IU Data Protection & Privacy Tutorial
30 Slides1.22 MB

IU Data Protection & Privacy Tutorial

IU Data Protection & Privacy Tutorial Overview As an employee of Indiana University, YOU have a responsibility to protect the data you come in contact with every day. This tutorial is intended to provide you with an understanding of: The types of data IU collects and how it is classified Your data handling responsibilities The basic privacy laws you must comply with as an employee of the university Data Protection & Privacy INDIANA UNIVERSITY 2

IU Data Protection & Privacy Tutorial IU Data Here at IU, we collect and store many types of data in the course of our daily business. Some examples are . . . student information employment records research information personal health information (PHI) vendor information e-commerce Data Protection & Privacy INDIANA UNIVERSITY 3

IU Data Protection & Privacy Tutorial IU Data IU’s students, parents, employees, alumni, donors, and other constituents expect that the data provided to IU will be protected and handled appropriately. So, how do I protect IU data? Data Protection & Privacy INDIANA UNIVERSITY 4

IU Data Protection & Privacy Tutorial You can protect IU data by . . . #1 – Knowing how IU classifies data #2 – Handling Data Appropriately #3 – Adhering to data access principles #4 – Knowing Privacy Laws, Regulations & Policies #5 – Taking Responsibility Data Protection & Privacy INDIANA UNIVERSITY 5

IU Data Protection & Privacy Tutorial #1 – Know how IU classifies data There are four data classifications to define the access, handling, and proper disposal of data. Public University Internal Restricted Critical # 1 - D a t a C l a s s i fi c a t i o n s INDIANA UNIVERSITY 6

IU Data Protection & Privacy Tutorial Public Data that has few or no restrictions for access, disclosure, and disposal such as: Schedule of classes Course Catalog Employee salary information Employee business phone or office assignment # 1 - D a t a C l a s s i fi c a t i o n s INDIANA UNIVERSITY 7

IU Data Protection & Privacy Tutorial University Internal Data that may be accessed by employees & designated appointees of the university in the conduct of university business, such as: University ID Basic building floor plans Tenure recommendations # 1 - D a t a C l a s s i fi c a t i o n s INDIANA UNIVERSITY 8

IU Data Protection & Privacy Tutorial Restricted Data that requires specific authorization to access or disclose. Secure disposal is required. Examples include: Student class schedule, advising notes, and grades Full date of birth, ethnicity, citizenship Employee address and home phone # 1 - D a t a C l a s s i fi c a t i o n s INDIANA UNIVERSITY 9

IU Data Protection & Privacy Tutorial Critical Data that requires authorization to access and the highest level of protection! Inappropriate handling of this data can result in personal criminal or civil penalties. Secure disposal is required! This would include things like: Social Security number Driver’s license number Banking and credit card account numbers Personal health information (PHI) # 1 - D a t a C l a s s i fi c a t i o n s INDIANA 10 UNIVERSITY

IU Data Protection & Privacy Tutorial #2 – Handle Data Appropriately In addition to understanding IU data classification, it is important for you to know how to Access data appropriately Share IU data securely Store IU data securely Transmit IU data securely Dispose of IU data securely #2-Appropriate Data Handling INDIANA UNIVERSITY 11

IU Data Protection & Privacy Tutorial Protect your IU Passphrase! Never share it with anyone Never use it for other applications and services not approved by the university Always say “NO” if prompted to save in memory Do change it at least every 2 years If you suspect your passphrase has been compromised, do change it as soon as possible and report it to [email protected] immediately. #2-Data Handling - Access (Passphrase) INDIANA UNIVERSITY 12

IU Data Protection & Privacy Tutorial Protect your Accounts! Set your screen to auto lock on all systems and devices Utilize passcodes on all mobile devices (smart phones, tablets, etc.) Encrypt mobile devices that store institutional data and/or critical mission systems Get technical assistance from the Knowledgebase or your Local Service Provider (LSP). #2-Data Handling – Access (Accounts) INDIANA UNIVERSITY 13

