Privacy and IT Security American Society of Access
63 Slides1.20 MB

Privacy and IT Security American Society of Access Professionals Presented by Samuel P. Jenkins, Director, Defense Privacy Office February 2010

Privacy and IT Security Agenda: Fair Information Practice Principles Laws and Statutes of Privacy and Security Privacy Defined IT Security Defined Annual FISMA Reporting Chief Information Officer Questions PIA/SORN Essential Elements Crosswalk Conclusion - The Way Ahead 2

Privacy and IT Security Fair Information Practice Principles 3
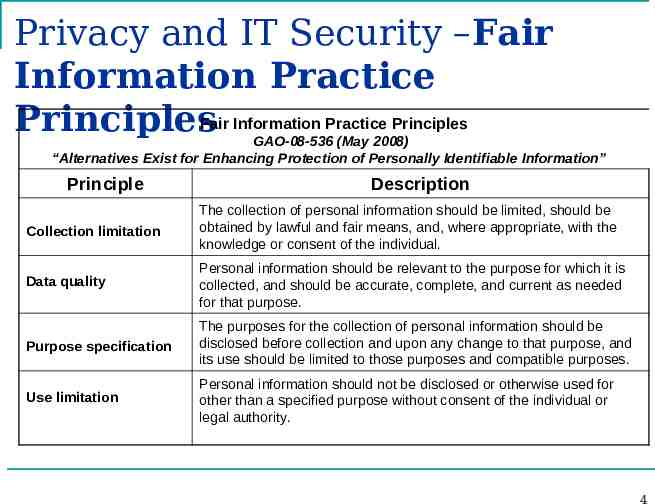
Privacy and IT Security –Fair Information Practice PrinciplesFair Information Practice Principles GAO-08-536 (May 2008) “Alternatives Exist for Enhancing Protection of Personally Identifiable Information” Principle Description Collection limitation The collection of personal information should be limited, should be obtained by lawful and fair means, and, where appropriate, with the knowledge or consent of the individual. Data quality Personal information should be relevant to the purpose for which it is collected, and should be accurate, complete, and current as needed for that purpose. Purpose specification The purposes for the collection of personal information should be disclosed before collection and upon any change to that purpose, and its use should be limited to those purposes and compatible purposes. Use limitation Personal information should not be disclosed or otherwise used for other than a specified purpose without consent of the individual or legal authority. 4
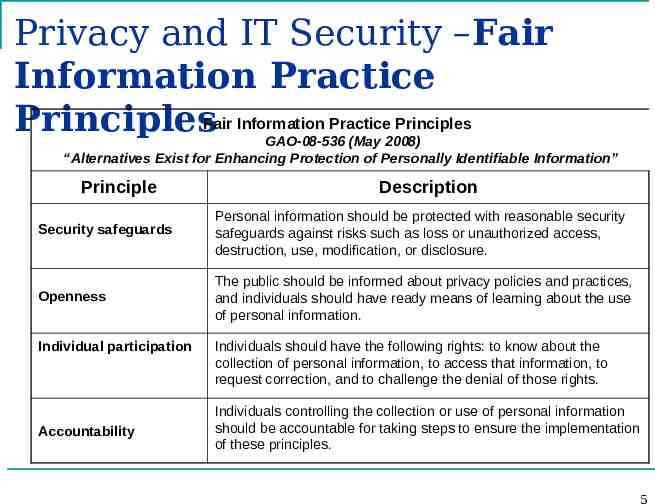
Privacy and IT Security –Fair Information Practice PrinciplesFair Information Practice Principles GAO-08-536 (May 2008) “Alternatives Exist for Enhancing Protection of Personally Identifiable Information” Principle Description Security safeguards Personal information should be protected with reasonable security safeguards against risks such as loss or unauthorized access, destruction, use, modification, or disclosure. Openness The public should be informed about privacy policies and practices, and individuals should have ready means of learning about the use of personal information. Individual participation Accountability Individuals should have the following rights: to know about the collection of personal information, to access that information, to request correction, and to challenge the denial of those rights. Individuals controlling the collection or use of personal information should be accountable for taking steps to ensure the implementation of these principles. 5

Privacy and IT Security Laws and Statutes of Privacy and Security 6
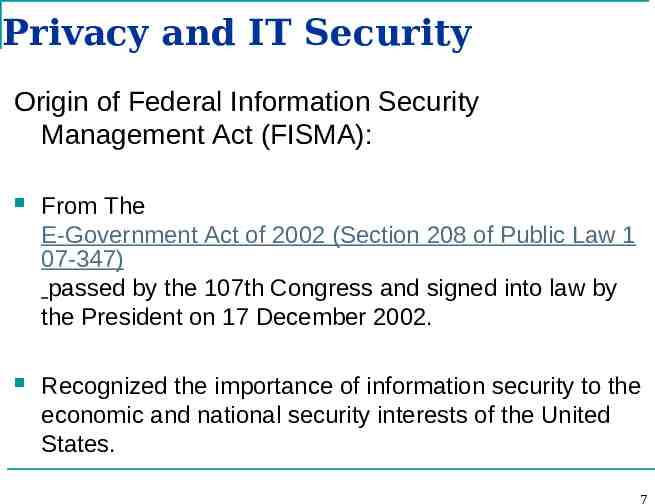
Privacy and IT Security Origin of Federal Information Security Management Act (FISMA): From The E-Government Act of 2002 (Section 208 of Public Law 1 07-347) passed by the 107th Congress and signed into law by the President on 17 December 2002. Recognized the importance of information security to the economic and national security interests of the United States. 7

