INTERNET OF THINGS(18EC64) MODULE-3
34 Slides2.11 MB
INTERNET OF THINGS(18EC64) MODULE-3
THE BUSINESS CASE FOR IP Data flowing from or to “things” is consumed, controlled, or monitored Dedicated applications are then run over virtualized or traditional operating systems or on network edge platforms (for ex-ample, fog computing). The system solutions combining various physical and data link layers call for an architectural approach with a common layer(s) independent from the lower (connectivity) and/or upper (application) layers --iP Llayer-1990s Ip is preferred in both IT and OT

K E Y A D VA N TA G E S O F I N T E R N E T PROTOCOL Open and standards-based Versatile Ubiquitous Scalable Manageable and highly secure Stable and resilient Consumers’ market adoption The innovation factor

A D O P T I O N O R A D A P TAT I O N O F T H E INTERNET PROTOCOL Bidirectional versus unidirectional data flow Overhead for last-mile communications paths Data flow model Network diversity
T H E N E E D F O R O P T I M I S AT I O N Constrained nodes Devices that are very constrained in resources, may communicate infrequently to transmit a few bytes, and may have limited security and management capabilities Devices with enough power and capacities to implement a stripped-down IP stack or non-IP stack. Devices that are similar to generic PCs in terms of computing and power resources but have constrained networking capacities, such as bandwidth

