FUSION CENTER October 2016 I T S S E C U R I T Y A N D P R I VA C
26 Slides9.41 MB

FUSION CENTER October 2016 I T S S E C U R I T Y A N D P R I VA C Y O P E R AT I O N S JOE THOMAS

OVERVIEW INCIDENT RESPONSE Security Goals Incident Benefits University Policies General Procedures Reporting to FSUPD, HR, FDLE, INFORMATION TECHNOLOGY SERVICES

INCIDENT RESPONSE Phishing - Accounts Compromised Compromised File Ransomware Stolen Property Final Comments INFORMATION TECHNOLOGY SERVICES

WHAT IS AN INCIDENT A computer security incident is any action or activity – accidental or deliberate – that compromises the confidentiality, integrity, or availability of data and information technology resources. Incidents also include the use of technology for criminal activities such as: fraud, child porn, theft, etc Policy violations may also be considered security incidents. INFORMATION TECHNOLOGY SERVICES

INCIDENT RESPONSE GOALS o Preserving the confidentiality, integrity and availability of enterprise information assets. o Minimizing the impact to the university. o Providing management with sufficient information to decide on appropriate course of action. o Providing a structured, logical, repeatable, and successful approach. INFORMATION TECHNOLOGY SERVICES

INCIDENT RESPONSE GOALS (CON’T) o Increase the efficiency and effectiveness of dealing with an incident o Reduce the impact to the university from both financial and human resources perspectives. o Provide evidence that may become significant should legal and liability issues arise. INFORMATION TECHNOLOGY SERVICES

UNIVERSITY POLICIES o The university has policies requiring action from IT administrators to report and respond to Security Incidents. o 4-OP-H-5 Information Technology Security o 4-OP-D-2-G Payment Cards o 4-OP-H-12 Information Privacy policy INFORMATION TECHNOLOGY SERVICES

TEAM LEADERSHIP AND DUTIES o CISO or Operations Team Lead usually acts as CSIRT Leader o o o o o o o o o o o Convene the CSIRT (Computer Security Incident Response Team). Select additional support members as necessary for the reported incident. Contact the Chief Information Officer. Conduct meetings of the CSIRT. Ensure meetings are documented. Direct team training on an ongoing basis. Periodically report status of incidents to the CIO. Manage incidents. Ensure Class 2 and Class 3 incidents are documented. Coordinate team incident research and response activities. Conduct a debriefing of lessons learned and report to the CIO. INFORMATION TECHNOLOGY SERVICES

TEAM EXPERTISE o Chief Information Office (CIO) o Registrar o Chief Auditor Office o Public Information Officer o Legal o Platform Specialists o Human Resources o Financial Administrators o Information Security (CISO or Representative) o Law Enforcement INFORMATION TECHNOLOGY SERVICES

ROLE OF THE CSIRT o The role of the CSIRT is to serve as the first responder to computer security incidents within and to perform vital functions in identifying, mitigating, reviewing and reporting findings to management. INFORMATION TECHNOLOGY SERVICES

RESPONSIBILITIES OF THE CSIRT o Classify security incidents. o Convene upon notification of a reported computer security incident. o Conduct a preliminary assessment to determine the root cause, source, nature, extent of damage. o Recommend response to a computer security incident. o Select additional support members as necessary for the reported incident. o Maintain confidentiality of information related to incidents. o Assist with recovery efforts and provide reports to the CIO. o Document incidents as appropriate. Examples include: lessons learned and recommended actions. o Report incidents to the Information Security and Privacy Office. o Maintain awareness of and implement procedures for effective response to computer security incidents. o Stay current on functional and security operations for the technologies within their area of responsibility. INFORMATION TECHNOLOGY SERVICES

CLASSIFICATION OF SECURITY INCIDENTS The CSIRT will classify each incident as a Class 1, Class 2, or Class 3 incident based upon risk severity. The following criteria are used to determine incident classification: Data Classification Business Impact Legal Issues Expanse of Service Disruption Policy Infraction Threat Potential Public Interest INFORMATION TECHNOLOGY SERVICES

CLASS 1 INCIDENT: LOW SEVERITY A Class 1 incident is any incident that has a low impact to university information technology resources and is contained within the unit. o The following criteria define Class 1 incidents: 1. 2. 3. 4. 5. 6. 7. Data classification: Unauthorized disclosure of confidential information has not occurred. Legal issues: Lost or stolen hardware that has low monetary value or is not part of a mission critical system. Business impact: Incident does not involve mission critical services. Expanse of service disruption: Incident is within a single unit. Threat potential: Threat to other information technology resources is minimal. Public interest: Low potential for public interest. Policy infraction: Security policy violations determined by the university. INFORMATION TECHNOLOGY SERVICES

CLASS 2 INCIDENT: MODERATE SEVERITY A Class 2 incident is any incident that has a moderate impact to university information technology resources and is contained within the unit. o The following criteria define Class 2 incidents: 1. Data classification: Unauthorized disclosure of confidential information has not been determined. 2. Legal issues: Lost or stolen hardware with high monetary value or that is part of mission critical system. 3. Business impact: Incident involves mission critical services. 4. Expanse of service disruption: Incident affects multiple units within the university. 5. Threat potential: Threat to other university information technology resources is possible. 6. Public interest: There is the potential for public interest. 7. Policy infraction: Security policy violations determined by the university. INFORMATION TECHNOLOGY SERVICES