Privacy and IT Security E-Government Act of 2002, Public Law 107- 347 Section 208 Requirements. Agencies are required to: conduct privacy impact assessments for electronic information systems and collections and, in general, make them publicly available (see Section II of this Guidance), Federal Agency PIA Requirements Section 208 of the E-Government Act of 2002 requires all agencies to conduct PIAs for all new or substantially changed information systems that collect, maintain, or disseminate PII on the public. 8

Privacy and IT Security Title III of the E-Government Act, entitled the Federal Information Security Management Act of 2002 (FISMA) requires: each federal agency to develop, document, and implement an agency-wide program to provide information security for the information and information systems that support the operations and assets of the agency, including those provided or managed by another agency, contractor, or other source. FISMA, along with the Paperwork Reduction Act of 1995 and the Information Technology Management Reform Act of 1996 (ClingerCohen Act), explicitly emphasizes a risk-based policy for costeffective security. 9

Privacy and IT Security Federal Information Security Management Act (FISMA), Title III of the E-Government Act of 2002 Agencies must: Develop information security plans that are based on assessments of risk/magnitude of harm that could result from unauthorized use, access, etc. Develop security awareness training to inform employees of these plans Periodic testing and evaluation of the effectiveness of IT security policies, procedures and practices. Procedures for detecting, reporting and responding to security incidents 10

Privacy and IT Security Office of Management and Budget (OMB). In support of and reinforcing this legislation, OMB through Circular A-130, Appendix III, Security of Federal Automated Information Resources, requires executive agencies within the federal government to: Plan for security Ensure that appropriate officials are assigned security responsibility Periodically review the security controls in their information systems Authorize system processing prior to operations and, periodically, thereafter 11

Privacy and IT Security National Institute of Standards and Technology (NIST) Several NIST publications help agencies to implement FISMA requirements: Federal Information Processing Standards Publication (FIPS PUB) 199 Standards for Security Categorization of Federal Information and Information Systems FIPS PUB 200 Minimum Security Requirements for Federal Information and Information Systems 12
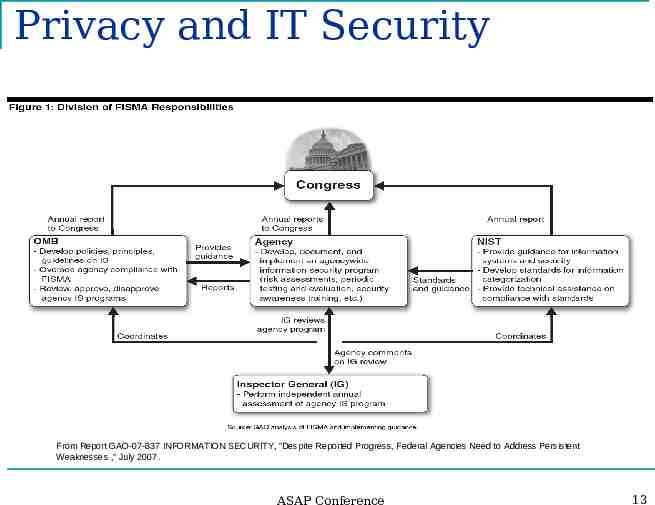
Privacy and IT Security From Report GAO-07-837 INFORMATION SECURITY, “Despite Reported Progress, Federal Agencies Need to Address Persistent Weaknesses ,“ July 2007. ASAP Conference 13

Privacy and IT Security Privacy Defined 14
Privacy and IT Security Privacy Defined Samuel D. Warren, a Boston attorney, and Louis D. Brandeis, a justice of the United States Supreme Court published in the Harvard Law Review their paper titled “The Right To Privacy” (December 1890) “ the right to be let alone.” Personal control over the collection, use and disclosure of any recorded information about an identifiable individual The organization's responsibility for data protection and safeguarding personal information in its custody or control 15

Privacy and IT Security Privacy Defined (Continued) A right of privacy has been based in the U.S. Supreme Court's examination of the Constitution. Case law has interpreted the U.S Constitution to protect personal freedoms, such as the right to privacy under the 14th amendment. The 1st, 4th, and 5th Amendments also provide some protection of privacy, although in all cases the right is narrowly defined. There is also the statutory right of privacy which limits access to personal information. The right of privacy must be balanced against the agency’s need to collect, use, maintain and disseminate information about a person and that person’s expectation of privacy 16