CONSTRAINED NETWORKS Network bandwidth capacity was restrained Constrained networks have unique characteristics and requirements They operate between a few kbps and a few hundred kbps Control plane traffic must also be kept at a minimum The power consumption in battery-powered nodes must be considered Constrained nodes and networks pose major challenges for IoT connectivity in the last mile

IP VERSIONS Application Protocol Cellular Provider and Technology Serial Communications IPv6 Adaptation Layer
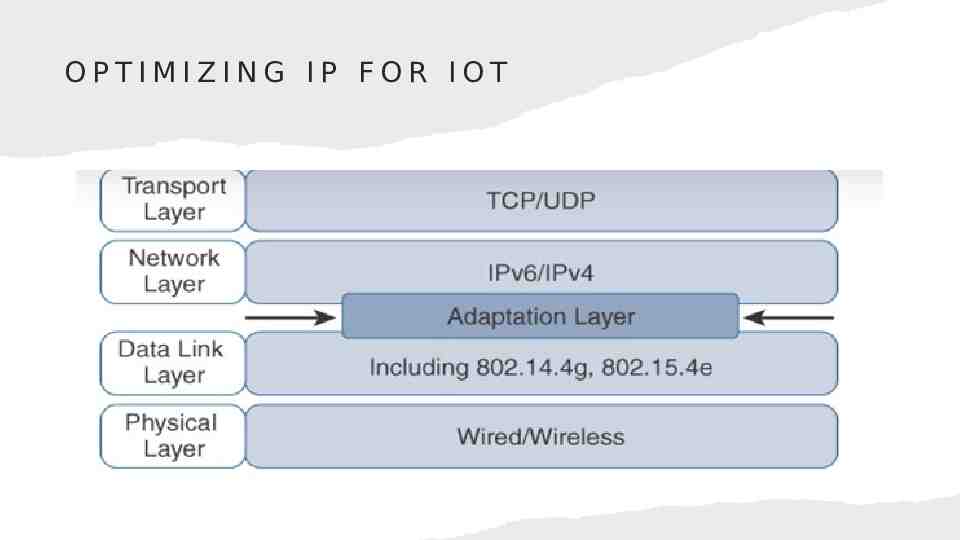
OPTIMIZING IP FOR IOT
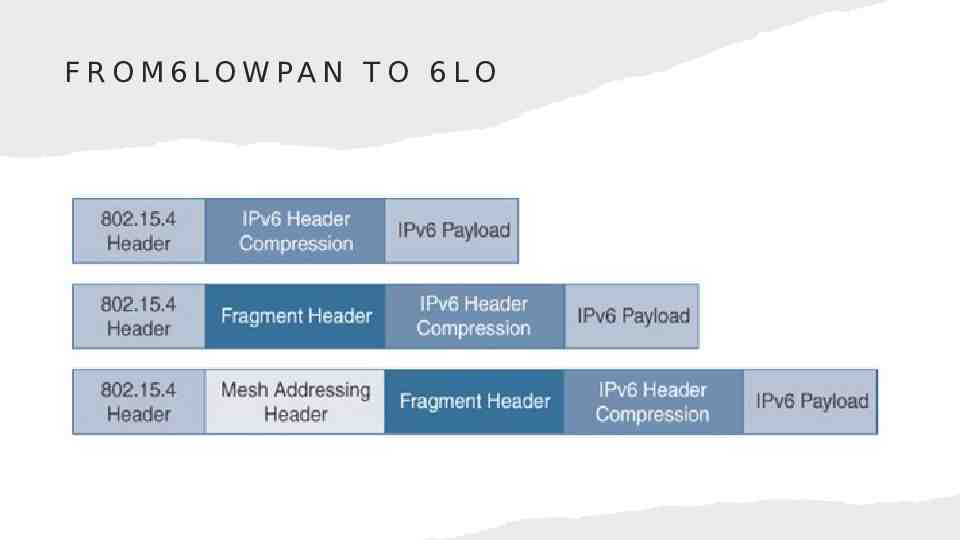
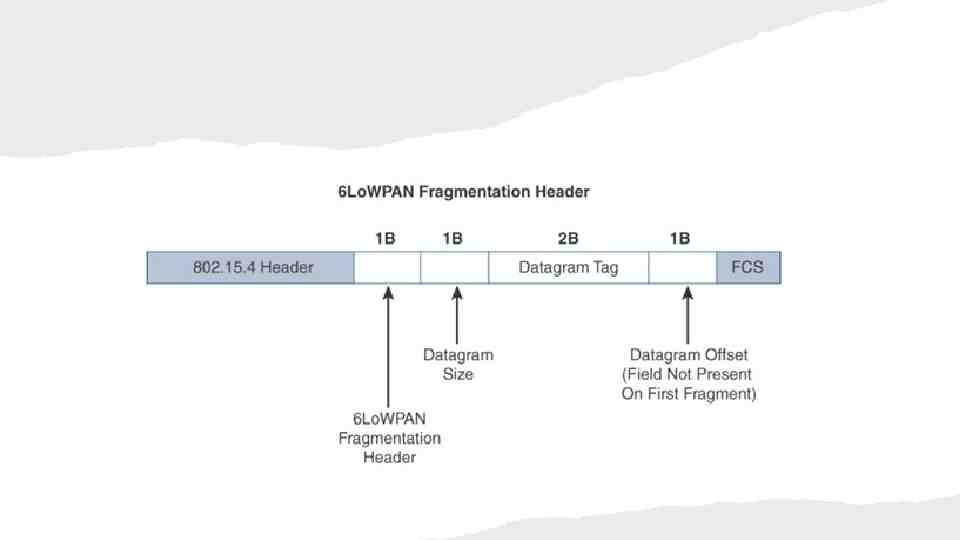
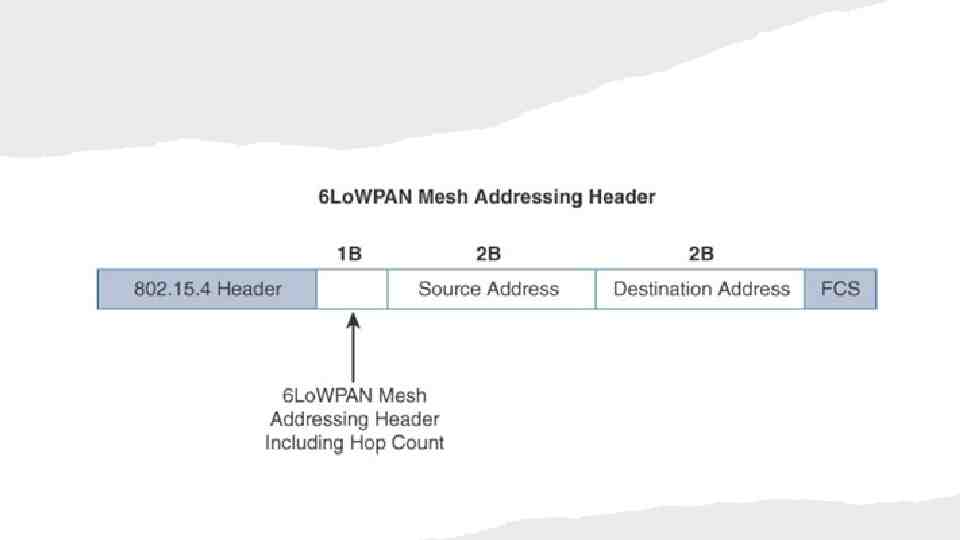
F R O M 6 LO W PA N T O 6 LO
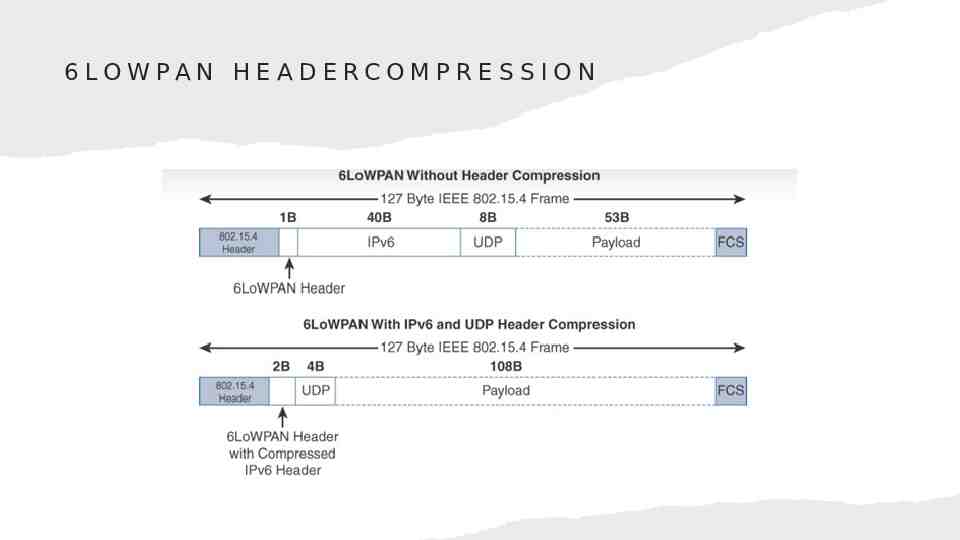
6 LO W PA N H E A D E RC O M P R E S S I O N
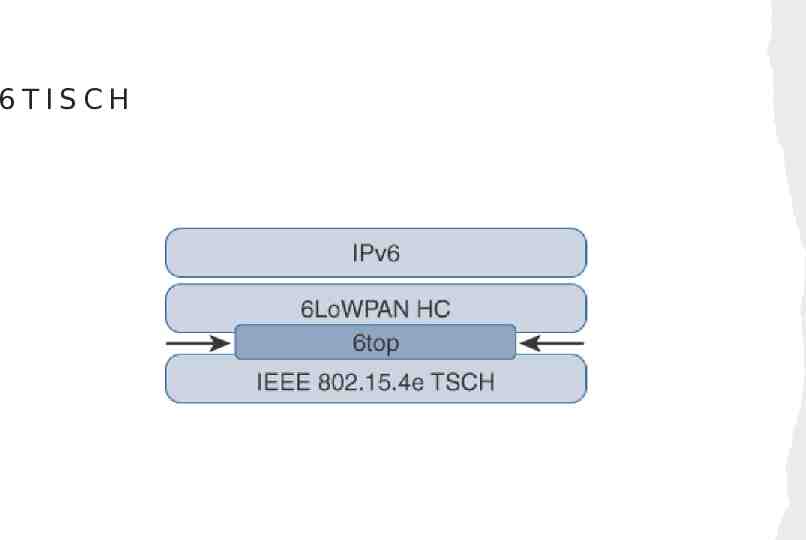
