Privilege Escalation CVE-2015-5477: ISC BIND CVE-2015-5477 Remote Denial of Service Vulnerability CVE-2015-1328: Ubuntu Linux CVE-2015-1328 Local Privilege Escalation Vulnerability CVE-2015-2590: Oracle Java SE CVE-2015-2590 Remote Security Vulnerability CVE-2015-1701: Microsoft Windows CVE-2015-1701 Local Privilege Escalation Vulnerability CVE-2015-2350: MikroTik RouterOS Cross Site Request Forgery Vulnerability CVE-2015-3246: libuser CVE-2015-3246 Local Privilege Escalation Vulnerability CVE-2015-0802: Mozilla Firefox CVE-2015-0802 Security Bypass Vulnerability CVE-2015-1724: Microsoft Windows Kernel Use After Free CVE-2015-1724 Local Privilege Escalation Vulnerability CVE-2015-1487: Symantec Endpoint Protection Manager CVE-2015-1487 Arbitrary File Write CVE-2015-2360: Microsoft Windows Kernel 'Win32k.sys' CVE-2015-2360 Local Privilege Escalation CVE-2015-4455: WordPress Aviary Image Editor Add-on For Gravity Forms Plugin Arbitrary File CVE-2015-5737: FortiClient CVE-2015-5737 Multiple Local Information Disclosure Vulnerabilities
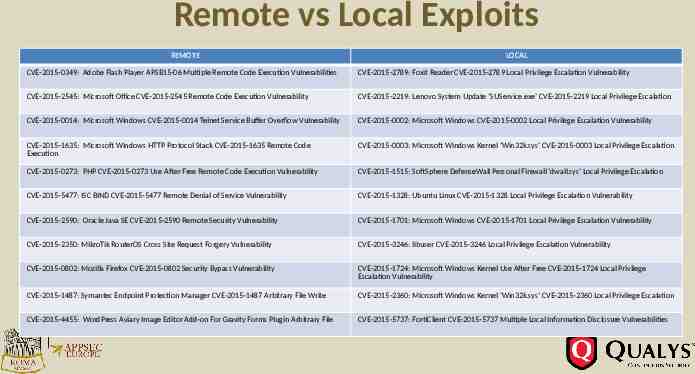
Remote vs Local Exploits Remotely Exploitable Requires Local Access 200 50 180 45 160 40 140 35 120 30 100 25 80 20 60 15 40 10 20 5 0 Microsoft Adobe Apple Others 0 Microsoft Adobe Apple Others
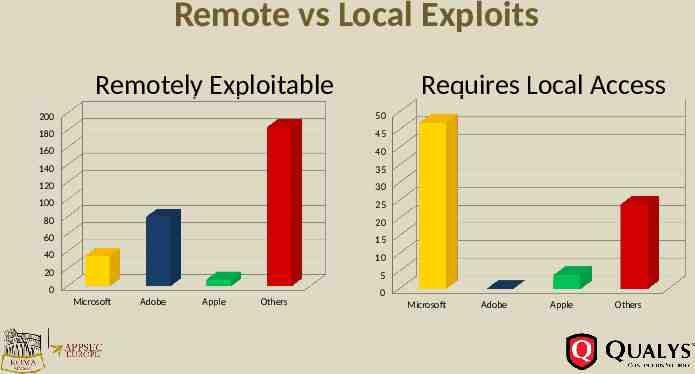
#4. Lateral Movement http://about-threats.trendmicro.com/cloud-content/us/ent-primers/pdf/tlp lateral movement.pdf
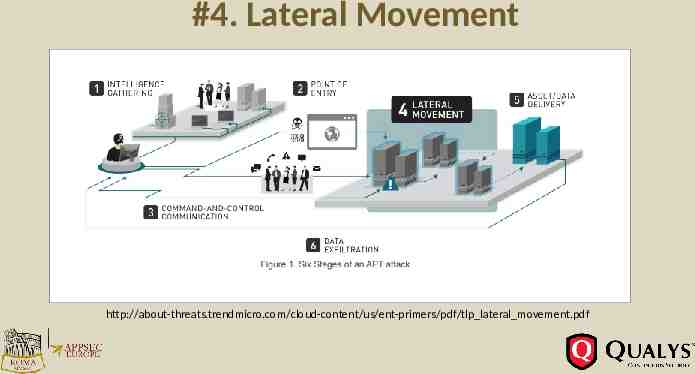
