AN OFFERING IN THE BLUE CYBER SERIES: CISA to the Rescue!
35 Slides7.74 MB

AN OFFERING IN THE BLUE CYBER SERIES: CISA to the Rescue! CISA Resources for DAF Small Business Presented by Mr. J.D. Henry Region 5 Cybersecurity Advisor (Indiana) 19 April 2022 Cybersecurity and Infrastructure Security Agency #25 in the Blue Cyber Education Series

TLP:WHITE

TLP:WHITE Agend a CISA Mission About CISA CISA Cybersecurity Advisor Program CISA Cyber Services Additional Resources 2

TLP:WHITE

TLP:WHITE
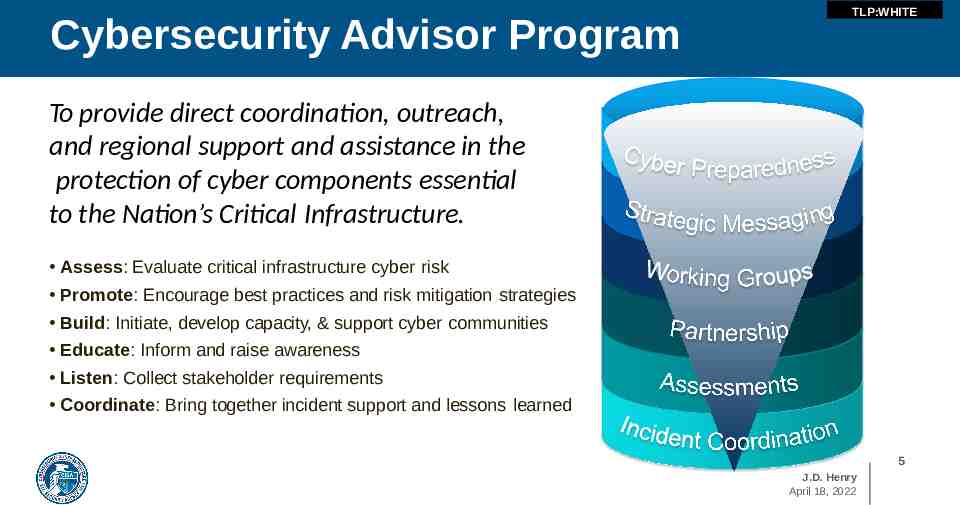
Cybersecurity Advisor Program TLP:WHITE To provide direct coordination, outreach, and regional support and assistance in the protection of cyber components essential to the Nation’s Critical Infrastructure. Assess: Evaluate critical infrastructure cyber risk Promote: Encourage best practices and risk mitigation strategies Build: Initiate, develop capacity, & support cyber communities Educate: Inform and raise awareness Listen: Collect stakeholder requirements Coordinate: Bring together incident support and lessons learned 5 J.D. Henry April 18, 2022
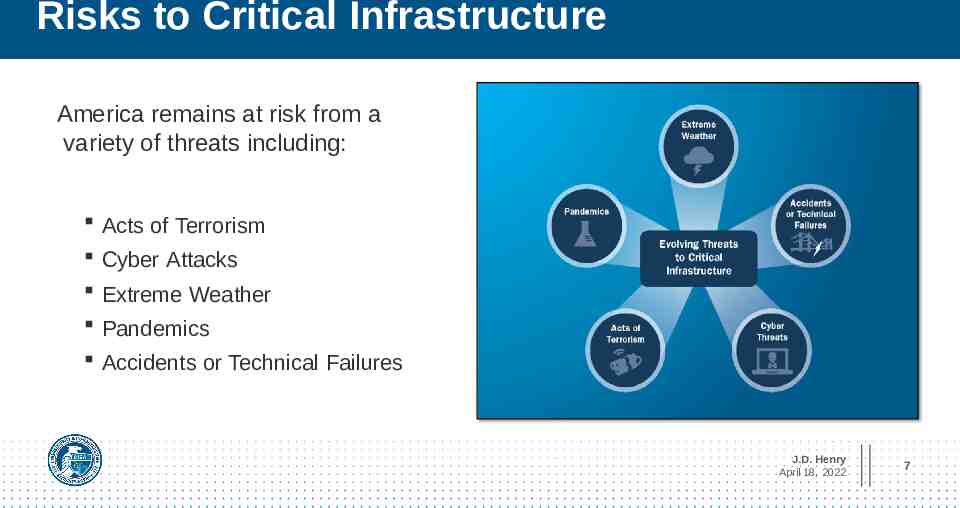
TLP:WHITE Risks to Critical Infrastructure America remains at risk from a variety of threats including: Acts of Terrorism Cyber Attacks Extreme Weather Pandemics Accidents or Technical Failures J.D. Henry April 18, 2022 7
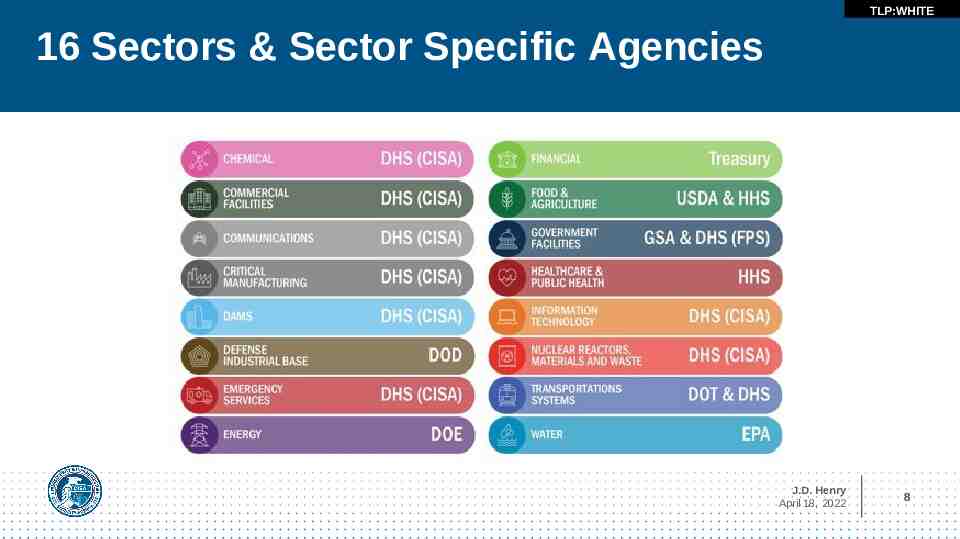
TLP:WHITE TLP:WHITE 16 Sectors & Sector Specific Agencies J.D. Henry April 18, 2022 8

