Quantum Cryptography Beyond the buzz Grégoire Ribordy CERN, May
43 Slides3.89 MB

Quantum Cryptography Beyond the buzz Grégoire Ribordy CERN, May 3rd 2006

Outline Quantum physics and information technology The limits of classical cryptography The principles of quantum cryptography Practical systems and applications Future directions www.idquantique.com 2
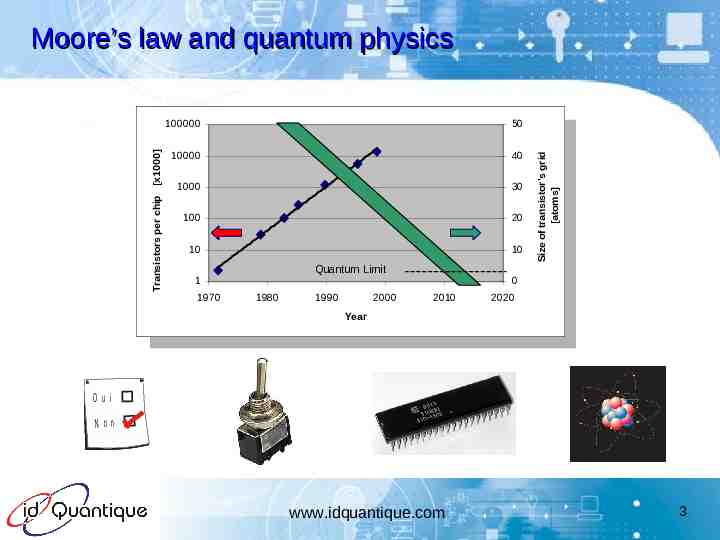
100000 50 10000 40 1000 30 100 20 10 10 Quantum Limit 1 1970 1980 1990 2000 Size of transistor's grid [atoms] Transistors chip [x1000] Transistors perper chip [x1000] Moore’s law and quantum physics 0 2010 2020 Year O ui N on www.idquantique.com 3
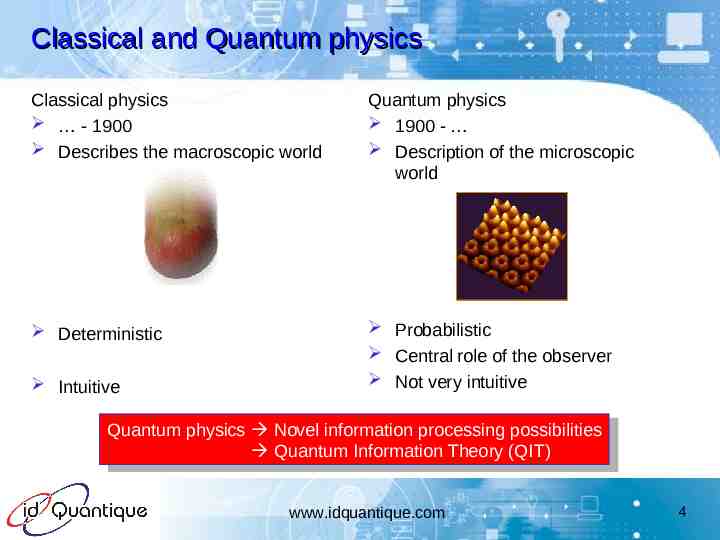
Classical and Quantum physics Classical physics - 1900 Describes the macroscopic world Quantum physics 1900 - Description of the microscopic world Deterministic Probabilistic Central role of the observer Not very intuitive Intuitive Quantum physics Novel information processing possibilities Quantum Information Theory (QIT) www.idquantique.com 4
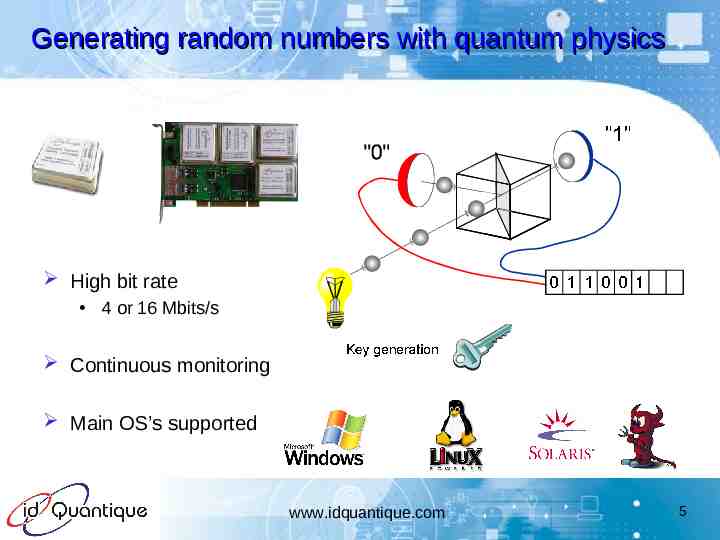
Generating random numbers with quantum physics High bit rate 4 or 16 Mbits/s Continuous monitoring Main OS’s supported www.idquantique.com 5

