Threat Assessment and Management in Virginia K-12 Public Schools
99 Slides9.46 MB

Threat Assessment and Management in Virginia K-12 Public Schools

Introduction and Overview Introductions VA DCJS Representative Trainer(s) Organization Role(s) Education, Training & Certifications: Experience:

Attendee Survey Who is present today?

Session Agenda Introduction and Overview Threat Assessment and Management: Rationale and Principles Threat Assessment Team: Structure and Responsibilities Identifying and Reporting Concerning, Aberrant or Threatening Behaviors Information Sharing Conducting the Threat Assessment Assessing and Classifying Cases Managing Threats Summary/Q and A Case Study Exercise

Goals of the Session Understand requirements for Virginia school boards, superintendents, and threat assessment teams Understand why violence prevention is possible and how threat assessment works Understand key concepts related to targeted violence and the practice of threat assessment and management Understand basic legal issues relevant to threat assessment and management processes Develop and practice skills to identify, assess and manage cases involving potential threats

Enhancing Your Experience! Maximize opportunities to enhance practice Contribute to and learn from others Build collaborative networks across Virginia Introduce yourself and share contact information Commit to a handful of practically achievable actions when you get back to work! Consider this: This icon identifies issues for consideration in maximizing your understanding and application of concepts. Extending your learning: Watch for the icon and the searchable internet references throughout the training

Why Are We Here? Virginia law (§ 22.1-79.4) requires threat assessment teams for public schools: Each local school board shall adopt policies for the establishment of threat assessment teams including the assessment of and intervention with individuals whose behavior may pose a threat to the safety of school staff or students consistent with the model policies developed by the DCJS Virginia Center for School and Campus Safety in accordance with § 9.1-184 Such policies shall include procedures for referrals to community service boards and health providers for evaluation and treatment, when appropriate

Model Policies, Procedures, and Guidelines Threat Assessment and Management in Vi rginia Public Schools: Model Policies, Proc edures, and Guidelines, 3rd Edition (Virgini a DCJS, 2020) Consider other key resources including: VA DCJS: Information Sharing Guide for K12 Public Schools (2020) VA DOE: Suicide Prevention Guidelines for Virginia Public Schools (2020)vor VA DOE: Model Guidance for Positive and Preventative Code of Student Conduct Polic y and Alternatives to Suspension (2019) VA DOE: Model Policy to Address Bullying in Virginia Public Schools (2013) USSS: Enhancing School Safety Using a Threat Assessment Model: An Operational Gui de for Preventing Targeted School Violence (2018) FBI: Making Prevention a Reality: Identifying, Assessing and Managing the Threat of T argeted Attacks (2017)

Why Are We Here? Beyond the law: Research and practice tell us that targeted violence is often detectable and preventable Threat assessment and management has evolved as a standard of practice for proactive approaches to prevention violence impacting schools Threat assessment and management processes are designed to identify and assist persons in need as early as possible Team members need a solid foundation for understanding violence as well as principles and practices for effective threat management

Section 1 Threat Assessment and Management: Rationale and Principles

What is “threat assessment and management?” How do staff, parents and students view the process? Do various groups in the school view threat assessment differently? Who does not understand the role and function of the threat assessment team as well as you would like?
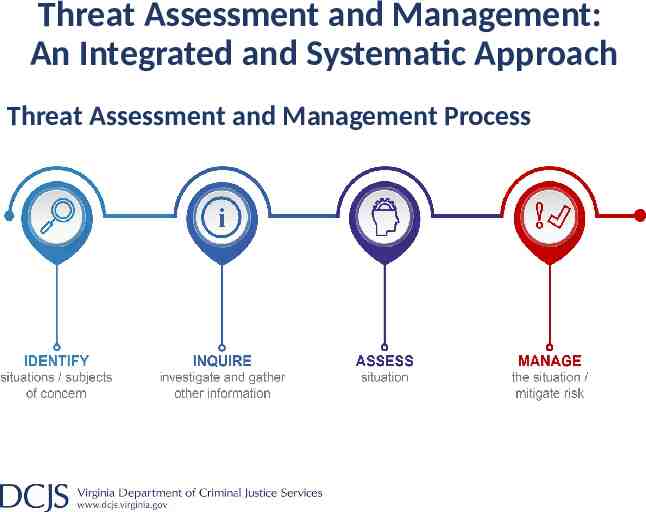
Threat Assessment and Management: An Integrated and Systematic Approach Threat Assessment and Management Process

What is a “Threat”? A threat: Is a concerning communication or behavior that: Indicates an individual may pose a danger to the safety of school staff or students: through acts of violence or other behavior that would cause harm to self or others May be expressed or communicated: behaviorally orally visually in writing electronically or through any other means Is considered a threat regardless of whether: observed by or communicated directly to the target or observed by or communicated to a third party and whether the target is aware of the threat

What is “Aberrant or Concerning Behavior”? Aberrant or concerning behavior: Atypical for the person or situation and: Causes concern for the safety or well-being of those involved Involves actions, statements, communications or responses that are unusual for the person or situation or actions which could lead to violence toward self or others or are reasonably perceived as threatening or causing concern for the well-being of the person

Threat Assessment and Management Goal The primary goal of the threat assessment and management process is to support and enhance the health, safety, and well-being of the school community. Threat Assessment and Management in Virginia K-12 Public Schools: Model Policies, Procedures, and Guidelines, 3rd Edition (Virginia DCJS, 2020) Page 30.

Key Finding Regarding Targeted Violence Safe School Initiative (USSS & US DOE, 2002) A Study of Pre-Attack Behaviors of Acti ve Shooters 2000-2013 (FBI, 2018) Protecting America’s Schools (USSS, 2019) Summary of School Safety Statistics (NIJ, 2017). Indicators of School Crime and Safety (US DOE, 2020). Crime, Violence, Discipline, & Safety in U.S. Public Schools (US DOE, 2019).