TLP:WHITE Common Misconceptions Many users share some common misconceptions about cyber threats I’m not important enough to be at risk of a cyberattack My devices are “secure enough” right out of the box Cybersecurity Problems are I.T.’s problems The human factor will always be a vulnerability J.D. Henry April 18, 2022 9
TLP:WHITE Maintaining Vigilance During Increased Threat Potential CISA continues to conduct extensive outreach to emphasize importance of remaining vigilant New Webpage on www.CISA.gov In response to increased geopolitical tensions and Russian threat potential, CISA created the Shields Up site to promote heightened cybersecurity awareness and emphasize near term steps to improve resiliency for any U.S. Organization Encourage all stakeholders to take proactive stance to ensure resiliency in the event of a cyber incident Learn more at: https://www.cisa.gov/shields-up All organizations should report incidents and anomalous activity to CISA and/or the FBI via your local FBI field office or the FBI’s 24/7 CyWatch at (855) 2923937 or [email protected]. J.D. Henry April 18, 2022 10

Cybersecurity Services CISA Cybersecurity Services TLP:WHITE Vulnerability Scanning Remote Penetration Testing Phishing Campaign Assessment Web Application Scanning External Dependencies Management Cyber Resilience Review & more For more information on these services, visit www.cisa.gov/publication/cisa-services-catalog -or https://www.cisa.gov/cyber-resource-hub J.D. Henry April 18, 2022 11

Protected Critical Infrastructure Information (PCII) TLP:WHITE The DHS Protected Critical Infrastructure Information (PCII) Program is an information protection program that enhances information sharing between the private sector and the government. The DHS and other federal, state and local analysts use PCII to analyze and secure critical infrastructure and protected systems, identify vulnerabilities and develop risk assessments, and enhance recovery preparedness measures. If the information submitted satisfies the requirements of the CII Act of 2002, it is protected from: The Freedom of Information Act (FOIA) State and local disclosure laws Use in civil litigation PCII cannot be used for regulatory purposes and can only be accessed in accordance with strict safeguarding and handling requirements. PCII may be accessed by federal, state or local government employees and their contractors who meet the requirements of the PCII Program standard access policy. Before accessing PCII, these individuals must: Complete training on the proper handling and safeguarding of PCII Have homeland security responsibilities Have a need-to-know the specific information Sign a non-disclosure agreement (non-federal employees only) Be certified by the PCII Program Manager or PCII Officer (contractors only) J.D. Henry April 18, 2022