Privacy and IT Security Definitions for Privacy & Privacy is the right of an individual to Security control your own personal information, and Confidentiality is the obligation of another party to respect privacy by not have it disclosed or used by others without permission. protecting personal information they receive, and preventing it from being used or disclosed without the subject’s knowledge and permission. Security is the means used to protect the confidentiality of personal information through physical, technical and administrative safeguards 17

Privacy and IT Security Information Technology (IT) Security Defined 18

Privacy and IT Security Information Technology Information technology has been defined as: "Any equipment, or interconnected system(s) or subsystem(s) of equipment used in the automatic acquisition, storage, manipulation, management, movement, control, display, switching, interchange, transmission, or reception of data or information by the agency.” 19

Privacy and IT Security Computer Security: A Practical Definition Defining “Computer (IT) security" is not trivial. The difficulty lies in developing a definition that is broad enough to be valid regardless of the system being described, yet specific enough to describe what security really is. In a generic sense, security is "freedom from risk or danger." In the context of computer science, security is the prevention of, or protection against, access to information by unauthorized recipients, and intentional but unauthorized destruction or alteration of that information this can be re-stated: “Security is the ability of a system to protect information and system resources with respect to confidentiality and integrity." Note that the scope of this second definition includes system resources, which include CPUs, disks, and programs, in addition to information. 20

Privacy and IT Security Computer security is not restricted to the three broad concepts. Additional ideas that are often considered part of the characteristics of computer security include: Access control -- Ensuring that users access only those resources and services that they are entitled to access and that qualified users are not denied access to services that they legitimately expect to receive Non-repudiation -- Ensuring that the originators of messages cannot deny that they in fact sent the messages 21

Privacy and IT Security Computer security characteristics include: Availability -- Ensuring that a system is operational and functional at a given moment, usually provided through redundancy; loss of availability is often referred to as "denial-ofservice" Privacy -- Ensuring that individuals maintain the right to control what information is collected about them, how it is used, who has used it, who maintains it, and what purpose it is used for 22

Privacy and IT Security Computer Security, A Functional View Analyzing security by function can be a valuable part of the security planning process addressing the following five areas: Risk avoidance -- A security fundamental that starts with questions: Does my organization or business engage in activities that are too risky? Do we really need an unrestricted Internet connection? Do we really need to computerize that secure business process? Should we standardize a desktop operating system with no access control fundamentals? Deterrence -- Reduces the threat to information assets through fear. Can consist of communication strategies designed to impress potential attackers of the likelihood of getting caught. 23

Privacy and IT Security Computer Security A Functional View (Continued) Prevention -- The traditional core of computer security. Consists of implementing safeguards and tools. Absolute prevention is theoretical, since there's a vanishing point where additional preventative measures are no longer cost-effective. Detection -- Works best in conjunction with preventative measures. When prevention fails, detection should kick in, preferably while there's still time to prevent damage. Includes log-keeping and auditing activities Recovery -- When all else fails, be prepared to pull out backup media and restore from scratch, or cut to backup servers and net connections, or fall back on a disaster recovery facility. Arguably, this function should be attended to before the others starting with recovery. 24

Privacy and IT Security In Summary, Security Plus Privacy Privacy is the right of individuals to control what information is: collected about them who maintains it how it is used, who has used it, and what purpose it is used for Security is the ability of a system to protect information and system resources with respect to: authentication data-integrity confidentiality non-repudiation data protection 25

Privacy and IT Security Annual FISMA Reporting Chief Information Officer Questions 26

Privacy and IT Security -FISMA Reporting Chief Information Officer Questions FY 2009 Question 1: System Inventory Identify the number of agency and contractors systems by component and FIPS 199 impact level (low, moderate, high). Please also identify the number of systems that are used by your agency but owned by another federal agency (i.e., ePayroll, etc.) by component and FIPS 199 impact level." 27
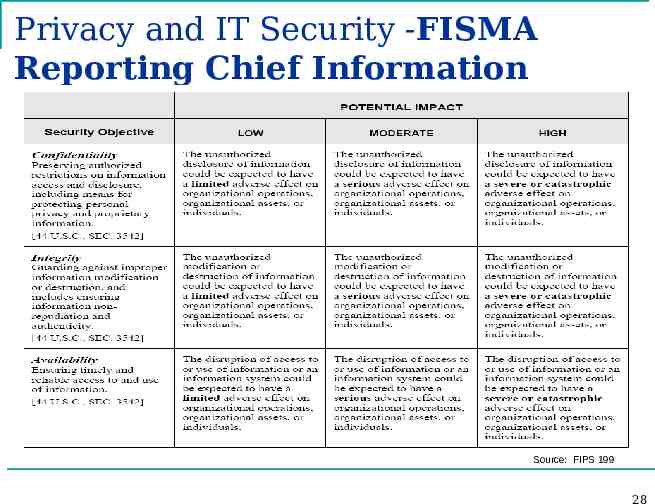
Privacy and IT Security -FISMA Reporting Chief Information Officer Questions FY 2009 Source: FIPS 199 28