Fact or Fiction? School attacks are often sudden, impulsive acts. Fiction Many attackers were bullied prior to the attack. Fact People often have no idea of the attacker's ideas or plans. Fiction There is no profile for the types of schools that have been targeted. Fact Most school attackers were motivated by suicidality as their primary motive for violence. Fiction Source: U.S. Department of Homeland Security, U.S. Secret Service, and the National Threat Assessment Center, Protecting America’s Schools: A U.S. Secret Service Analysis of Targeted School Violence (2019).

Fact or Fiction? Potential school attackers can be identified by demographic information, personality traits, and school history. Fiction Most attackers threatened their target directly prior to the attack. Fiction Most attackers used firearms and they were acquired from their home. Fact Most attackers were “under the radar” showing no indicators they were in need of help. Fiction Most incidents are stopped by law enforcement. Source: U.S. Department of Homeland Security, Fiction U.S. Secret Service, and the National Threat Assessment Center, Protecting America’s Schools: A U.S. Secret Service Analysis of Targeted School Violence (2019).

Implications for Prevention Many acts of targeted violence can be prevented. Information about a subject’s ideas and plans for violence can often be observed or discovered before harm can occur. Information is likely to be scattered and fragmented. Key is to act quickly upon an initial report of concern, gather other pieces of the puzzle, then assemble to see what picture emerges. 12/16/22

Beyond Targeted Mass Violence Beyond mass violence there are a broad range of concerns that impact safety and well-being at school: Bullying and harassment Bias and hate crimes Mental health and developmental concerns Suicidal behaviors Domestic/dating violence Stalking Predatory sexual assault/misconduct Human trafficking Preventing Violent Extremism in Schools Gang violence Summary of School Safety Statistics Indicators of School Crime and Safety Violent extremism Crime, Violence, Discipline, & Safety in U.S. Public Schools Youth Risk Behavior Survey - 2019
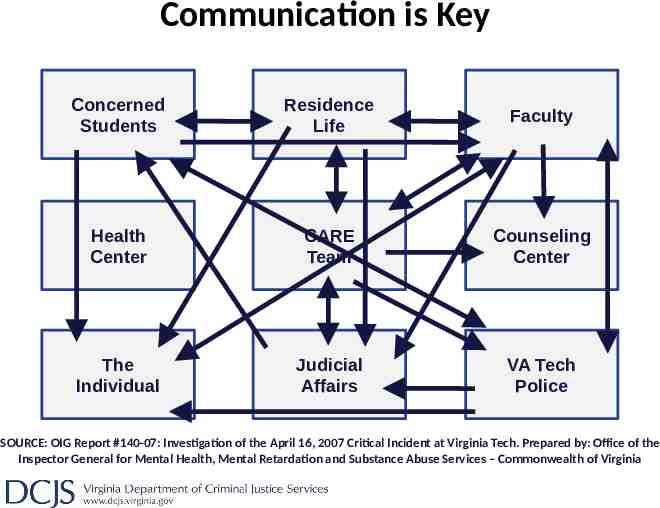
Communication is Key Concerned Students Residence Life Faculty Health Center CARE Team Counseling Center The Individual Judicial Affairs VA Tech Police SOURCE: OIG Report #140-07: Investigation of the April 16, 2007 Critical Incident at Virginia Tech. Prepared by: Office of the Inspector General for Mental Health, Mental Retardation and Substance Abuse Services – Commonwealth of Virginia

Principles of Threat Assessment Threat assessment is about prevention, not prediction Primarily a helping process, rather than punitive or adversarial Effective threat assessment is based upon observations of behavior rather than on general characteristics, traits, or profiles An inquisitive, objective and diligent mindset is critical to successful threat assessment and management A central question is whether a subject poses a threat not just whether the subject has made a threat Violence is a dynamic process Enhancing School Safety Using a Threat Assessment Model: An Operational Guide for Preventing Targeted School Violence
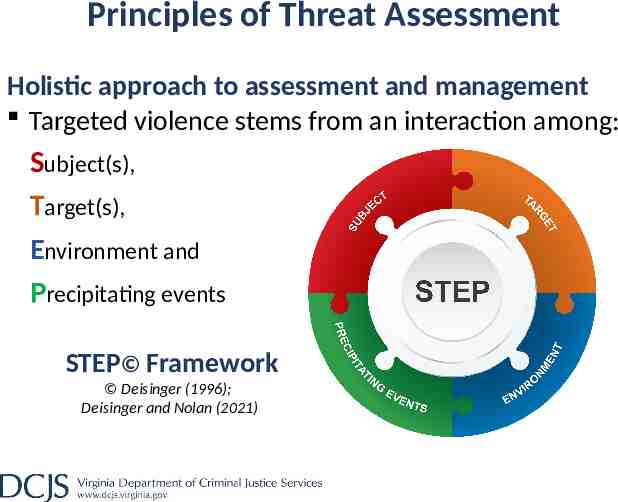
Principles of Threat Assessment Holistic approach to assessment and management Targeted violence stems from an interaction among: Subject(s), Target(s), Environment and Precipitating events STEP Framework Deisinger (1996); Deisinger and Nolan (2021)

