SEC555 Presentation based on SEC555: SIEM with Tactical Analytics
23 Slides2.66 MB

SEC555 Presentation based on SEC555: SIEM with Tactical Analytics Stuck in the Box: A SIEM’s Tale Justin Henderson (GSE # 108) @SecurityMapper

About Me Author of SEC555: SIEM with Tactical Analytics GIAC GSE # 108, Cyber Guardian Blue and Red 58 industry certifications (need to get a new hobby) Two time NetWars Core tournament winner (offense) And security hobbyist and community supporter Collecting interns/contributors in bulk (research teams) SEC555 SIEM with Tactical Analytics 2

Welcome! A copy of this talk is available at https://www.securitymapper.com Virtual machine used during presentation is available for download at above link More free stuff: https://github.com/SMAPPER Disclaimer: This talk is not about bashing SIEM solutions or promoting one vendor/solution above the others SEC555 SIEM with Tactical Analytics 3

SIEM Detection Gap Working with multiple organizations there are clearly gaps in SIEM deployments Example: One organization spent 14 months in deployment SIEM was/is within top 5 of magic quadrant 2014 - 2017 Two employees during roll out ( 1 FTE of labor for 14 months) Within less than 1 month open source solution exceeded what they SEC555 had SIEM with Tactical Analytics 4

SIEM Deployment Well they must have lacked training and planning, right? Both employees attended week long vendor training POC lasted well over three months Implementation had 30 days of professional services One employee hired as dedicated FTE to SIEM One PTE and other employee(s) available to help SEC555 SIEM with Tactical Analytics 5

What Happened? Ultimately the company discarded commercial solution Open source solution still in place People and processes are more important than the tool! Focus should not be solely on SIEM care and feeding Detection techniques are required and must scale SEC555 SIEM with Tactical Analytics Automation is a must! 6
NXLog AutoConfig Overcomes log agent deficiencies and is a functional proof of concept https://github.com/SMAPPER/NXLog-AutoConfig Checks systems each day looking for components (IIS, etc) If found, automatically configures for consistency Or initial configuration Then sets up agent to start shipping logs Largest deployment maintained 12 K systems SEC555 SIEM with Tactical Analytics 7
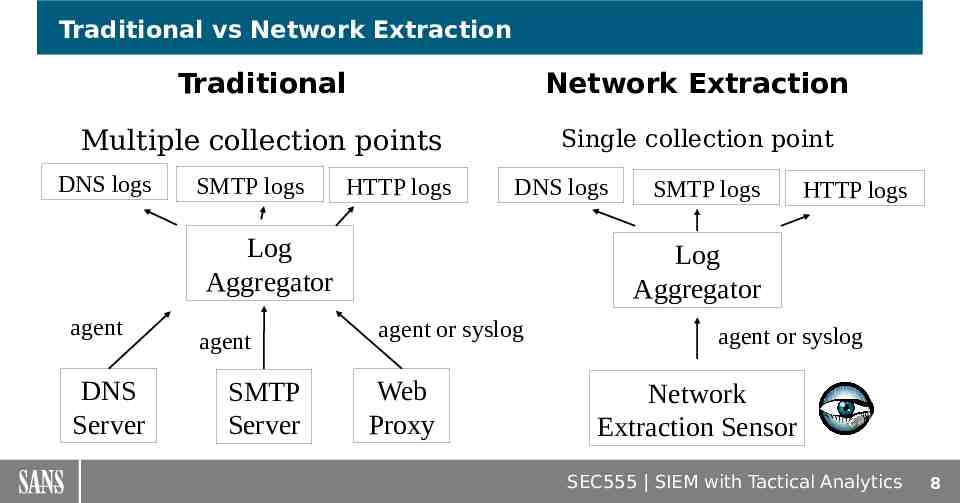
Traditional vs Network Extraction Traditional Network Extraction Multiple collection points Single collection point DNS logs SMTP logs HTTP logs DNS logs Log Aggregator agent DNS Server agent SMTP Server SMTP logs HTTP logs Log Aggregator agent or syslog Web Proxy agent or syslog Network Extraction Sensor SEC555 SIEM with Tactical Analytics 8

