Technical Introduction to System Center Data Protection Manager
47 Slides3.61 MB

Technical Introduction to System Center Data Protection Manager 2010 Anthony Tyler Storage Technology Architect

Session Objectives and Takeaways Why build DPM ? Introducing DPM 2010 and partner solutions Demo – Protecting Data How Does DPM work ? Demo – Rapid & Reliable Recovery Protected Platforms

1993 - 2005 If we build it someone else will back it up someone else will make it highly available someone else will take it off-site but, who will support it?

Active Directory System State Disk-based Recovery Disaster Recovery file services Tape-based Backup

Customer Backup Pains Better nightly backups needed Tape is inefficient Lack of application support WAN not feasible for centralized backups Remote and branch-office data protection is expensive and cumbersome Multiple vendor support challenges

Customer Backup Pains Better nightly backups needed Tape is inefficient Lack of application support WAN not feasible for centralized backups Remote and branch-office data protection is expensive and cumbersome Multiple vendor support challenges

Customer Backup Pains Better nightly backups needed Tape is inefficient Lack of application support WAN not feasible for centralized backups Remote and branch-office data protection is expensive and cumbersome Multiple vendor support challenges
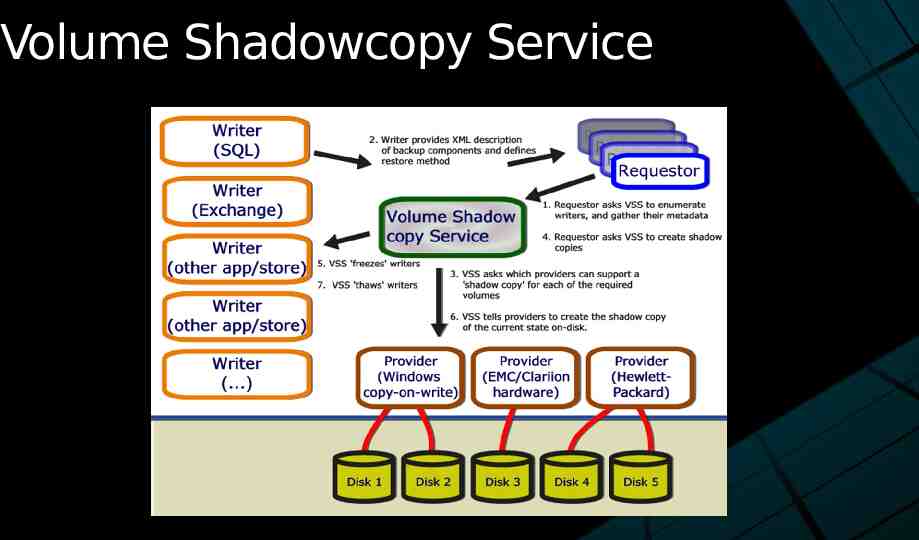
Volume Shadowcopy Service
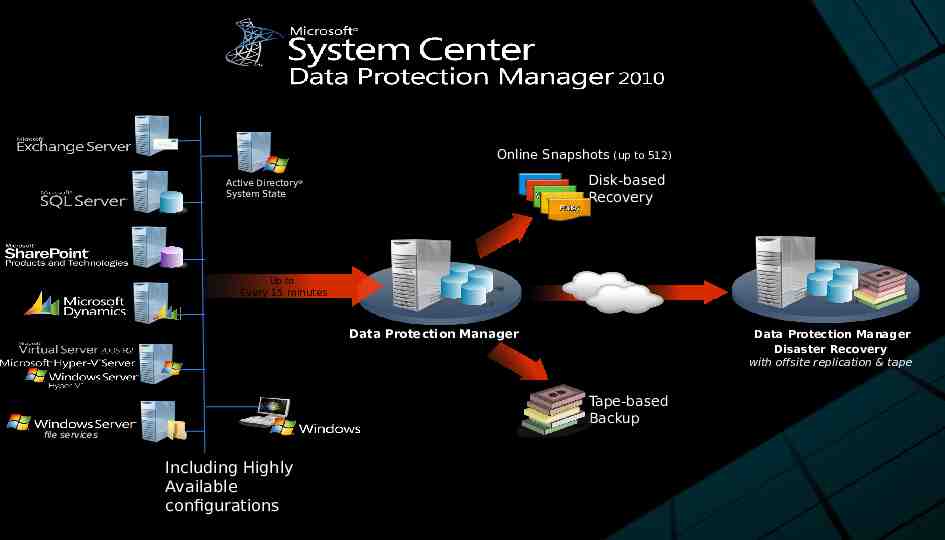
Online Snapshots (up to 512) Disk-based Recovery Active Directory System State Up to Every 15 minutes Data Protection Manager Data Protection Manager Disaster Recovery with offsite replication & tape Tape-based Backup file services Including Highly Available configurations
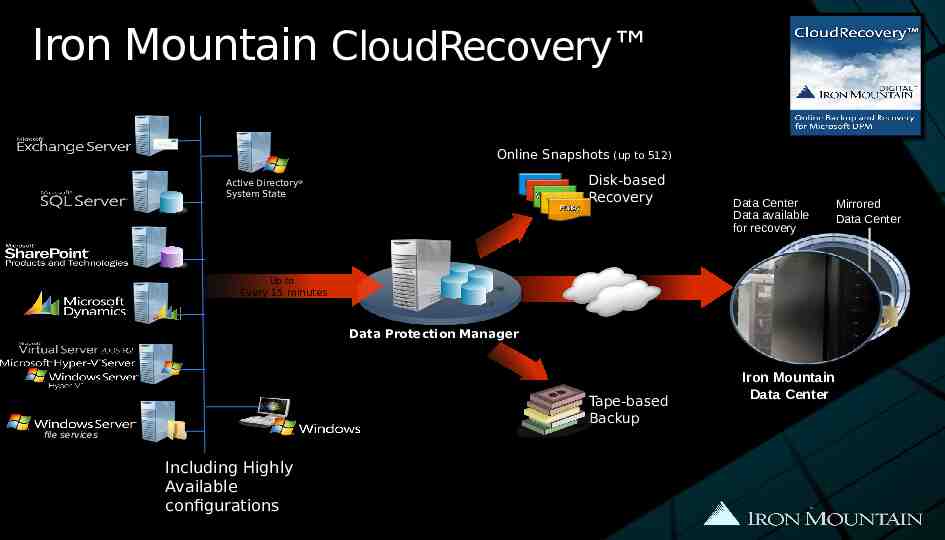
Iron Mountain CloudRecovery Online Snapshots (up to 512) Disk-based Recovery Active Directory System State Data Center Data available for recovery Up to Every 15 minutes Data Protection Manager Tape-based Backup file services Including Highly Available configurations Iron Mountain Data Center Mirrored Data Center
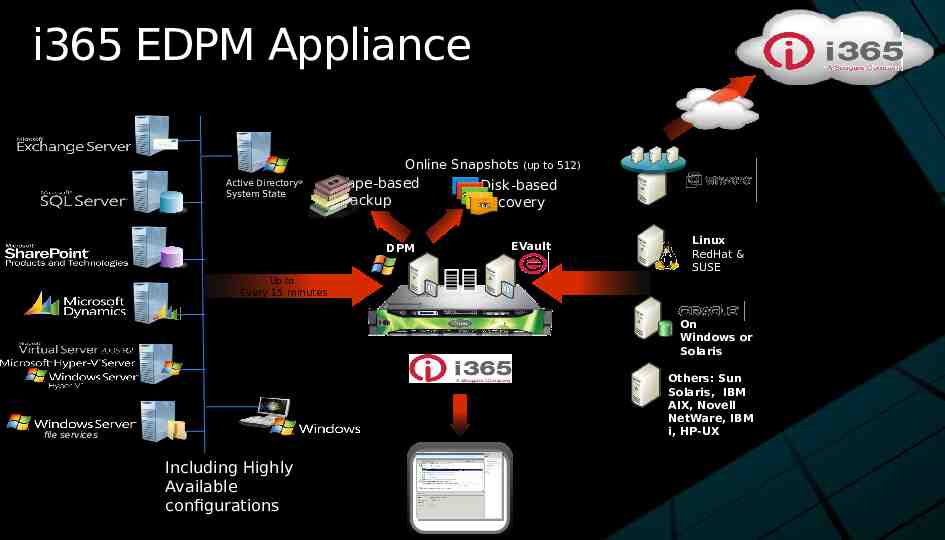
i365 EDPM Appliance Online Snapshots (up to 512) Active Directory System State Tape-based Backup DPM Disk-based Recovery EVault Linux RedHat & SUSE Up to Every 15 minutes On Windows or Solaris Others: Sun Solaris, IBM AIX, Novell NetWare, IBM i, HP-UX file services Including Highly Available configurations