Outline Quantum physics and information technology The limits of classical cryptography The principles of quantum cryptography Practical systems and applications Future directions www.idquantique.com 6
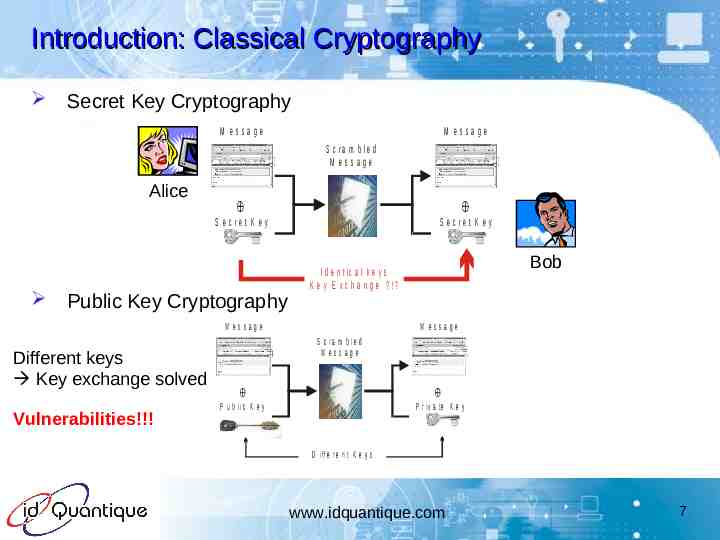
Introduction: Classical Cryptography Secret Key Cryptography M essage M essage S c r a m b le d M essage Alice S e c re t K e y S e c re t K e y Public Key Cryptography M essage Different keys Key exchange solved Vulnerabilities!!! Bob I d e n t ic a l k e y s K e y E x c h a n g e ? !? M essage S c r a m b le d M essage P u b li c K e y P r iv a t e K e y D iff e r e n t K e y s www.idquantique.com 7
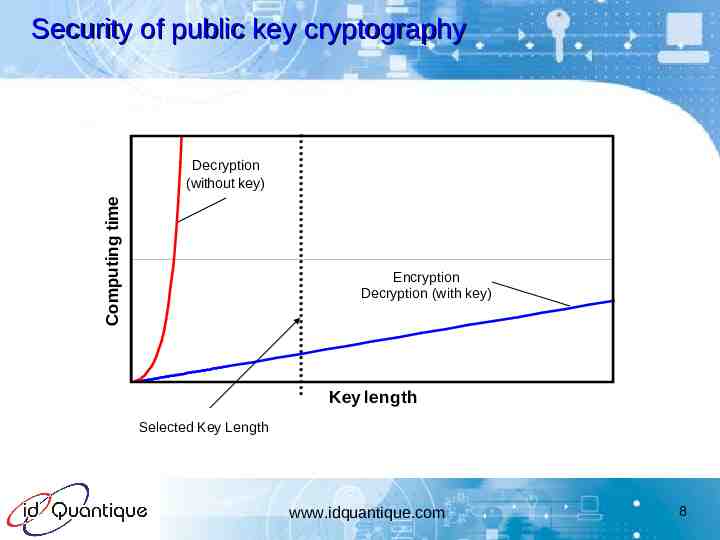
Security of public key cryptography Computing time Decryption (without key) Encryption Decryption (with key) Key length Selected Key Length www.idquantique.com 8
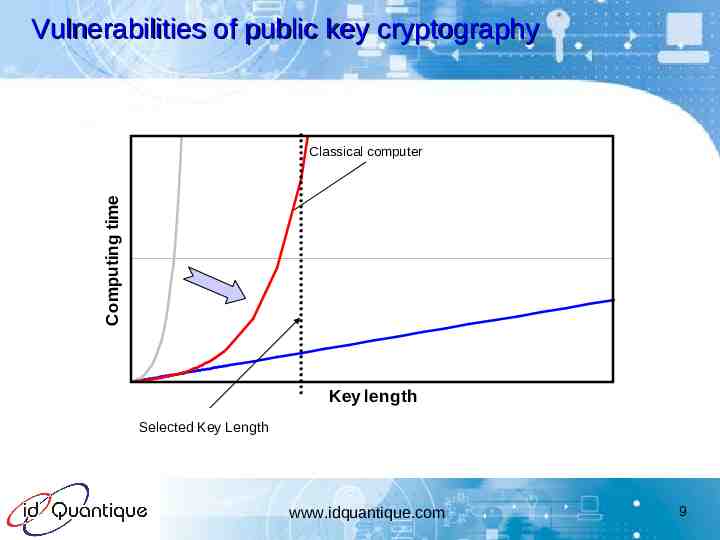
Vulnerabilities of public key cryptography Computing time Classical computer Key length Selected Key Length www.idquantique.com 9
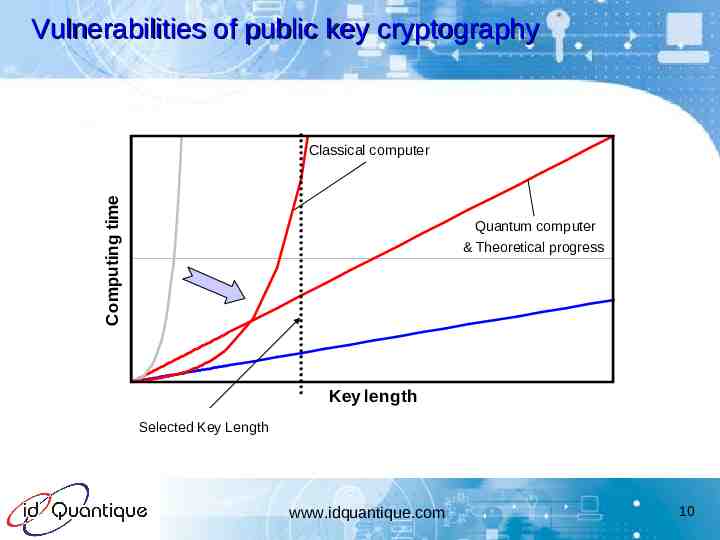