Principles of Threat Assessment The relationship between mental illness and violence is complex. Social media and online activity are critical considerations in many cases A collaborative and coordinated approach between systems within the school and the community is critical for an effective threat assessment and management processes.
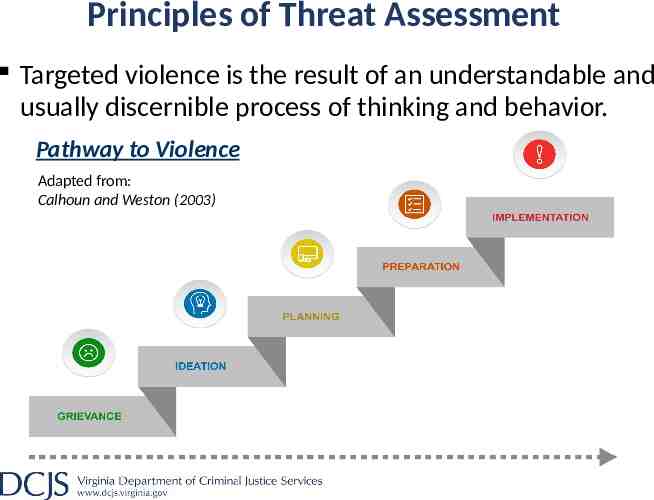
Principles of Threat Assessment Targeted violence is the result of an understandable and usually discernible process of thinking and behavior. Pathway to Violence Adapted from: Calhoun and Weston (2003)

The Path to Violence Insert relevant image behind this slide Insert title of next section here PBS Path to Violence PBS After Newtown

Section 2 Threat Assessment Teams: Structure and Responsibilities

Threat Assessment Team: Membership The superintendent of each school division shall establish a threat assessment team for each school Each team shall include persons with expertise in: Counseling Instruction School administration Law enforcement Team may include or consult with persons with other expertise Threat assessment teams may serve more than one school (as determined by the superintendent) Who else could be included either as a core member of a TAT or as someone consulted with when specialized expertise would be of value? 12/16/22

Threat Assessment Team: Responsibilities Each threat assessment team shall: Provide guidance to students, faculty, and staff on recognizing threatening/aberrant behavior that may represent a threat to the community, school, or self Identify members of the school community to whom threats should be reported Implement school board policies for the assessment of and intervention with individuals whose behavior poses a threat to the safety of school staff or students Report quantitative data on its activities according to guidance developed by the Virginia Department of Criminal Justice Services (DCJS) 12/16/22

Threat Assessment Team: Scope TATs assess and intervene with individuals whose behavior may pose a threat to the safety of the school Individuals who may pose a threat: Students: current, former and prospective Employees: current, former and prospective Indirectly affiliated: Parents, guardians or other family members Persons who are/have been in relationships with staff or students Contractors, vendors or other visitors Unaffiliated persons What challenges do you see in addressing individuals who may have no, or limited, connection to the school community?

Threat Assessment Team: Responsibilities Upon a preliminary determination that a student poses a threat of violence or physical harm to self or others, the team shall: Immediately report its determination to the division superintendent or designee The division superintendent or designee shall immediately attempt to notify the student's parent or legal guardian Nothing in this subsection shall preclude school division personnel from acting immediately to address an imminent threat 12/16/22

Divisional Oversight Committee Divisional Oversight Committee Superintendent may establish a committee: Charged with oversight of the threat assessment team(s) Can be an existing committee If established, the committee shall include individuals with expertise in: Human resources Education School administration Mental health, and Law enforcement

Additional Considerations Designated team leader Back-up members Training for Threat Assessment Team members Foundational and refresher training consistent with DCJS Table-top exercises Develop and implement operational procedures Establish and engage community about reporting procedures/mechanisms External Consultants: Threat Management Specialist Independent Violence Risk Evaluator Legal Counsel 12/16/22

Additional Considerations Identify local resources: community mental health services, child protective services, law enforcement crisis response units, emergency psychiatric screening services, etc. Establish liaisons Build relationships and communication Engage with other school divisions Identify state-level resources: Guidance and technical assistance from state board of education, school board association, union, state center for school safety, law enforcement fusion center, etc. Establish liaisons Build relationships and communication 12/16/22

Section 3 Identifying and Reporting Concerning, Aberrant or Threatening Behaviors

Importance of Reporting Key considerations: Reporting allows concerns to be addressed Earlier reporting allows greater range of options The threat management process is designed to help Goals are to maintain the health, safety and wellbeing of the school community “If you know something, say something and do something.” Adapted from: NYC Metropolitan Transportation Authority What might create barriers to reporting? How can we overcome these?

Facilitate Bystander Engagement Facilitate engagement: Emphasize that it is everyone’s role and responsibility to share and address concerns Identify concerning, aberrant, threatening, and prohibited behaviors to be reported Establish and promote effective reporting mechanisms Establish and identify how and where concerns can be reported Respond to reports in timely and effective manner Provide regular reminders of issues and process USSS and DOE Prior Knowledge of Potential School-Based Violence K-12 Threat Assessment in Virginia: A Prevention Overview for School S taff, Parents, and Community Members K-12 Threat Assessment in Virginia (Video)

Who Can Report? Require all division personnel, volunteers and contractors to report to designated administrator: Acts of violence or any expression of intent to harm another person, concerning communications or behaviors that suggest an individual may intend to commit an act of violence, or otherwise be in need of intervention or assistance Reports of concern can come from: Students Staff Parents Community members Outside entities How can we educate the school community on recognizing concerns and how/when to report? How do we build trust and engagement in the process? K-12 Threat Assessment in Virginia: A Prevention Overview for School Staff, Parents, and Community Members
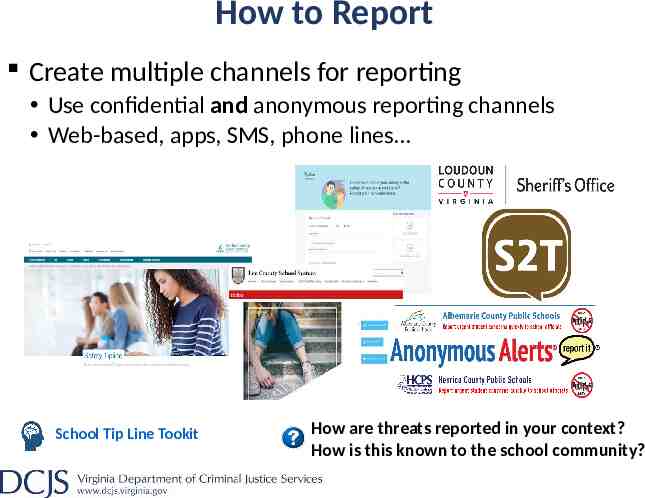
How to Report Create multiple channels for reporting Use confidential and anonymous reporting channels Web-based, apps, SMS, phone lines School Tip Line Tookit How are threats reported in your context? How is this known to the school community?