Lateral Movement HIGH LATERAL MOVEMENT LOW LATERAL MOVEMENT CVE-2015-0117: IBM Domino CVE-2015-0117 Arbitrary Code Execution Vulnerability CVE-2015-1155: Apple Safari CVE-2015-1155 Information Disclosure Vulnerability CVE-2015-2545: Microsoft Office CVE-2015-2545 Remote Code Execution Vulnerability CVE-2015-5737: FortiClient CVE-2015-5737 Multiple Local Information Disclosure Vulnerabilities CVE-2015-1635: Microsoft Windows HTTP Protocol Stack CVE2015-1635 Remote Code Execution Vulnerability CVE-2015-1830: Apache ActiveMQ CVE-2015-1830 Directory Traversal Vulnerability CVE-2015-2590: Oracle Java SE CVE-2015-2590 Remote Security Vulnerability CVE-2015-1427: Elasticsearch Groovy Scripting Engine Sandbox Security Bypass Vulnerability CVE-2015-0240: Samba 'TALLOC FREE()' Function Remote Code Execution Vulnerability CVE-2015-1479: ManageEngine ServiceDesk Plus 'CreateReportTable.jsp' SQL Injection Vulnerability CVE-2015-2342: VMware vCenter Server CVE-2015-2342 Remote Code Execution Vulnerability CVE-2015-1592: Movable Type CVE-2015-1592 Unspecified Local File Include Vulnerability CVE-2015-2219: Lenovo System Update 'SUService.exe' CVE2015-2219 Local Privilege Escalation Vulnerability CVE-2015-2560: ManageEngine Desktop Central CVE-20152560 Password Reset Security Bypass Vulnerability
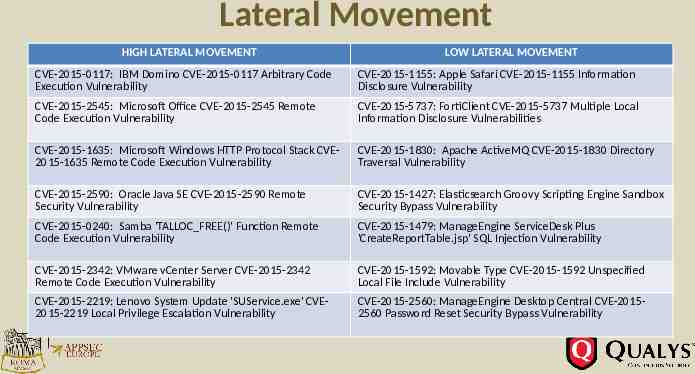
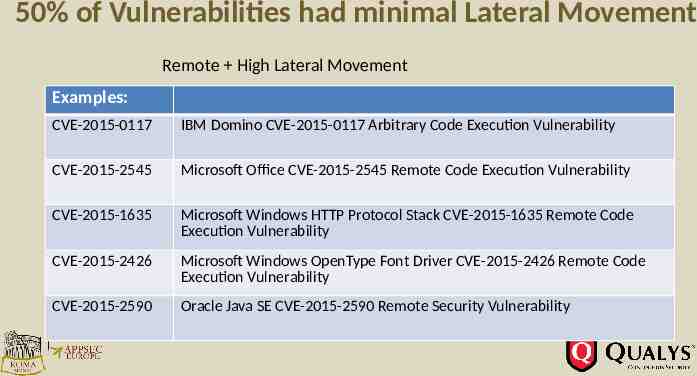
50% of Vulnerabilities had minimal Lateral Movement Remote High Lateral Movement Examples: CVE-2015-0117 IBM Domino CVE-2015-0117 Arbitrary Code Execution Vulnerability CVE-2015-2545 Microsoft Office CVE-2015-2545 Remote Code Execution Vulnerability CVE-2015-1635 Microsoft Windows HTTP Protocol Stack CVE-2015-1635 Remote Code Execution Vulnerability CVE-2015-2426 Microsoft Windows OpenType Font Driver CVE-2015-2426 Remote Code Execution Vulnerability CVE-2015-2590 Oracle Java SE CVE-2015-2590 Remote Security Vulnerability