Service Profiling with SIEM Infrastructure Service Logs DNS HTTP HTTPS SMTP Almost every network uses them Lots of noise lots of logs Yet can be high value Enrichment Techniques Low value logs can morph into highly actionable detects Baby Domains Entropy Test (PH Imbalance) Invalid Fields (wrong state) Fuzzy Phishing SEC555 SIEM with Tactical Analytics 9
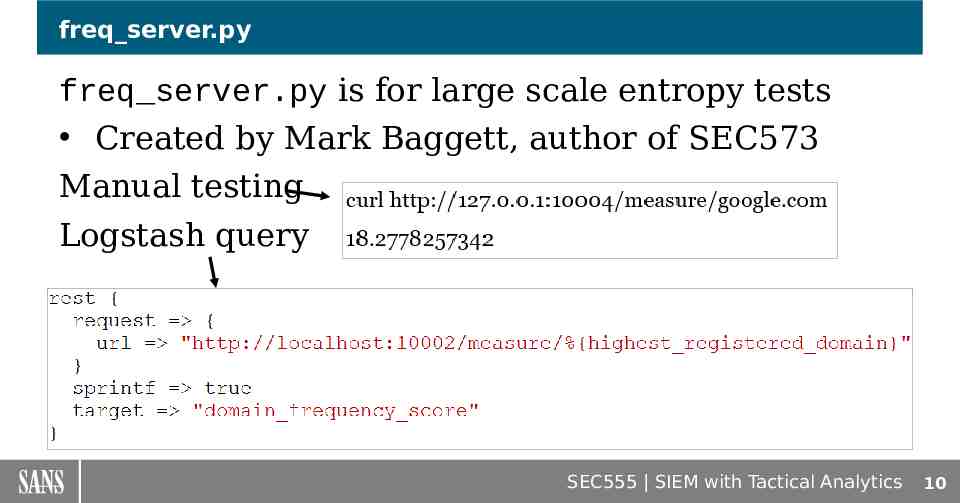
freq server.py freq server.py is for large scale entropy tests Created by Mark Baggett, author of SEC573 Manual testing Logstash query SEC555 SIEM with Tactical Analytics 10
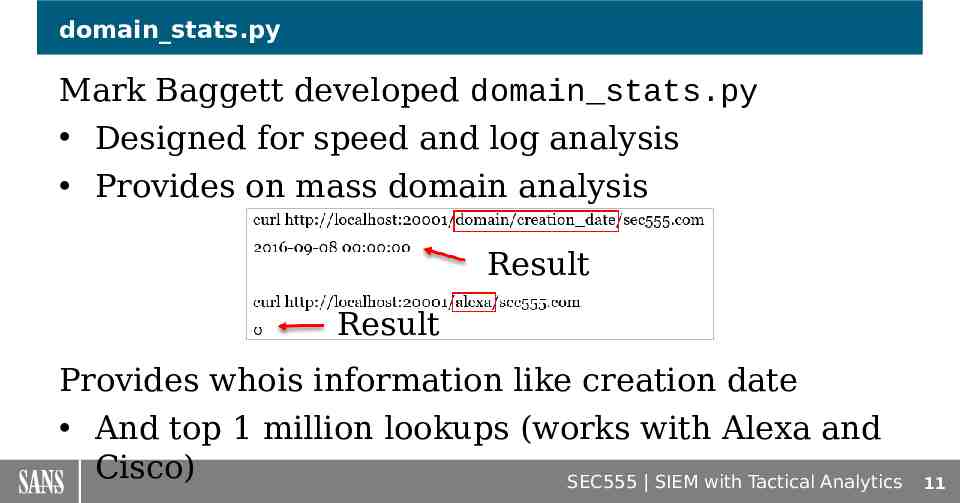
