CONTEXTUAL, FLOW-BASED ACCESS CONTROL WITH SCALABLE HOST-BASED SDN
36 Slides1.99 MB

CONTEXTUAL, FLOW-BASED ACCESS CONTROL WITH SCALABLE HOST-BASED SDN TECHNIQUES [Taylor-INFOCOM16] Taylor, Curtis R., Douglas C. MacFarland, Doran R. Smestad, and Craig A. Shue. "Contextual, Flow-Based Access Control with Scalable Host-based SDN Techniques.", IEEE International Conference on Computer Communications (INFOCOM) 2016. 1 Present by: Wenzhi Cai

OUTLINE I. Introduction SDN OpenFlow Challenges of SDN Approach Specific technical problems II. Description Threat Model Approach Contextual Policies III. Evaluation IV. Criticism 2

I. INTRODUCATI ON

4

Travel to another country! Hello world! 5

Traditional systems: Blind to intra- subnet traffic Recent innovations: OpenFlow (2010) Software-defined networking (SDN) (2011) 6

7

Overview: 1. The SDN controller defines the data flows that occur in the SDN Data Plane. 2. If the controller allows a flow, it compute a route for the flow to take, and adds an entry for that flow. 3. Communication between the controller and the switches uses a standardized protocol and API. Requirements of practical implementation: 1. A common logical architecture in all switches, routers, and other network devices managed by an SDN controller 2. A standard, secure protocol between the SDN controller and the network devices 8
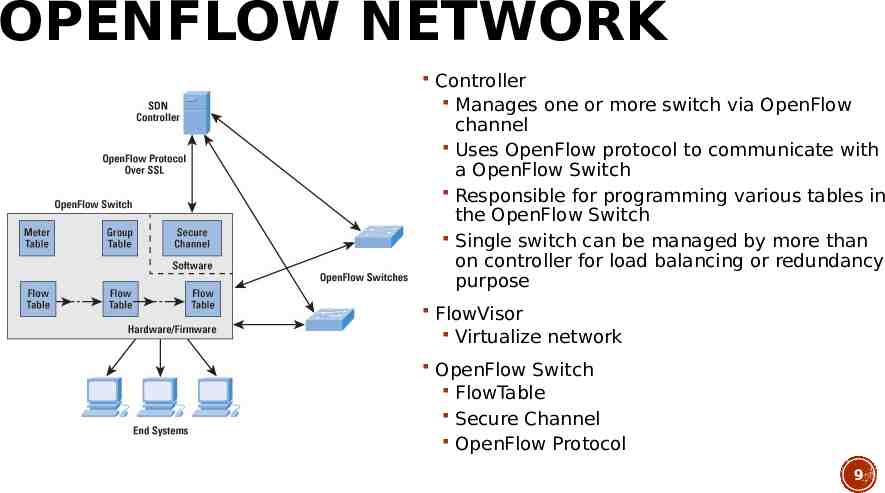
OPENFLOW NETWORK Controller Manages one or more switch via OpenFlow channel Uses OpenFlow protocol to communicate with a OpenFlow Switch Responsible for programming various tables in the OpenFlow Switch Single switch can be managed by more than on controller for load balancing or redundancy purpose FlowVisor Virtualize network OpenFlow Switch FlowTable Secure Channel OpenFlow Protocol 9

OPENFLOW PROTOCOL (SOUTHBOUND) Allows control (controller) and data(switches) to be split up Switches send information about flows to control plane Control plane sends instructions for handling flows to switches Enables the controller perform add, update, and delete actions in the flow table Implemented on top of SLL or TLS Secure OpenFlow channel Support 3 types of messages Asynchronous Messages Packet-In Message Flow Removed Message Controller-to-Switch Messages Multi-part, statistics gathering Symmetric Messages Hello messages Echo request and reply messages Experimenter message 10

SDN & OPENFLOW SDNs, implemented using OpenFlow, provide a powerful, vendor-independent approach to managing complex networks with dynamic demands. SDN with OpenFlow protocol allows a centralized controller to learn each time a new flow is created The software-defined network can continue to use many of the useful network technologies already in place, such as virtual LANs and an MPLS infrastructure. SDNs and OpenFlow are likely to become commonplace in large carrier networks, cloud infrastructures, and other networks that support the use of big data 11