IU Data Protection & Privacy Tutorial Share Information Securely You may need to transfer or share information externally as part of your job. Three secure methods for sharing restricted data include: 1. Slashtmp.iu.edu for all classifications of data including critical data 2. Box Entrusted Data Account for restricted data 3. Box Health Data Account for protected health information (PHI) and some restricted data #2-Data Handling – Share Securely INDIANA UNIVERSITY 14

IU Data Protection & Privacy Tutorial Use Email Appropriately Do NOT send restricted and critical data via email unless: Your role requires it AND Email will: a. stay within IU (does not include Imail/Umail) OR b. be encrypted by the Cisco Secure Email Encryption Service (CSEES) Never ask an external party to transfer critical information to you via email (ex. social security card, driver’s license, visa, tax returns, banking information, etc.) #2-Data Handling – Sharing with Email INDIANA UNIVERSITY 15
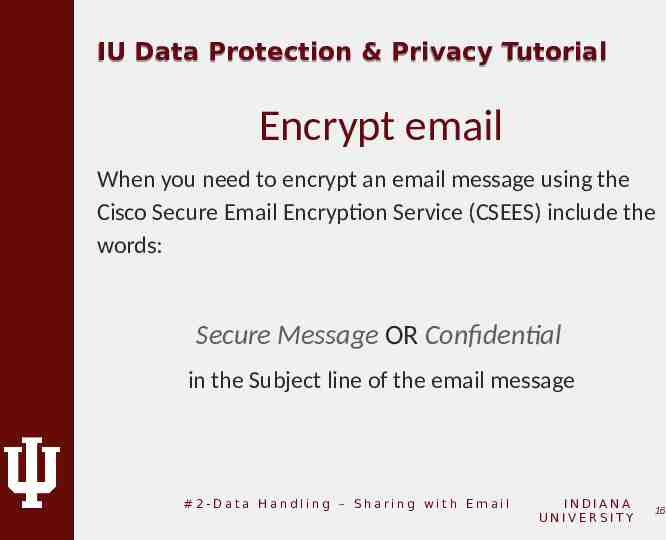
IU Data Protection & Privacy Tutorial Encrypt email When you need to encrypt an email message using the Cisco Secure Email Encryption Service (CSEES) include the words: Secure Message OR Confidential in the Subject line of the email message #2-Data Handling – Sharing with Email INDIANA UNIVERSITY 16

IU Data Protection & Privacy Tutorial Don’t Fall for Phishing Scams IU will never request your passphrase, SSN or confidential information via email. Be suspicious of email that asks you to enter or verify personal information thru a website or by replying to the message itself. Not sure? Here are some tips to keep you from getting hooked: Are you expecting an email of this nature (e.g., password reset, account expiration, wire transfer, travel confirmation, etc.)? Does the email ask for personal info (password, credit cards, SSN, etc.)? When hovering over links, do the hover-text link match the actual text? Do the actual links look like sites you do business with? Click “Reply.” Does the address in the "To" field match the sender? If from an IU email account, does the header include “external-relay.iu.edu”? If so, it’s likely not coming from a legitimate IU sender. Still not sure? Want to report an attack? Send the email message along with full email headers to [email protected] . #2-Data Handling-Share Info Securely INDIANA UNIVERSITY 17

IU Data Protection & Privacy Tutorial Never Store Sensitive Data In email Longer than required On a webserver used to host a web site open to the public On your mobile devices (laptop, USB flash drive, tablet, smartphone) unless the information is properly encrypted and you have written approval from the senior executive of your unit #2-Data Handling – Storing Securely INDIANA UNIVERSITY 18