6TISCH
5TISCHSCHEDULEMANAGEMENT METHODS Static scheduling Neighbor-to-neighbor scheduling Remote monitoring and scheduling management Hop-by-hop scheduling
6 T I S C H F ORWA R D I N G M O D E L S Track Forwarding (TF) Fragment forwarding (FF) IPv6 Forwarding (6F)

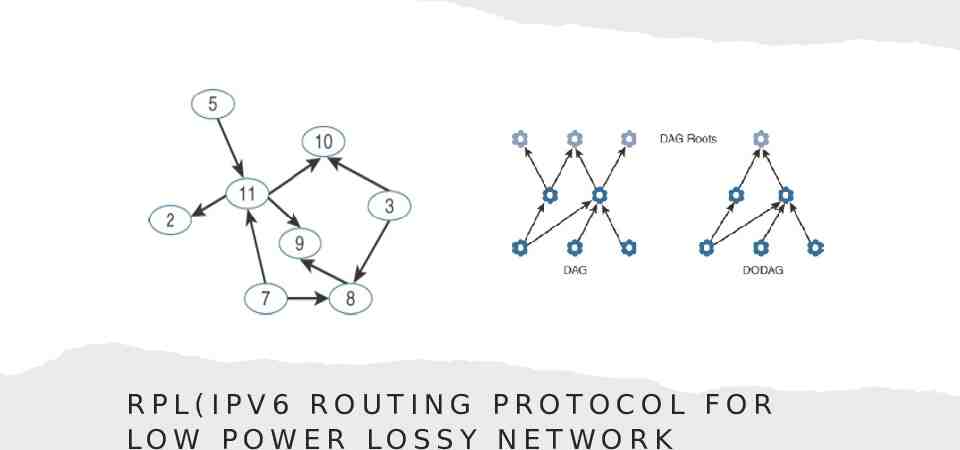
RPL(IPV6 ROUTING PROTOCOL FOR LOW POWER LOSSY NETWORK

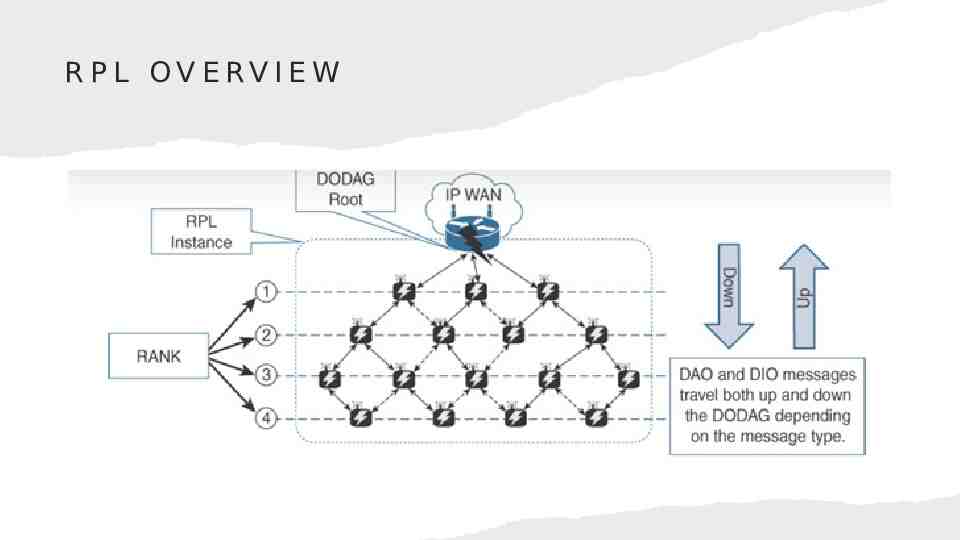
R P L OV E RV I E W
RPL METRICES Expected Transmission Count (ETX) Hop Count Latency Link Quality Level Link Color Node State and Attribute Node Energy Throughput
A U T H E N T I C AT I O N A N D E N C RY P T I O N ON CONSTRAINED NODES Authentication and Authorization for Constrained Environments (ACE) DTLS in Constrained Environments (DICE)
