Minimizing Risk by Implementing Vulnerability Management Process
24 Slides3.55 MB

Minimizing Risk by Implementing Vulnerability Management Process On time – On Budget – On demand Edvinas Pranculis, MM, CISA, CISM

Agenda Environment, Challenges & Impact: Need for Vulnerability Management Vulnerability Management Process Capabilities Overview: QualysGuard Overview Software as a Service Model: Security & Coverage Summary Advantages & Benefits
Need for Vulnerability Management Vulnerabilities on a network are GOLD to cyber criminals: Provide unauthorized entry to networks Can expose confidential information, fuel stolen identities, violate privacy laws, or paralyse operations Exposure is extreme for networks with vulnerable devices connected by IP Sources of Vulnerabilities Programming errors Unintentional mistakes or intentional malware in General Public License software Improper system configurations Mobile users sidestepping perimeter security controls Rising attacks through viewing popular websites
Need for Vulnerability Management Despite utilization of basic defenses, network security breaches abound TJX exposed 46M records DSW exposed 1.4M records CardSystems exposed 40M records 215M reported record exposures since 2005 (actual is significantly higher) Automation is Crucial Manual detection and remediation workflow is too slow, too expensive and ineffective Attack Trends Increased professionalism and commercialization of malicious activities Threats that are increasingly tailored for specific regions Increasing numbers of multistaged attacks Attackers targeting victims by first exploiting trusted entities Convergence of attack methods Shift from “Hacking for Fame” to “Hacking for Fortune”