Section 4 Information Sharing

EXERCISE: Information Sharing and FERPA A teacher approaches you (member of TAT) very concerned about an interaction they just had with a student after a class. During that conversation, the student engaged in behaviors and made statements that lead the teacher to believe that the student was a serious threat to the safety of themselves and others at the school. Based on the information shared, you concur there appears to be a significant threat. When you ask the name of the student, the teacher becomes very cautious and says they are not sure if they can provide that information, that they don’t want to violate privacy law and be sued by the student. What mistakes, if any, are being made?

Information Sharing: FERPA Is not an impediment to effective threat assessment and management. Protects educational records, not observations, verbal communications, direct personal knowledge, etc. Allows sharing with: School officials with legitimate educational interest Other educational settings for enrollment or transfer Outside of school to protect health or safety Does not govern law enforcement unit records. If created and maintained by law enforcement unit, for law enforcement purposes. Does not permit a private right of action. DCJS Information Sharing Guide for K-12 Public Schools

Information Sharing: HIPAA Disclosures allowed under Health Insurance Portability and Accountability Act (HIPAA) Privacy Rule: Disclosures to prevent a serious and imminent threat: Health care providers may share PHI as necessary to prevent or lessen a serious and imminent threat to the health or safety of the individual, another person, or the public Health care providers may disclose, without a patient’s authorization, (otherwise) protected health information to anyone who can prevent or lessen the threatened harm, including family, friends, caregivers, school officials, and law enforcement DCJS Information Sharing Guide for K-12 Public Schools DOE and DHHS Guidance on Application of FERPA and HIPAA to Student Health Records

Information Sharing Upon a preliminary determination by the threat assessment team that an individual: poses a threat of violence to self or others or exhibits significantly disruptive behavior or need for assistance A threat assessment team may obtain: Criminal history record information per § 19.2-389 or § 19.2-389.1, and Health records per § 32.1-127.1:03 No TAT member shall: Redisclose any such criminal history or health information or Use any such record beyond the purpose for which such disclosure was made to the team

Protections for Staff Reporting Code of Virginia: § 8.01-47: Grants immunity from civil liability to: Any person, who in good faith Reports, investigates, or causes an investigation That any person poses a credible danger of serious bodily injury or death to any other person on school property § 8.01-220.1:2: grants immunity from civil liability for: Any teacher Regarding acts or omissions resulting from the supervision, care or discipline of students, or Reporting of alleged bullying or crimes against others When such acts were within the teacher’s scope of employment and done in good faith

Exclusion from Freedom of Information Act Code of Virginia § 2.2-3705.4 : Information held by a threat assessment team is excluded from FOIA! However, if a subject who has been under assessment: Commits an act or Is prosecuted for the commission of an act that caused the death of, or serious bodily injury, to another person Threat assessment team information shall be made available Except for any criminal history, health, or scholastic records The school shall remove identifying information of any person who provided information to the threat assessment team under a promise of confidentiality

Stalked and harassed Insert relevant image behind this slide Insert title of next section here
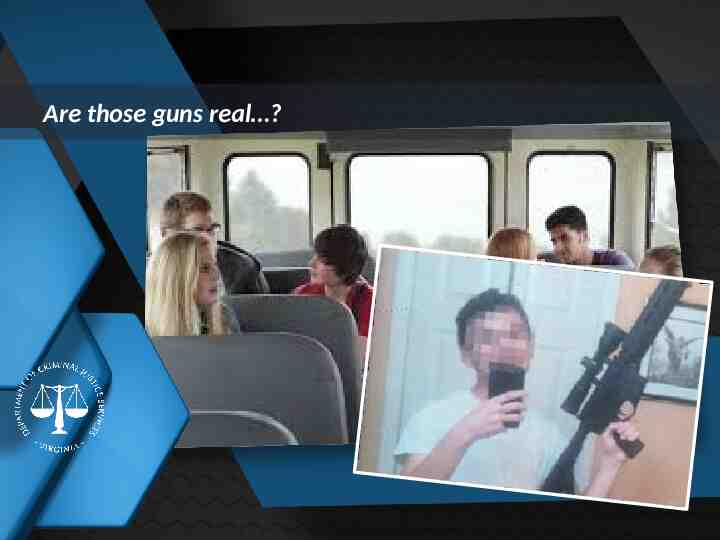
Are those guns real ? Insert relevant image behind this slide Insert title of next section here

They’re all on my hit list Insert relevant image behind this slide Insert title of next section here

I’m really worried about him Insert relevant image behind this slide Insert title of next section here

CreepyPasta drawings Insert relevant image behind this slide Insert title of next section here

Section 5 Conducting the Threat Assessment Process

Steps in the Threat Assessment Process Threat assessment team: Receives report of threat Intake: How you take in reports and being processing Triage: Assigning urgency/priority to cases Screening: Determining appropriateness for TAM Gathers additional relevant information Analyzes information and assesses threat If the team decides subject poses a threat: Team alerts superintendent Responds to manage threat Monitors and re-evaluates plan Follow up as appropriate Threat Assessment and Management Flowchart – page 91