PROFILES AND COMPLIANCES Internet Protocol for Smart objects (IPSO) Alliance Wi-SUN Alliance Thread IPv6 Ready Logo

A P P L I C AT I O N P R O T O C O L S F O R I O T Transmission Control Protocol (TCP) -transport large volumes of data into smaller sets of packets -reassembly in a correct sequence, flow control and window adjustment, and retransmission of lost packets User Datagram Protocol (UDP) -Domain Name System (DNS) -Dynamic Host Control Protocol (DHCP) -performance and latency are more import-ant than packet retransmissions because re-sending a lost voice or video packet does not add value

I O T A P P L I C AT I O N T R A N S P O RT METHODS Application layer protocol not present

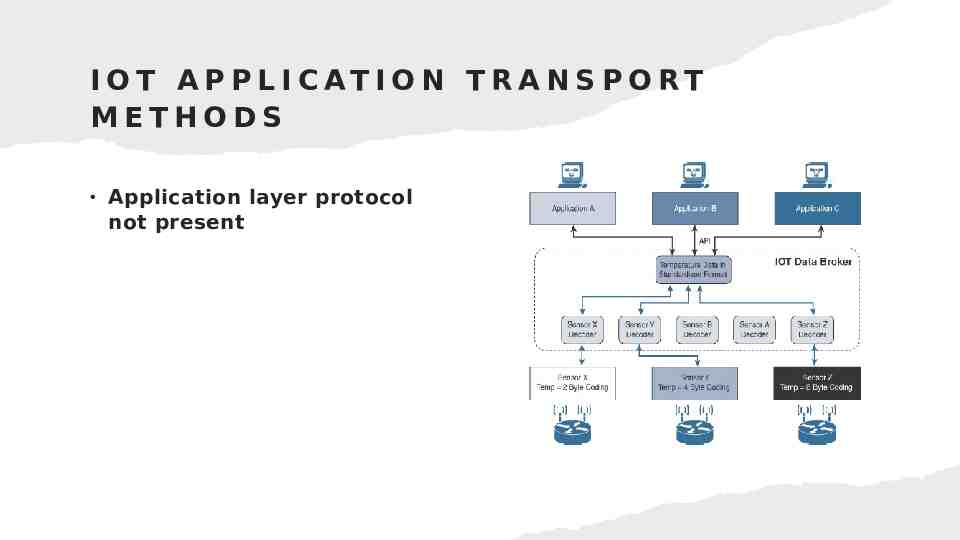