DPM 2010 System Center Data Protection Manager 2010 delivers unified data protection for Windows servers and clients as a best-ofbreed backup & recovery solution from Microsoft, for Windows environments. DPM 2010 provides the best protection and most supportable restore scenarios from disk, tape and cloud -- in a scalable, reliable, manageable and cost-effective way.

DPM 2010 System Center Data Protection Manager 2010 delivers unified data protection for Windows servers and clients as a best-ofbreed backup & recovery solution from Microsoft, for Windows environments. DPM 2010 provides the best protection and most supportable restore scenarios from disk, tape and cloud -- in a scalable, reliable, manageable and cost-effective way.

DPM 2010 System Center Data Protection Manager 2010 delivers unified data protection for Windows servers and clients as a best-ofbreed backup & recovery solution from Microsoft, for Windows environments. DPM 2010 provides the best protection and most supportable restore scenarios from disk, tape and cloud -- in a scalable, reliable, manageable and cost-effective way.

DPM 2010 System Center Data Protection Manager 2010 delivers unified data protection for Windows servers and clients as a best-ofbreed backup & recovery solution from Microsoft, for Windows environments. DPM 2010 provides the best protection and most supportable restore scenarios from disk, tape and cloud -- in a scalable, reliable, manageable and cost-effective way.

DPM 2010 System Center Data Protection Manager 2010 delivers unified data protection for Windows servers and clients as a best-ofbreed backup & recovery solution from Microsoft, for Windows environments. DPM 2010 provides the best protection and most supportable restore scenarios from disk, tape and cloud -- in a scalable, reliable, manageable and cost-effective way.