Privacy and IT Security -FISMA Reporting Chief Information Officer Questions FY 2009 Question 2: Certification and Accreditation (C&A), Security Controls Testing, and Contingency Plan Testing. For the Total Number of Systems identified by Component/Bureau and FIPS System Impact Level in the table for Question 1, identify the number and percentage of systems which have: a current certification and accreditation, security controls tested and reviewed within the past year, and a contingency plan tested within in accordance with policy. Please identify all systems reported as not having a C&A. You will need to provide the System Name, and Unique Project Identifier (UPI). 29
Privacy and IT Security - FISMA Reporting Chief Information Officer Questions FY 2009 Question 3: Annual Testing and Continuous Monitoring. What tools and techniques do you use for continuous monitoring? 30

Privacy and IT Security - FISMA Reporting Chief Information Question 4: Incident Detection, Monitoring, and Response Officer Questions FY 2009 Capabilities. What tools, techniques, technologies, etc., does the agency use for incident detection? How often does the agency log and monitor activities involving access to and modification of critical information? (Answer will be a range in percentages) What percentage of systems maintain audit trails that provide a trace of user actions? Does the agency maintain an incident handling and response capability? What tools, techniques, technologies, etc. does the agency use for incident handling and response? 31

Privacy and IT Security - FISMA Reporting Chief Information Officer Questions FY 2009 Question 5: Security Awareness Training. Federal agencies and organizations cannot protect the confidentiality, integrity, and availability of information in today’s highly networked systems environment without ensuring that all people involved in using and managing IT: Understand their roles and responsibilities related to the organizational mission; Understand the organization’s IT security policy, procedures, and practices; and Have at least adequate knowledge of the various management, operational, and technical controls required and available to protect the IT resources for which they are responsible. 32

Privacy and IT Security - FISMA Reporting Chief Information Officer Questions FY 2009 Question 6: Peer-to-Peer File Sharing Does the agency explain policies regarding the use of peer-to-peer file sharing in information security awareness training, ethics training, or any other agency-wide training? 33

Privacy and IT Security - FISMA Reporting Chief Information Officer Questions Interesting Peer-to-Peer FactsFY 2009 There are 150 million users of peer-to-peer software. (Internetfilterreview.com) Students 12-18 years old make up 41% of American P2P users. (Recording Industry Association of America) 56% of files found using innocent search terms were pornographic. (House committee on Government Reform and General Accounting Office) Understanding Peer-to-Peer Networking i-SAFE America Inc. 34

Privacy and IT Security - FISMA Reporting Chief Information 1 Officer FY 2009 What is fileQuestions sharing? File sharing involves using technology that allows internet users to share files that are housed on their individual computers. Peer-to-peer (P2P) applications, such as those used to share music files, are some of the most common forms of file-sharing technology. However, P2P applications introduce security risks that may put your information or your computer in jeopardy. From US-CERT Cyber Security Tip ST05-007, produced by Mindi McDowell, Brent Wrisley, Will Dormann, Carnegie Mellon University, 2005, 2008. 1 35

Privacy and IT Security - FISMA Reporting Chief Information 1What risks does file-sharing technology Officer Questions FY 2009introduce? Installation of malicious code - When you use P2P applications, it is difficult, if not impossible, to verify that the source of the files is trustworthy. Exposure of sensitive or personal information - By using P2P applications, you may be giving other users access to personal information. Susceptibility to attack - Some P2P applications may ask you to open certain ports on your firewall to transmit the files. Denial of service - Downloading files causes a significant amount of traffic over the network. Prosecution - Files shared through P2P applications may include pirated software, copyrighted material, or pornography. If you download these, even unknowingly, you may be faced with fines or other legal action. 36
Privacy and IT Security - FISMA Reporting Chief Information 1How can you minimize these risks? Officer Questions FY 2009 The best way to eliminate these risks is to avoid using P2P applications. However, if you choose to use this technology, you can follow some good security practices to minimize your risk: use and maintain anti-virus software - Anti-virus software recognizes and protects your computer against most known viruses. install or enable a firewall - Firewalls may be able to prevent some types of infection by blocking malicious traffic before it can enter your computer. From US-CERT Cyber Security Tip ST05-007, produced by Mindi McDowell, Brent Wrisley, Will Dormann, Carnegie Mellon University, 2005, 2008. 1 37

Privacy and IT Security - FISMA Reporting Chief Information Officer Questions FY 2009 Question 7: Configuration Management Is there an agency wide security configuration policy? Yes or No. If "Yes" is selected, then agency will enter systems/platforms/applications for which configuration policies exist and give status of implementation of policies. What tools, techniques is your agency using for monitoring compliance? Indicate the status of the implementation of FDCC at your agency Agency has documented deviations from FDCC standard configuration. Yes/No 38