Vulnerability Scanning CRITICAL HIGH TLP:WHITE Evaluates external network presence by executing continuous scans of public, static IPs for accessible services and vulnerabilities. This service provides weekly vulnerability reports and ad-hoc alerts. MEDIUM LOW NONE INACTIVE J.D. Henry April 18, 2022 13
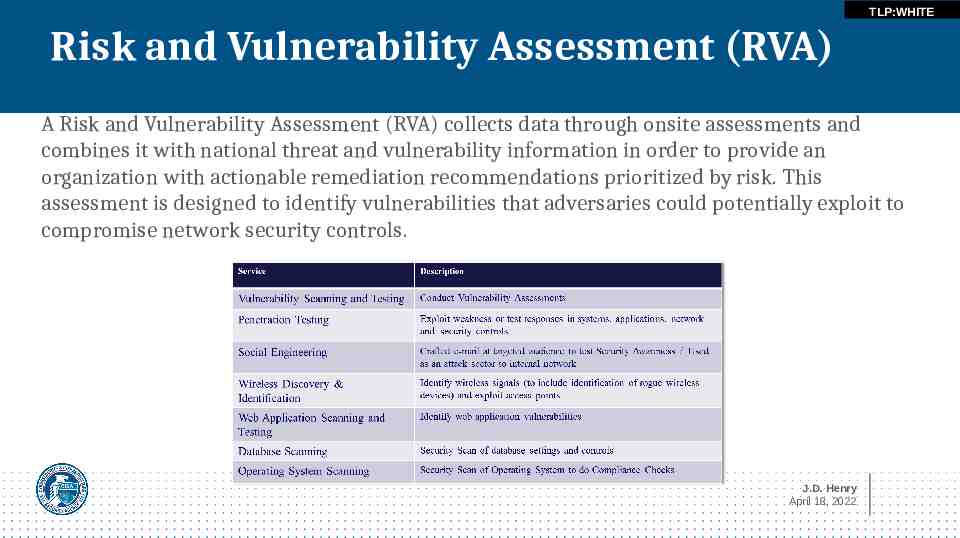
TLP:WHITE Risk and Vulnerability Assessment (RVA) A Risk and Vulnerability Assessment (RVA) collects data through onsite assessments and combines it with national threat and vulnerability information in order to provide an organization with actionable remediation recommendations prioritized by risk. This assessment is designed to identify vulnerabilities that adversaries could potentially exploit to compromise network security controls. J.D. Henry April 18, 2022
Remote Penetration Test (RPT) TLP:WHITE Utilizes a dedicated remote team to assess and identify vulnerabilities and work with customers to eliminate exploitable pathways. RPTs are similar to risk and vulnerability assessments but focus only on externally accessible systems with a tradeoff made for more service capacity at the expense of assessment scope. As a remote service, it is more cost effective and scalable than onsite offerings at the expense of organizational insight and context. J.D. Henry April 18, 2022