CHALLENGES OF SDN APPROACH Data Plane Scalability concerns Limit Visibility contextual into end-host Malware Approach OpenFlow Switch Limitation Handling new flows Varies into 150 and 750 new flows per second Slow speed memory reduce new flow Lead to performance bottleneck, Denial of Services and user- level adversaries 12

SPECIFIC TECHNICAL PROBELMS How can we scalable obtain flow-level information for all network traffic? How can we provide network operator with details context surrounding each network flow? 13

II. APPROACH DESCRIPTION

CONTRIBUTIONS Scalable, fine grained flow-base access control Leveraging distribute computing power of the end host Allow host to apply fine-grain rules Hardware to apply coarse-grain rules Take OpenFlow agent functionality into end-host Host Context for all network flows Allow operator to develop detail policies for flow authorisation 15

THREAT MODEL: User-Level Adversary Key assumptions: oTrusted Operating System oNo physical attacks Focus on devices can be modified by an IT staff oFull flow-management compatibility 16

APPROACH OVERVIEW Host-Based Approach Implementation: Ubuntu Linux Operating System Network layer and above Features: Flow-based controls and context A capability to arbitrarily route traffic through proxies, IDSes, and other middleboxes A modular design Explicit notification to network controllers when a flow ends, allowing accurate realtime network flow insight Optimal traffic filtering at the source host to avoid network overheads Avoids the need for kernel or application modifications by using established kernel features 17

APPROACH OVERVIEW 1. Host Agent: Intercepting Packets Marking Features Mark or unmark packets Drop mark 2. Host Agent: Extraction Operating Context Module Design and Plug-ins 3. SDN Controller 18

19

Application Layer Travel to another country! Control Plane Hello world! SDN Agent A flow Packets 20

1. HOST AGENT: INTERCEPTING PACKETS The iptables firewall: mark or unmark feature netfilter queue: intercept unmarked packets Upadate iptables: create a ”drop mark” used to discard a flow Two communication parties The initial packet will not match any existing approval kernel flow 1. SDN Agent: analyzes the intercepted packet and determines the context (step 3-4) 2. SDN Agent: transmits a message to the SDN controller and requests instructions (step 5) 3. SDN Controller: issue rules (step 6) 4. SDN Agent: install appropriate NAT, firewall, routing, forwarding rules; (step 7) 5. iptables: update the marking to indicate the flow is authorized 6. SDN Agent: signal netfilter queue for transmission 7. netfilter queue: release the packet (step 8) 8. Routing Policy DB: select routing table 21

2. HOST AGENT: EXTRATING OPERATING CONTEXT 1. Plugins: provide context 2. Netfilter queue: allows the Agent to determine user name and group associated with the extracted packet 3. Socket: gather data (Isof: process ID) /proc: executable path associated with the process and the command line arguments Examine the executable path Collect similar information about the process’s ancestors 22

3. SDN CONTROLLER “BRAINS” of the network Manage flow control to the Northbound switches ‘below’ Manage the applications and business logical ‘above’ Southbound Implementation: a Python Controller Future: make implementation enhancements 23

CONTEXTUAL POLICIES Specify the high-level policies: Policies: Contextual languages POL-EH Flow-based security Language (FSL) Flow-based Management Language 1) Allow Administrative Process 2) Deny All User-Installed Programs 3) Default Allow Summary: Allow administrative background and daemon processes. Ensure that only process from administrator-installed sources can use the network. Act as a template for additional organization constraints 24