Protecting Applications demo

DPM 2010 – Express Full Using the native application VSS writer Check out http://edge.technet.com/Media/DP M-2007-SP1-How-does-DPM-really -work/ How DPM Protects Data
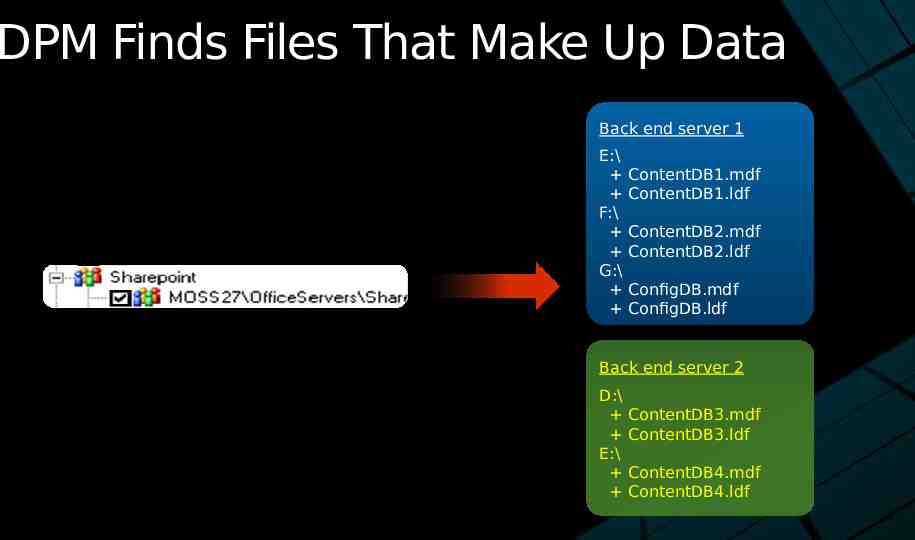
DPM Finds Files That Make Up Data Back end server 1 E:\ F:\ G:\ ContentDB1.mdf ContentDB1.ldf ContentDB2.mdf ContentDB2.ldf ConfigDB.mdf ConfigDB.ldf Back end server 2 D:\ E:\ ContentDB3.mdf ContentDB3.ldf ContentDB4.mdf ContentDB4.ldf
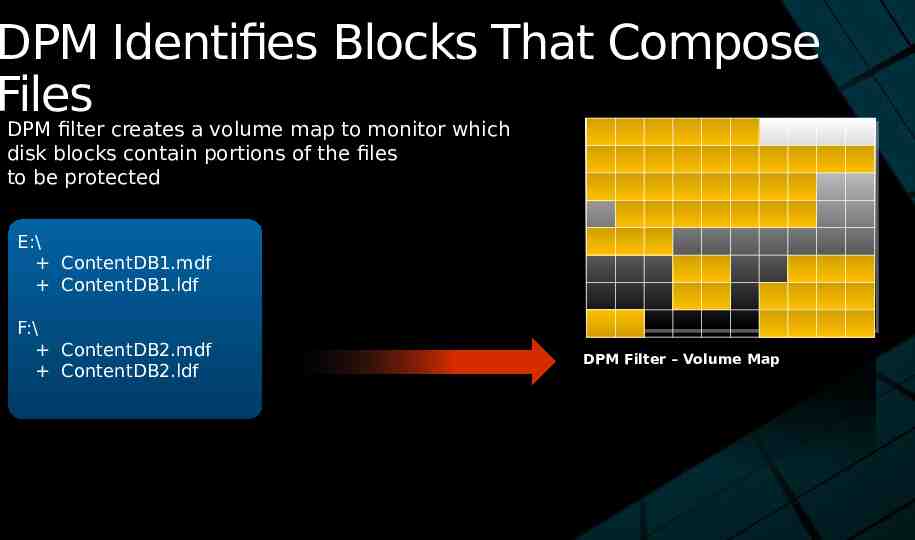
DPM Identifies Blocks That Compose Files DPM filter creates a volume map to monitor which disk blocks contain portions of the files to be protected E:\ ContentDB1.mdf ContentDB1.ldf F:\ ContentDB2.mdf ContentDB2.ldf DPM Filter – Volume Map
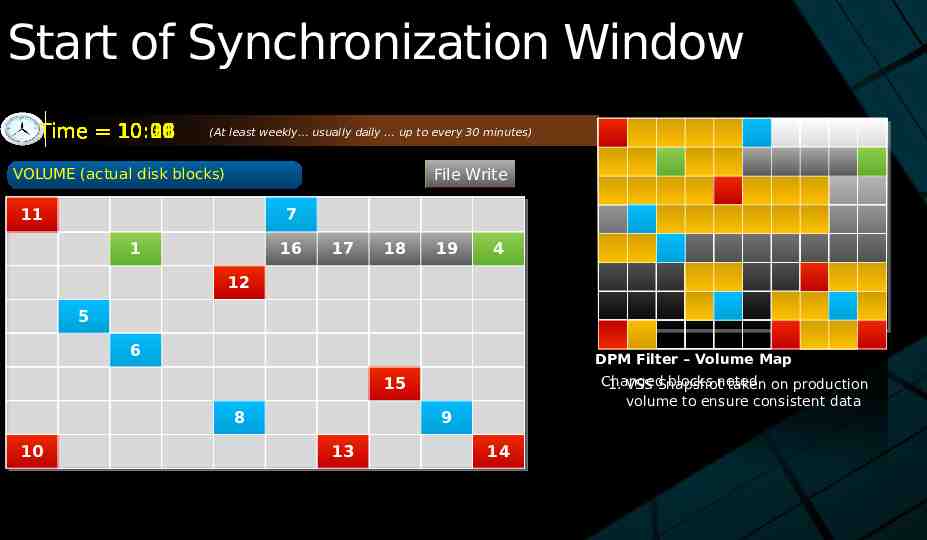
Start of Synchronization Window Time 10:30 10:00 10:01 10:06 10:18 10:26 (At least weekly usually daily up to every 30 minutes) File Write File Write VOLUME (actual disk blocks) 11 7 1 16 17 2 18 3 19 4 12 5 6 DPM Filter – Volume Map Changed blocks noted 1. VSS Snapshot taken on production volume to ensure consistent data 15 8 10 9 13 14
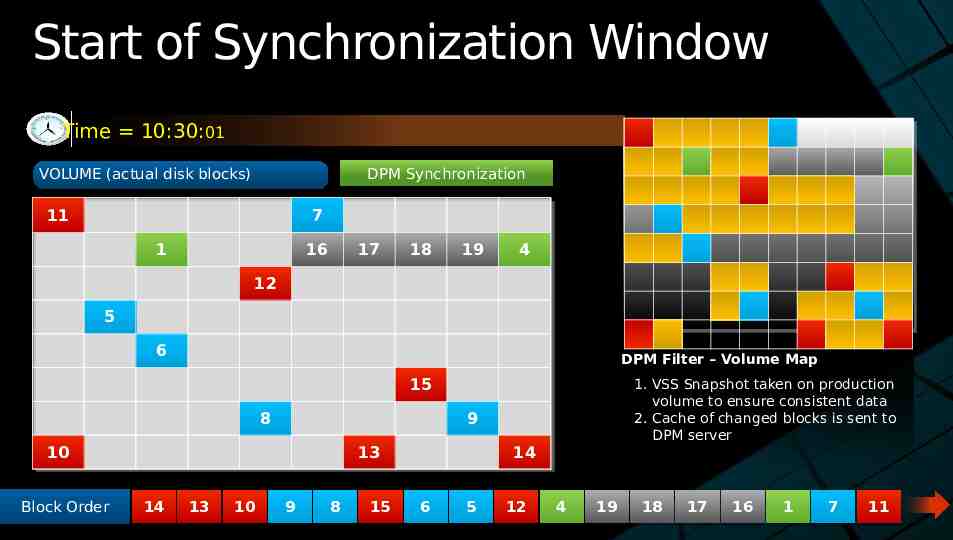