Privacy and IT Security - FISMA Reporting Chief Information Officer Questions FY 2009 Question 7: Configuration Management Federal Acquisition Regulation 2007-004 language, which modified "Part 39—Acquisition of Information Technology", is included in all contracts related to common security settings. Yes or No.7c.3 will be eliminated Federal Acquisition Regulation (Part 24, Protection of Privacy and Freedom of Information) 52-224-1 Privacy Act Notification 52-224-2 Privacy Act 39

Privacy and IT Security - FISMA Reporting Chief Information Officer FY 2009 Question Questions 8: Incident Reporting* How often does the agency follow documented policies and procedures for identifying and reporting incidents internally? How often does the agency comply with documented policies and procedures for timelines of reporting to USCERT? How often does the agency follow documented policies and procedures for reporting to law enforcement? *All answers are a percentage range 40

Privacy and IT Security - FISMA Reporting Chief Information Officer FYfor2009 Question 9:Questions Performance Metrics Security Policies and Procedures IT security metrics provide a practical approach to measuring information security. Metrics related roles and responsibilities are dispersed throughout an organization. Many IT security metrics can be created to measure each aspect of the organization’s IT security. Provide three (3) outcome/output-based performance metrics your agency uses to measure the effectiveness or efficiency of security policies and procedures. 41

Privacy and IT Security - FISMA Reporting Chief Information Officer 2009 Question Questions 10: HomelandFY Security Presidential Directive (HSPD-12) Policy for a Common Identification Standard for Federal Employees and Contractors Number of FISMA applications in which federal employees and contractors are using HSPD-12 Personal Identity Verification credentials for access. 42
Privacy and IT Security Privacy Impact Assessments (PIA) 43

Privacy and IT Security What is a PIA? A “Privacy Impact Assessment (PIA)--is an analysis of how information is handled: to ensure handling conforms to applicable legal, regulatory, and policy requirements regarding privacy, to determine the risks and effects of collecting, maintaining and disseminating information in identifiable form in an electronic information system, and to examine and evaluate protections and alternative processes for handling information to mitigate potential privacy risks.” OMB 03-22 (9/26/2003), EGOV 208(b) 44

Privacy and IT Security When is a PIA Required? When PII is collected, a PIA is required for: Existing information systems and electronic collections where a PIA has not previously been completed to include systems that collect PII about Federal personnel and contractors. New information systems or electronic collections: 45 Prior to developing or purchasing, and when converting paper-based records to electronic systems.

Privacy and IT Security When is a PIA not Required? 46 When the information system or electronic collection: Does not collect, maintain or disseminate personal identifying information Is a National Security System (including systems that process classified information)