Intake Upon receipt of initial report, the team obtains basic information about the situation: Initial Report of Concern: Date and time reported, date and time reviewed, person receiving report Reporting Party: Name, affiliation, contact information, relationship to subject of concern Incident/Nature of Concern: Date and time occurred, location, nature of concern, weapons involved or threatened, details about concerns, and any relevant background Subject of Concern: Name, affiliation, contact information, relationship to reporting party or target(s) Identified/Identifiable Target(s): Name, affiliation, contact information, relationship to reporting party or subject

Imminent Situation? Determine if situation is emergency/imminent Subject intends imminent and/or serious harm to self/others, e.g.,: Has weapon on school grounds, on a school bus, at a school activity, or enroute to/from any of those Imminent intent to use weapon(s) or cause serious injury Attempting to breach security and/or to gain access to targets Lack of inhibitions for using violence, indicated by: Feels justified in using violence to address grievances Has no perceived alternatives to the use of violence Lack of concern for or desiring of consequences Has the capability and willingness to cause harm

Imminent Situation If the situation is emergent or imminent: Initiate crisis response procedures according to school policy, e.g.: Involve law enforcement and appropriate security personnel Initiate relevant security protocols Notify key school administrators When safe to do so, move on to triage and assessment steps to further resolve any ongoing threat posed If the situation is NOT emergent or imminent: Continue with triage/screening or assessment process

Triage and Screening Timely and systematic review by trained personnel Consider Triage/Screening Team: Minimum of two (2) members Different roles/departments Review initial report(s) Consult relevant records/sources Triage process shall: Consider the nature and level of concern indicated Determine if existing resources and mechanisms are sufficient to address those concerns Determine whether the full team needs to further assess and manage the situation Initiate any crisis responses as appropriate

Inquire/Gather Information Review relevant records based on lawful and ethical access to information, such as: Prior threat assessment team contacts Work or school performance history Special education or disability accommodations Disciplinary or personnel actions Law enforcement or security contacts: school and community Critical involvement with mental health/social services Current or historical stressors, grievances, or losses Written materials/communications Online searches: internet, social media, email, etc.

Inquire/Gather Information Consider interviews: Initial interviews to verify report: Person(s) reporting threat Person(s) receiving report of threat Target/Recipient(s) of threat Witness(es) Subject of concern Other potential sources: Peers: Friends/Co-workers Employers, teaches, other staff Parents/guardians Relational Partners Local law or state enforcement Community services Corroboration Corroboration of of information information across across these these sources sources will will be be powerful powerful in in helping helping to to assess assess the the level level and and nature nature of of the the threat threat What What might might significant significant differences differences in in the the information information provided provided by by these these sources sources reveal? reveal?
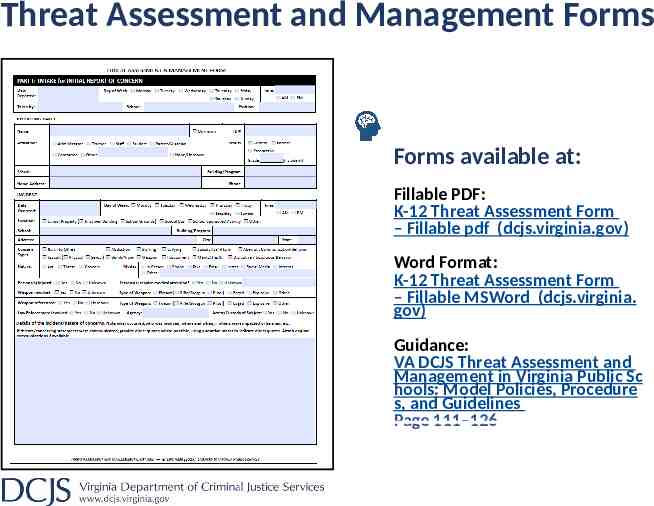
Threat Assessment and Management Forms Forms available at: Fillable PDF: K-12 Threat Assessment Form – Fillable pdf (dcjs.virginia.gov) Word Format: K-12 Threat Assessment Form – Fillable MSWord (dcjs.virginia. gov) Guidance: VA DCJS Threat Assessment and Management in Virginia Public Sc hools: Model Policies, Procedure s, and Guidelines Page 111–126

Documentation Record keeping Consult with administration and legal counsel: Record creation, storage, access, sharing, and destruction Consider: Database of threat assessment team cases Documentation of the subject’s exact words and actions Documentation of target reactions and protective actions Copies of emails, memos, voicemails, assignments, etc. Agenda and minutes of team staffing and consultations. Data Assessment Plan

Documentation Record retention Student Threat Assessment Records Retain for five (5) years after student graduates, completes a Board of Education program, transfers, or withdraws. Non-Student Threat Assessment Records Retain for five (5) years after the incident documented. Employee Health Records, as part of Threat Assessment Record Retain for thirty (30) years after end of employment Schedule GS-21 (Threat Assessments; page 20) Schedule GS-03 (Incident Reports; page 6) Schedule GS-03 (Employee Health Records; page 4)

Key Areas for Inquiry – Subject What behaviors are causing concern about the subject? Does the situation or circumstance that led to these concerns still exist? When and where and do the behaviors tend to occur? Is there a pattern to the behaviors or a change in pattern of behavior that is causing concern? If the behaviors have occurred previously, how has the subject dealt with the grievances? Has subject previously come to someone’s attention? Are the subject’s behaviors causing others concern for the welfare of the subject, or others, or both? Adapted from: FBI (2017) Making Prevention a Reality: Identifying, Assessing & Managing Threats of Targeted Attacks; USSS NTAC (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence

Key Areas for Inquiry – Subject Have there been any concerning, aberrant, threatening, or violent communications? Were there Directly Communicated Threats*? Has there been Leakage*? How and to whom is the subject communicating? What is the Intensity of Effort** in communications or attempts to address grievance? Do the communications provide insight about motives/grievances, ideation, planning, preparation, timing, targets, etc.? Has anyone been alerted or “warned away”? Adapted from: * Meloy, et al. (2011). The Role of Warning Behaviors in Threat Assessment; ** FBI (2017) Making Prevention a Reality: Identifying, Assessing & Managing Threats of Targeted Attacks; USSS NTAC (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence

Key Areas for Inquiry – Subject What are the subject’s motives and goals? Does the subject have a major grievance or grudge? Against whom? What is the relationship? Are there other motives that support use of violence such as desire for notoriety/fame? What do they seem to want to achieve? Is the subject exhibiting Fixation*? Increasing perseveration on person/cause or need for resolution Increasingly strident and negative characterization of target Angry emotional undertone, accompanied by Social or occupational deterioration What efforts have been made to resolve the problem? Adapted from: * Meloy, et al. (2011). The Role of Warning Behaviors in Threat Assessment; FBI (2017) Making Prevention a Reality: Identifying, Assessing & Managing Threats of Targeted Attacks; USSS NTAC (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence

Key Areas for Inquiry – Subject Has subject demonstrated identification and/or inappropriate interest with other perpetrators: Do they exhibit heightened interest, fascination, obsession, or fixation with acts of violence? Do they immerse themselves in violence? Is there Identification* (strong desire or need to emulate/be like others) with: Perpetrators of targeted violence or powerful figures Grievances of other perpetrators Weapons or tactics of other perpetrators Effect or notoriety of other perpetrators Ideologies or groups that support and encourage violence Adapted from: * Meloy, et al. (2011). The Role of Warning Behaviors in Threat Assessment; FBI (2017) Making Prevention a Reality: Identifying, Assessing & Managing Threats of Targeted Attacks; USSS NTAC (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence

Key Areas for Inquiry – Subject Does the subject have (or are they developing) the capacity to engage in targeted violence? Are there Pathway Behaviors* ? Planning Preparation (Means, Method, Opportunity, Proximity) Where on the Pathway? Are there changes in activity levels or Energy Bursts* ? How organized is the subject’s thinking and behavior? History of violence or aspects of Novel Aggression* ? Is subject developing perceived capability? Adapted from: * Meloy, et al. (2011). The Role of Warning Behaviors in Threat Assessment; FBI (2017) Making Prevention a Reality: Identifying, Assessing & Managing Threats of Targeted Attacks; USSS NTAC (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence

Key Areas for Inquiry – Subject Is the subject experiencing hopelessness, desperation, and/or despair? Has subject experienced perceived loss, failure, injustice? Does subject express shame or humiliation? Is subject having significant difficulty coping? Are there indications of Last Resort Behaviors* ? Desperation, despair, finality or action imperative Violence justified to address perceived grievance Lack of perceived alternatives Lack of concern for, or welcoming consequences Development of legacy token** Adapted from: * Meloy, et al. (2011). The Role of Warning Behaviors in Threat Assessment; ** FBI (2017) Making Prevention a Reality: Identifying, Assessing & Managing Threats of Targeted Attacks; USSS NTAC (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence

Key Areas for Inquiry Dangerousness is not a permanent state of being nor solely an attribute of a person. Dangerousness is situational and based on: Justification; Alternatives; Consequences; and Ability. Source: Gavin de Becker (1997) The Gift of Fear

Key Areas for Inquiry – Subject Has the subject’s behavior indicated or raised concern of need for intervention or supportive services? Does subject have difficulty coping? Symptoms of severe, acute, untreated mental illness: Significant lack of contact with reality: Hallucinations (especially command hallucinations) Delusions (especially paranoid/persecutory or grandiosity) Extreme wariness, distrust, paranoia Symptoms that impact subject’s perceptions of grievances or how others respond to subject Significant or sustained agitation or anxiousness Significant or sustained depressed mood Alcohol or other drug use/abuse Pervasive patterns of maladaptive behavior Does subject have access to and actively engaged in Adapted from: FBI (2017) Making Prevention a Reality: Identifying, treatment? Assessing and Managing Threats of Targeted Attacks

Key Areas for Inquiry – Subject Does the subject have protective factors, stabilizers, or buffers that inhibit use of violence? Views violence as unacceptable/immoral Accepts responsibility for actions Demonstrates remorse for inappropriate behavior Respects reasonable limits and expectations Uses socially sanctioned means to address grievances Values life, job, relationships, freedom Maintains and uses effective coping skills Treatment compliance/engagement Sustains trusted and valued relationships Adapted from: FBI (2017). Making Prevention a Reality: Identifying, Assessing and Managing Threats of Targeted Attacks; National Threat Assessment Center (2018). Enhancing School Safety Using a Threat Assessment Model: An operational guide for preventing targeted school violence.

Key Areas for Inquiry – Target Are targets (or others) indicating vulnerability or concern about the subject’s potential for violence? Are others concerned that subject may take action? Are others concerned about a specific target? Are others concerned for the well-being of the subject? Are targets or others around the subject engaging in protective actions? Do targets have adequate support resources? Are targets or others experiencing stress, trauma, or other symptoms that may benefit from intervention? Are targets engaging in behaviors that increase their: Desirability Availability Vulnerability Adapted from: Deisinger (1996); Deisinger and Nolan (2020); FBI (2017). Making Prevention a Reality: Identifying, Assessing and Managing Threats of Targeted Attacks.

Key Areas for Inquiry – Environment Are there environmental/systemic factors that are impacting the situation? Systemic, policy, or procedural problems Silos, gaps, or delays in reporting of concerns Poor conflict management skills Poor supervisory skills and/or willingness to address Organizational climate concerns Lack of support resources in community Social influences of others in environment, e.g.: Actively discourage or encourage/dare use of violence Deny/minimize the possibility of violence Passively collude with act Deisinger (1996); Deisinger and Nolan (2020); FBI (2017). Making Prevention a Reality: Identifying, Assessing and Managing Threats of Targeted Attacks.