Start of Synchronization Window Time 10:30:01 DPM DPM Synchronization Synchronization VOLUME (actual disk blocks) 11 7 1 16 17 18 19 4 12 5 6 DPM Filter – Volume Map 15 8 9 10 Block Block Order Order 13 14 14 13 13 10 10 1. VSS Snapshot taken on production volume to ensure consistent data 2. Cache of changed blocks is sent to DPM server 9 9 8 8 15 15 14 6 6 5 5 12 12 4 4 19 19 18 18 17 17 16 16 1 1 7 7 11 11
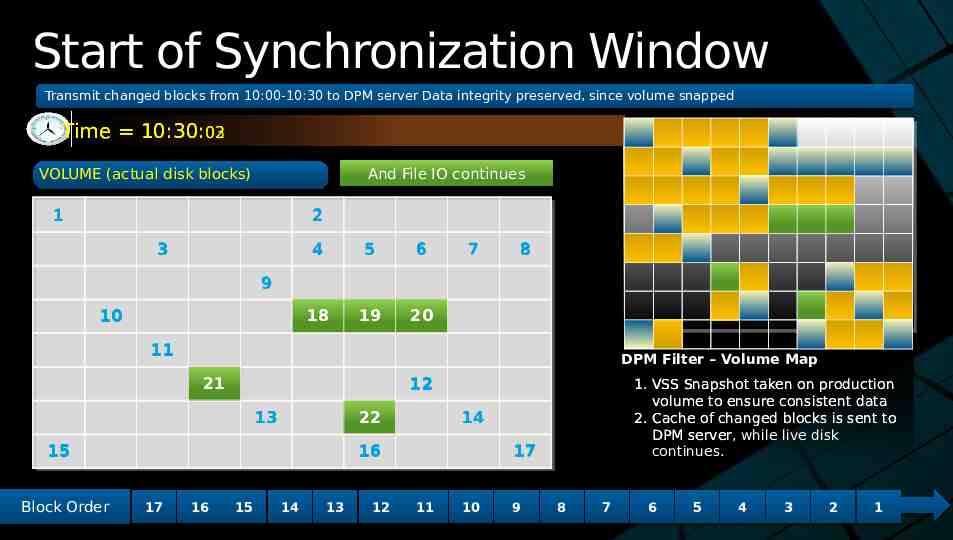
Start of Synchronization Window Transmit Transmit changed changed blocks blocks from from 10:00-10:30 10:00-10:30 to to DPM DPM server server Data Data integrity integrity preserved, preserved, since since volume volume snapped snapped Time 10:30:03 02 DPM And Synchronization IO DPM And File File Synchronization IO continues continues VOLUME (actual disk blocks) 1 2 3 4 5 6 18 19 20 7 8 9 10 11 DPM Filter – Volume Map 21 12 13 22 15 Block Block Order Order 14 16 17 17 16 16 15 15 14 14 13 13 12 12 1. VSS Snapshot taken on production volume to ensure consistent data 2. Cache of changed blocks is sent to DPM server, server while live disk continues. 17 11 11 10 10 9 9 8 8 7 7 6 6 5 5 4 4 3 3 2 2 1 1
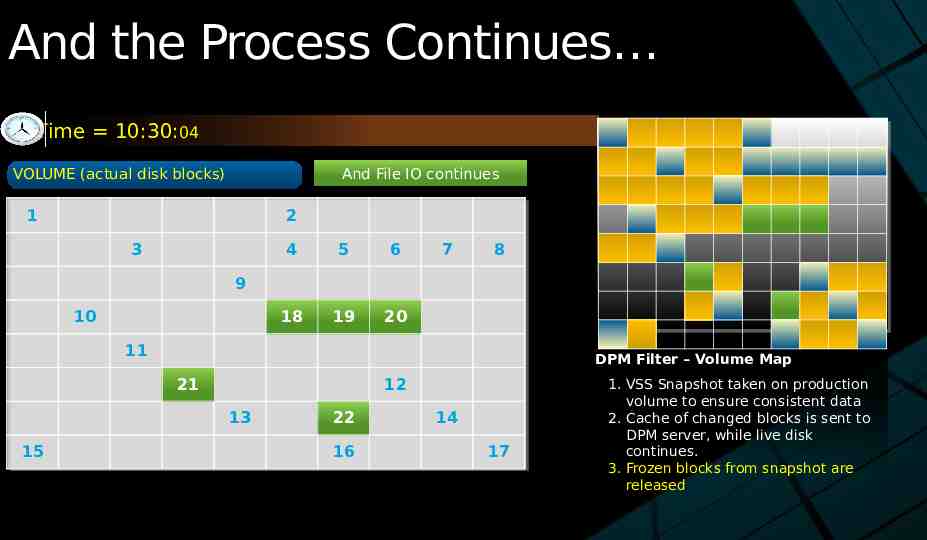
And the Process Continues Time 10:30:04 And And File File IO IO continues continues VOLUME (actual disk blocks) 1 2 3 4 5 6 18 19 20 7 8 9 10 11 DPM Filter – Volume Map 21 12 13 15 22 16 14 17 1. VSS Snapshot taken on production volume to ensure consistent data 2. Cache of changed blocks is sent to DPM server, while live disk continues. 3. Frozen blocks from snapshot are released