Vulnerabilities of public key cryptography Computing time Classical computer Quantum computer & Theoretical progress Key length Selected Key Length www.idquantique.com 10
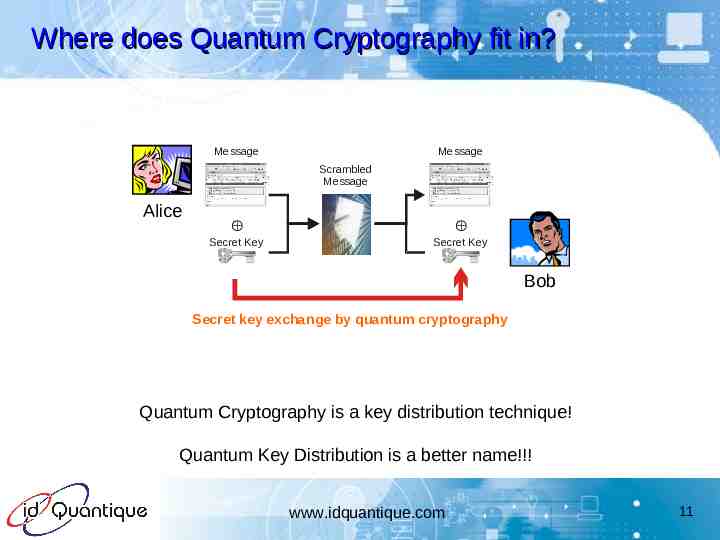
Where does Quantum Cryptography fit in? Message Message Scrambled Message Alice Secret Key Secret Key Bob Secret key exchange by quantum cryptography Quantum Cryptography is a key distribution technique! Quantum Key Distribution is a better name!!! www.idquantique.com 11

Outline Quantum physics and information technology The limits of classical cryptography The principles of quantum cryptography Practical systems and applications Future directions www.idquantique.com 12
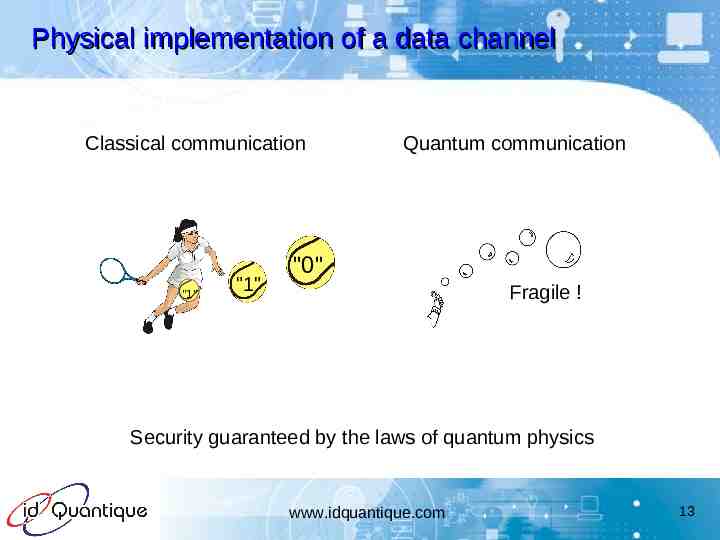
Physical implementation of a data channel Classical communication "1" "1" Quantum communication "0" Fragile ! Security guaranteed by the laws of quantum physics www.idquantique.com 13
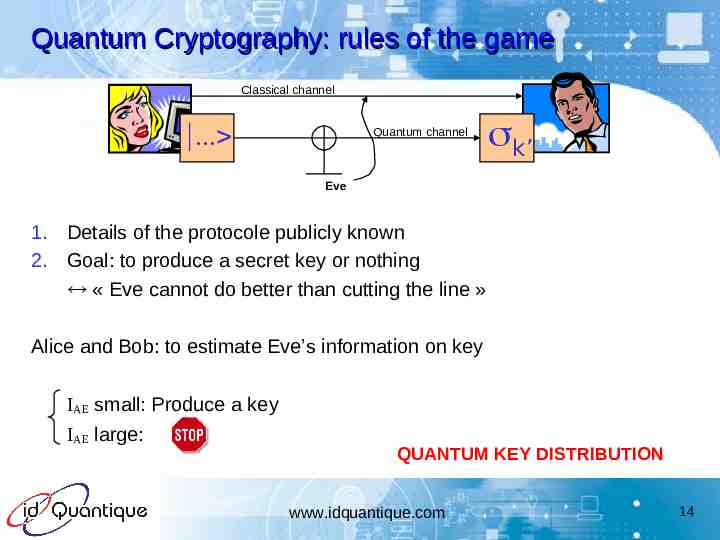
Quantum Cryptography: rules of the game Classical channel Quantum channel k’ Eve 1. Details of the protocole publicly known 2. Goal: to produce a secret key or nothing « Eve cannot do better than cutting the line » Alice and Bob: to estimate Eve’s information on key IAE small: Produce a key IAE large: QUANTUM KEY DISTRIBUTION www.idquantique.com 14