#5. Exploits for EOL Applications
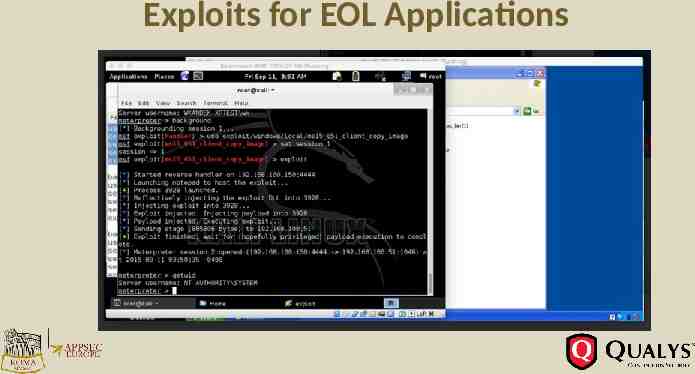
Exploits for EOL Applications
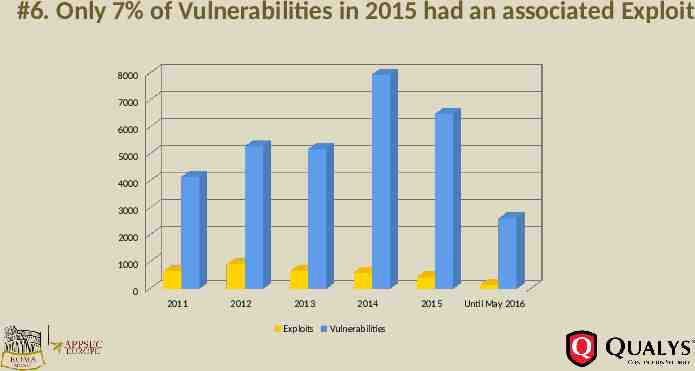
#6. Only 7% of Vulnerabilities in 2015 had an associated Exploit 8000 7000 6000 5000 4000 3000 2000 1000 0 2011 2012 2013 Exploits 2014 Vulnerabilities 2015 Until May 2016
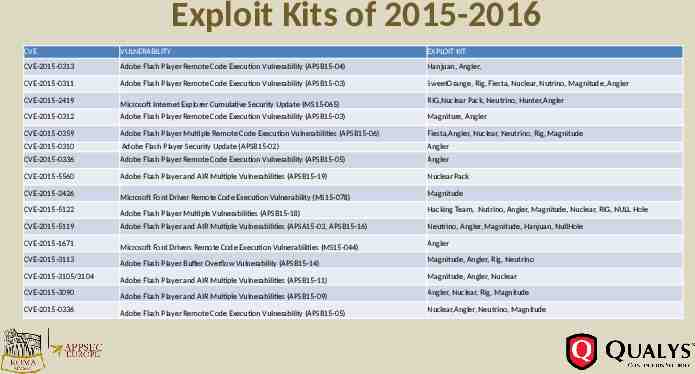
Exploit Kits of 2015-2016 CVE VULNERABILITY EXPLOIT KIT CVE-2015-0313 Adobe Flash Player Remote Code Execution Vulnerability (APSB15-04) Hanjuan, Angler, CVE-2015-0311 Adobe Flash Player Remote Code Execution Vulnerability (APSB15-03) SweetOrange, Rig, Fiesta, Nuclear, Nutrino, Magnitude, Angler CVE-2015-2419 Microsoft Internet Explorer Cumulative Security Update (MS15-065) RIG,Nuclear Pack, Neutrino, Hunter,Angler CVE-2015-0312 Adobe Flash Player Remote Code Execution Vulnerability (APSB15-03) Magniture, Angler CVE-2015-0359 Adobe Flash Player Multiple Remote Code Execution Vulnerabilities (APSB15-06) Fiesta,Angler, Nuclear, Neutrino, Rig, Magnitude CVE-2015-0310 Adobe Flash Player Security Update (APSB15-02) Angler CVE-2015-0336 Adobe Flash Player Remote Code Execution Vulnerability (APSB15-05) Angler CVE-2015-5560 Adobe Flash Player and AIR Multiple Vulnerabilities (APSB15-19) Nuclear Pack CVE-2015-2426 CVE-2015-5122 CVE-2015-5119 CVE-2015-1671 CVE-2015-3113 CVE-2015-3105/3104 CVE-2015-3090 