Key Areas for Inquiry – Precipitating Events Are there precipitating events that may impact the situation currently and in foreseeable future? Loss, failure, or injustice Key dates/events Triggers and reminders of any of the above Opportunity Contagion effect Case management interventions Source: Deisinger (1996); Deisinger and Nolan (2020)

Key Areas for Inquiry – Global What is the consistency and credibility and completeness of information about the situation? Are the subject’s conversation and “story” consistent? Do collateral sources confirm or dispute each other? Do sources have direct and unique knowledge? Are there multiple sources? Do any sources have ulterior motives? What gaps exist in understanding of situation? What biases or misperceptions may be present? Source: Deisinger (1996); Deisinger and Nolan (2020)

Threats to Self: The Nexus Between Threat Assessment and Suicide Risk Assessment Benefits of utilizing the TAT in the suicide risk assessment process: TAT practiced in working collaboratively to address concerns related to the health, safety, and well-being of the school Utilizing TAT for all cases that pose a threat to self or others enhances consistent application of policies, procedures, and practices across cases TAT members have lawful access to protected records TAT law enforcement members have access to other records and resources to supplement response Sensitive information gathered during the TA process is not allowed to be re-disclosed outside of the TAT, therefore making the process more confidential and protected

Threats to Self: The Nexus Between Threat Assessment and Suicide Risk Assessment If triage identifies any of the following concerns, in addition to, or in place of, a potential threat to self, then the TAT should assume primary responsibility: Subject also has ideation or intent to harm others Subject’s acts of harm to self would pose a threat of harm to others, whether intended or not, OR Has engaged in behaviors (e.g., planning or preparation) that would place others at risk of harm, whether intended or not Subject’s suicidal or self-harm behaviors are responses to victimization, bias, bullying, harassment, or to other environmental/climate issues within the school Others are, or may reasonably be, significantly impacted by the threat of harm to self

Threats to Self: The Nexus Between Threat Assessment and Suicide Risk Assessment School or community mental health professionals retain primary responsibility for the direct assessment and mental health interventions with the student, per school guidelines Other team members assist with assessment and intervention actions and address any other concerns impacting upon the case If none of the above conditions are met, then no other actions are needed by the threat assessment team and the threat assessment case can be closed The suicide risk assessment and interventions are completed by the Suicide Crisis Response Team as relevant for the case Suicide Prevention Guidelines for Virginia Public Schools t
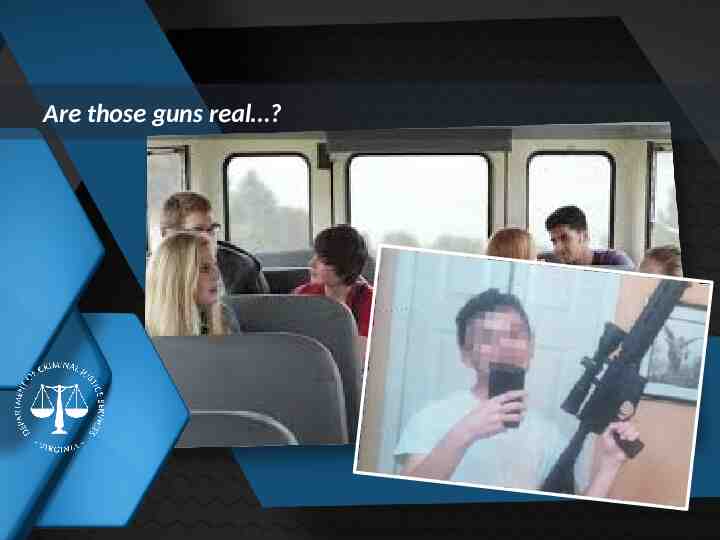
Are those guns real ? Insert relevant image behind this slide Insert title of next section here

I’m really worried about him Insert relevant image behind this slide Insert title of next section here

CreepyPasta drawings Insert relevant image behind this slide Insert title of next section here

Section 6 Assessing and Classifying Cases

Facilitating Case Discussions Fostering Effective Case Discussions: Active participation by all team members Keep discussion focused on the case Minimize bias in decision-making Consider totality and context of information available Consider information sources, credibility and relevance Corroborate critical information; resolve discrepancies Avoid generalizations or stereotypes, focus on behavior Consider changes in behavior or circumstances Be inquisitive and challenge assumptions Consider the impact of the unknowns Focus on active problem-solving Consider the STEP Domains

Classifying/Prioritizing Cases Priority 1: Critical Level of Concern/Imminent – Subject poses an imminent threat of serious violence or harm to self/others. Has or may reasonably have significant impact on others. Requires immediate law enforcement and school administration notification, subject containment, target protection and safety planning, Implementation of crisis response and notification protocols. Ongoing assessment and management plan, and active monitoring. Priority 2: High Level of Concern – Subject poses, or is rapidly developing capability for, a threat of serious violence or harm to self or others; or is in urgent need of hospitalization or treatment, Targets/others are impacted. Typically involves environmental factors and consideration for precipitating events. Requires immediate notification of school administration and law enforcement, subject containment, target protection and safety plan. Activation of crisis response protocols, ongoing assessment and management plan, active monitoring and referrals.