domain stats.py Mark Baggett developed domain stats.py Designed for speed and log analysis Provides on mass domain analysis Result Result Provides whois information like creation date And top 1 million lookups (works with Alexa and Cisco) SEC555 SIEM with Tactical Analytics 11
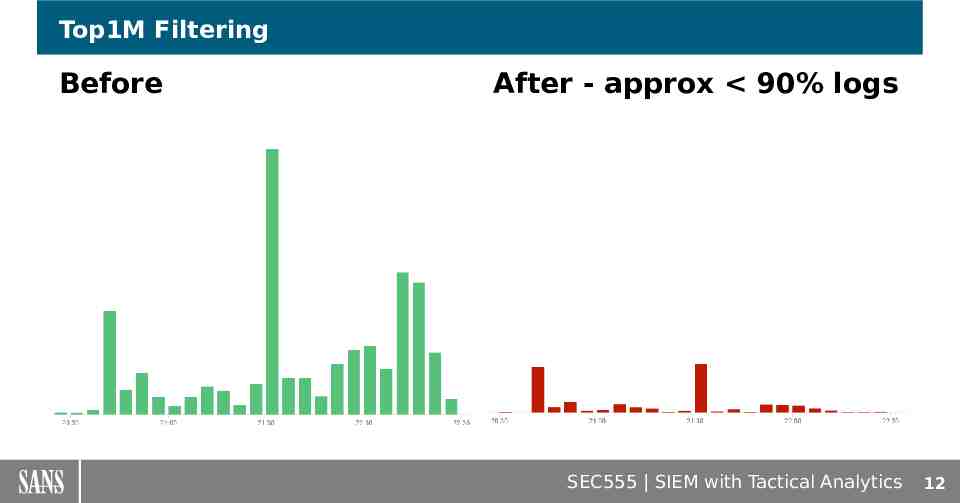
Top1M Filtering Before After - approx 90% logs SEC555 SIEM with Tactical Analytics 12
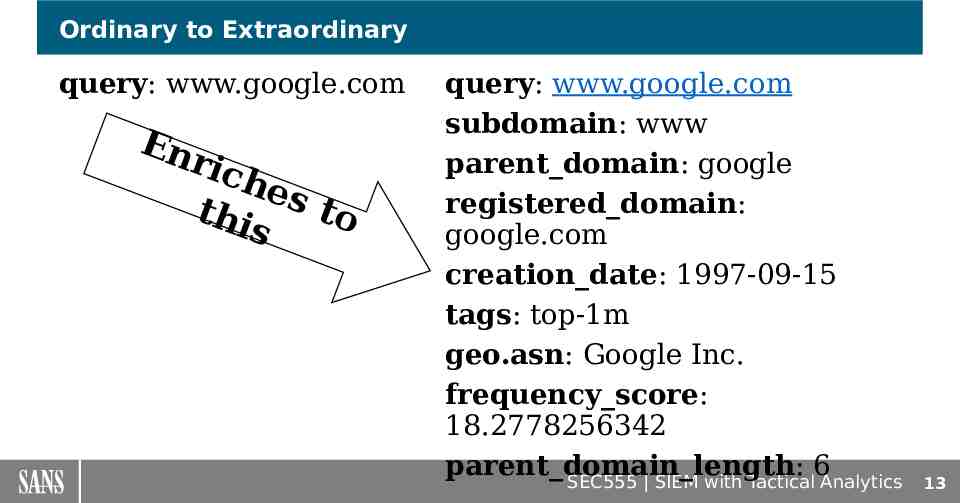
Ordinary to Extraordinary query: www.google.com En ric hes to t hi s query: www.google.com subdomain: www parent domain: google registered domain: google.com creation date: 1997-09-15 tags: top-1m geo.asn: Google Inc. frequency score: 18.2778256342 parent domain length: 6 SEC555 SIEM with Tactical Analytics 13