CVE-2015-0336 Microsoft Font Driver Remote Code Execution Vulnerability (MS15-078) Adobe Flash Player Multiple Vulnerabilities (APSB15-18) Adobe Flash Player and AIR Multiple Vulnerabilities (APSA15-03, APSB15-16) Microsoft Font Drivers Remote Code Execution Vulnerabilities (MS15-044) Adobe Flash Player Buffer Overflow Vulnerability (APSB15-14) Adobe Flash Player and AIR Multiple Vulnerabilities (APSB15-11) Adobe Flash Player and AIR Multiple Vulnerabilities (APSB15-09) Adobe Flash Player Remote Code Execution Vulnerability (APSB15-05) Magnitude Hacking Team, Nutrino, Angler, Magnitude, Nuclear, RIG, NULL Hole Neutrino, Angler, Magnitude, Hanjuan, NullHole Angler Magnitude, Angler, Rig, Neutrino Magnitude, Angler, Nuclear Angler, Nuclear, Rig, Magnitude Nuclear,Angler, Neutrino, Magnitude
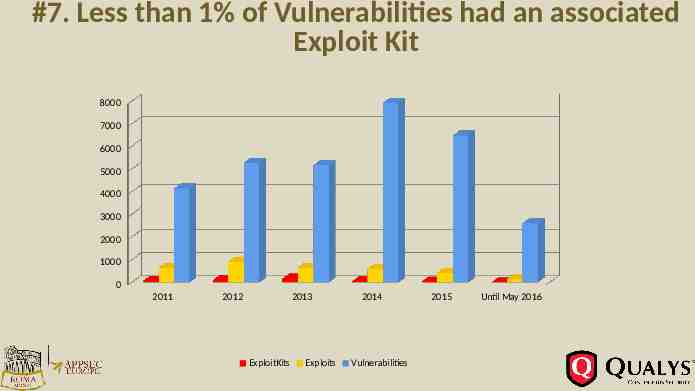
#7. Less than 1% of Vulnerabilities had an associated Exploit Kit 8000 7000 6000 5000 4000 3000 2000 1000 0 2011 2012 2013 ExploitKits Exploits 2014 Vulnerabilities 2015 Until May 2016
Applying Exploit knowledge Next Week: Create inventory of : – – – – Applications with weaponized Exploit packs EOL Applications and EOL Operating Systems Vulnerabilities with working exploits Vulnerabilities that can be remotely compromised Next Month: – Upgrade EOL applications – Patching all vulnerabilities with Exploit packs and exploits Next Quarter: – Automatic inventory and alerting – Debate if most exploited applications, like Flash, are required for business.

Thank You Amol Sarwate @amolsarwate Director of Vulnerability Labs, Qualys Inc.