Phishing Campaign Assessment (PCA) TLP:WHITE Objectives: Increase cybersecurity awareness within stakeholder organizations Decrease risk of successful malicious phishing attacks, limit exposure, reduce rates of exploitation Benefits: Receive actionable metrics Highlight need for improved security Training Scope: 6-week engagement period Phishing emails capture click-rate only, no payloads will be used Varying Levels of Complexity -- Levels 1 - 6 (Easy to Difficult) J.D. Henry April 18, 2022
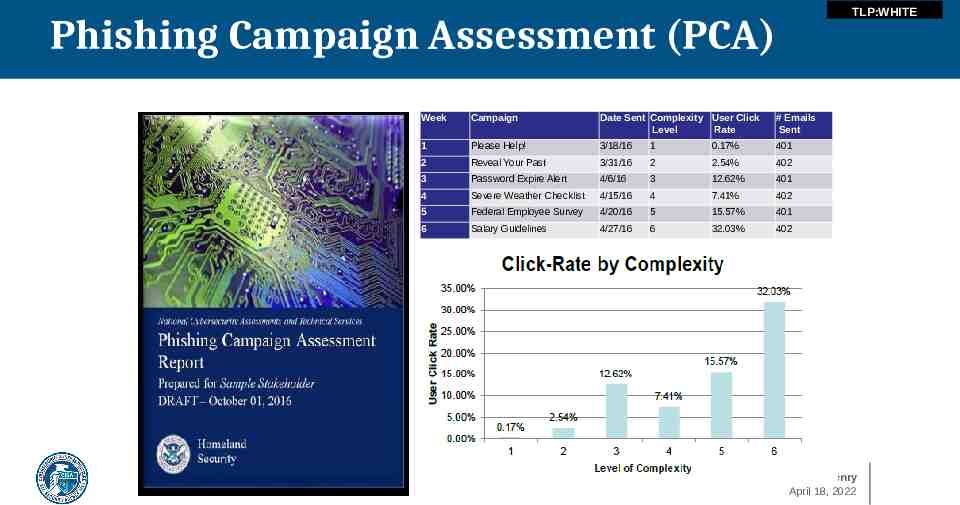
TLP:WHITE Phishing Campaign Assessment (PCA) Week Campaign Date Sent Complexity User Click Level Rate # Emails Sent 1 Please Help! 3/18/16 1 0.17% 401 2 Reveal Your Past 3/31/16 2 2.54% 402 3 Password Expire Alert 4/6/16 3 12.62% 401 4 Severe Weather Checklist 4/15/16 4 7.41% 402 5 Federal Employee Survey 4/20/16 5 15.57% 401 6 Salary Guidelines 4/27/16 6 32.03% 402 J.D. Henry April 18, 2022