Classifying/Prioritizing Threats Priority 3: Moderate Level of Concern – Subject does not pose a threat of serious violence or harm though risk cannot be ruled-out. Subject may be developing capability for harm and is engaging in aberrant or concerning behaviors that indicate need for assistance/intervention. Targets/others likely concerned and impacted. Environmental or precipitating factors may be present. Requires ongoing assessment and management plan, active monitoring, and referrals as appropriate. Priority 4: Low Level of Concern – Subject does not indicate a threat of violence or harm to self or others; would or may benefit from intervention or assistance with concerns, Target, environmental or precipitating events may be present at low levels. May involve some ongoing assessment management with passive monitoring and/or periodic active monitoring, Referrals as appropriate. Close case if no team interventions or monitoring indicated. Priority 5: Routine/No Known Concerns – Subject does not indicate a threat of violence or harm to self or others; or need for assistance or intervention, No impact on others, environmental factors, or precipitants that need team intervention. Close case.
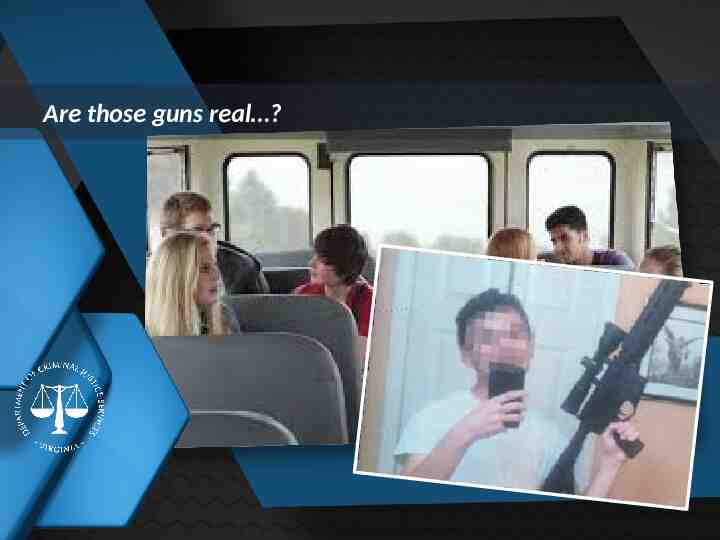
Are those guns real ? Insert relevant image behind this slide Insert title of next section here

I’m really worried about him Insert relevant image behind this slide Insert title of next section here

Section 7 Managing Threats
Develop a Case Management Plan Develop an individualized, contextually-relevant, plan based on inquiry and assessment. Plan must be contextually relevant and situationally specific Accountability is critical Consider the STEP Framework Engagement can be critical Especially with internal subjects Personalities, backgrounds and skills (of threat managers) matter Consider use of trusted sources Source: Deisinger (1996); Deisinger and Nolan (2021)

Subject-Based Strategies Implement appropriate strategies: No further action Direct monitoring, watch and wait; Third party monitoring Direct intervention: support, referral, confrontation Third party intervention Administrative actions No contact/communication notice, probation, suspension, expulsion/termination, no trespass/ban from premises Civil actions Mental health interventions (voluntary or involuntary) Criminal justice interventions Adapted from: Calhoun and Weston (2003) Contemporary Threat Management

Considerations Regarding Subject Removal Leave, suspension, or termination options that focus solely on removing the subject of concern do not address the long-term challenges of: Moving subject away from thoughts and plans of, and capacity for, violence and/or disruption Connecting subject to resources (where needed) Mitigating environmental/systemic factors Monitoring subject when they are no longer connected to organization Use with intentionality, awareness of limitations, and anticipation of consequences. Source: Deisinger (1996); Deisinger and Nolan (2020)

Re-Entry Planning and Preparation Prepare for re-integration of subject: Establish conditions for return Evaluate subject readiness to safely and effectively return to participate in school or work experience Develop proactive case management plan Align ongoing interventions Coach subject about re-entry Anticipate environmental aspects which may impact subject Prepare community for subject’s re-entry Consider precipitating events Monitor, re-assess and intervene as appropriate Source: Deisinger (2011); Deisinger and Nolan (2020)

Target Management Strategies Coaching regarding personal safety approaches Set clear limits and boundaries Monitor communications for changes/escalations Avoid contact/response Document all contacts from/with subject Minimize reactivity to subject actions Minimize public information Maintain/enhance situational awareness Vary routine Develop contingency plans: Escape, shelter, defense Utilize support systems Source: Deisinger (1996); Deisinger and Nolan (2020)

Target Management Strategies Organizational roles in reducing target vulnerability Engagement with target Support for target Change work/school hours Change work location Notice to co-workers/classmates Enhance physical security Security staffing Safety escorts Fear management EAP/Counseling referrals Source: Deisinger (1996); Deisinger and Nolan (2020)

Environmental Management Strategies Address systemic, policy, or procedural problems Identify/address reporting gaps/delays Enhance bullying prevention/intervention programs Intervene with associates that support violent behavior Enhance conflict management skills Enhance supervisory skills and accountability Enhance organizational climate – caring community Emphasize fairness and respect Effective communication People rewarded, supported, and held accountable Prevention and early intervention with inappropriate behaviors Build engagement for mutual safety and well-being Source: Deisinger (1996); FBI (2004); Deisinger and Nolan (2020)

Precipitating Events: Strategies Anticipate and prepare for precipitating events Minimize unnecessary precipitants where possible Consider impact of timing and location of interventions Monitor reactions to case management/interventions Monitor and plan for loss or injustice Monitor and plan for key dates or events Monitor for reactions to administrative/court actions Consider contingency plans Source: Deisinger (1996); Deisinger and Nolan (2020)

Summary Virginia law requires threat assessment teams, policy, reporting Threat assessment is an established standard of practice to support school violence prevention DCJS model policies, procedures, and guidelines offer guidance consistent with Virginia and federal law, peer-reviewed research, and standards of practice Consult with DCJS/VCSCS, colleagues, threat assessment experts regarding concerns Request for Service Form: Technical Assistance for Threat Assessment and Management Teams for Virginia Schools

Questions?

Resources and Contact Information DCJS Virginia Center for School and Campus Safety K-12 Resources, Training and Points of Contact Brad Stang Threat Assessment Program Coordinator (804) 997-1278 [email protected]