Privacy and IT Security PIA/SORN Essential Elements Crosswalk 47
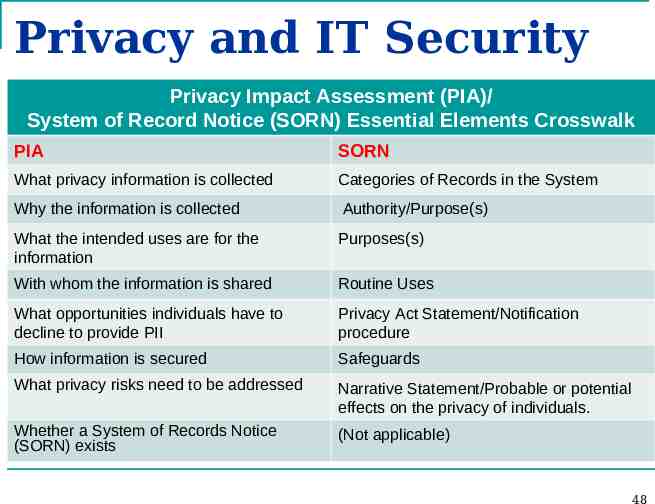
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN What privacy information is collected Categories of Records in the System Why the information is collected Authority/Purpose(s) What the intended uses are for the information Purposes(s) With whom the information is shared Routine Uses What opportunities individuals have to decline to provide PII Privacy Act Statement/Notification procedure How information is secured Safeguards What privacy risks need to be addressed Narrative Statement/Probable or potential effects on the privacy of individuals. Whether a System of Records Notice (SORN) exists (Not applicable) 48
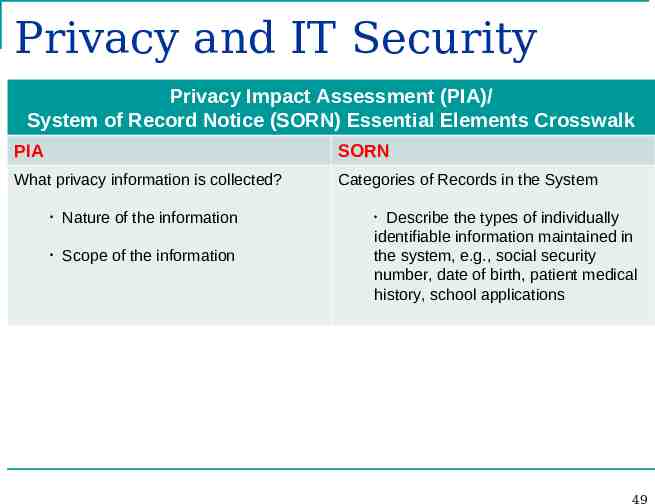
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN What privacy information is collected? Categories of Records in the System Nature of the information Scope of the information Describe the types of individually identifiable information maintained in the system, e.g., social security number, date of birth, patient medical history, school applications 49
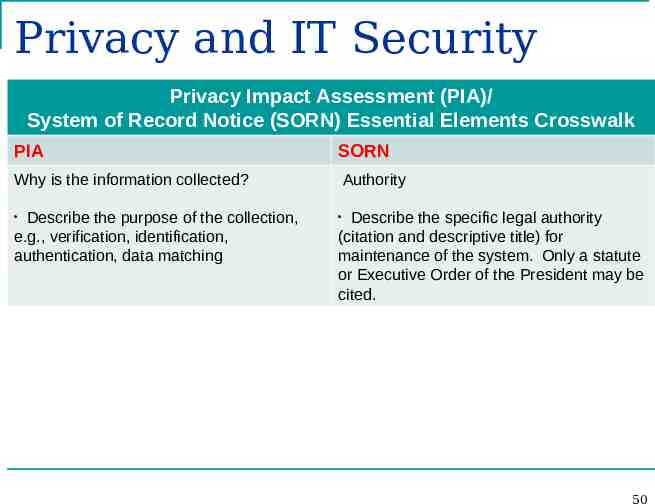
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN Why is the information collected? Authority Describe the purpose of the collection, e.g., verification, identification, authentication, data matching Describe the specific legal authority (citation and descriptive title) for maintenance of the system. Only a statute or Executive Order of the President may be cited. 50
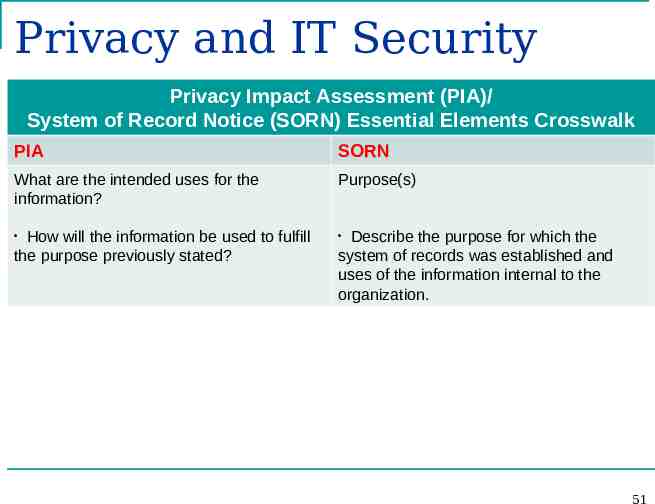
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN What are the intended uses for the information? Purpose(s) How will the information be used to fulfill the purpose previously stated? Describe the purpose for which the system of records was established and uses of the information internal to the organization. 51
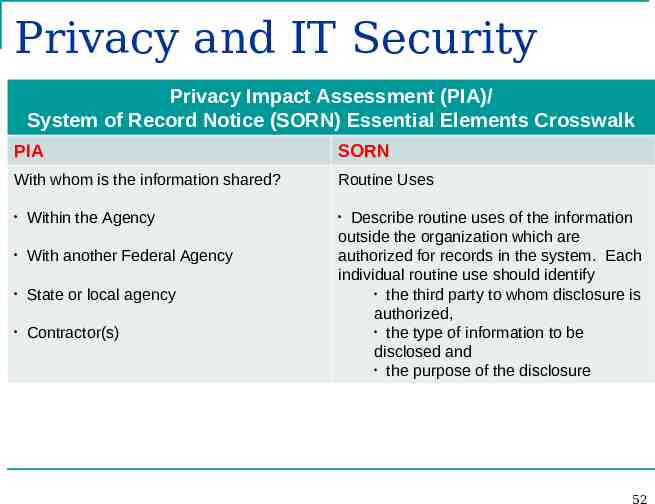
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN With whom is the information shared? Routine Uses Within the Agency With another Federal Agency State or local agency Contractor(s) Describe routine uses of the information outside the organization which are authorized for records in the system. Each individual routine use should identify the third party to whom disclosure is authorized, the type of information to be disclosed and the purpose of the disclosure 52
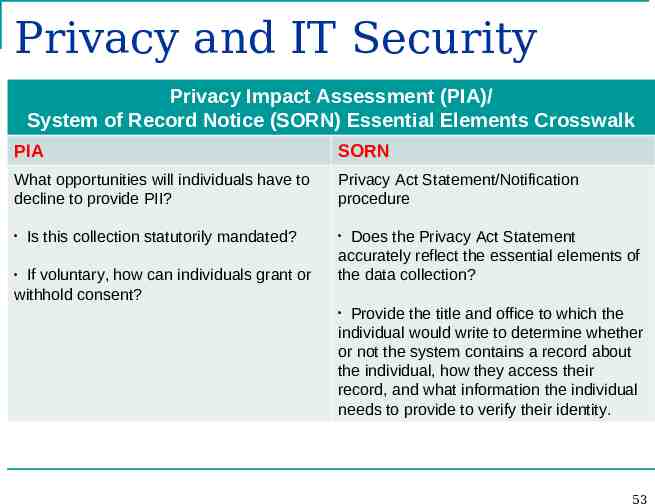
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN What opportunities will individuals have to decline to provide PII? Privacy Act Statement/Notification procedure Is this collection statutorily mandated? If voluntary, how can individuals grant or withhold consent? Does the Privacy Act Statement accurately reflect the essential elements of the data collection? Provide the title and office to which the individual would write to determine whether or not the system contains a record about the individual, how they access their record, and what information the individual needs to provide to verify their identity. 53