TLP:WHITE Cyber Infrastructure Survey (CIS) Structured, interview based assessment (2 ½ to 4 hours) of essential cybersecurity practices inplace for critical services within your organization Identifies interdependencies, capabilities, and the emerging effects related to current cybersecurity posture Broadly aligns to the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) CIS Survey Question Domains CIS Domains Cybersecurity Forces Personnel Cybersecurity Training Cybersecurity Controls Authentication and Authorization Controls Access Controls Cybersecurity Measures Information Protection User Training Defense Sophistication and Compensating Controls Incident Response Incident Response Measures Alternate Site and Disaster Recovery Cybersecurity Management Cybersecurity Leadership Cyber Service Architecture Change Management Lifecycle Tracking Assessment and Evaluation Cybersecurity Plan Cybersecurity Exercises Information Sharing Dependencies Data at Rest Data in Motion Data in Process End Point Systems J.D. Henry April 18, 2022
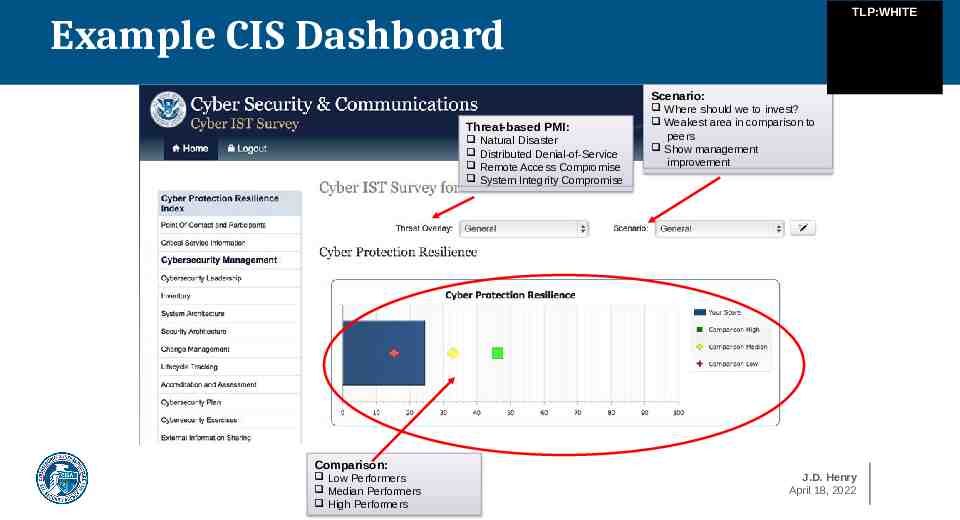
TLP:WHITE Example CIS Dashboard Scenario: Threat-based PMI: Natural Disaster Distributed Denial-of-Service Remote Access Compromise System Integrity Compromise Where should we to invest? Weakest area in comparison to peers Show management improvement Comparison: Low Performers Median Performers High Performers J.D. Henry April 18, 2022
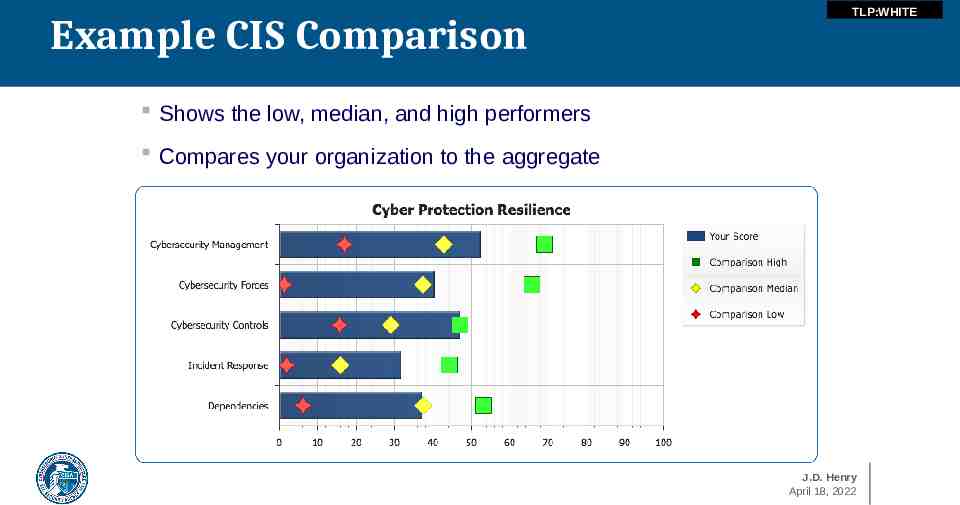
Example CIS Comparison TLP:WHITE Shows the low, median, and high performers Compares your organization to the aggregate J.D. Henry April 18, 2022
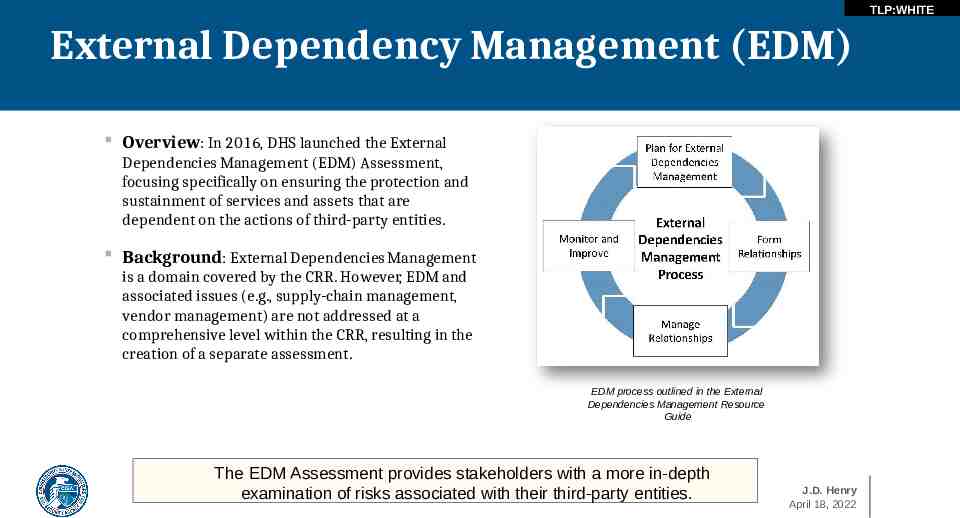
TLP:WHITE External Dependency Management (EDM) Overview: In 2016, DHS launched the External Dependencies Management (EDM) Assessment, focusing specifically on ensuring the protection and sustainment of services and assets that are dependent on the actions of third-party entities. Background: External Dependencies Management is a domain covered by the CRR. However, EDM and associated issues (e.g., supply-chain management, vendor management) are not addressed at a comprehensive level within the CRR, resulting in the creation of a separate assessment. EDM process outlined in the External Dependencies Management Resource Guide The EDM Assessment provides stakeholders with a more in-depth examination of risks associated with their third-party entities. J.D. Henry April 18, 2022