How DPM protects data Transactional Log backups

Efficient Protection Beyond De-duplication Baseline initial mirror Production Server Database 0:00 DPM Replica Baseline Initial Mirror Database 0:00
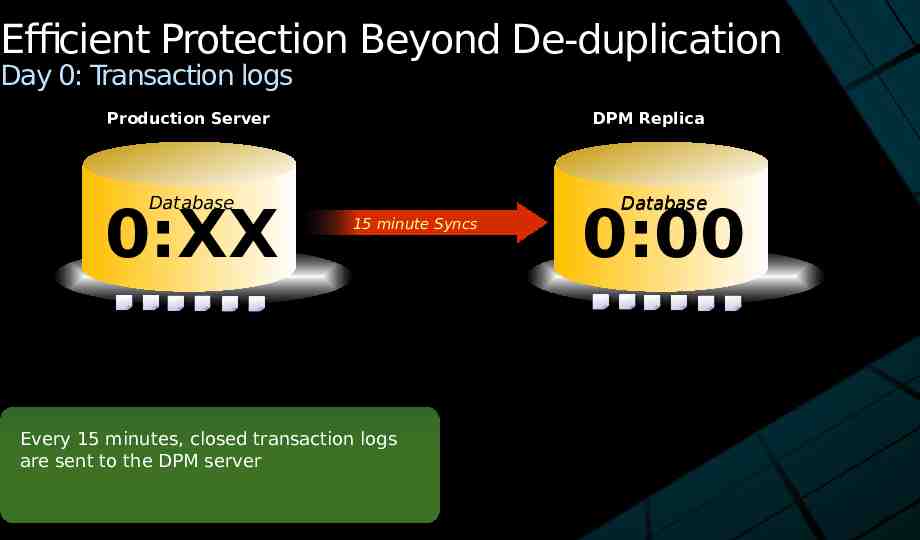
Efficient Protection Beyond De-duplication Day 0: Transaction logs Production Server DPM Replica Database 0:XX Database 15 minute Syncs Every 15 minutes, closed transaction logs are sent to the DPM server 0:00
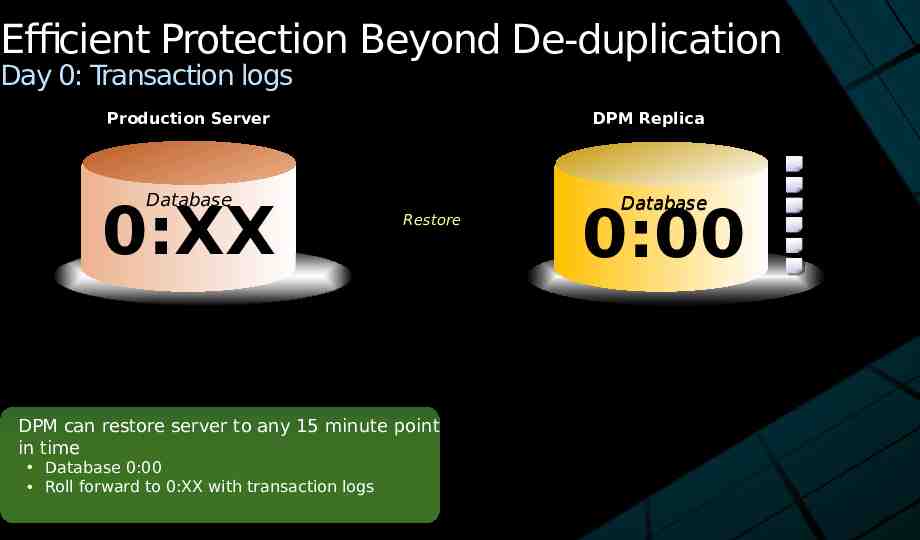
Efficient Protection Beyond De-duplication Day 0: Transaction logs Production Server DPM Replica Database 0:XX Restore DPM can restore server to any 15 minute point in time Database 0:00 Roll forward to 0:XX with transaction logs Database 0:00
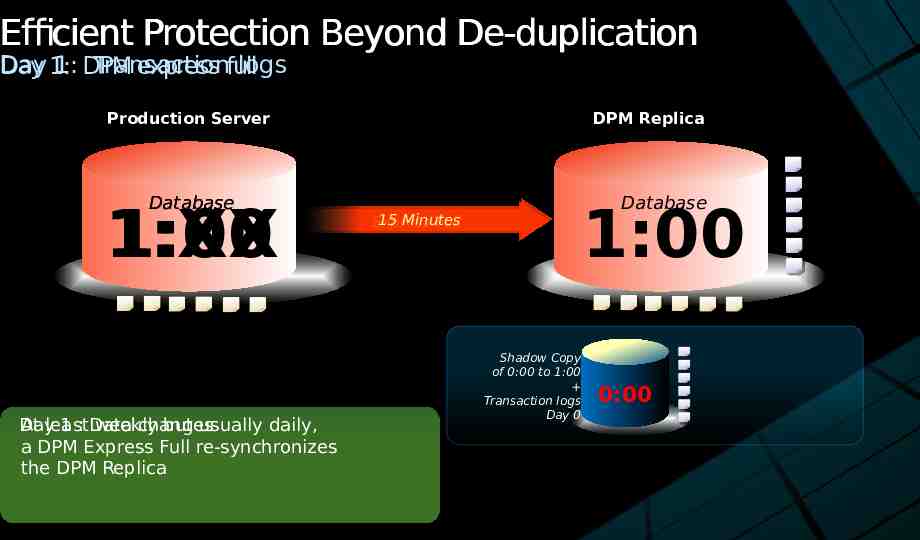
Efficient Protection Beyond De-duplication Day 1: DPM Transaction logs Day 1: express full Production Server Database 1:XX 1:00 Day At least 1 : Data weekly changes but usually daily, a DPM