The Quality Payment Program: Security Risk Assessment Kim
33 Slides1.98 MB

The Quality Payment Program: Security Risk Assessment Kim Salamone, PhD Vice President, Health Information Technology Chad Jans, MBA Health Informatics Specialist Health Services Advisory Group (HSAG)

Disclosure I have nothing to report, nor are there any real or perceived conflicts of interest, implied or expressed, in the following presentation. Kim Salamone, PhD 2

Agenda Introduce HSAG Wrap-up QPP—Year 1 (2017) Security Risk Assessment No-cost assistance Questions 3

Acronyms Alternative Payment Model (APM) Electronic Health Record (EHR) Electronic Protected Health Information (ePHI) Enterprise Identity Management (EIDM) Health Care Quality Information Systems (HCQIS) Access Roles and Profile (HARP) Health Insurance Portability and Accountability Act (HIPAA) Merit-based Incentive Payment System (MIPS) Meaningful Use (MU) Office of the National Coordinator (ONC) Quality Innovation Network-Quality Improvement Organization (QIN-QIO) Quality Payment Program (QPP) Security Risk Assessment (SRA) Small, Underserved, and Rural Support (SURS) Program Tax Identification Number (TIN) 4

HSAG: Your Partner in Healthcare Quality HSAG is the Medicare QIN-QIO for Arizona, California, Florida, Ohio, and the U.S. Virgin Islands. – QPP support for 16 eligible clinicians through the QIN-QIO HSAG is the QPP technical assistance contractor for Hawaii, California, Arizona, Florida, New Mexico, and the U.S. Virgin Islands. – 15 eligible clinicians through the QPP SURS program 4

QPP Year 1 (2017) Wrap-Up 6

Audience Participation Questions? – Are you submitting data for 2018? – How many of you are prepared to submit your 2019 MIPS? – Did you do a SRA? 7

Fact Check QPP Year 1 (2017) is in the books and we are now in the submitting data for Year 2 (2018)! CMS Administrator Seema Verma announced via blog: – 91 percent of MIPS-eligible clinicians participated in Year 1. – 94 percent of eligible rural practices submitted MIPS data. – 98 percent of eligible ACOs participated. MIPS Year 1 Final Reports were released on June 29, 2018. – Do you know how you performed? 8

Lessons Learned from MIPS Year 1 (2017) Did not take the time to educate themselves Did not have all staff on board with the requirements Did not confirm submitted data or relied on others Did not have EIDM account set-up or let password expire Did not submit data under all TINs when “Included” Did not submit early or waited at the last minute Did not submit enough data or reach data completeness 9 Did not monitor progress or switched measures too late Did not ? Fill in the blank. Did not prepare for vendor issues or delays (no back-up plan)

Security Risk Assessment 10

ONC’s Top 10 Myths of SRA 1. The SRA is optional for small providers. 2. Simply installing a certified EHR fulfills the PI requirement. 3. My EHR vendor took care of everything I need to do about privacy and security. 4. I have to outsource the SRA. 5. A checklist will suffice for the risk analysis requirement. 11 Source: HealthIT.gov website. Accessed on January 22, 2019. Available at https://www.healthit.gov/topic/privacy-security/top-10-myths-security-risk-analysis

ONC’s Top 10 Myths of SRA (cont.) 6. There is a specific risk assessment method that I must follow. 7. My SRA only needs to look at my EHR. 8. I only need to do a risk assessment once. 9. Before I attest, I must fully mitigate all risks. 10. Each year, I will have to completely redo my SRA. 12 Source: HealthIT.gov website. Accessed on January 22, 2019. Available at https://www.healthit.gov/topic/privacysecurity/top-10-myths-security-risk-analysis

What Is Required Under the HIPAA Security Rule? The HIPAA Security Rule requires healthcare providers, health plans, and business associates to conduct risk assessment and implement technical, physical, and administrative safeguards to protect ePHI. – Administrative (e.g., security management process) – Physical (e.g., security badges) – Technical (e.g., encryption on the network) 13 Source: HealthIT.gov website. Accessed on January 22, 2019. Available at https://www.healthit.gov/sites/default/files/page/201810/SRA Tool User Guide 101518.pdf