IU Data Protection & Privacy Tutorial Storage Options at IU Intelligent Infrastructure–all data classifications Slashtmp – all data classifications Entrusted Box – restricted data or less (no critical data) Health Data Box – ePHI critical data and some restricted or less Sharepoint – restricted data or less (no critical data) Canvas – restricted data or less (no critical data) OnBase – all data classifications Secure IU file server – to be assessed by Department Ask questions if you are unsure of where to store sensitive information! #2-Data Handling – Storing Securely INDIANA UNIVERSITY 19
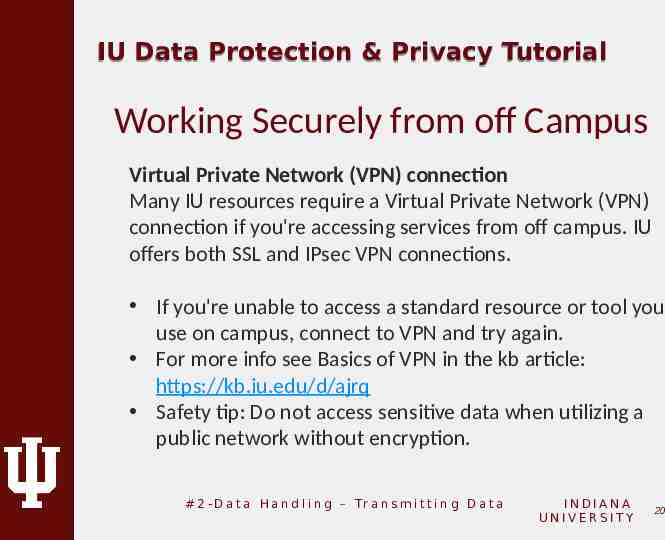
IU Data Protection & Privacy Tutorial Working Securely from off Campus Virtual Private Network (VPN) connection Many IU resources require a Virtual Private Network (VPN) connection if you're accessing services from off campus. IU offers both SSL and IPsec VPN connections. If you're unable to access a standard resource or tool you use on campus, connect to VPN and try again. For more info see Basics of VPN in the kb article: https://kb.iu.edu/d/ajrq Safety tip: Do not access sensitive data when utilizing a public network without encryption. # 2 - D a t a H a n d l i n g – Tr a n s m i t t i n g D a t a INDIANA UNIVERSITY 20

IU Data Protection & Privacy Tutorial Proper Disposal Cross-shred paper containing critical and restricted data when no longer required for business Shred Failed devices and media containing sensitive data including laptops/phones Check with your campus on what shredding services are available locally (such as IU Surplus Stores) #2-Data Handling – Proper Disposal INDIANA UNIVERSITY 21

IU Data Protection & Privacy Tutorial #3 Adhere to Data Access Principles Access data only to conduct university business Do not access data for personal profit or curiosity Limit access to the minimum amount of information needed to complete your task Respect the confidentiality and privacy of individuals whose records you access Do not share IU data with third parties unless it is part of your job responsibilities and has been approved by the appropriate data stewards Ask questions when you are unsure about data handling procedures #3-Data Access Principles INDIANA UNIVERSITY 22