Supervisory control and data acquisition (SCADA) Adapting SCADA for IP
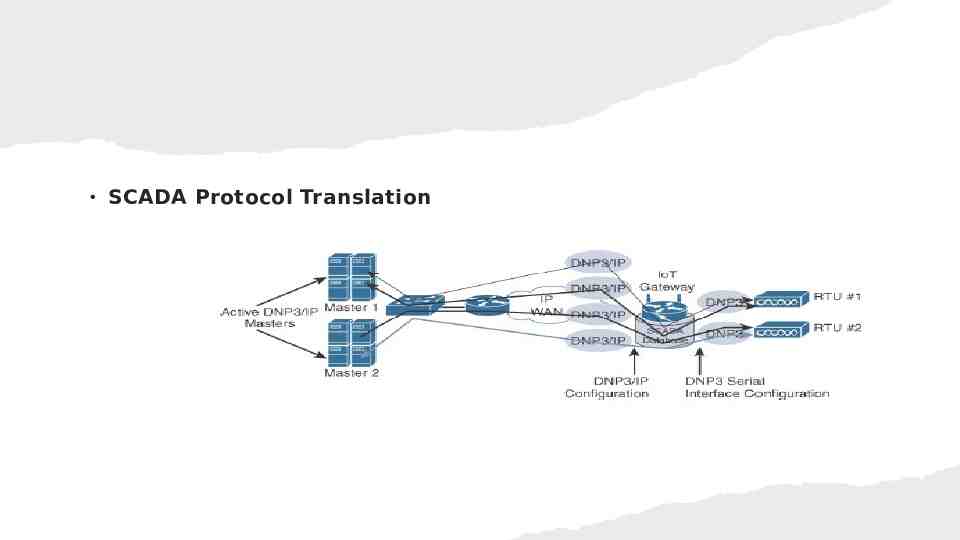
SCADA Protocol Translation
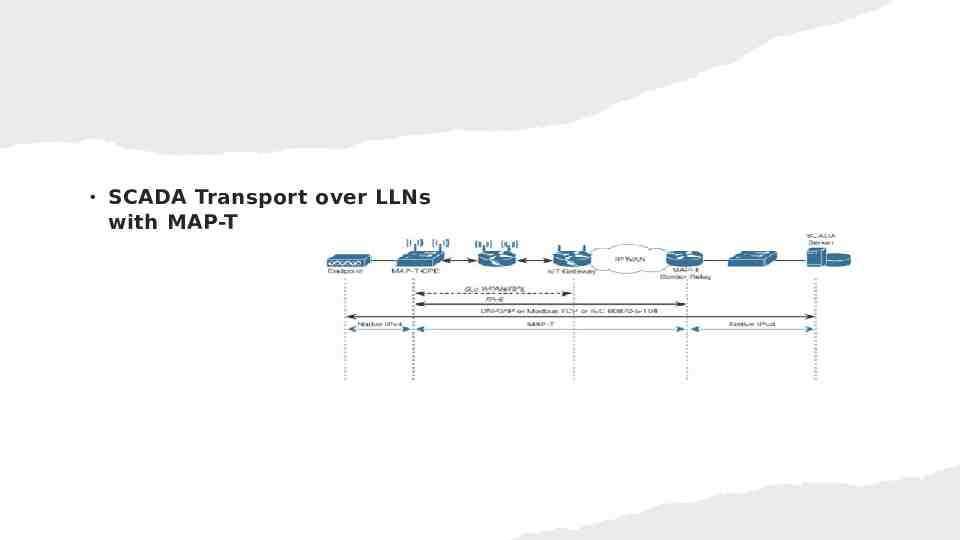
SCADA Transport over LLNs with MAP-T
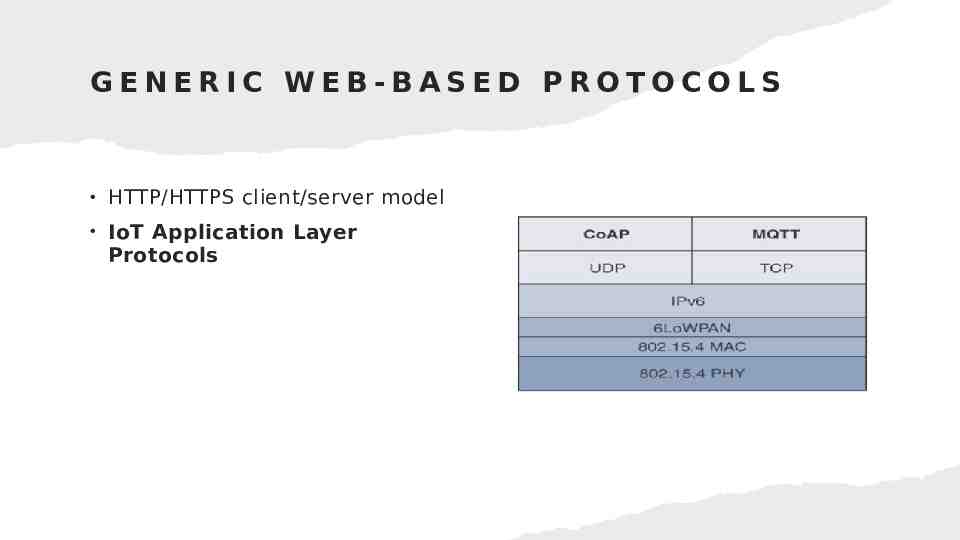
GENERIC WEB-BASED PROTOCOLS HTTP/HTTPS client/server model IoT Application Layer Protocols
COAP Constrained Application Protocol (CoAP) RFC 6690: Constrained RESTful Environments (CoRE) Link Format RFC 7252: The Constrained Application Protocol (CoAP) RFC 7641: Observing Resources in the Constrained Application Protocol (CoAP) RFC 7959: Block-Wise Transfers in the Constrained Application Protocol (CoAP) RFC 8075: Guidelines for Mapping Implementations: HTTP to the Constrained Application Protocol (CoAP).
