Improving data security and maintaining patient confidentiality in
35 Slides316.50 KB

Improving data security and maintaining patient confidentiality in a time of evolving information technology (IT) and limited resources

J. Jackson-Thompson, MSPH, PhD Operations Director, Missouri Cancer Registry and Research Associate Professor, Health Management & Informatics, University of MissouriColumbia [email protected] 573 882-7775 http://mcr.umh.edu

Acknowledgments Co-author: Nancy Cole, BS, CTR, MCR Operations Manager ( [email protected]) MCR Staff – Saba Yemane, BA, BS, Database Manager – Iris Zachary, CTR, MS (Informatics), Asst DBM – Alena Headd, MSIT Systems Analyst University of Missouri IT Security Team

This project was supported in part by a cooperative agreement between the Centers for Disease Control and Prevention (CDC) and the Missouri Department of Health and Senior Services (DHSS) (U58/DP000820-02/3) and a Surveillance contract between DHSS and the University of Missouri. No personal financial relationships with commercial interests relevant to this presentation existed during the past 12 months.
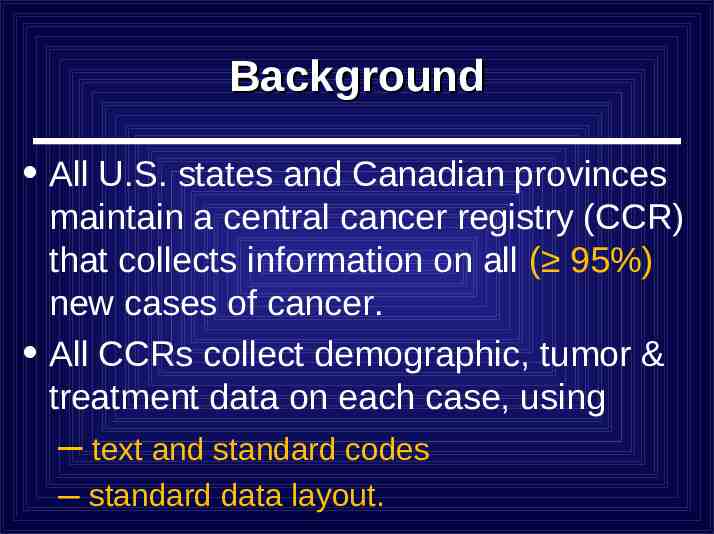
Background All U.S. states and Canadian provinces maintain a central cancer registry (CCR) that collects information on all ( 95%) new cases of cancer. All CCRs collect demographic, tumor & treatment data on each case, using – text and standard codes – standard data layout.
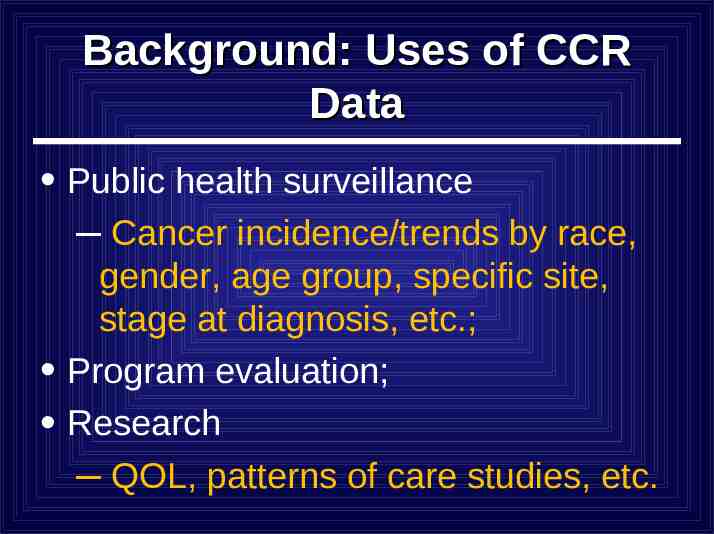
Background: Uses of CCR Data Public health surveillance – Cancer incidence/trends by race, gender, age group, specific site, stage at diagnosis, etc.; Program evaluation; Research – QOL, patterns of care studies, etc.