III. EVALUATION

EVALUATION OVERVIEW Implementation: In a small network of virtual machines (VMs) Preparations VMs: Runs on a single server with 16 cores operating at 2.8 GHz and 64 GBytes running with a KVM hypervisor Network Controller: Allocated two cores and 2048 MBytes of RAM Each Client system: Allocated a single core & 512 Mbytes of RAM All machines: Ubuntu 14.04 Server as Operating Systems Each host: Preinstalled iptables; Load the conntrack kernel module to allow fine-grained manipulation Three aspects A. The agent instrumentation B. The data plane and controller scalability C. The effectiveness of the security policy 26
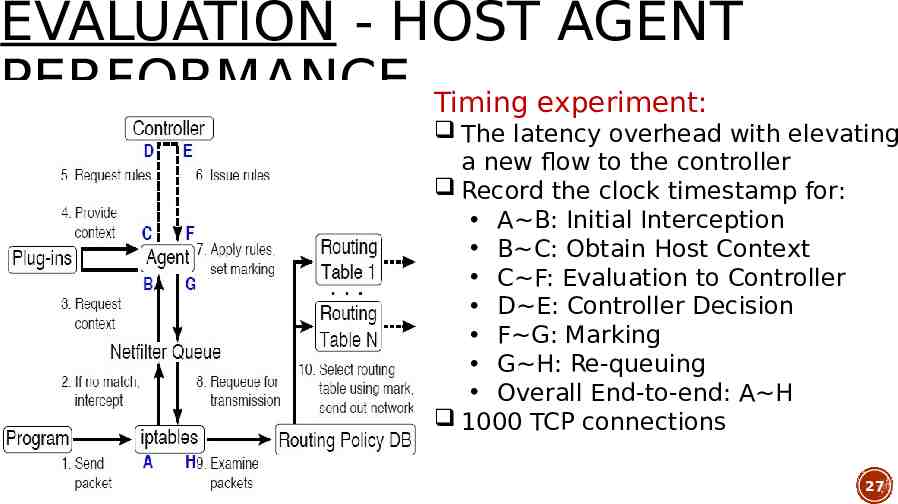
EVALUATION - HOST AGENT PERFORMANCE Timing experiment: The latency overhead with elevating a new flow to the controller Record the clock timestamp for: A B: Initial Interception B C: Obtain Host Context C F: Evaluation to Controller D E: Controller Decision F G: Marking G H: Re-queuing Overall End-to-end: A H 1000 TCP connections 27

Overall SDN Agent: a median under 17ms Minimal time Communication between kernel and agent via netfilter queue 100ms delay Gathering of host context Roundtrip to the controller Packet marking approach 28

Optimizations for delay: Host context collection can be parallelized Communication protocol can be greatly simplified Packet marking can use a more efficient netfilter- conntrack call The use of a compiled language would greatly improve performance 29

EVALUATION- DATA PALNE & CONTROLLER SCALABILITY Scalability experiment Number of hosts: 2, 4, 6, 8, 10, 12, 14 & 28 hosts Each host sequentially creates 1,000 new TCP flows to another host Sender calculated the RTT ( Round trip times) Record the number of new created flows per second for each host 30

Median RRT: Approximately From the timing results: double the Overall End-to-end result which is 16.7ms 350 flows per second (25 *14) All the data plane flow state is The controller can handle around 200,000 new stored at the hosts flows per second by spending 0.005 ms on each packet 31

EVALUATION- POLICY ENHANCEMENT ON SECURITY Simulated Linux Malware (n00bRAT) experiment: 1) Test a case where a user on a host receives and runs the malware 2) Perform a browser-based attack using Metasploit and launch the malware using the compromised browser Results: The malware is denied network access Conclusion: The policy will allow the adversary to establish a connection to download the malware to the user’s machine If the adversary launch the malware, the policy denies the malware any network access. 32

IV. CRITICISM

CRITICISM Approach can interact with legacy devices (BYOD). Connecting Embedded devices like printer. Isolate VLAN with physical proxy to avoid bottlenecks. Approach are compatible with non Linux hosts. Apple’s Mac OS X and Microsoft’s Windows OS OS X’s firewall, pf, is based upon OpenBSD firewall implementation. Devices or OS unable to support a native host agent: A “bump-in-the-wire” solution Fine grained policies and host context enable by default. Allow organisation to flexibility in respond to a compromised Provides Robust control include intra-subnet traffic with less disrupt to network 34

Reviews Background knowledge SDN & OpenFlow Research problems How can we scalable obtain flow-level information for all network traffic? How can we provide network operator with details context surrounding each network flow? Proposed approach Scalable flow-based access control: Host Agent- Intercepting packets (mark/unmark feature of iptable) Contextual (fine-grained): Host Agent- Context extraction ( Socket plugins) Security enhancement: Contextual polices Evaluation 1) Timing experiment – Host agent performance 2) Scalability experiment – data and control plane 3) Simulated malware experiment – contextual policies Conclusion: Scalable flow base monitoring Reuse existing network infrastructure Easily mitigate traffic floods Logically centralize access control 35

THANKS! 36