Fuzzy Phishing Many SIEM techniques use insider information Such as fuzzy phishing searches Take legitimate company domains and look for variants Extremely effective against phishing domains Best used in combination with email alerts or scripts Great for targeted attacks SEC555 SIEM with Tactical Analytics 14
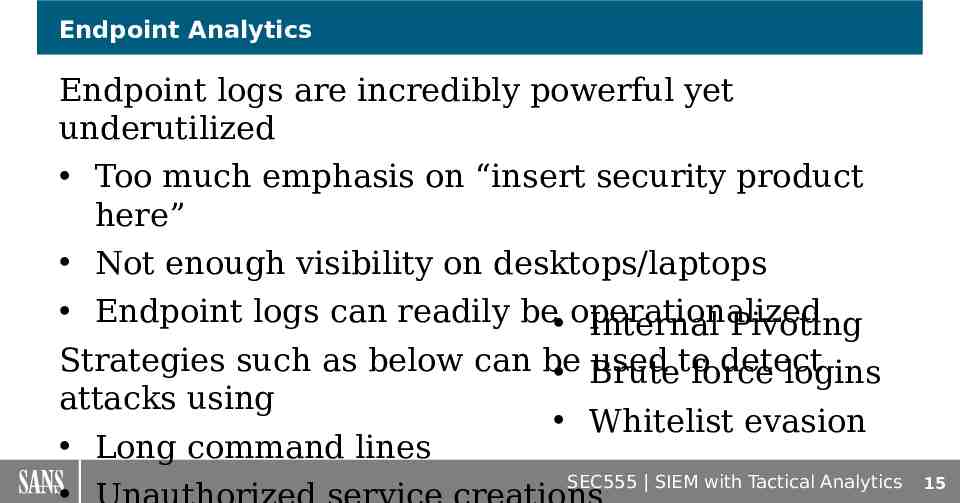
Endpoint Analytics Endpoint logs are incredibly powerful yet underutilized Too much emphasis on “insert security product here” Not enough visibility on desktops/laptops Endpoint logs can readily be operationalized Internal Pivoting Strategies such as below can be used to detect Brute force logins attacks using Whitelist evasion Long command lines SEC555 SIEM with Tactical Analytics 15

