Introductory Computer Security CS461/ECE422 Fall 2010 Susan Hinrichs
27 Slides220.00 KB

Introductory Computer Security CS461/ECE422 Fall 2010 Susan Hinrichs Slide #1-1
Outline Administrative Issues Class Overview Information Assurance Overview – – – – Components of computer security Threats, Vulnerabilities, Attacks, and Controls Policy Assurance Slide #1-2
Administrivia Staff – Susan Hinrichs, lecturer – Sonia Jahid, TA – Jurand Nogiec, TA Communications – Class web page http://www.cs.illinois.edu/class/fa09/cs461 – Newsgroup cs461 Office Hours – Susan: 12:30-1:30pm Wednesday and after class – Sonia and Jurand: TBA Slide #1-3

More Administrivia Grades – 2 midterms worth 25% each. Tentatively: October 6 and November 17. – Final worth 35%. 8am, December 16. – Roughly weekly homework worth 15%. Can drop low homework. 8 homeworks last year. – Extra project worth 20% for grad students taking for 4 credits – Submit homework via compass Class Sections – Online students: geographically distributed – ECE and CS 3 and 4 credit sections Slide #1-4
A Few Words on Class Integrity Review department and university cheating and honor codes: – https://agora.cs.illinois.edu/display/under gradProg/Honor Code – http://admin.illinois.edu/policy/code/artic le1 part4 1-402.html This has been an issue in the past Expectations for exams, homeworks, projects, and papers Slide #1-5

Class Readings Text Computer Security: Art and Science by Matt Bishop Additional readings provided via compass or public links Books on reserve at the library Slide #1-6

Class Format Meet three times a week Mostly lecture format – Will attempt to have a class exercise about once a week. Will be noted on class web site. – Will attempt to make this relevant for online students too. Lectures video taped for online students – All have access to tapes. Link on class web site. A few lectures will be video only. Noted on schedule – Will still play video in class Posted slides not sufficient to master material alone Slide #1-7

Class communication Limited physical access – Lecturer part time on campus Use technology to help – Newsgroup for timely, persistent information – Email and phone Slide #1-8

Security Classes at UIUC Three introductory courses – Information Assurance (CS461/ECE422) Covers NSA 4011 security professional requirements Taught every semester – Computer Security (CS463/ECE424) Continues in greater depth on more advanced security topics Taught every semester or so – Applied Computer Security Lab Taught last spring as CS498sh Will be CS460 With CS461 covers NSA 4013 system administrator requirements Two of the three courses will satisfy the Security Specialization in the CS track for Computer Science majors. Slide #1-9

More Security Classes at UIUC Theoretical Foundations of Cryptography – Prof Manoj Prabhakaran and Prof. Borisov Security Reading Group CS591RHC Advanced Computer Security CS563 Math 595/ECE 559 – Cryptography Local talks http://www.iti.illinois.edu/content/seminars-and -events ITI Security Roadmap – http://www.iti.illinois.edu/content/security Slide #1-10

Security in the News DNS flaws – Dan Kamisky found flaw in widely used DNS protocol requiring upgrade of network infrastructure – http://blog.wired.com/27bstroke6/2008/07/details-of-dns.html InfoWar – Estonia http://blog.wired.com/27bstroke6/2007/08/cyber-war-and-e.html Extortion – Threaten DDoS attack unless company pays up – DDoS protection from carriers can cost 12K per month Privacy/Identity theft – Albert Gonzalez and 130 million credit card numbers. – Facebook – ChoicePoint, Bank of America, disgruntled waiter Worms – Conflicker, twitter worms – Slammer worm crashed nuclear power plant network Slide #1-11

Class Topics Mix of motivation, design, planning, and mechanisms See lecture page – http://www.cs.illinois.edu/class/fa10/cs461/ lectures.html A few open lecture spots if there are topics of particular interest May have some industry guest lectures Slide #1-12

Security Components Confidentiality – Keeping data and resources hidden Integrity – Data integrity (integrity) – Origin integrity (authentication) Availability – Enabling access to data and resources Slide #1-13

CIA Examples Slide #1-14

Threat Terms Threat – Set of circumstances that has the potential to cause loss or harm. Or a potential violation of security. Vulnerability – Weakness in the system that could be exploited to cause loss or harm Attack – When an entity exploits a vulnerability on system Control – A means to prevent a vulnerability from being exploited Slide #1-15
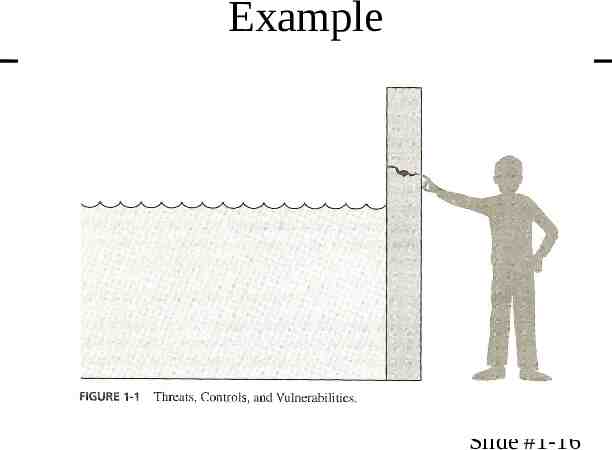
Example Slide #1-16

Classes of Threats Disclosure – Unauthorized access to information Deception – Acceptance of false data Disruption – Interruption or prevention of correct operation Usurpation – Unauthorized control of some part of a system Slide #1-17

Some common threats Snooping – Unauthorized interception of information Modification or alteration – Unauthorized change of information Masquerading or spoofing – An impersonation of one entity by another Repudiation of origin – A false denial that an entity sent or created something. Denial of receipt – A false denial that an entity received some Slide #1-18 information.

More Common Threats Delay – A temporary inhibition of service Denial of Service – A long-term inhibition of service Slide #1-19

More definitions Policy – A statement of what is and what is not allowed – Divides the world into secure and non-secure states – A secure system starts in a secure state. All transitions keep it in a secure state. Mechanism – A method, tool, or procedure for enforcing a security policy Slide #1-20

Is this situation secure? Web server accepts all connections – No authentication required – Self-registration – Connected to the Internet Slide #1-21

Trust and Assumptions Locks prevent unwanted physical access. – What are the assumptions this statement builds on? Slide #1-22

Policy Assumptions Policy correctly divides world into secure and insecure states. Mechanisms prevent transition from secure to insecure states. Slide #1-23

Another Policy Example Bank officers may move money between accounts. – Any flawed assumptions here? Slide #1-24

Assurance Evidence of how much to trust a system Evidence can include – System specifications – Design – Implementation Mappings between the levels Slide #1-25

Aspirin Assurance Example Why do you trust Aspirin from a major manufacturer? – FDA certifies the aspirin recipe – Factory follows manufacturing standards – Safety seals on bottles Analogy to software assurance Slide #1-26

Key Points Must look at the big picture when securing a system Main components of security – Confidentiality – Integrity – Availability Differentiating Threats, Vulnerabilities, Attacks and Controls Policy vs mechanism Assurance Slide #1-27