IU Data Protection & Privacy Tutorial #4 Know Privacy Laws, Regs, Policies Every IU employee should also be aware of the following federal privacy regulations: The Family Educational Rights and Privacy Act (FERPA) generally prohibits the disclosure of student education records without the prior written consent of the student. The Health Insurance Portability and Accountability Act (HIPAA) imposes numerous, strict privacy and security requirements on protected health information. #4-Laws, Regs & Policies INDIANA UNIVERSITY 23
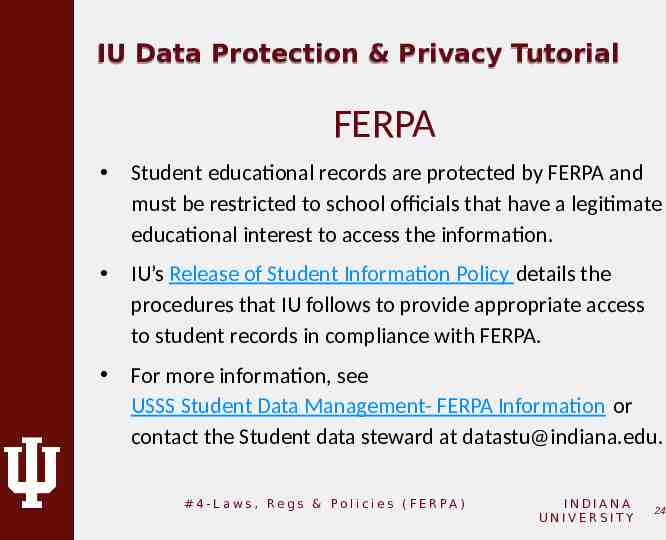
IU Data Protection & Privacy Tutorial FERPA Student educational records are protected by FERPA and must be restricted to school officials that have a legitimate educational interest to access the information. IU’s Release of Student Information Policy details the procedures that IU follows to provide appropriate access to student records in compliance with FERPA. For more information, see USSS Student Data Management- FERPA Information or contact the Student data steward at [email protected]. # 4 - L a w s , Re g s & Po l i c i e s ( F E R PA ) INDIANA UNIVERSITY 24

IU Data Protection & Privacy Tutorial HIPAA The HIPAA Privacy Rules protects all “individually identifiable health information” held or transmitted by a “covered entity,” regardless of medium. The Privacy Rule calls this information “protected health information (PHI).” # 4 - L a w s , Re g s & Po l i c i e s ( H I PA A ) INDIANA UNIVERSITY 25

IU Data Protection & Privacy Tutorial HIPAA The vast majority of IU units should maintain no personal health information (PHI) whatsoever. If you are in a unit other than the HIPAA Affected Areas (e.g., Student Health Centers, Schools of Medicine, Dentistry, Nursing, and Optometry), and you encounter records that constitute PHI, you should contact the University HIPAA Privacy and Security Compliance Office for guidance. # 4 - L a w s , Re g s & Po l i c i e s ( H I PA A ) INDIANA UNIVERSITY 26

IU Data Protection & Privacy Tutorial Indiana Law Indiana data protection laws also help safeguard data! Indiana law Makes it a crime to disclose more than the last four digits of someone’s social security number to someone outside of the university (unless specific exceptions apply) Requires IU to notify anyone whose personal information is acquired by an unauthorized person Provides guidance on the proper disposal of sensitive information. #4-L aws, Regs & Policies (State ) INDIANA UNIVERSITY 27

IU Data Protection & Privacy Tutorial Reporting an Incident All individuals are required to immediately report the following: Suspected or actual security breaches of information Abnormal systematic unsuccessful attempts to compromise information Suspected or actual weaknesses in the safeguards protecting information You should notify UISO by phone (call until you get to a human) AND you should email [email protected] # 5 - Ta k e R e s p o n s i b i l i t y - R e p o r t i n g INDIANA UNIVERSITY 28

IU Data Protection & Privacy Tutorial Data Protection is a Priority Thanks for taking a moment to review your data responsibilities and please make it a priority to protect the IU data you manage in your daily work! Additional resources on data protection and privacy can be found at: http://datamgmt.iu.edu/ https://protect.iu.edu/ # 5 - Ta k e R e s p o n s i b i l i t y - P r i o r i t y INDIANA UNIVERSITY 29

IU Data Protection & Privacy Tutorial A Final Note To be entrusted with access to Indiana University data and systems, employees must accept responsibility for, and stay informed of, IU policies and standards of acceptable use, as affirmed in the Acceptable Use Agreement, on a biennial basis. If you have not reviewed the agreement or attested to it in the last 24 months, please take a moment to review it. Also, please note that additional system access may have other training requirements, such as FERPA and HIPAA compliance training. This tutorial does not replace these requirements. # 5 - Ta k e R e s p o n s i b i l i t y – U s e A g r e e m e n t INDIANA UNIVERSITY 30