SRA Tool 3.0 (SRA 3.0) The ONC for Health IT worked together with the Office for Civil Rights, which enforces the HIPAA Security Rule, to develop this tool to assist providers and business associates with meeting their responsibility to protect ePHI. The tool is designed to assist an organization with its review and documentation of its risk assessment. A thoroughly completed SRA 3.0 will make you aware of areas where attention is needed to bring your organization into compliance with the HIPAA Security Rule. 14 Source: HealthIT.gov website. Accessed on January 22, 2019. Available at https://www.healthit.gov/sites/default/files/page/2018-10/SRA Tool User Guide 101518.pdf

SRA 3.0 (cont.) The SRA 3.0 Tool is a Windows-based single downloadable module that runs on your computer. – The legacy iOS SRA Tool 2.0 application for iPad can be downloaded from the Apple App Store. The SRA 3.0 Tool uses a wizard based workflow and section summary reporting that provides feedback and progress indicators as the risk assessment is worked through. The SRA 3.0 Tool supports multiple user accounts and a collaborative file sharing feature. 15 Source: HealthIT.gov website. Accessed on January 22, 2019. Available at https://www.healthit.gov/sites/default/files/page/2018-10/SRA Tool User Guide 101518.pdf

Additional Resources for SRA on HealthIT.gov A paper-based version of the Legacy SRA Tool Version 2.0 can be downloaded, and printed, along with the companion SRA Tool 2.0 User Guide. SRA Videos. A Model Privacy Notice (MPN) Privacy and Security Resources and Tools for providers and consumers. https://www.healthit.gov/topic/privacy-security-andhipaa 16 Source: HealthIT.gov website. Accessed on January 22, 2019. Available at https://www.healthit.gov/topic/privacy-securityand-hipaa/security-risk-assessment

Let’s Get Started 17
Downloading the Tool Download the tool from the HealthIT.gov website. – https://www.healthit.gov/topic/privacy-security-andhipaa/security-risk-assessment Once downloaded, run the downloaded executable file to begin installation. When installation is complete, double click on the SRA-Tool icon to begin. Hardware Requirements: – Windows 7/8/10 – 2 GHz Pentium processor – 2 GB RAM 18

Starting an Assessment SRA 3.0 Tool must be downloaded and installed on a compatible system. – The first steps to starting a new assessment are entering a user name of your choosing, creating a file name for your SRA, and selecting a location to save your SRA file. Select “START NEW SRA”. Enter a user name. Click “Continue.” Select “Pick a spot to save your SRA file.” This launches a system-file browser. In order to begin a new assessment and save progress, a location and file name for the .SRA file must be selected. Choose a location and file name for the assessment, click “Save” when finished. Click “Continue” to move forward. 19

Starting a New Assessment Source: SRA Tool V.3.0 User Guide, pg. 5 20

Go to Tool: Fill Out Practice Information 21

Look at Reports 22
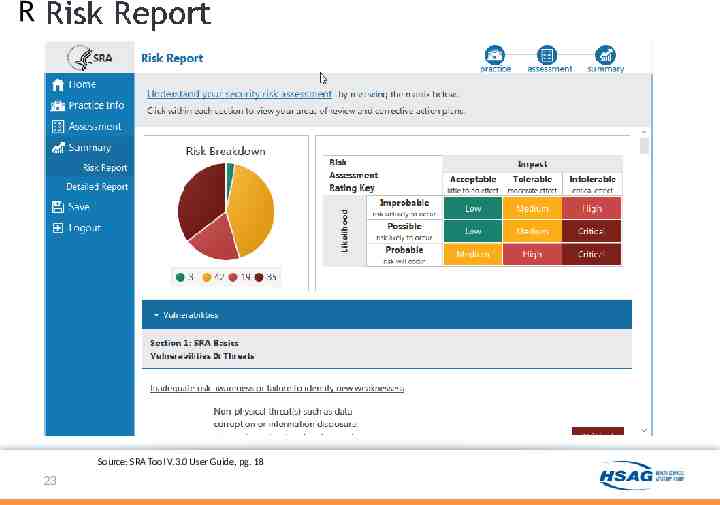
Risk report screenshot Source: SRA Tool V.3.0 User Guide, pg. 18 23

