WSU IT Risk Assessment Process March 22, 2017 Keela
18 Slides793.53 KB

WSU IT Risk Assessment Process March 22, 2017 Keela Ruppenthall Information Security Analyst

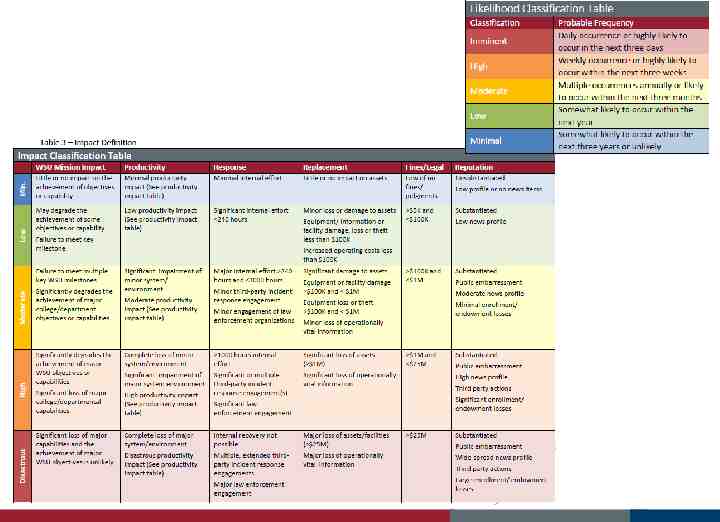
Background Structured Assessment of Operational Environment – Evaluate adequacy of existing security controls Internal and/or external – Determine Risk Level for WSU Information Systems and Services – Identify Cost-Effective Security Requirements for Systems/Services

Risk Assessment Types Contract Risk Assessment – WSU BPPM 70.24: Purchasing – Acquisition of Computer Equipment, Services, or Software Information System or Service Risk Assessment – Any IT information System or Service Applications Servers Networks Any process or procedure by which systems are administered and/or maintained

Contract Risk Assessment WSU BPPM 70.24: Purchasing – Acquisition of Computer Equipment, Services, or Software – Information Services Review Questionnaire for Technology Contracts and Purchases computer equipment, services, or software purchases under 10,000 that require a signed contract or an agreement purchases costing in excess of 10,000 BPPM 70.25: Information Security Risk Assessment (draft) – Requirement Clarification – Updated Questionnaire

Contract Risk Level Questionnaire Responses – Verify compliance with WSU information security requirements – Uncover Impact/Likelihood Assign a Risk Classification Level – Purchasing Services and/or Contract Office Uses rating to determine whether or not to proceed – Risk Level of HIGH should be investigated further
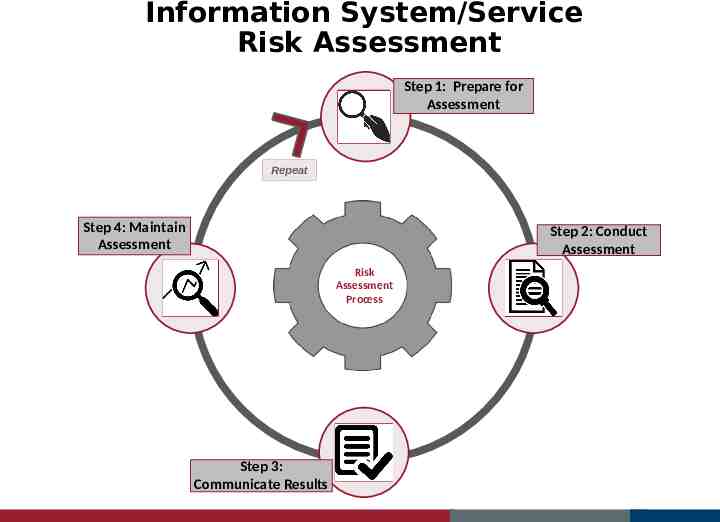
Information System/Service Risk Assessment Step 1: Prepare for Assessment Repeat Step 4: Maintain Assessment Step 2: Conduct Assessment Risk Assessment Process Step 3: Communicate Results