Service Creation Gone Bad (Event ID: 7045) Common attack techniques create services Top example is of Meterpreter compromise through PSExec Bottom event is of privilege escalation SEC555 SIEM with Tactical Analytics 16
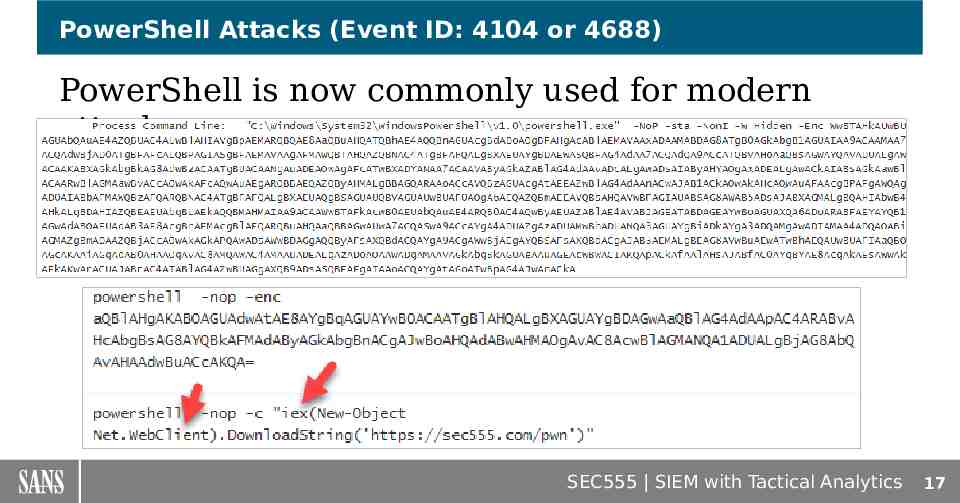
PowerShell Attacks (Event ID: 4104 or 4688) PowerShell is now commonly used for modern attacks SEC555 SIEM with Tactical Analytics 17
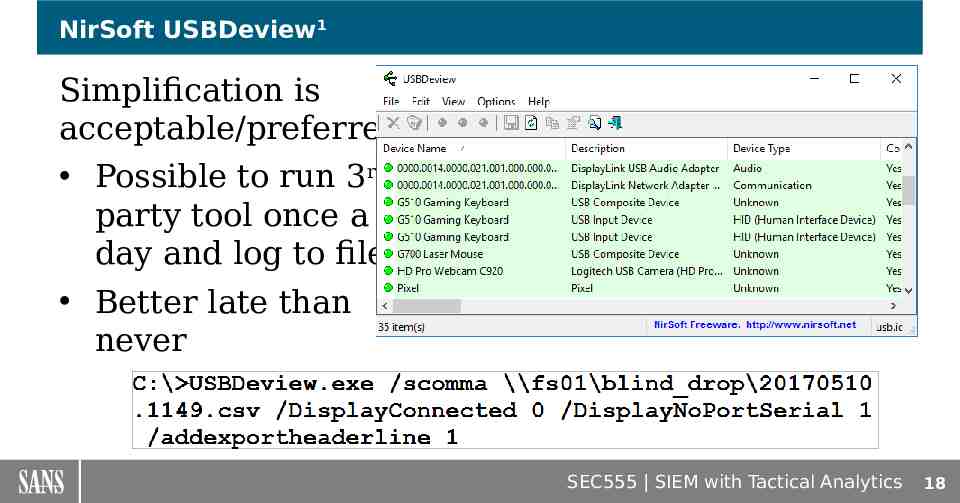
NirSoft USBDeview1 Simplification is acceptable/preferred Possible to run 3rd party tool once a day and log to file Better late than never SEC555 SIEM with Tactical Analytics 18
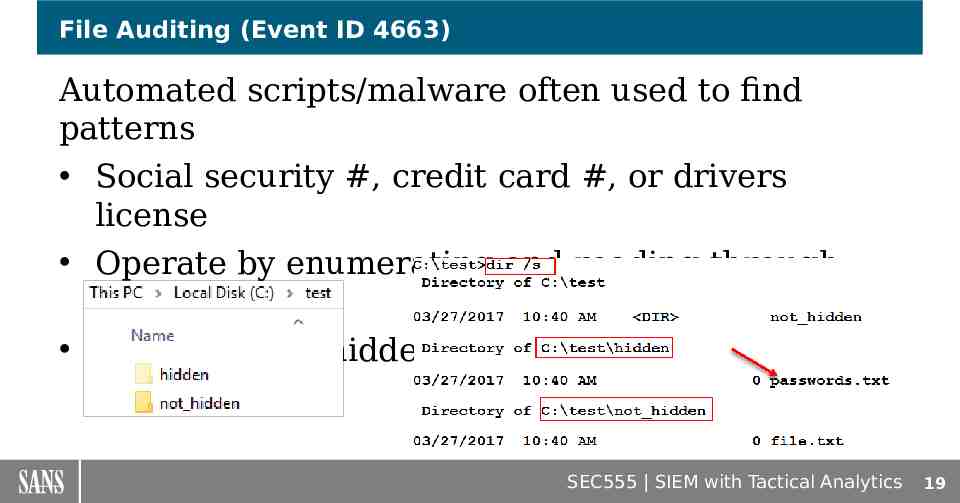
File Auditing (Event ID 4663) Automated scripts/malware often used to find patterns Social security #, credit card #, or drivers license Operate by enumerating and reading through files Often ignores hidden folders SEC555 SIEM with Tactical Analytics 19
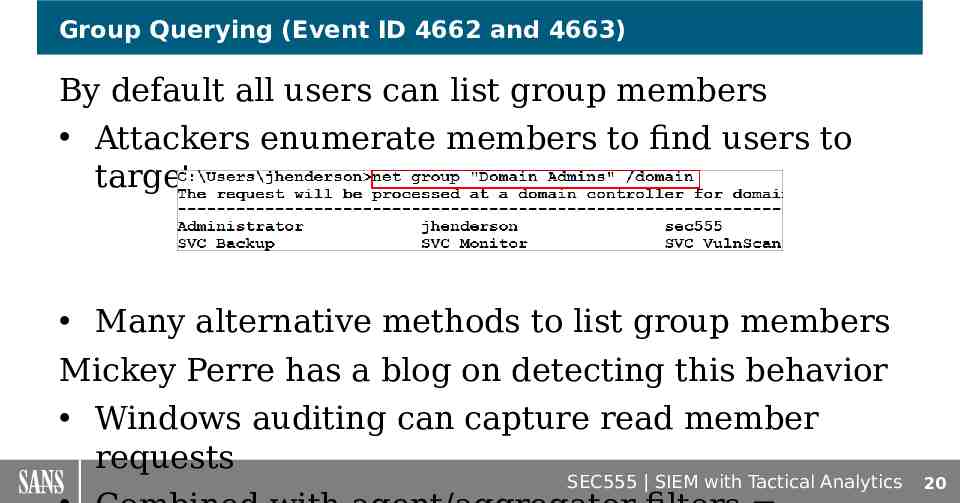
Group Querying (Event ID 4662 and 4663) By default all users can list group members Attackers enumerate members to find users to target Many alternative methods to list group members Mickey Perre has a blog on detecting this behavior Windows auditing can capture read member requests SEC555 SIEM with Tactical Analytics 20