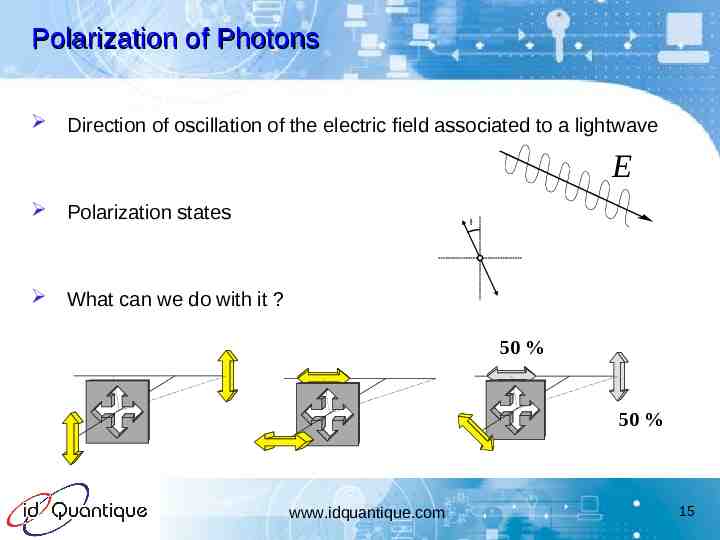
Polarization of Photons Direction of oscillation of the electric field associated to a lightwave Polarization states What can we do with it ? E 50 % 50 % www.idquantique.com 15
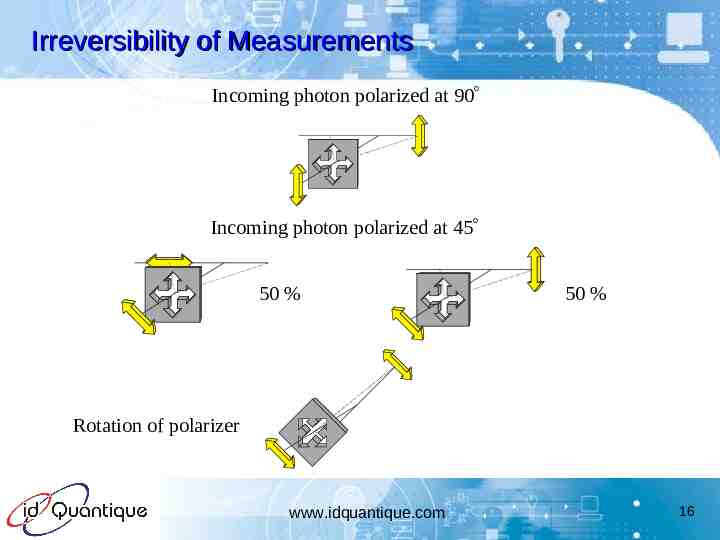
Irreversibility of Measurements Incoming photon polarized at 90 Incoming photon polarized at 45 50 % 50 % Rotation of polarizer www.idquantique.com 16

Quantum communications Transmitting information with a single-photon Liner States Use a quantum property to carry information "0" 0 "1" 1 www.idquantique.com 17
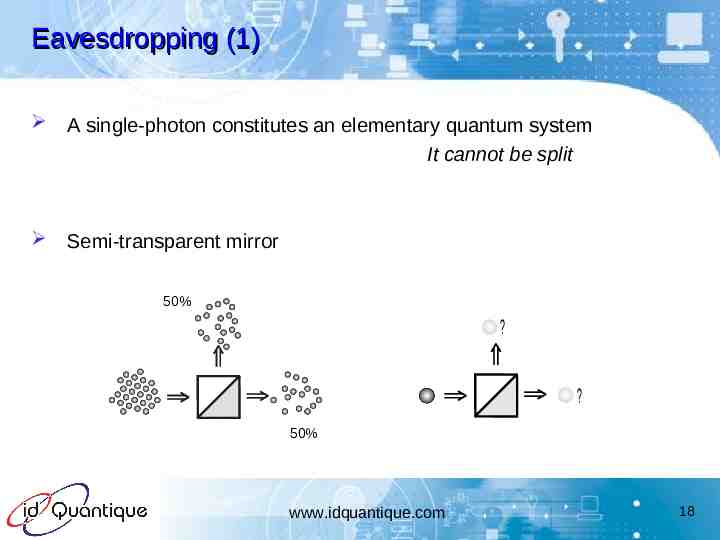
Eavesdropping (1) A single-photon constitutes an elementary quantum system It cannot be split Semi-transparent mirror 50% ? ? 50% www.idquantique.com 18
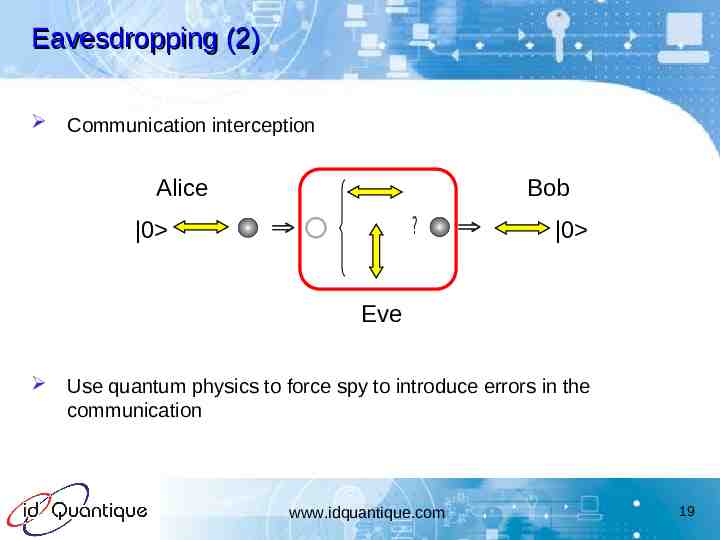
Eavesdropping (2) Communication interception Alice Bob ? 0 0 Eve Use quantum physics to force spy to introduce errors in the communication www.idquantique.com 19
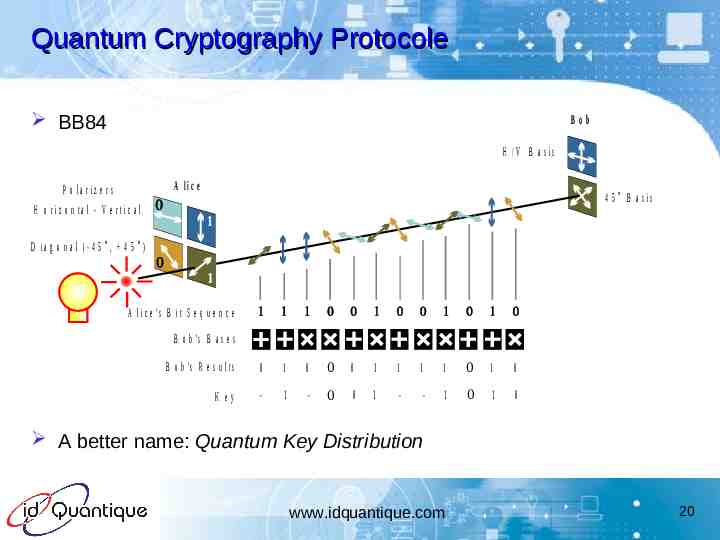