Express Full re-synchronizes the DPM Replica DPM Replica Database 1:00 0:00 15 Minutes Express Full Shadow Copy of 0:00 to 1:00 Transaction logs Day 0 0:00
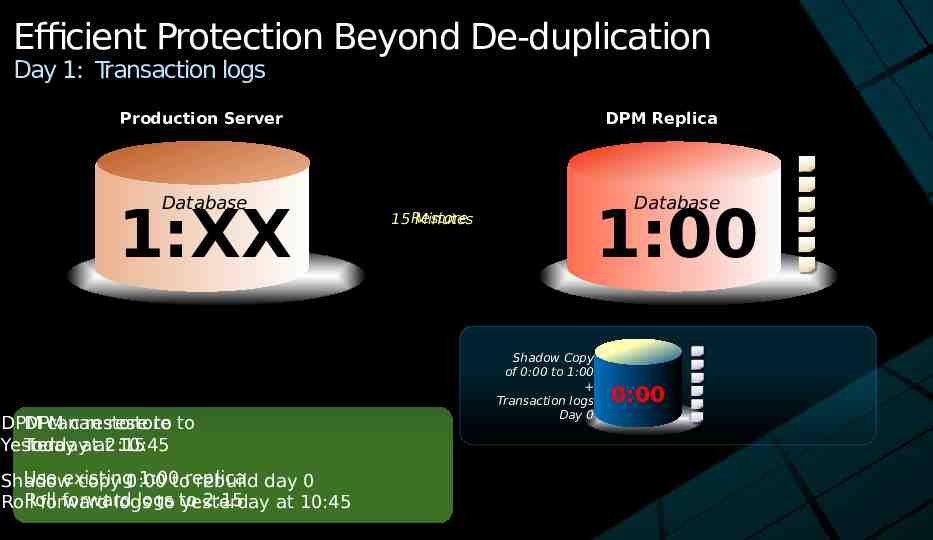
Efficient Protection Beyond De-duplication Day 1: Transaction logs Production Server Database 1:XX DPM can restore to to DPM can restore Yesterday 10:45 Today atat2:15 Use existing 1:00toreplica Shadow copy 0:00 rebuild day 0 Roll forward logs 2:15 Roll forward logs to to yesterday at 10:45 DPM Replica Database 1:00 15 Restore Minutes Shadow Copy of 0:00 to 1:00 Transaction logs Day 0 0:00
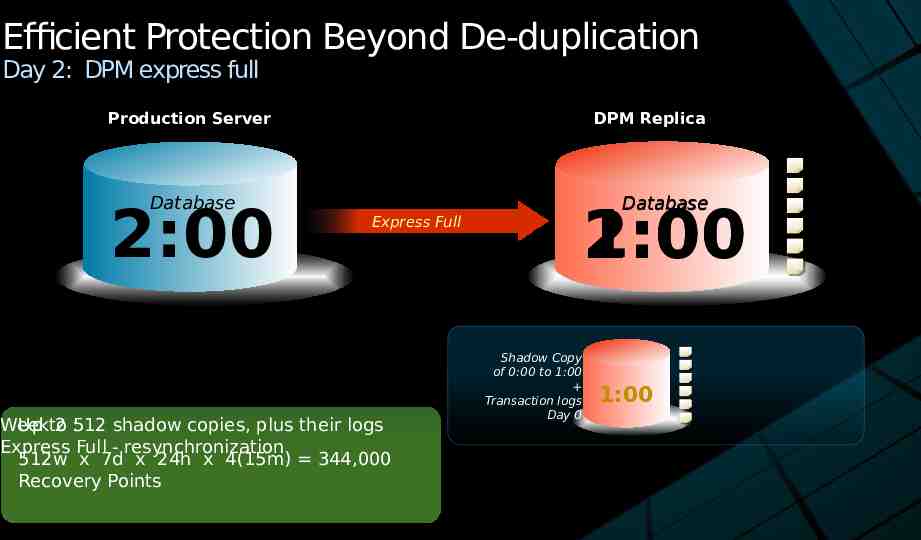
Efficient Protection Beyond De-duplication Day 2: DPM express full Production Server Database 2:00 DPM Replica Database 1:00 2:00 Express Full Week Up to 2 :512 shadow copies, plus their logs Express Full - resynchronization 512w x 7d x 24h x 4(15m) 344,000 Recovery Points Shadow Copy of 0:00 to 1:00 Transaction logs Day 0 0:00 1:00