CLASS 3 INCIDENT: HIGH SEVERITY A Class 3 incident is any incident that has impacted or has the potential to impact other external information technology resources and/or events of public interest. oThe following criteria define Class 3 incidents: 1. Data classification: Unauthorized disclosure of confidential information has occurred outside the university. 2. Legal issues: Incident investigation and response is transferred to law enforcement. 3. Business impact: Threat to other university information technology resources is high. 4. Expanse of service disruption: Disruption is wide spread across the university and/or other entities. 5. Threat potential: Incident has potential to become wide spread across the university and/or threatens external, third-party information technology resources. 6. Public interest: There is active public interest in the incident. 7. Policy infraction: Security policy violations determined by the university. INFORMATION TECHNOLOGY SERVICES

REPORTING PROCESS The CSIRT Leader reports and documents all incidents classified or reclassified as a Class 2 or Class 3 incidents. The Report should include the following: Executive Summary Description of the Incident CSIRT Members Participating CSIRT Findings Conclusions Recommendations INFORMATION TECHNOLOGY SERVICES

GENERAL PROCEDURES o End users need to communicate computer incidents to unit ISMs. o Information security managers must immediately notify the FSU IT Security Incident Officer of Incident. o Payment card data breach – the department head notifies the Security manager who then notifies the Director of Information Security and Privacy of the incident. o Information security manager notifies the Police Department involving threats to human beings, property, child pornography, or breach of CJIS information. o External Law enforcement if needed will be referred to the FSUPD who will serve as liaison during the Security Investigations. o General Counsel, Director of Information Security and Privacy, and FSUPD must be notified when a subpoena is issued. INFORMATION TECHNOLOGY SERVICES

REPORTING OF IT SECURITY INCIDENTS o Different departments will become involved in the remediation of an incident. o Criminal activities should be reported to FSUPD o Employee misconduct, both criminal and otherwise should be reported to HR. o Incidents of technical nature from an external source should be reported to the Director Information Security & Privacy. o All University data should be classified into one of three levels: o Level 1 – Protected o Level 2 – Private o Level 3 – Public INFORMATION TECHNOLOGY SERVICES

IT SECURITY INCIDENTS REPORTED TO FSUPD o Electronic transmission / storage of child pornography o Electronic transmission of threats to the physical safety of human beings or physical assets o Harassment and other criminal offenses involving user accounts o Loss or theft of computing device o Using FSU computing resource in the commission of a fraudulent activity against the university, individual, or outside entity. o Incidents involving a breach of CJIS information. INFORMATION TECHNOLOGY SERVICES

IT SECURITY INCIDENTS REPORTED TO HUMAN RESOURCES o Misuse of FSU IT resources is described in 4-OP-H-5 with some examples below: o Commercial use of IT resources that is not pre-approved o Advertisement for personal gain in FSU.EDU websites o Use of IT resources that interferes with the performance of employee’s job o Use of IT resources that result in an incremental cost to the University INFORMATION TECHNOLOGY SERVICES

TYPES OF MAJOR SECURITY INCIDENTS REPORTED TO THE FSU DIRECTOR OF INFORMATION SECURITY AND PRIVACY o Breach of Personal Identifiable Information (PII). o Root or system-level attacks on mission critical information system(s) desktop, laptop, tablet, server, storage device, or network infrastructure. o Compromise of restricted protected service accounts or software installations, for data classified as “Protected” or “Private”. o Denial of Service attacks that Impair FSU resources. o Malicious code attacks including malware infections on devices that allow an unauthorized user access to data. INFORMATION TECHNOLOGY SERVICES

TYPES OF MAJOR SECURITY INCIDENTS REPORTED (CON’T) o Open mail relay used to forward spam or other unauthorized communications with FSU email system. o Compromise user logon account credentials. o Denial of service on individual user accounts o Other attacks that may constitute a risk to confidentiality, integrity, or availability of university data or systems. INFORMATION TECHNOLOGY SERVICES

TYPES OF MINOR SECURITY INCIDENTS o Virus infections on servers and end-points INFORMATION TECHNOLOGY SERVICES

DEPARTMENTAL RESPONSE TO IT SECURITY INCIDENTS o Isolation and Protection of Compromised Devices o o o o o o Discontinue use of that device immediately Do not power off the device Disconnect the Network Cable at the Network Jack Isolate computer to prevent any further use. Preserve logs Contact FSUPD, HR, Director of Information Security and Privacy, to assist in investigation o If necessary get a backup of the hard drive. o Identification of Personally Identifiable Data o Calculation of Campus Unit Fiscal Cost to Remediate INFORMATION TECHNOLOGY SERVICES
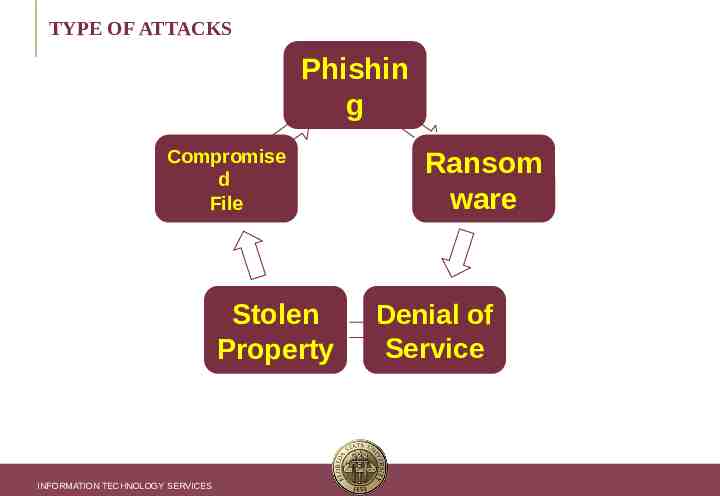
TYPE OF ATTACKS Phishin g Compromise d File Stolen Property INFORMATION TECHNOLOGY SERVICES Ransom ware Denial of Service

FINAL COMMENTS Any Questions? INFORMATION TECHNOLOGY SERVICES