TLP:WHITE External Dependency Management (EDM) Delivery: The EDM can be Facilitated The CRR and EDM Self-Assessment Packages are available on the CISA website. Self-administered To provide the organization with an understandable and useful structure for the evaluation, the EDM Assessment is divided into three distinct areas (domains): 1. RELATIONSHIP FORMATION – how the organization considers third party risks, selects external entities, and forms relationships with them so that risk is managed from the start 2. RELATIONSHIP MANAGEMENT AND GOVERNANCE–how the organization manages ongoing relationships with external entities to support and strengthen its critical services at a managed level of risk and cost 3. SERVICE PROTECTION AND SUSTAINMENT – how the organization plans for, anticipates, and manages disruption or incidents related to external entities J.D. Henry April 18, 2022

TLP:WHITE Cyber Resilience Review (CRR) Purpose: The CRR is an assessment intended to evaluate an organization’s operational resilience and cybersecurity practices of its critical services Delivery: The CRR can be Facilitated Self-administered CRR and EDM Self-Assessment Packages are available on the CISA website. Helps public and private sector partners understand and measure cyber security capabilities as they relate to operational resilience and cyber risk Based on the CERT Resilience Management Model (CERT RMM)) CRR Question Set & Guidance The CRR provides organizations with a no-cost method to assess their cybersecurity postures and measure against the NIST CSF. J.D. Henry April 18, 2022
TLP:WHITE Cyber Security Evaluation Tool (CSET ) A stand-alone desktop application that guides asset owners and operators through a systematic process of evaluating Operational Technology and Information Technology. Contains Industry Standards for Compliance NERC CIP HIPPA PCI DSS NIST 800-171 R1 DoDI 8510.01 Etc. Available at: https://github.com/cisagov/cset/releases Contains extensive resource library J.D. Henry April 18, 2022 24

TLP:WHITE Where do I Start? Backup Data Employ a backup solution that automatically and continuously backs up critical data and system configurations. Multi-Factor Authentication Require multi-factor authentication (MFA) for accessing your systems whenever possible. MFA should be required of all users, but start with privileged, administrative, and remote access users. Patch & Update Management Enable automatic updates whenever possible. Replace unsupported operating systems, applications and hardware. Test and deploy patches quickly. Learn more at: https://www.cisa.gov/cyber-essentials J.D. Henry April 18, 2022 25

TLP:WHITE CISA Cyber Essentials: Building a Culture of Cyber Readiness What is Leadership's role in Cybersecurity? What is the Staff’s role in Cybersecurity? How is our data, intellectual property, or other sensitive information protected? What is needed for us to respond to an event? Learn more at: https://www.cisa.gov/cyber-essentials J.D. Henry April 18, 2022 26

TLP:WHITE Federal Virtual Training Environment (FedVTE) FedVTE provides FREE online cybersecurity training to federal, state, local, tribal, and territorial government employees, federal contractors, US military veterans and the public. Managed by DHS, FedVTE contains more than 800 hours of training on topics such as ethical hacking and surveillance, risk management, and malware analysis. FedVTE offers: Courses for all proficiency levels from beginner to advanced 800 hours of training mapped to the NICE Framework Certification prep courses on topics such as Ethical Hacking, Certified Information Security Manager (CISM), and Certified Information Systems Security Professional (CISSP) The ability to work at your own pace from any computer or mobile device Create a new account at: https://fedvte.usalearning.gov/register.php J.D. Henry April 18, 2022 31

INFORMATI ON SHARING AND developed and implemented numerous information sharing AWARENESS programs. Through these programs, CISA develops partnerships and shares substantive information with state, local, tribal, and territorial governments, private sector entities, and with international partners. National Cyber Awareness System (NCAS) TLP:WHITE Current Activity provides up-to-date information about high-impact security activity affecting the community at-large. Alerts provide timely information about current security issues, vulnerabilities, and exploits. Advisories provide timely information about current ICS security issues, vulnerabilities, and exploits. Bulletins provide weekly summaries of new vulnerabilities. Patch information is provided when available. Tips provide guidance on common security issues. Learn more about NCAS and other CISA information sharing programs at: https:// www.cisa.gov/information-sharing- andawareness J.D. Henry April 18, 2022 32

