Vulnerability Analysis of 2013 SCADA issues Amol Sarwate Director
46 Slides3.16 MB

Vulnerability Analysis of 2013 SCADA issues Amol Sarwate Director of Vulnerability Labs, Qualys Inc. Hosted by OWASP & the NYC Chapter

Agenda SCADA components 2013 Vulnerability Analysis Recommendations and Proposals Hosted by OWASP & the NYC Chapter

SCADA DCS ICS Hosted by OWASP & the NYC Chapter

Hosted by OWASP & the NYC Chapter

Accidents liquid pipeline failures http://www.ntsb.gov/doclib/safetystudies/SS0502.pdf power failures http://www.nerc.com/docs/docs/blackout/Status Report 081104.pdf other accidents http://en.wikipedia.org/wiki/List of industrial disasters Hosted by OWASP & the NYC Chapter

Vandalism vandals destroy insulators http://www.bpa.gov/corporate/BPAnews/archive /2002/NewsRelease.cfm?ReleaseNo 297 Hosted by OWASP & the NYC Chapter

Insider disgruntle employee http://www.theregister.co.uk/2001/10/31 /hacker jailed for revenge sewage/ Hosted by OWASP & the NYC Chapter

APT terrorism or espionage http://www.symantec.com/content/en/us/enterprise/ media/security response/whitepapers/w32 duqu the precursor to the next stuxnet.pdf Hosted by OWASP & the NYC Chapter

2009 - 2013 SCADA Vulnerabilities (estimate) Hosted by OWASP & the NYC Chapter

Components Remote Sensors Meters Field Devices I/O Field Hosted by OWASP & the NYC Chapter PLC IED RTU Master Protocols FEP Wired Wireless HMI DCS SCADA Communication Control Center

Acquisition Convert parameters like light, temperature, pressure or flow to analog signals Hosted by OWASP & the NYC Chapter

Conversion Converts analog and discrete measurements to digital information Hosted by OWASP & the NYC Chapter

Communication Front end processors (FEP) and protocols Wired or wireless communication Hosted by OWASP & the NYC Chapter Modbus DNP 3 OPC ICCP ControlNet BBC 7200 ANSI X3.28 DCP 1 Gedac 7020 DeviceNet DH ProfiBus Tejas TRE UCA

Presentation & Control Control, monitor and alarming using human machine interface (HMI) Hosted by OWASP & the NYC Chapter
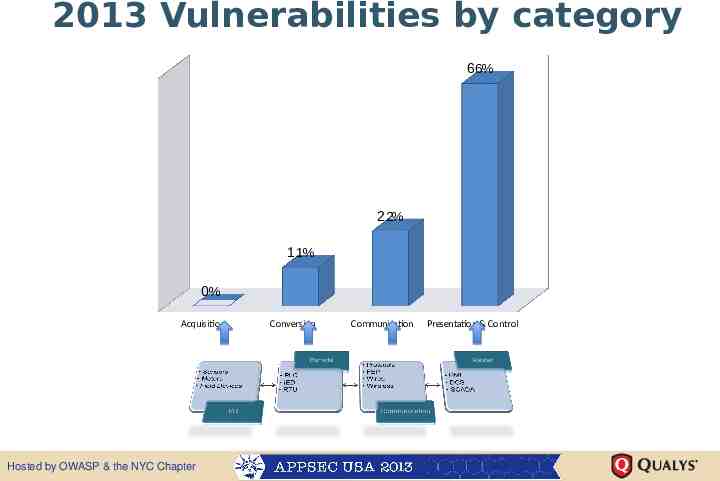
2013 Vulnerabilities by category 6 6% 2 2% 1 1% 0% Acquisition Hosted by OWASP & the NYC Chapter Conversion Communication Presentation & Control

Acquisition – – – – Requires physical access Field equipment does not contain process information Information like valve 16 or breaker 9B Without process knowledge leads to nuisance disruption 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Emerson ROC800 Vulnerabilities – – – – – CVE-2013-0693: Network beacon broadcasts allows detection CVE-2013-0692: OSE Debug port service CVE-2013-0694: Hardcode accounts with passwords Access: AV:N, AC:L, Au:N Impact: C:C, I:C, A:C – Patch available from Emerson 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%
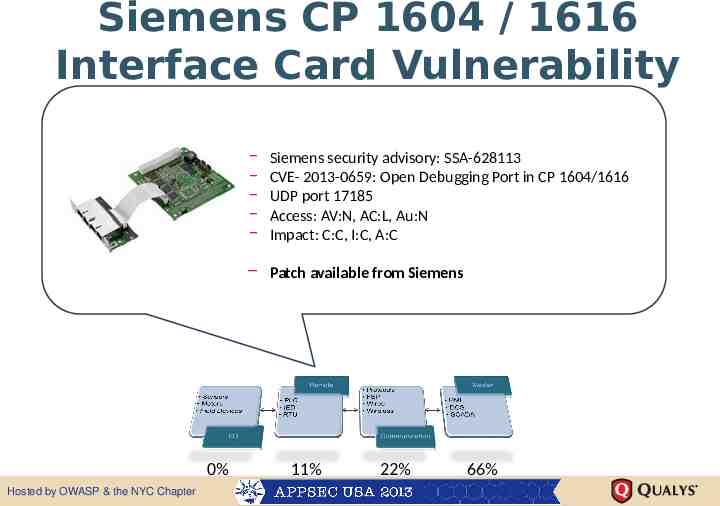
Siemens CP 1604 / 1616 Interface Card Vulnerability – – – – – Siemens security advisory: SSA-628113 CVE- 2013-0659: Open Debugging Port in CP 1604/1616 UDP port 17185 Access: AV:N, AC:L, Au:N Impact: C:C, I:C, A:C – Patch available from Siemens 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Communication 24% 16% 12% 16% 12% 12% 4% General ModBus 0% Hosted by OWASP & the NYC Chapter DNP C37.118 11% IGMP 22% 4% SNMP FTP/TFTP 66% SSH/SSL