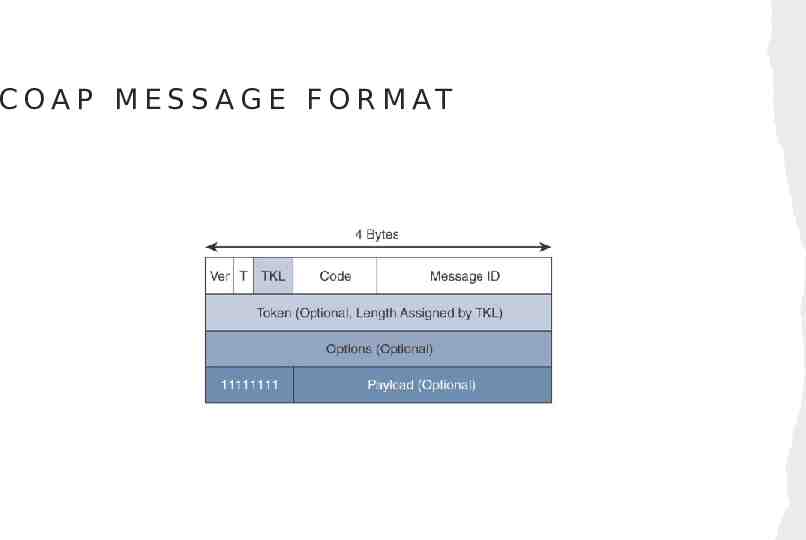
C O A P M E S S A G E F O R M AT

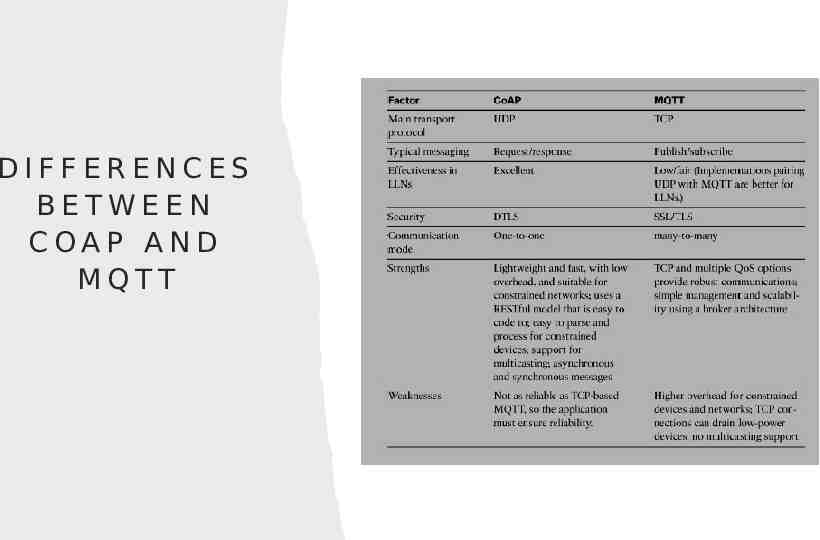
DIFFERENCES BETWEEN COAP AND MQTT
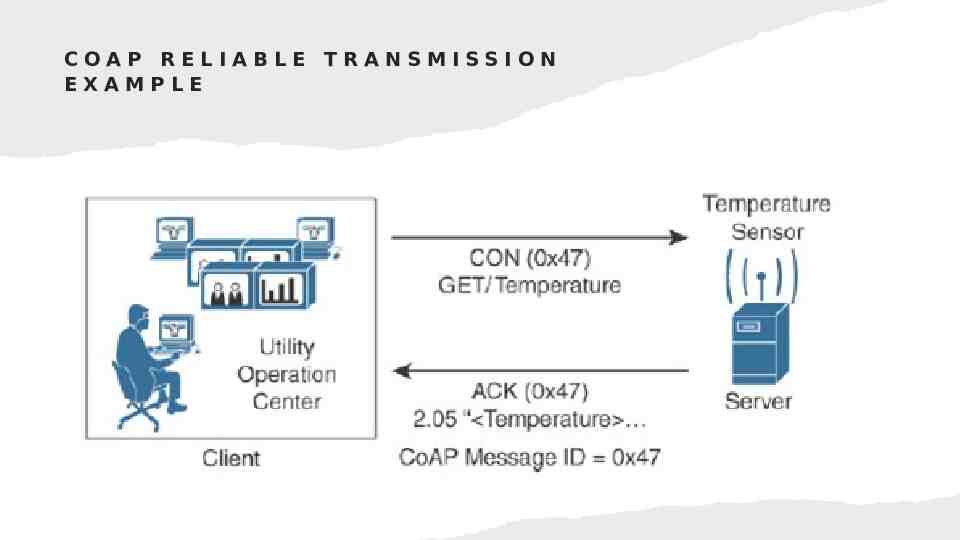
COAP RELIABLE TRANSMISSION EXAMPLE

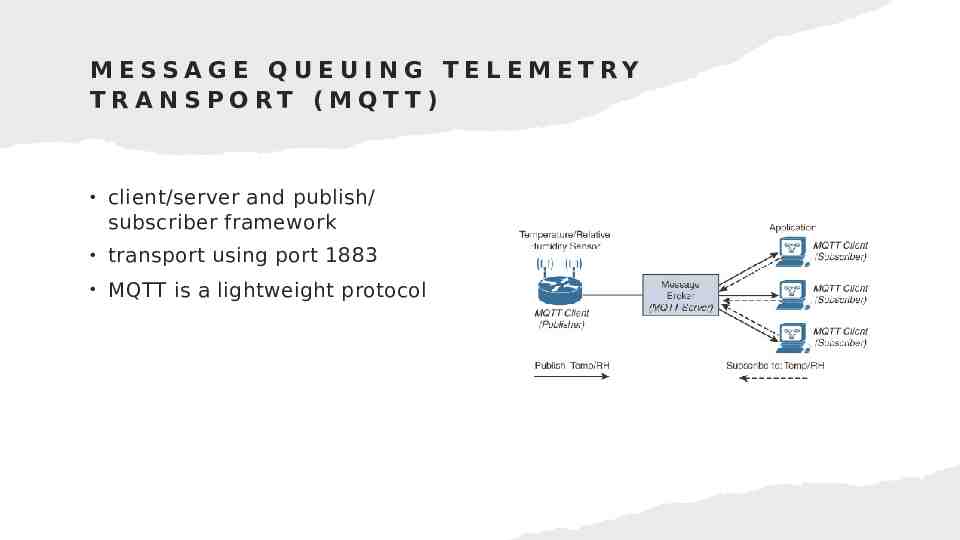