Need for Vulnerability Management Did we learn our lessons? Most vulnerabilities are long known before exploited Successful exploitation of vulnerabilities can cause substantial damage and financial loss A few vulnerable systems can disrupt the whole network System misconfiguration can make systems vulnerable Challenges IT Security Face NOT enough TIME, PEOPLE, BUDGET Prioritization of efforts for minimize business risks and protecting critical assets. We can’t fix all problems - what can we live with? Reduction of operational & capital expenses Adapting to accelerating change in sophistication of attacks and increasing number of regulations
Key to Security: Network Scanning Hacking Linux Exposed “ the countermeasure that will protect you, should a hacker scan your machines with a scanner, is to scan your own systems first. Make sure to address any problems and then a scan by a hacker will give him no edge ”
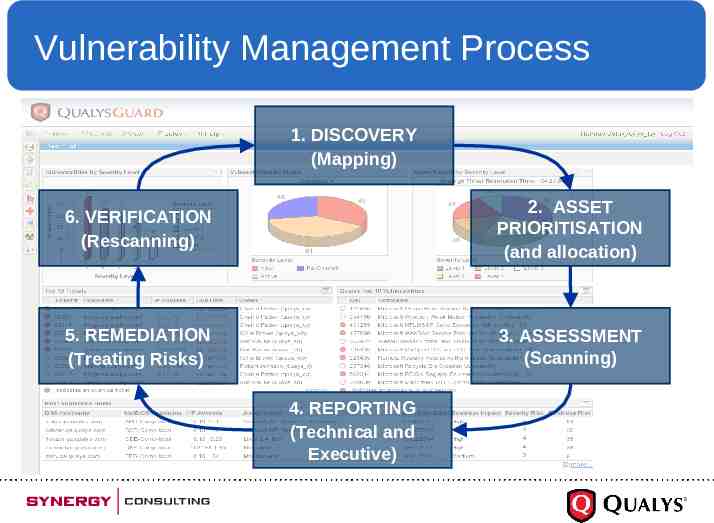
Vulnerability Management Process 1. DISCOVERY (Mapping) 6. VERIFICATION (Rescanning) 2. ASSET PRIORITISATION (and allocation) 5. REMEDIATION (Treating Risks) 3. ASSESSMENT (Scanning) 4. REPORTING (Technical and Executive)
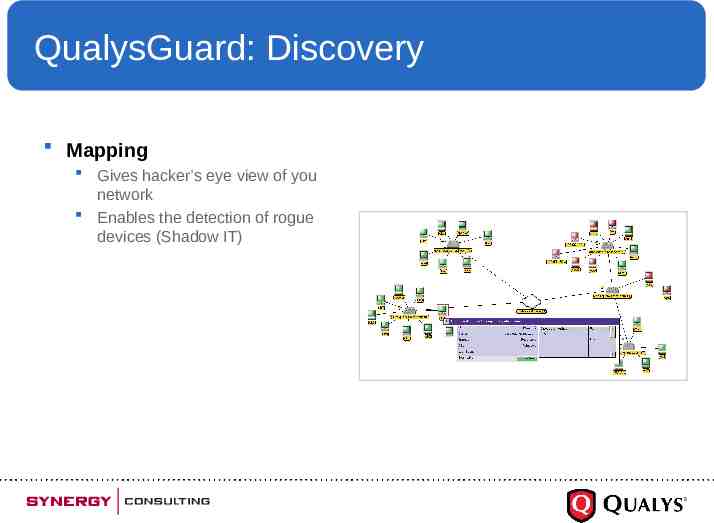
QualysGuard: Discovery Mapping Gives hacker’s eye view of you network Enables the detection of rogue devices (Shadow IT)
QualysGuard: Asset Prioritisation Asset Prioritisation Some assets are more critical to business then others Criticality depends of business impact Asset Allocation Each asset should have an owner
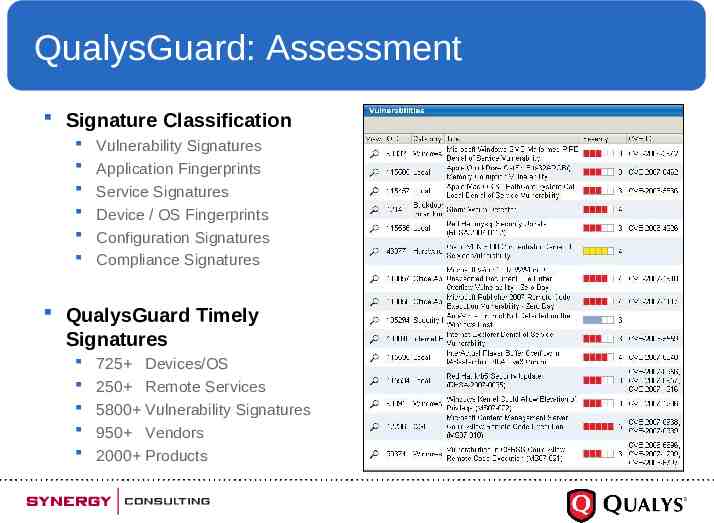
QualysGuard: Assessment Signature Classification Vulnerability Signatures Application Fingerprints Service Signatures Device / OS Fingerprints Configuration Signatures Compliance Signatures QualysGuard Timely Signatures 725 Devices/OS 250 Remote Services 5800 Vulnerability Signatures 950 Vendors 2000 Products