ModBus Vulnerabilities – CVE-2013-2784: Triangle Research Nano-10 PLC Crafted Packet Handling Remote DoS – CVE-2013-0699: Galil RIO-47100 PLC Crafted Modbus Packet Handling Remote DoS – RBS -2013- 003: Schneider Electric Multiple Modbus MBAP DoS and RCE Nano-10 PLC RIO-47100 PLC 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

DNP Vulnerabilities – – – – CVE-2013-2791: MatrikonOPC Server DNP3 Packet Handling buffer overflow CVE-2013-2798: Schweitzer Real-Time Automation Controllers (RTAC) Local DoS CVE-2013-2788: SUBNET SubSTATION Server DNP3 Outstation Slave Remote DoS CVE-2013-2783: IOServer DNP3 Packet Handling Infinite Loop Schweitzer RTAC 0% Hosted by OWASP & the NYC Chapter Matrikon OPC Server 11% 22% IOServer 66%

Security Analysis of SCADA protocols Modbus and DNP free tool: http://code.google.com/p/scadascan/ 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

SSH, FTP, TFTP, IGMP, SNMP – – – – – – – – CVE-2013-0137: Monroe Electronics Default root SSH Key Remote Access CVE-2012-4697: TURCK BL20 / BL67 FTP Service Hardcoded Admin Credentials CVE-2013-2800: OSIsoft PI Interface for IEEE C37.118 Memory Corruption CVE-2013-0689: Emerson RTU TFTP Server File Upload Arbitrary Code Execution CVE-2013-3634: Siemens Scalance X200 IRT SNMP Command Execution Korenix Multiple JetNet Switches TFTP Server Arbitrary File Creation RuggedCom ROX-II IGMP Packet Saturation RSTP BPDU Prioritization Weakness Korenix Multiple JetNet Switches SSL / SSH Hardcoded Private Keys 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Presentation & Control 31% 26% 13% 9% 5% 5% 3% Generic XSS SQL Injection 0% Hosted by OWASP & the NYC Chapter 5% 4% Database Generic Web 11% Directory & File Disclosure 22% CSRF 66% ActiveX Crypto

Presentation & Control – – – – – – CVE-2013-2299: Advantech WebAccess /broadWeb/include/gAddNew.asp XSS CVE-2013-0684: Invensys Wonderware Information Server (WIS) SQL Injection CVE-2013-3927: Siemens COMOS Client Library Local Database Object Manipulation CVE-2013-0680: Cogent DataHub Crafted HTTP Request Header Parameter Stack Overflow CVE-2013-0652: General Electric (GE) Intelligent Proficy Java Remote Method Invocation CVE-2008-0760: SafeNet Sentinel Protection Server HTTP Request Directory Traversal and Arbitrary File Access – CVE-2012-3039: Moxa OnCell Gateway Predictable SSH / SSL Connection Key Generation – Weidmüller WaveLine Router Web Interface config.cgi Configuration Manipulation CSRF 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues Control system network connected to corporate network or internet 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues No authentication No per user authentication 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%
Real world issues Delayed patching if any 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues Default passwords Shared passwords No password change policy 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues Systems not restarted in years 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues Off-the-shelf software Operating system, Database, Browser, Web Server 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues Un-necessary services 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

Real world issues Internal differences between IT and SCADA engineers 0% Hosted by OWASP & the NYC Chapter 11% 22% 66%

System Wide Challenges SCADA system long life cycle Long life cycle of a SCADA system Hosted by OWASP & the NYC Chapter

System Wide Challenges SCADA system long life cycle Cost and difficulty of an upgrade Hosted by OWASP & the NYC Chapter

Proposals SCADA network auditing Hosted by OWASP & the NYC Chapter

Proposals Is you SCADA system exposed on the internet? Hosted by OWASP & the NYC Chapter

Proposals Password policy, access control and access roles Hosted by OWASP & the NYC Chapter

Proposals Are all services necessary? Hosted by OWASP & the NYC Chapter

Proposals Use secure protocols Hosted by OWASP & the NYC Chapter

Proposals Strategy for Software Update and patching Hosted by OWASP & the NYC Chapter

Proposals SCADA test environment Hosted by OWASP & the NYC Chapter

Proposals Keep up-to-date with vulnerabilities Hosted by OWASP & the NYC Chapter

Proposals Apply experience from IT network management Hosted by OWASP & the NYC Chapter

ScadaScan Current version Scan network range Works with TCP/IP Identifies Modbus TCP slaves Identifies DNP 3 TCP slaves Beta version SCADA master vulnerability scanning SNMP support HTTP support 1.0 Release User configurable signature files Authenticated support for Windows and *nix Code cleanup Hosted by OWASP & the NYC Chapter

Thank You Twitter: @amolsarwate http://code.google.com/p/scadascan/ https://community.qualys.com Hosted by OWASP & the NYC Chapter