Quantum Cryptography Protocole BB84 B ob H /V B a s is A lic e P o la riz e r s 4 5 B a s is H o r iz o n ta l - V e rtic a l D ia g o n a l (-4 5 , 4 5 ) A l i c e 's B i t S e q u e n c e B o b 's B a s e s B o b 's R e s u l t s 0 1 0 0- 0 1 1 K ey - 1 - 0- 0 1 - 1 - 1 0- 1 0 1 0- 1 0 A better name: Quantum Key Distribution www.idquantique.com 20
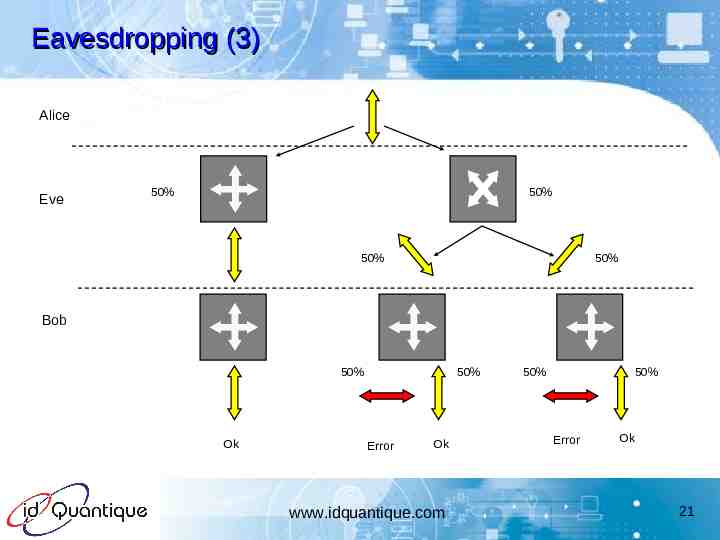
Eavesdropping (3) Alice Eve 50% 50% 50% 50% Bob 50% Ok 50% Error Ok www.idquantique.com 50% 50% Error Ok 21
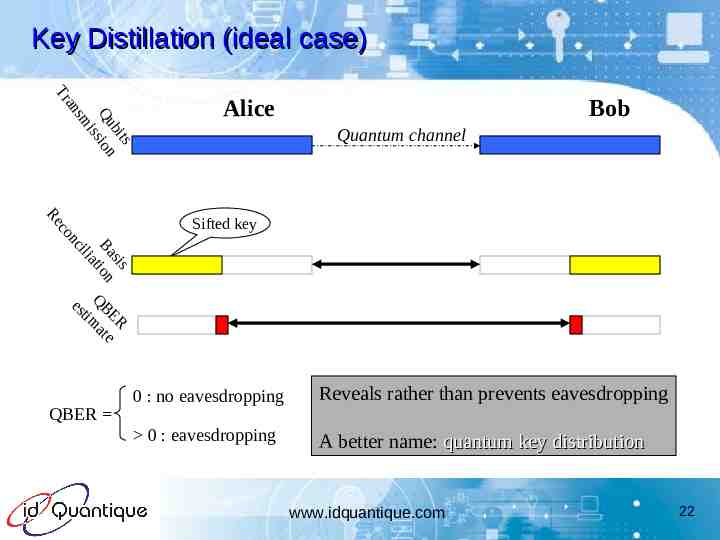
Key Distillation (ideal case) s bit Qu sion is sm an Tr Alice Bob Quantum channel s is Ba ion iat il nc co Re Sifted key es QB tim ER at e QBER 0 : no eavesdropping Reveals rather than prevents eavesdropping 0 : eavesdropping A better name: quantum key distribution www.idquantique.com 22
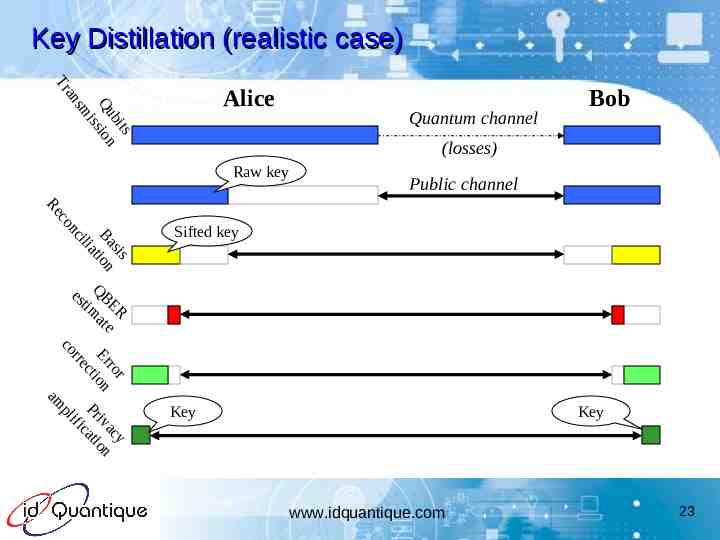
Key Distillation (realistic case) an Tr s bi t Qu sion is sm Alice Quantum channel Bob (losses) Raw key Public channel s is Ba ion iat il nc co Re Sifted key es QB tim ER at e r ro Er on cti re r co y ac i v on Pr cati ifi pl am Key Key www.idquantique.com 23