CCRs are required to: Meet national standards for completeness, timeliness & quality – e.g., NAACCR, CDC/NPCR, NCI/SEER Protect patient and provider confidentiality – Specific state & federal statutes/laws/regs Maintain data security – Some guidelines
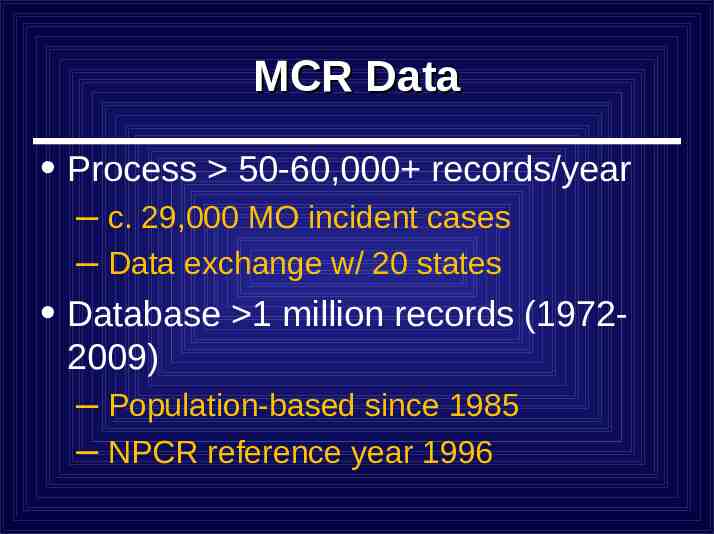
MCR Data Process 50-60,000 records/year – c. 29,000 MO incident cases – Data exchange w/ 20 states Database 1 million records (19722009) – Population-based since 1985 – NPCR reference year 1996
MCR Software Registry Plus suite of products – Started w/ Abstract Plus, then Web Plus & Link Plus – Switched to CRS Plus in 2007 Use other software as needed – SEERStat* and SAS for data analysis – MoveIT for importing VA data
MCR Approach to Data Security Similar to reporting of cancer cases: – Report not because of a law but so we can work together for better patient outcomes. Be vigilant about data security not based on statutory & contractual obligations but because it is the right thing to do: – Reporting facilities & cancer patients trust us.

MCR Concerns Minimal IT input on MCR software, hardware or data flow since 2005; No strong passwords on Registry Plus products: – Web , CRS , Abstract , Prep Strong passwords not on all laptops: – Passwords taped to some laptops.

Purpose of Presentation To describe steps taken by MCR to assess and improve the security of data, systems and processes.

Methods Reviewed MCR’s security processes and procedures. Identified and assessed data security measures already in place. Measures: – Designed to cover all data, electronic or paper – Included Policies and Procedures that were updated as needed
Examples of Data Policies and Procedures No PHI on thumb drives No PHI in e-mails or attachments Lock file cabinets & offices Only MCR staff have keys to MCR offices Send charts/records to PO Box or by FedEx Carry mail & data in locked bags

Data Security Measures Ongoing training for staff All MCR staff reminded annually by signing: –Confidentiality agreement; –Acknowledgment of state and federal laws about penalties; and –MCR laptop security policy. “The Security Mouse was here”

Weather alert changed MCR’s paper-handling policies Tornado drill – staff from another unit directed to MCR office Led to changes: – – – – – Change in drill location More locking cabinets Lock doors if leave No papers visible Cross-cut shredder