MESSAGE QUEUING TELEMETRY TRANSPORT (MQT T) client/server and publish/ subscriber framework transport using port 1883 MQTT is a lightweight protocol
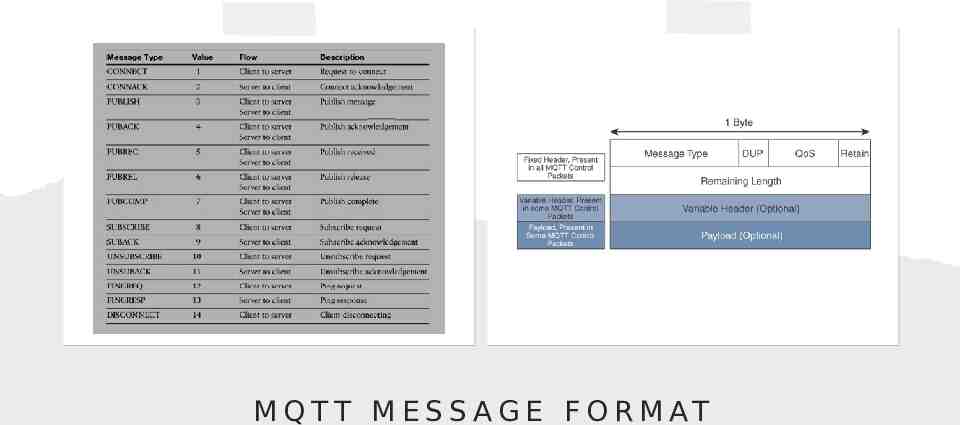
M Q T T M E S S A G E F O R M AT
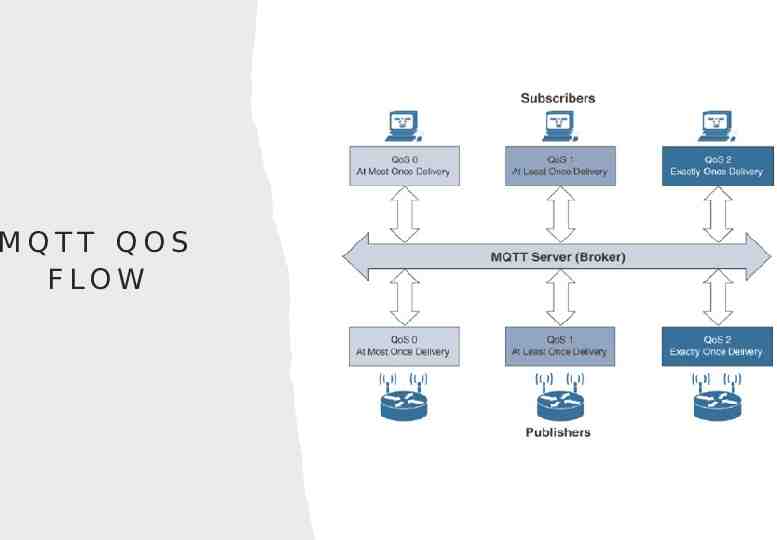
MQTT QOS FLOW
DIFFERENCES BETWEEN COAP AND MQTT