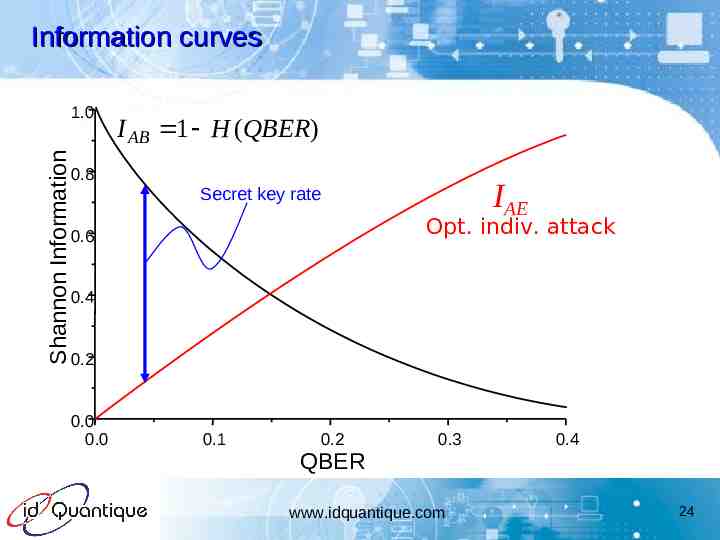
Information curves Shannon Information 1.0 I AB 1 H (QBER) 0.8 IAE Secret key rate Opt. indiv. attack 0.6 0.4 0.2 0.0 0.0 0.1 0.2 QBER 0.3 www.idquantique.com 0.4 24
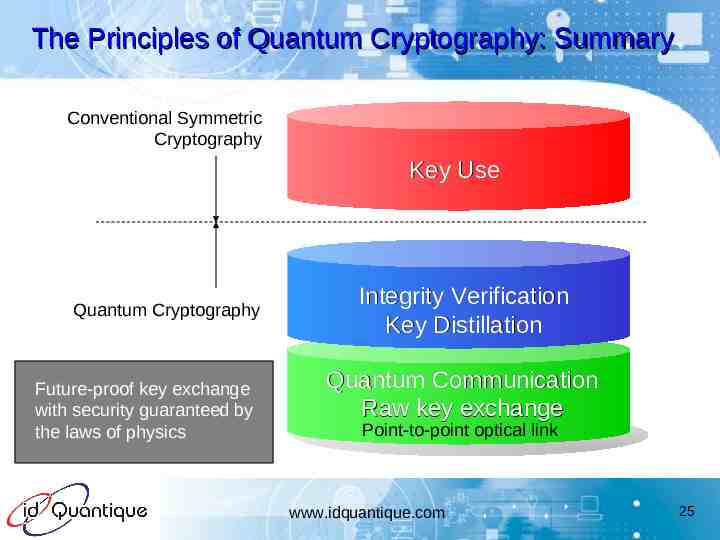
The Principles of Quantum Cryptography: Summary Conventional Symmetric Cryptography Key Use Quantum Cryptography Future-proof key exchange with security guaranteed by the laws of physics Integrity Verification Key Distillation Quantum Communication Raw key exchange Point-to-point optical link www.idquantique.com 25

Outline Quantum physics and information technology The limits of classical cryptography The principles of quantum cryptography Practical systems and applications Future directions www.idquantique.com 26
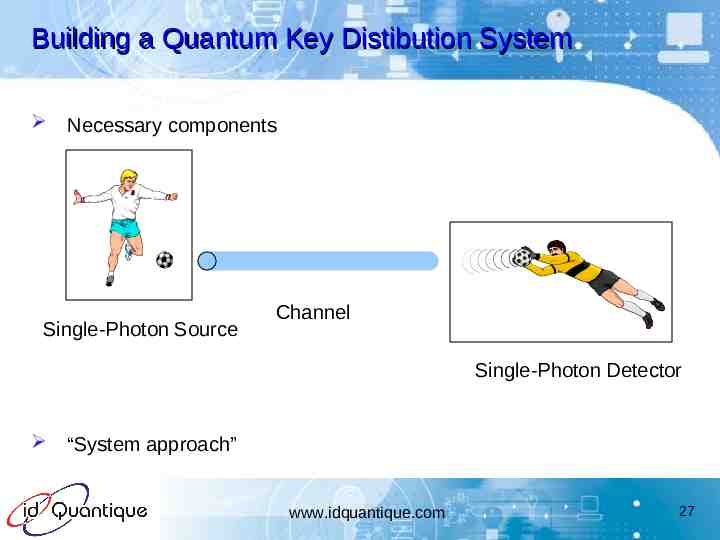
Building a Quantum Key Distibution System Necessary components Single-Photon Source Channel Single-Photon Detector “System approach” www.idquantique.com 27
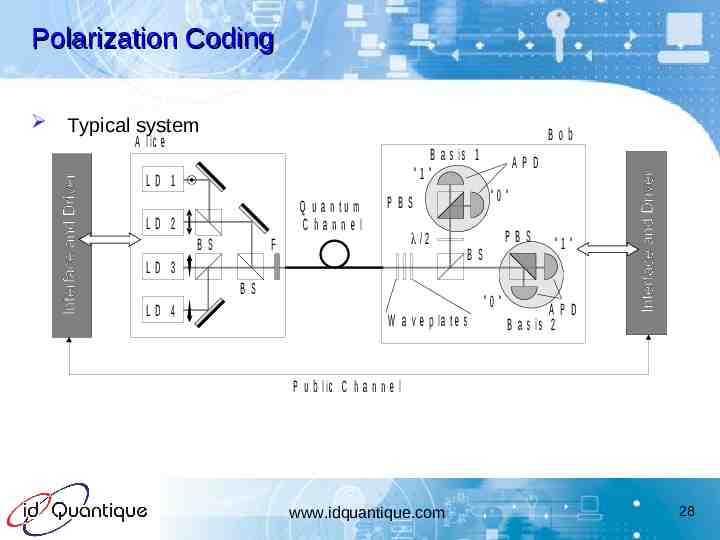
Polarization Coding Typical system Bob A lic e B a s is 1 "1 " LD 1 Q u a n tu m Channel LD 2 BS "0 " PBS /2 F LD 3 PBS BS BS LD 4 APD "0 " W a v e p la t e s "1 " APD B a s is 2 P u b lic C h a n n e l www.idquantique.com 28