Actions re. electronic data security Requested that the University of Missouri’s (MU) IT security team audit our systems & business practices.
Data Security Structure MU – IT: dept, campus and hospital –Servers housed offsite in 24/7 IT facility –Most reporting facilities use Web Plus (VA hospitals use MoveIT) DHSS/State Office of Administration – SFTP site folder restrictions at DHSS – BCCCP data – Some path lab data (PHIN/MS)
MU Information Security Program System initiative - all 4 campuses MCR & IT Security Team met to review issues: –Data classification systems –General security procedures strong passwords, encryption, etc. –Workplace security manual –Audits

Steps for each phase of security inspection program Identification Coordination Inspection Evaluation Recommendation Repetition

What IT Audit Includes Hard drive security Data flow Applications Desktop risks Firewall issues with individual computers Hardening operating system Laptop & jump drive encryption Virtual servers

Audit priorities established Start with Web Plus: – Considered MCR’s most vulnerable area by Audit team – Concern about text fields – places where hackers could include hazardous characters.

First phase: Applications – Web Plus Audit Facility abstractor/uploader and central administrator/central abstractor/reviewer. – 52 hours of testing using an automated vulnerability scanner and manual inspection of web pages. Results: 4 high-risk vulnerabilities, several moderate risks. Auditor comments: – “Went better than expected.” – “Web Plus is a good application.”

Web Plus Audit - continued Results sent to CDC –High-risk vulnerabilities & some moderate risks fixed immediately – Requested 2nd scan to test fixes Second scan results – No high-risk vulnerabilities detected – Fixes on moderate risks also worked Remaining moderate risks fixed.
Second Phase: Hardening operating systems Server audit issues related to: – Configuration Proper port use, etc. – Management Managing administrative infrastructure Controlled access to file system & resources Process is ongoing (virtual servers)
Next Steps Increase security on mobile devices (Laptops, external hard drives, etc.): – Identify & purchase encryption software Consider alternatives: – Remote access reduces need for abstracting software (and PHI) on laptops.
Future Steps Research use of encryption software for desktop computers: – TruCrypt (an open-source software) – Other options Determine security level of networked drive.

Other Security Concerns Physical space: – MCR has P & Ps for off-site and commuting staff – MCR developed P & Ps for paper containing PHI, locking office, etc. – Audit of MCR’s space by MU Security requested 10/09 Attempt to kick in door

Recommendations Start with your institution’s P&Ps: – CCR’s may need to be more restrictive. Use CDC/NPCR or other guidance. Annually, require that CCR staff sign: – Confidentiality agreement; – Acknowledgments of state and federal – laws about penalties; and CCR security policy.

Recommendations continued Look for opportunities to further employee awareness: – Items in the news, etc. – Computer stolen from unsecured work station. Learn from other organizations’ practices and mistakes.

Conclusions Frequent review of security processes and business practices is needed to maintain data security. Many improvements involve minimal cost; others require funding.

Causes of Data Breaches Private files available in public spaces. Unused files with personal information. Lost or stolen laptops. Old or unused equipment without updated security protection. Sending files/allowing file access to wrong (reporting) facility.
You think you are secure! “ no matter how secure you are you fundamentally still are at risk.” – Howard, Schmidt, a former Bush cyber-security adviser, now president of the Information Security Forum. February 23, 2009 – fcw.com “The only way to 100 percent protect yourself from attacks is to turn off your computers.” – Dan Chenok, chairman of the Information Security and Privacy Advisory Board, an advisory panel to NIST. February 23, 2009 – fcw.com

Resources CDC/NPCR Data Security: http://www.cdc.gov/cancer/npcr/tools/security/ For complete details about MU’s Information Security program: http://doit.missouri.edu/security/ Federal Computer Week - Complimentary paper subscriptions, also available on-line. Variety of topics, including security: http://www.fcw.com

MU IT security team http://doit.missouri.edu/security/ Manager - Brandon Audit coordinator Hough Auditors –Tyler Hargis –Michael Morrison –Caine Henderson –Sara Rohrs Becky Fowler Safety awareness Kristy White Account management: –Megan Hartz –Joanne Boomer