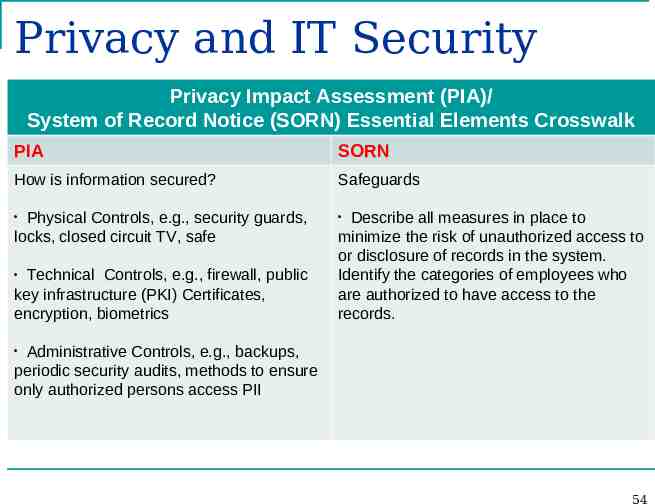
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN How is information secured? Safeguards Physical Controls, e.g., security guards, locks, closed circuit TV, safe Technical Controls, e.g., firewall, public key infrastructure (PKI) Certificates, encryption, biometrics Describe all measures in place to minimize the risk of unauthorized access to or disclosure of records in the system. Identify the categories of employees who are authorized to have access to the records. Administrative Controls, e.g., backups, periodic security audits, methods to ensure only authorized persons access PII 54
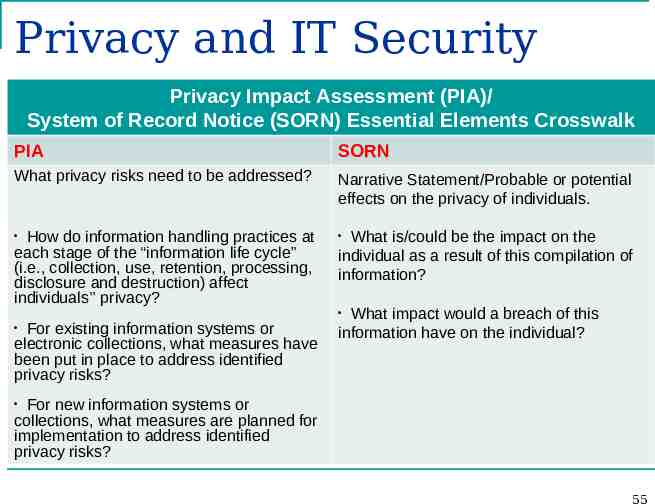
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN What privacy risks need to be addressed? Narrative Statement/Probable or potential effects on the privacy of individuals. How do information handling practices at each stage of the “information life cycle” (i.e., collection, use, retention, processing, disclosure and destruction) affect individuals’’ privacy? For existing information systems or electronic collections, what measures have been put in place to address identified privacy risks? What is/could be the impact on the individual as a result of this compilation of information? What impact would a breach of this information have on the individual? For new information systems or collections, what measures are planned for implementation to address identified privacy risks? 55
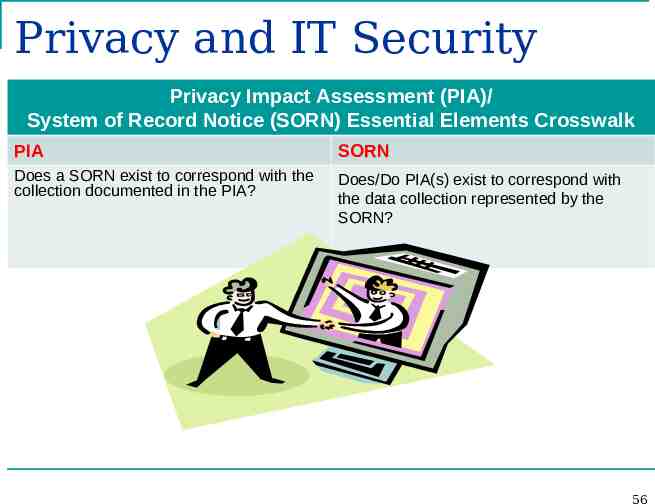
Privacy and IT Security Privacy Impact Assessment (PIA)/ System of Record Notice (SORN) Essential Elements Crosswalk PIA SORN Does a SORN exist to correspond with the collection documented in the PIA? Does/Do PIA(s) exist to correspond with the data collection represented by the SORN? 56
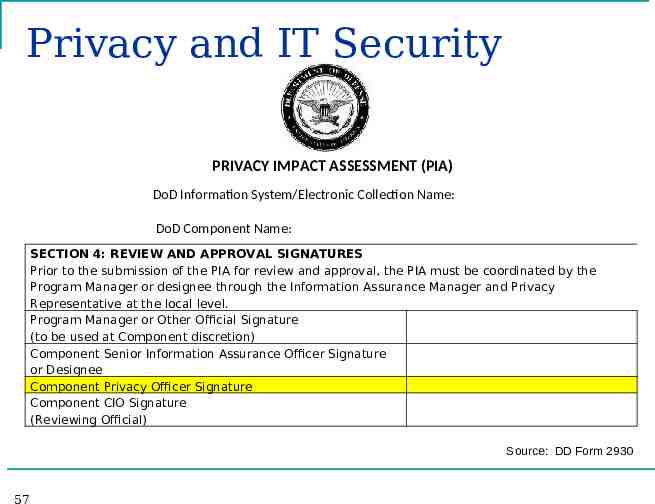
Privacy and IT Security PRIVACY IMPACT ASSESSMENT (PIA) DoD Information System/Electronic Collection Name: DoD Component Name: SECTION 4: REVIEW AND APPROVAL SIGNATURES Prior to the submission of the PIA for review and approval, the PIA must be coordinated by the Program Manager or designee through the Information Assurance Manager and Privacy Representative at the local level. Program Manager or Other Official Signature (to be used at Component discretion) Component Senior Information Assurance Officer Signature or Designee Component Privacy Officer Signature Component CIO Signature (Reviewing Official) Source: DD Form 2930 57