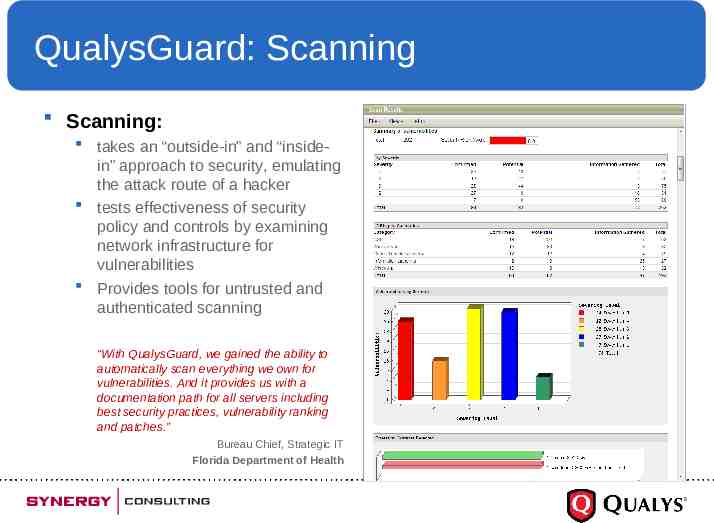
QualysGuard: Scanning Scanning: takes an “outside-in” and “insidein” approach to security, emulating the attack route of a hacker tests effectiveness of security policy and controls by examining network infrastructure for vulnerabilities Provides tools for untrusted and authenticated scanning “With QualysGuard, we gained the ability to automatically scan everything we own for vulnerabilities. And it provides us with a documentation path for all servers including best security practices, vulnerability ranking and patches.” Bureau Chief, Strategic IT Florida Department of Health
QualysGuard: Reporting Reporting: Allows for generation, storage and distribution of reports for large enterprise networks E-mail notifications allow users to review reports upon completion Reports can be generated for various compliance initiatives and security requirements: Business Policy, PCI, SOX, HIPAA, Basel II, etc. Security trend over a period of time Business risk or CVSS scoring Share reports with auditors, operation staff, security & network managers, executives
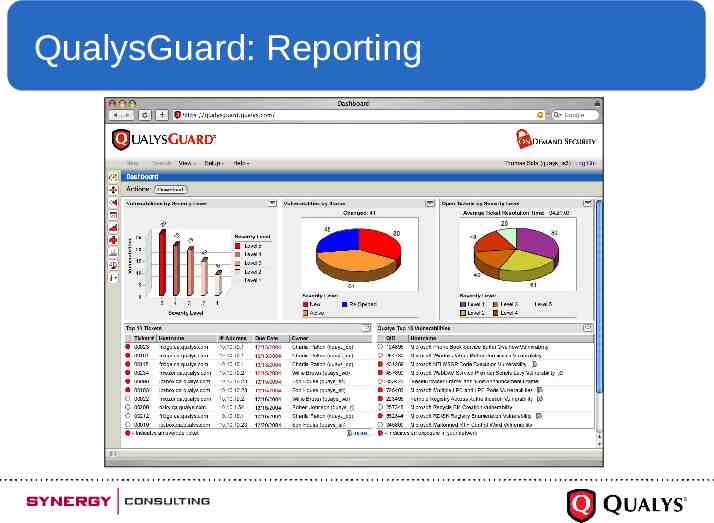
QualysGuard: Reporting
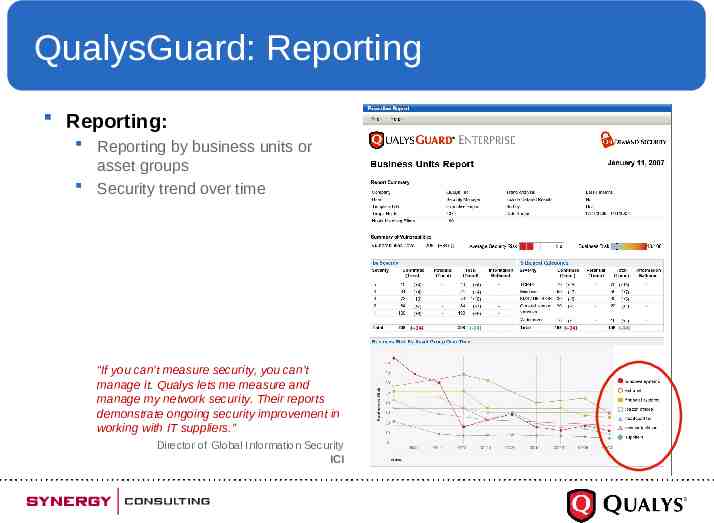
QualysGuard: Reporting Reporting: Reporting by business units or asset groups Security trend over time “If you can’t measure security, you can’t manage it. Qualys lets me measure and manage my network security. Their reports demonstrate ongoing security improvement in working with IT suppliers.” Director of Global Information Security ICI