Rapid & Reliable Recovery demo

DPM 2010 Windows Application and File servers Microsoft Virtualization Windows Clients Disaster Recovery Enterprise-Ready Scalability & Reliability

DPM 2010 – Windows Platforms Windows Server 2008 R2 Windows Server 2008 Windows Storage Server 2008 Windows Windows Windows Windows Server 2003 R2 Server 2003 Service Pack 1 Storage Server 2003 R2 Unified Data Storage Server Windows 7 Windows Vista Business or higher Windows XP Professional - Service Pack 2

DPM 2010 – Application Platforms Microsoft SQL Server 2008 Microsoft SQL Server 2005 Microsoft SQL Server 2000 Service Pack 4 SAP running on Microsoft SQL Server Microsoft Exchange Server 2010 Microsoft Exchange Server 2007 Microsoft Exchange Server 2003 – including DAG – including LCR, CCR , and SCR Service Pack 2 Microsoft Office SharePoint Server 2010 Microsoft Office SharePoint Server 2007 Microsoft Office SharePoint Portal Server 2003 Windows SharePoint Foundation Services 4.0 Windows SharePoint Services version 3.0 Windows SharePoint Services version 2.0 Microsoft Dynamics AX 2009 Windows Essential Business Server 2008 Windows Small Business Server 2008 new in DPM 2010
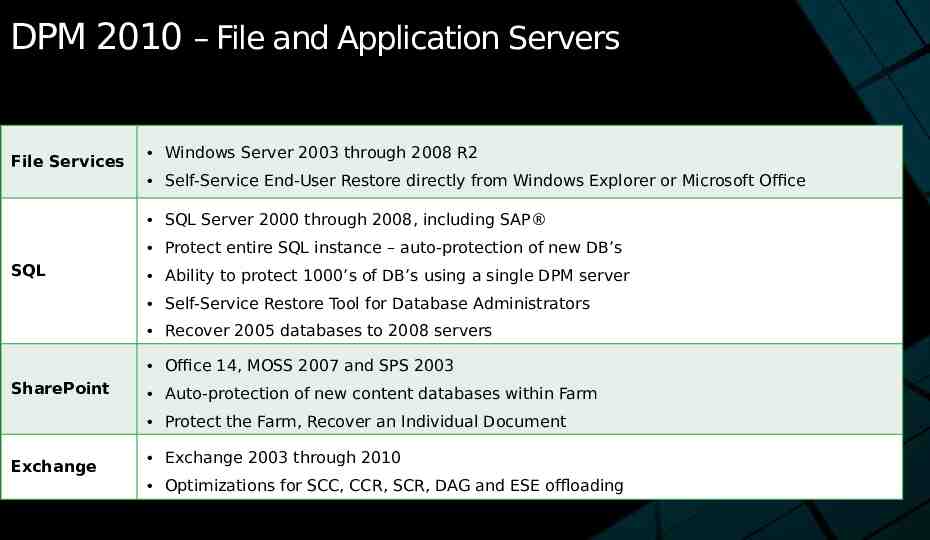
DPM 2010 – File and Application Servers File Services Windows Server 2003 through 2008 R2 Self-Service End-User Restore directly from Windows Explorer or Microsoft Office SQL Server 2000 through 2008, including SAP Protect entire SQL instance – auto-protection of new DB’s SQL Ability to protect 1000’s of DB’s using a single DPM server Self-Service Restore Tool for Database Administrators Recover 2005 databases to 2008 servers Office 14, MOSS 2007 and SPS 2003 SharePoint Auto-protection of new content databases within Farm Protect the Farm, Recover an Individual Document Exchange Exchange 2003 through 2010 Optimizations for SCC, CCR, SCR, DAG and ESE offloading
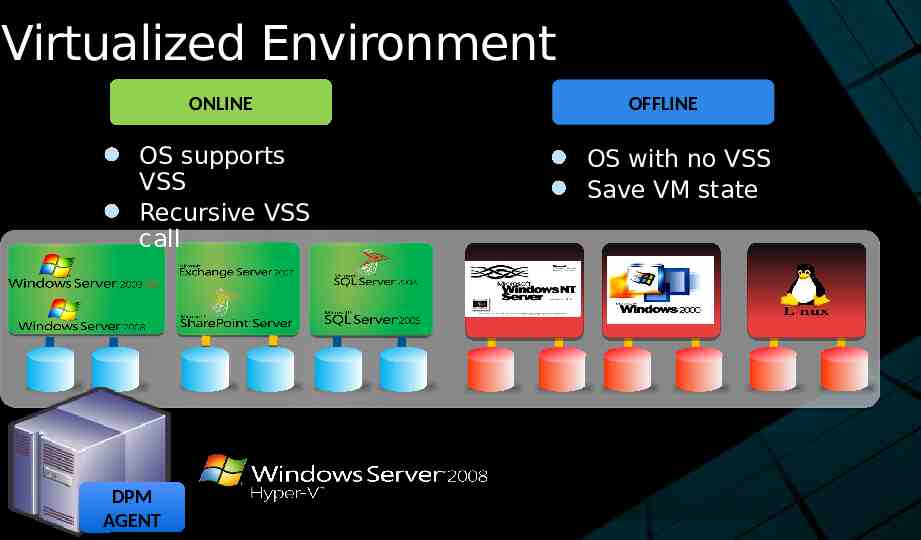
Virtualized Environment ONLINE OS supports VSS Recursive VSS call DPM AGENT OFFLINE OS with no VSS Save VM state

Protect from host or guest? Host Protect or recover the whole machine “Bare Metal Recovery” & “Item Level Recovery” of every VM Protect non-Windows servers & LOB applications without VSS writers No granularity of backup Single DPM license on host, all guests protected DPML Guest Protect or recover data specifically SQL / Exchange / SharePoint / Files No different than protecting a physical server DPML per Guest DPML Yes, they can work together !
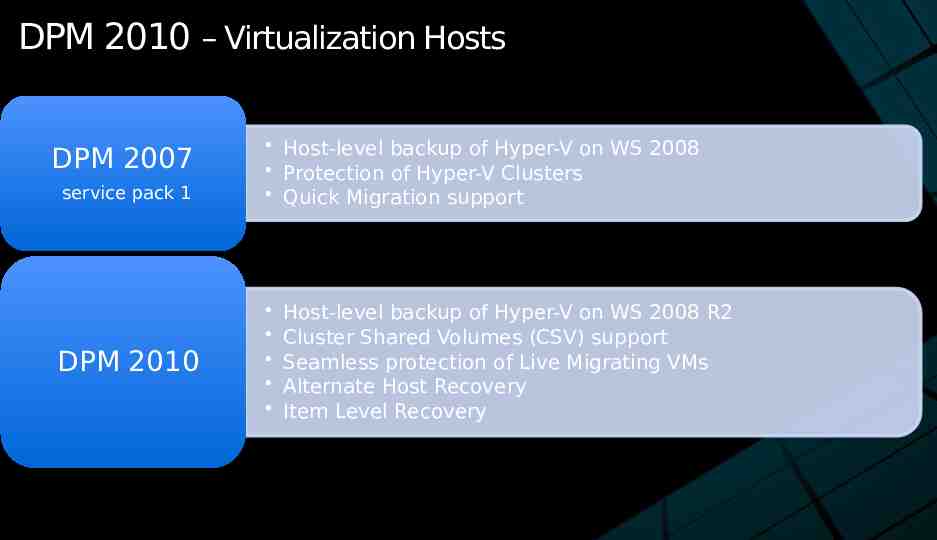
DPM 2010 – Virtualization Hosts DPM 2007 service pack 1 DPM 2010 Host-level backup of Hyper-V on WS 2008 Protection of Hyper-V Clusters Quick Migration support Host-level backup of Hyper-V on WS 2008 R2 Cluster Shared Volumes (CSV) support Seamless protection of Live Migrating VMs Alternate Host Recovery Item Level Recovery