Step 1: Prepare for Assessment Risk Assessment Team – Determine System/Service Scope – Rules Of Engagement – Members Departmental Managers Departmental Technical Managers Information Security Services (ISS) ISS Generates Risk Assessment Report Package – Risk Assessment Results – Living Artifact Updated periodically Begin Data Collection
Documentation Request Acce Acce ptabl ptabl e e Use Use Documen tation Request
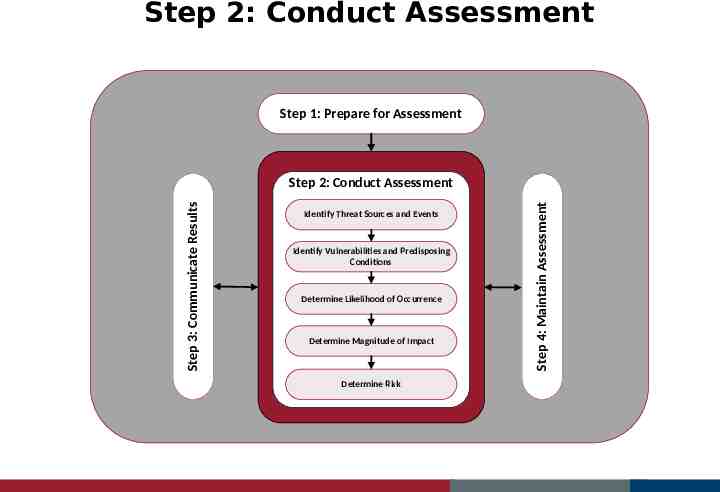
Step 2: Conduct Assessment Step 1: Prepare for Assessment Identify Threat Sources and Events Identify Vulnerabilities and Predisposing Conditions Identify Threat Sources and Events Determine Likelihood of Occurrence Determine Magnitude of Impact Determine Risk Step 4: Maintain Assessment Step 3: Communicate Results Step 2: Conduct Assessment

Identify Threat Sources/Events Discussion/Interview Review/Inspect Collected Data – ISS Vulnerability Discovery Process – NIST SP 800-53A, Rev 4 Controls – Compliance Specific Requirements (HIPAA, PCI) – WSU’s Enterprise Threat Vectors Testing will not include: Changes to assigned user passwords Modification of user files or system files Telephone modem probes and scans (active and passive) Intentional viewing of Enrollment Information Technology and Enterprise Computing Services staff email, Internet caches, and/or personnel cookie files Denial of Service attacks Exploits that will introduce new weaknesses to the system Intentional introduction of malicious code (viruses, Trojans, worms, etc.) Attempted logins or other use of systems, with any account name/password Attempted SQL injection and other forms of input parameter testing Use of exploit code for leveraging discovered vulnerabilities Adding user accounts Spoofing or deceiving servers regarding network traffic Altering running system configuration except where denial of service would result Password cracking via capture and scanning of authentication databases
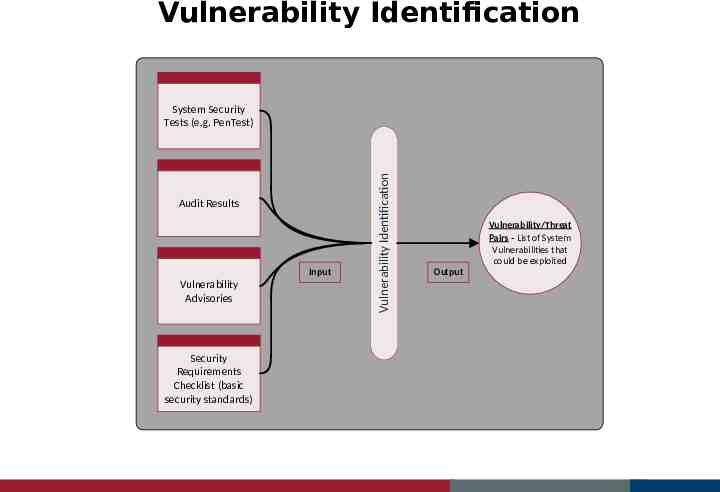
Vulnerability Identification Audit Results Input Vulnerability Advisories Security Requirements Checklist (basic security standards) Vulnerability Identification System Security Tests (e.g. PenTest) Vulnerability/Threat Pairs - List of System Vulnerabilities that could be exploited Output
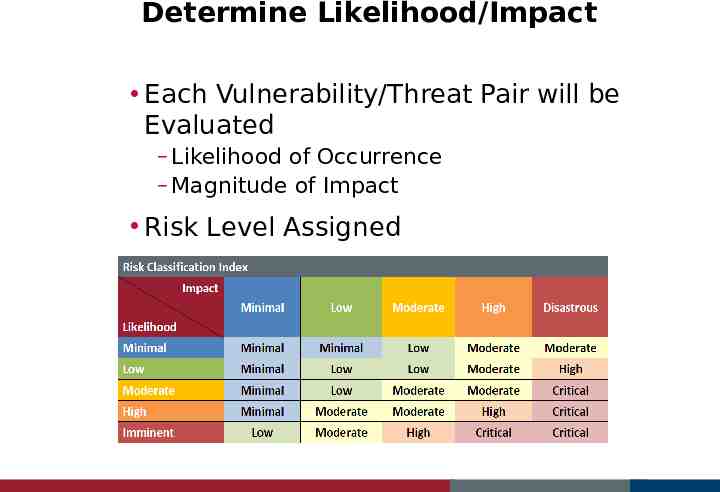
Determine Likelihood/Impact Each Vulnerability/Threat Pair will be Evaluated – Likelihood of Occurrence – Magnitude of Impact Risk Level Assigned