HALO (Honeytokens Against Leveraging OSINT) Fake users can be created publicly to combat recon Could be just in hidden metadata and/or key public sites Example: Peter Parker([email protected]) On LinkedIn, Facebook, Adobe, PGP, Github, etc. Likely to be picked up during OSINT Eventually may make compromised account lists Takes minimal time to setup can get fairly elaborate SEC555 SIEM with Tactical Analytics 21
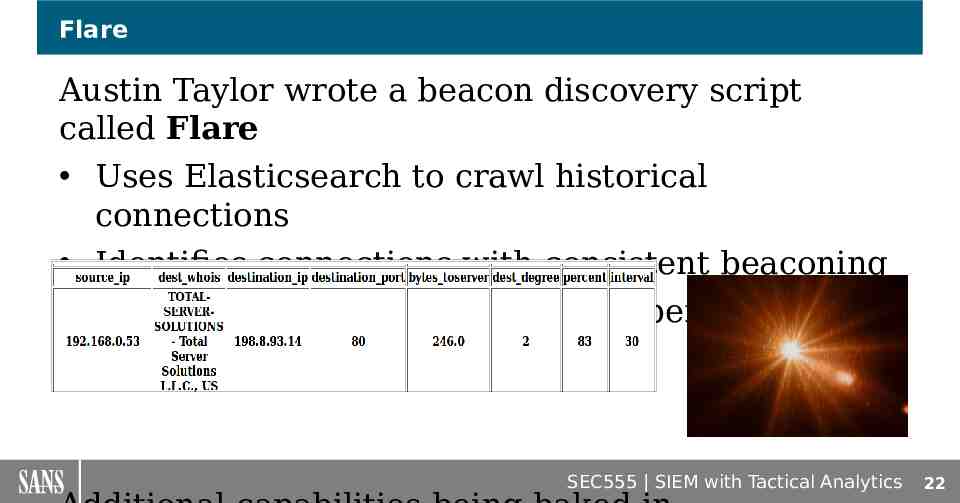
Flare Austin Taylor wrote a beacon discovery script called Flare Uses Elasticsearch to crawl historical connections Identifies connections with consistent beaconing Supports analysis of custom time periods SEC555 SIEM with Tactical Analytics 22

ELK Hunter Designed for analysis, research, and proof of concept ELK Hunter is a test bed for configs and concepts Contains Security Onion, ELK, and analysis scripts Designed to plug into network or deploy to hypervisor Verifies legitimacy of techniques and configurations Discover new techniques or abnormal behaviors SEC555 SIEM with Tactical Analytics 23