DPM 2010 – Roaming Laptops Best in class laptop protection for Windows Clients Support for XP, Vista, and W7 Backup over VPN and Direct Access Scale to 1000 clients per DPM server “Unique user data” only Not the whole machine, so that the OS is not repeatedly backed up Integration with local Shadow Copies for Vista & W7 Centrally configured from DPM admin UI End User enabled restore from local copies offline and online, as well as DPM copies Admin enabled restore from DPM copies
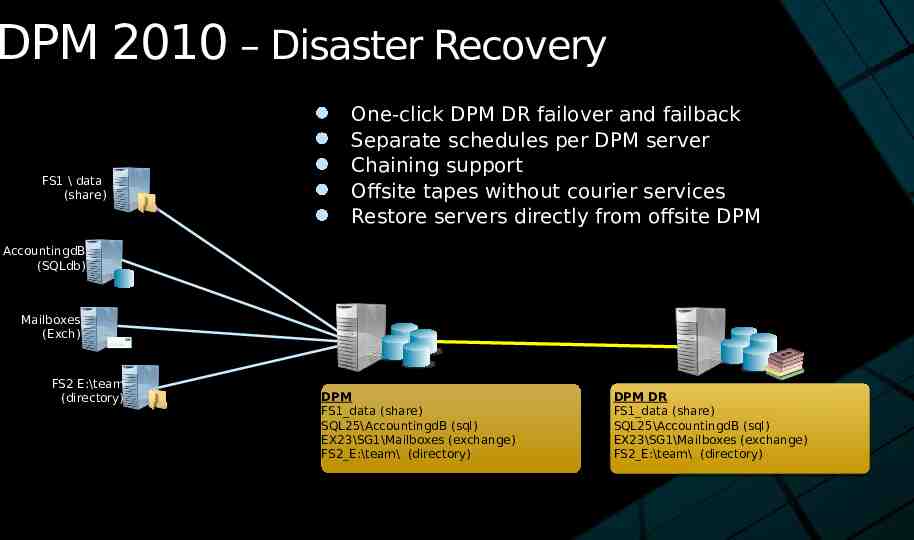
DPM 2010 – Disaster Recovery FS1 \ data (share) One-click DPM DR failover and failback Separate schedules per DPM server Chaining support Offsite tapes without courier services Restore servers directly from offsite DPM AccountingdB (SQLdb) Mailboxes (Exch) FS2 E:\team (directory) DPM FS1 data (share) SQL25\AccountingdB (sql) EX23\SG1\Mailboxes (exchange) FS2 E:\team\ (directory) DPM DR FS1 data (share) SQL25\AccountingdB (sql) EX23\SG1\Mailboxes (exchange) FS2 E:\team\ (directory)

DPM 2010 – Enterprise Ready 100 Servers, 1000 Laptops, up to 2000 Database per Server Scalability Significantly increased fan-in of data sources per DPM server Up to 80 TB per DPM server Automatic re-running of jobs and improved self-healing Reliability Automatic protection of new data sources for SQL & MOSS Decreased “Inconsistent Replicas” errors Reduced Alert volume
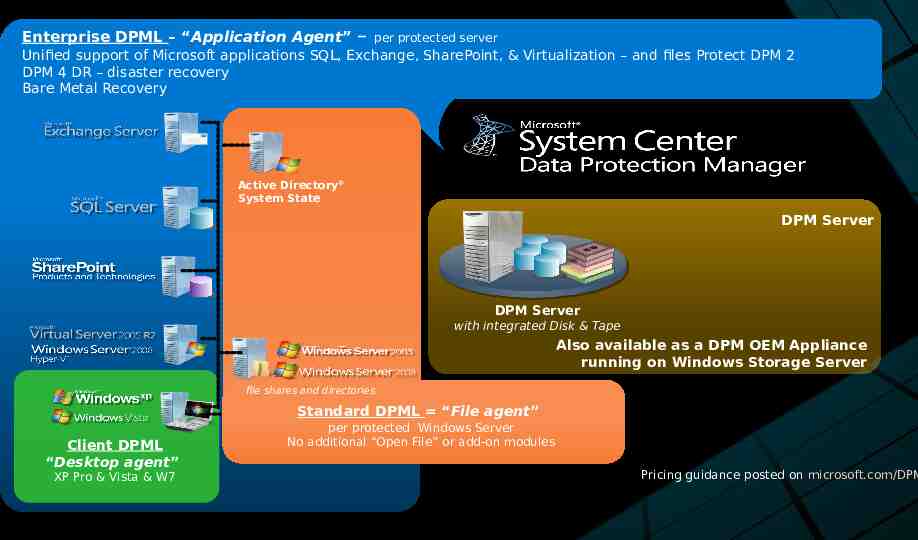
Enterprise DPML – “Application Agent” – per protected server Unified support of Microsoft applications SQL, Exchange, SharePoint, & Virtualization – and files Protect DPM 2 DPM 4 DR – disaster recovery Bare Metal Recovery Active Directory System State DPM Server DPM Server with integrated Disk & Tape Also available as a DPM OEM Appliance running on Windows Storage Server file shares and directories Standard DPML “File agent” Client DPML “Desktop agent” XP Pro & Vista & W7 per protected Windows Server No additional “Open File” or add-on modules Pricing guidance posted on microsoft.com/DPM

DPM 2010 Best for Windows file and application servers – from Microsoft Built for Microsoft Virtualization environments Designed for Windows Clients Enterprise-Ready scalability and reliability
Resources & Tools for DPM Web Site www.microsoft.com/DPM blogs.technet.com/DPM Info DPM 2010 overview datasheet and webcast Datasheets, technical white papers, and on-demand webcasts: How to Protect SQL Server with DPM 2010 How to Protect Microsoft Exchange with DPM 2010 How to Protect SharePoint with DPM 2010 How to Protect Virtualized Environments with DPM 2010 TechNet virtual labs - for hands-on learning with DPM DPM 2010 overview information and webcast E-mail [email protected] MS http://SystemCenterWeb

2010 Microsoft Corporation. All rights reserved. Microsoft, Windows, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U.S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.