SRA Maintenance Log into your QPP account using your HARP credential every 60 days to keep it active. Update your SRA yearly and keep documentation. Develop necessary policies and procedures. Update assets each time a new piece of equipment is purchased that will contain ePHI or disposed of that contains ePHI. Review and update business associate agreements yearly. Ensure mobile devices used in the practice are secured. 24

Securing Mobile Devices Use a password or other user authentication. Install and enable encryption. Install and activate remote wiping and/or remote disabling. Disable and do not install or use file sharing applications. Install and enable a firewall. Install and enable security software. Keep security software up to date. Research mobile apps before downloading. Use adequate security to send or receive health information over public Wi-Fi networks. Delete all stored health information before discarding or reusing the mobile device. https://www.healthit.gov/topic/privacy-security-and-hipaa/how-can-you-protect-and-secure-health-information-when-using-mobile-device 25

Paper Tool 26
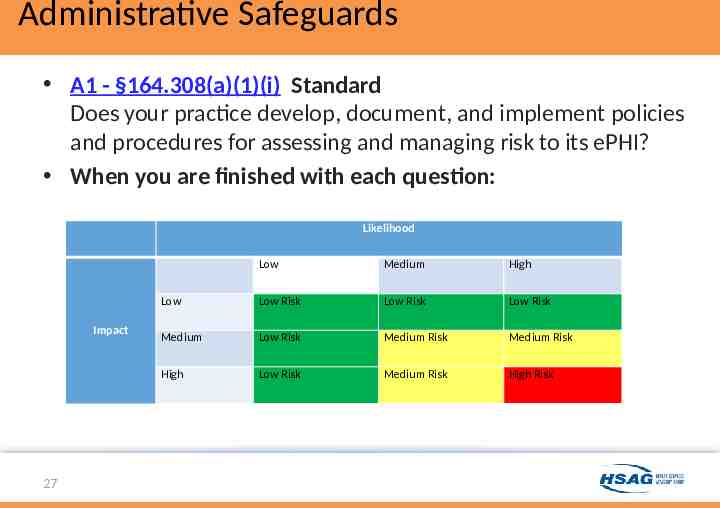
Administrative Safeguards A1 - §164.308(a)(1)(i) Standard Does your practice develop, document, and implement policies and procedures for assessing and managing risk to its ePHI? When you are finished with each question: Likelihood Impact 27 Low Medium High Low Low Risk Low Risk Low Risk Medium Low Risk Medium Risk Medium Risk High Low Risk Medium Risk High Risk

Physical Safeguards PH1 - §164.310(a)(1) Standard Do you have an inventory of the physical systems, devices, and media in your office space that are used to store or contain ePHI? When you are finished with each question: Likelihood Impact 28 Low Medium High Low Low Risk Low Risk Low Risk Medium Low Risk Medium Risk Medium Risk High Low Risk Medium Risk High Risk

Technical Safeguards T1 - §164.312(a)(1) Standard Does your practice have policies and procedures requiring safeguards to limit access to ePHI to those persons and software programs appropriate for their role? When you are finished with each question: Likelihood Impact 29 Low Medium High Low Low Risk Low Risk Low Risk Medium Low Risk Medium Risk Medium Risk High Low Risk Medium Risk High Risk

How Do I Get Help? 30

Call to Action–Request No-Cost Assistance Request the appropriate technical assistance now! www.hsag.com/QPP QPP support for practices with 15 or less clinicians under TIN, visit https://goo.gl/MTGhua QPP support for practices with 16 or more clinicians under TIN, visit https://www.hsag.com/QPPEnroll 31

Questions 32

Thank you! Kim Salamone, PhD HSAG Vice President, Health Information Technology 602.801.6960 [email protected]