TLP:WHITE Cybersecurity “So What?” Cybersecurity starts with YOU There are over 32 million small business in the United States Currently an estimated 4.95 billion internet users or 62% of the world’s population There is a ransomware attack every 11 seconds Every time you use the Internet, you face choices related to your security and the security of your business Prevent crisis from becoming chaos, crisis will happen, crisis will end. It’s really about preparation and not panic J.D. Henry April 18, 2022 33

TLP:WHITE Incident Response What is an incident? The CISA Cybersecurity Division (CSD) Threat Hunting team defines an individual incident as a distinct, potentially malicious event, perpetrated by a single threat actor, using a single tactic, technique, or procedure (TTP); or series of related TTPs, against a single victim. Contact CISA Report cybersecurity incidents and vulnerabilities: 888-282-0870 [email protected] Threat Hunting Services Provides incident response, management and coordination activities for cyber incidents occurring in the critical infrastructure sectors as well as government entities at the Federal, State, Local, Tribal, and Territorial levels J.D. Henry April 18, 2022 34
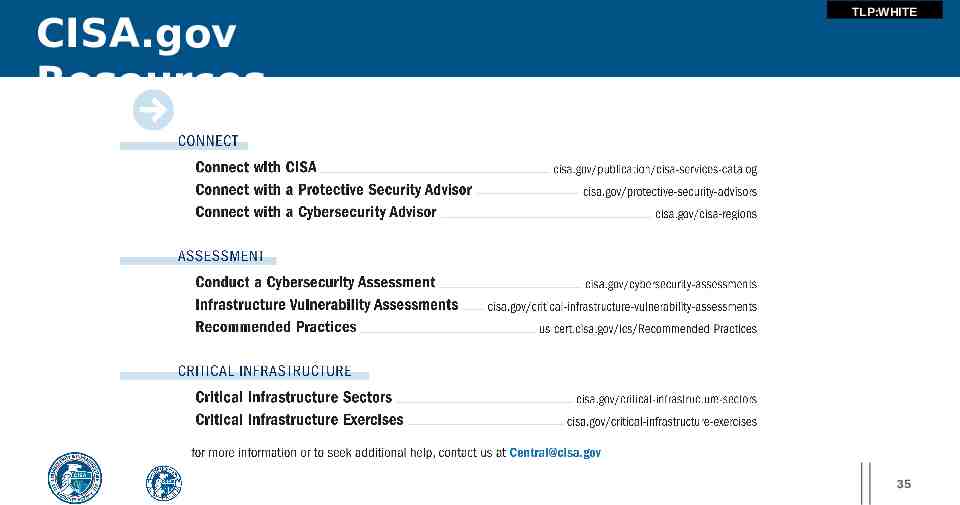
CISA.gov Resources TLP:WHITE 35

TLP:WHITE Questions? Please reach out at [email protected] 888-282-0870 https://www.cisa.gov/contact-us Presenter’s Name April 18, 2022 36

TLP:WHITE
DAF CISO’S BLUE CYBERSECURITY BOOT CAMP APRIL 20, 2022 I 10 AM–4PM EST LINK The Blue Cyber Education Series for DAF Small Businesses on the DAF CISO webpage www.safcn.af.mil/CISO/SmallBusiness-CybersecurityInformation/ Daily Office Hours for answering/researching your questions about DAF Small Business cybersecurity and data protection! Every Tuesday 1pm EST, dial in for the DAF CISO Small Business Cybersecurity AskMe-Anything. Register in advance for this Zoom Webinar: https:// www.zoomgov.com/webinar/registe r/WN 6Gz84TQGRvm6YHMSVyE0Qg 34
Any Questions? This briefing is not a substitute for reading the FAR and DFARS in your contract. This presentation and other presentations in the DAF CISO Blue Cyber Educational Series and be found on the DAF CISO webpage: https:// www.safcn.af.mil/CISO/Small-Business-Cybersecurity-Information/ Please provide questions, feedback or if you just want to talk about your cyber security /data protection questions to [email protected] Daily Office Hours for answering/researching your questions about DAF Small Business cybersecurity and data protection! Every Tuesday, 1pm Eastern, dial in for the DAF CISO Small Business Cybersecurity Ask-Me-Anything. Register in advance for this Zoom Webinar: https:// www.zoomgov.com/webinar/register/WN 6Gz84TQGRvm6YHMSVyE0Qg Distribution Statement A: Approved for public release. Distribution is unlimited. Case Number: AFRL-2021-4521, 22 Dec 2021 35