QualysGuard: Remediation Remediation Tickets are either generated automatically upon scan completion based on polices or on demand by users from any report Trouble tickets capture complete audit trails and history of a vulnerabilities on hosts QualysGuard scanners verifies the ticket after its closed Integration with other helpdesk solutions is available through API “In vulnerability management, it’s all about response time. Qualys’ remediation agent directly assigns tickets to fix things to my network technicians. The system then tracks those fixes.” Director of Enterprise Security Wescorp
QualysGuard: Verification Re-scanning: Verifies applied patches and confirm compliance Verifies the tickets after they are closed “Before QualysGuard we had an ad hoc process; Qualys brought much stronger control and visibility into our processes. QualysGuard gives us the ability to detect our vulnerabilities across our network and really ensure that we have the level of security and compliance we need.” Chief Information Protection Officer CIGNA
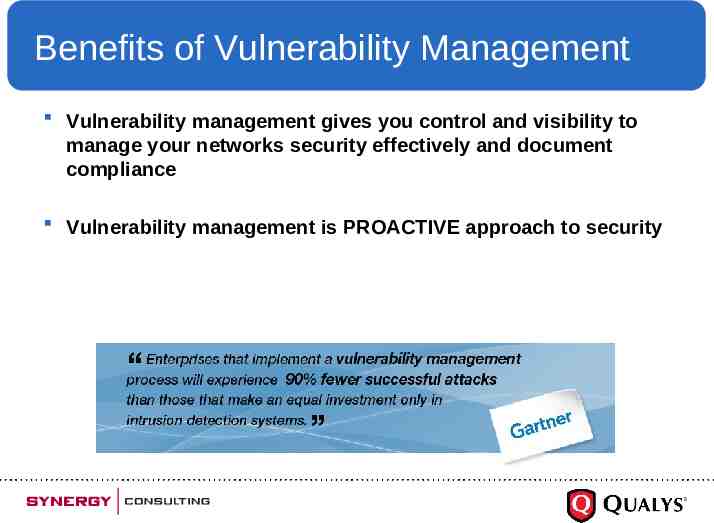
Benefits of Vulnerability Management Vulnerability management gives you control and visibility to manage your networks security effectively and document compliance Vulnerability management is PROACTIVE approach to security
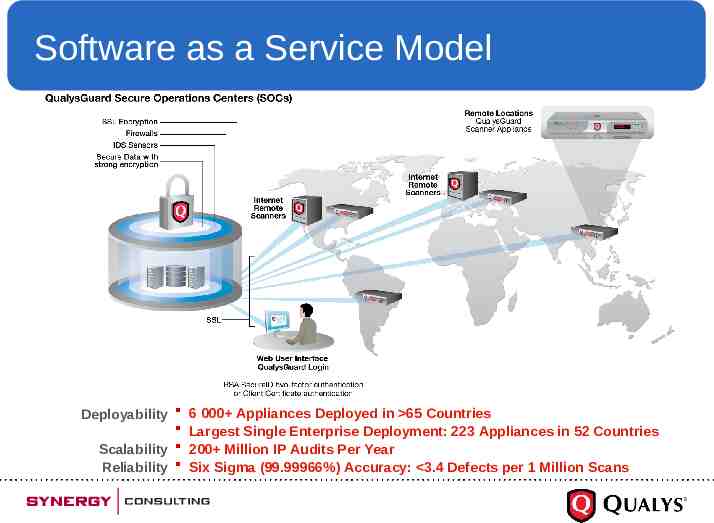
Software as a Service Model Deployability 6 000 Appliances Deployed in 65 Countries Largest Single Enterprise Deployment: 223 Appliances in 52 Countries Scalability 200 Million IP Audits Per Year Reliability Six Sigma (99.99966%) Accuracy: 3.4 Defects per 1 Million Scans

QualysGuard Security & Coverage European Secure Operation Center (Frankfurt/Germany) Multiple Security Levels 24x7 Security Monitoring Scan Data Encrypted (AES) Regular Customer On-Site Audits SAS 70, BS 7799 & TUEV Certification