Interferences www.idquantique.com 29
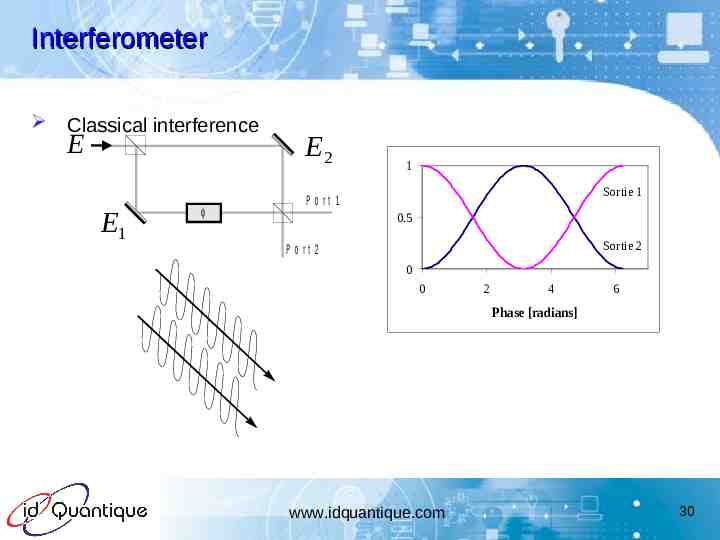
Interferometer Classical interference E E1 E2 1 Sortie 1 P o rt 1 0.5 Sortie 2 P o rt 2 0 0 2 4 6 Phase [radians] www.idquantique.com 30
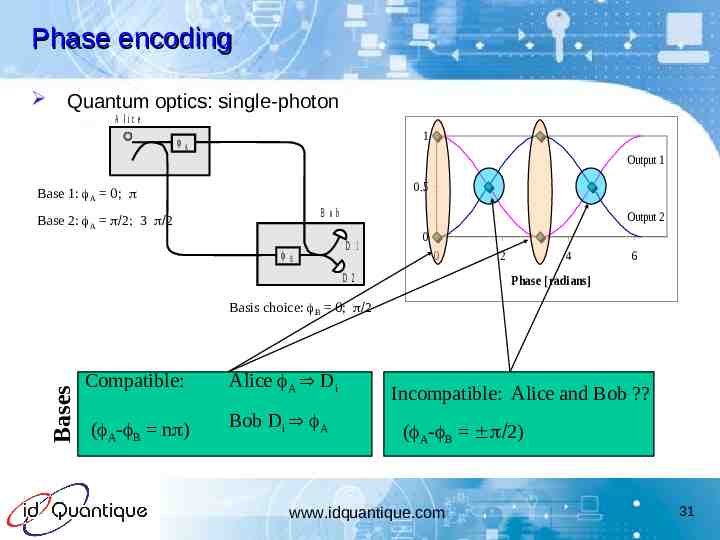
Phase encoding Quantum optics: single-photon A lic e 1 A Output 1 0.5 Base 1: A 0; B ob Base 2: A Output 2 D 1 B 0 0 D 2 2 4 6 Phase [radians] Bases Basis choice: B 0; Compatible: Alice A Di ( A- B n ) Bob Di A Incompatible: Alice and Bob ? ( A- B ) www.idquantique.com 31
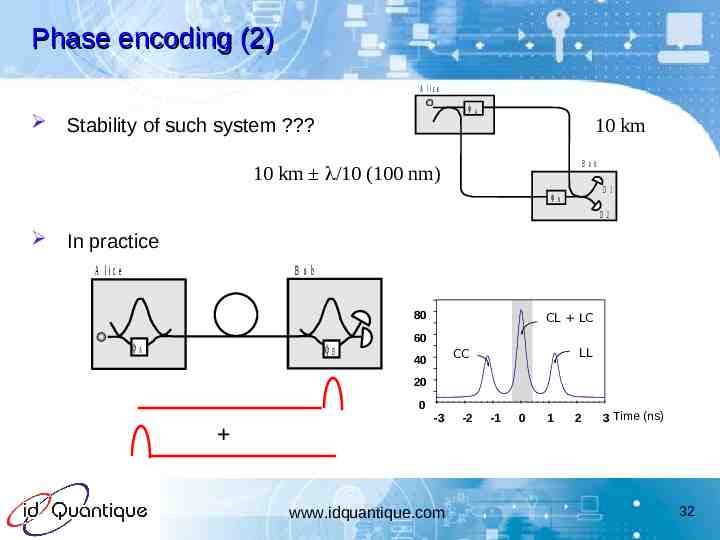
Phase encoding (2) A lic e A Stability of such system ? 10 km B ob 10 km /10 (100 nm) D 1 B D 2 In practice A lic e B ob 80 A B CL LC 60 LL CC 40 20 0 -3 www.idquantique.com -2 -1 0 1 2 3 Time (ns) 32
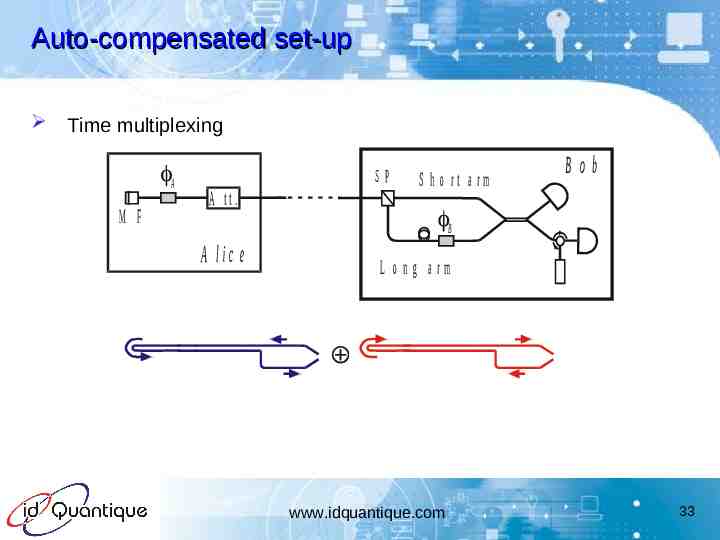
Auto-compensated set-up Time multiplexing A M F SP A tt. S h o rt a rm Bob B A lic e L o n g a rm www.idquantique.com 33
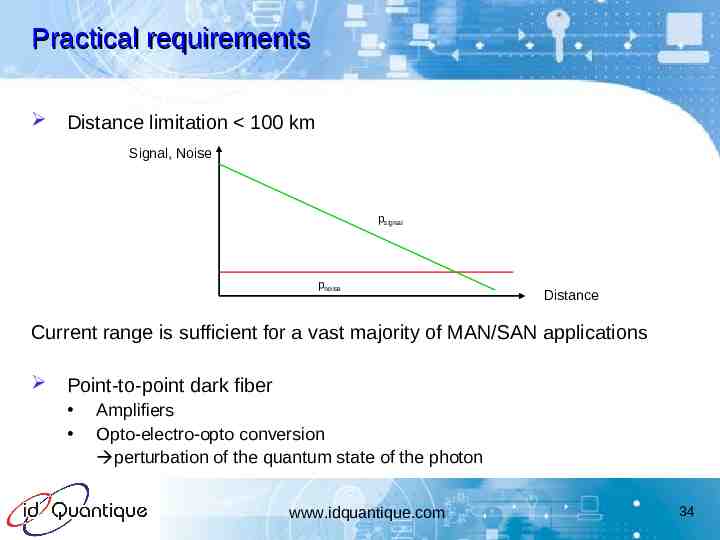