Privacy and IT Security Conclusion-Way Ahead 58

Privacy and IT Security Lessons in Privacy and Security, can they exist together? Quote: “The thing I think should never be lost in our discussion, is the discussion about privacy I’ve said for along time, privacy and security are two sides of the same coin. Very clearly, without security, we have no privacy. As I was going through and discussing with leadership coming into this position, I always made sure we had a discussion about privacy.” Also spoke about privacy, security and innovation, an often challenged viewpoint by security people. Howard Schmidt, January 29, 2010 in first speech as White House Cybersecurity coordinator in a speech about privacy, security and innovation. 59

Privacy and IT Security Important Lessons: What Can Be Done Organizations should implement goals and consider the following: Update privacy and security policies Be aware of how and what personal information is collected, transmitted, and processed All need to understand their specific information environment to control and protect it. A Privacy official needs to understand Security, and a Security official needs to understand Privacy Need top-down commitment to implement successful data protection programs. 60

Privacy and IT Security Conclusion-What important lessons should we learn? IT/Security staff need to have a basic understanding of privacy protection laws (especially the Privacy Act) Privacy staff needs to understand security laws Which should lead to positive, transparent relationships Include records management Ensure the information is promptly disposed of in accordance with approved records control schedules. Could reduce potential breaches Don’t look at security issues and privacy issues in a vacuum, they are often interrelated 61
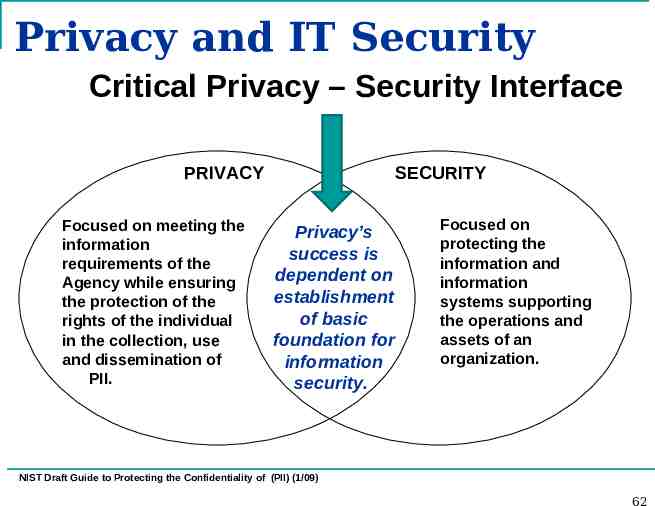
Privacy and IT Security Critical Privacy – Security Interface PRIVACY Focused on meeting the information requirements of the Agency while ensuring the protection of the rights of the individual in the collection, use and dissemination of PII. SECURITY Privacy’s success is dependent on establishment of basic foundation for information security. Focused on protecting the information and information systems supporting the operations and assets of an organization. NIST Draft Guide to Protecting the Confidentiality of (PII) (1/09) 62

Questions? 63