Step 3: Communicate Results Risk Assessment Report List of recommended controls – Reduce level of risk to the IT system or service and its data to an acceptable level Risk Mitigation and Tracking – POA & M - Plan of Action and Milestones
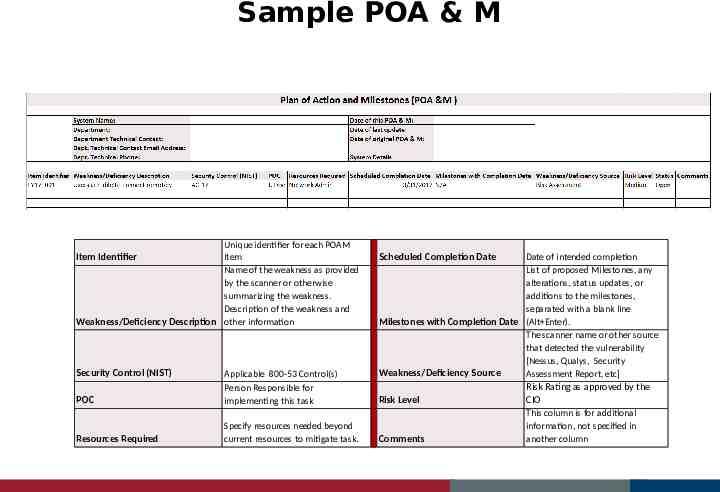
Sample POA & M Unique identifier for each POAM Item Identifier Item Name of the weakness as provided by the scanner or otherwise summarizing the weakness. Description of the weakness and Weakness/Deficiency Description other information Security Control (NIST) POC Applicable 800-53 Control(s) Person Responsible for implementing this task Resources Required Specify resources needed beyond current resources to mitigate task. Scheduled Completion Date Date of intended completion List of proposed Milestones, any alterations, status updates, or additions to the milestones, separated with a blank line Milestones with Completion Date (Alt Enter). The scanner name or other source that detected the vulnerability [Nessus, Qualys, Security Weakness/Deficiency Source Assessment Report, etc] Risk Level Risk Rating as approved by the CIO Comments This column is for additional information, not specified in another column

Step 4: Maintain Assessment Enables Information Security Continuous Monitoring – Ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions Assessment Results Periodically Updated Results Maintained as Compliance Evidence
Continuous Monitoring Step 1: Prepare for Assessment Repeat Step 4: Maintain Assessment Step 2: Conduct Assessment Risk Assessment Process Step 3: Communicate Results

Questions?