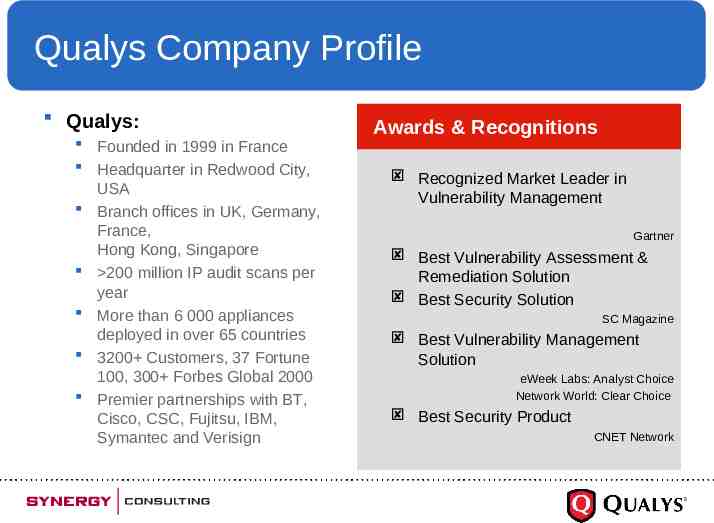
Qualys Company Profile Qualys: Founded in 1999 in France Headquarter in Redwood City, USA Branch offices in UK, Germany, France, Hong Kong, Singapore 200 million IP audit scans per year More than 6 000 appliances deployed in over 65 countries 3200 Customers, 37 Fortune 100, 300 Forbes Global 2000 Premier partnerships with BT, Cisco, CSC, Fujitsu, IBM, Symantec and Verisign Awards & Recognitions Recognized Market Leader in Vulnerability Management Gartner Best Vulnerability Assessment & Remediation Solution Best Security Solution SC Magazine Best Vulnerability Management Solution eWeek Labs: Analyst Choice Network World: Clear Choice Best Security Product CNET Network
Qualys “Hall of Fame” by Industries Insurance Portals/Internet Financial Services Retail Financial Services Technology Chemical Consulting
Qualys “Hall of Fame” by Industries Media Manufacturing Energy/Utilities Education Consumer Products Transportation Health Care Government D
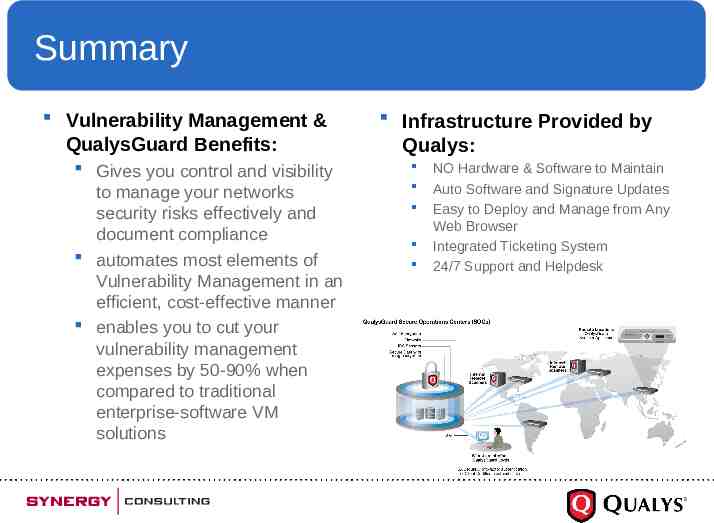
Summary Vulnerability Management & QualysGuard Benefits: Gives you control and visibility to manage your networks security risks effectively and document compliance automates most elements of Vulnerability Management in an efficient, cost-effective manner enables you to cut your vulnerability management expenses by 50-90% when compared to traditional enterprise-software VM solutions Infrastructure Provided by Qualys: NO Hardware & Software to Maintain Auto Software and Signature Updates Easy to Deploy and Manage from Any Web Browser Integrated Ticketing System 24/7 Support and Helpdesk
Q&A Thank you! [email protected] www.synergy.lt www.qualys.com