Practical requirements Distance limitation 100 km Signal, Noise psignal pnoise Distance Current range is sufficient for a vast majority of MAN/SAN applications Point-to-point dark fiber Amplifiers Opto-electro-opto conversion perturbation of the quantum state of the photon www.idquantique.com 34
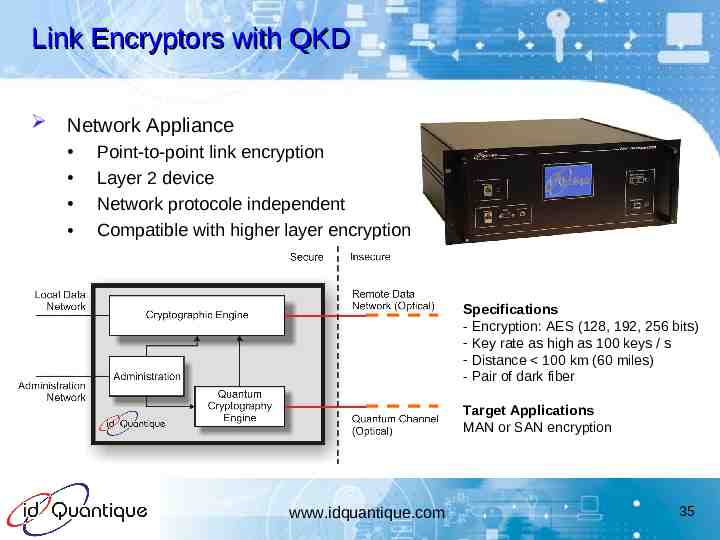
Link Encryptors with QKD Network Appliance Point-to-point link encryption Layer 2 device Network protocole independent Compatible with higher layer encryption Specifications - Encryption: AES (128, 192, 256 bits) - Key rate as high as 100 keys / s - Distance 100 km (60 miles) - Pair of dark fiber Target Applications MAN or SAN encryption www.idquantique.com 35

« Swiss Quantum » Pilot Site www.idquantique.com 36

Outline Quantum physics and information technology The limits of classical cryptography The principles of quantum cryptography Practical systems and applications Future directions www.idquantique.com 37
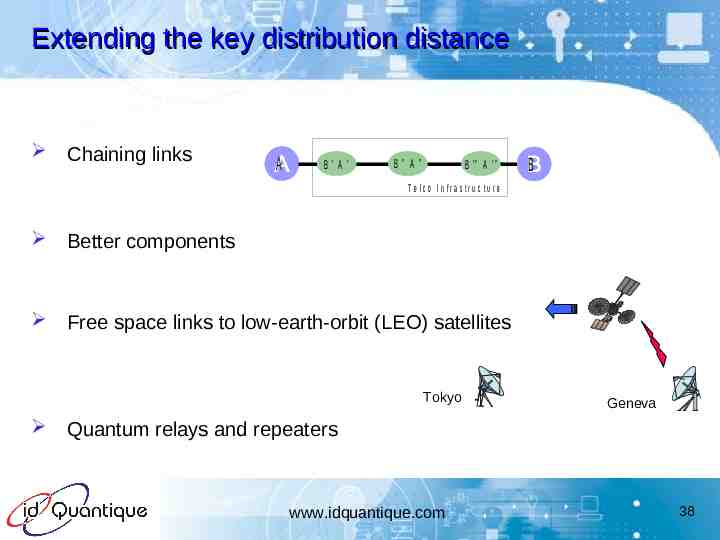
Extending the key distribution distance Chaining links A B'A' B" A" B '" A '" B T e lc o I n fr a s t r u c tu r e Better components Free space links to low-earth-orbit (LEO) satellites Tokyo Geneva Quantum relays and repeaters www.idquantique.com 38
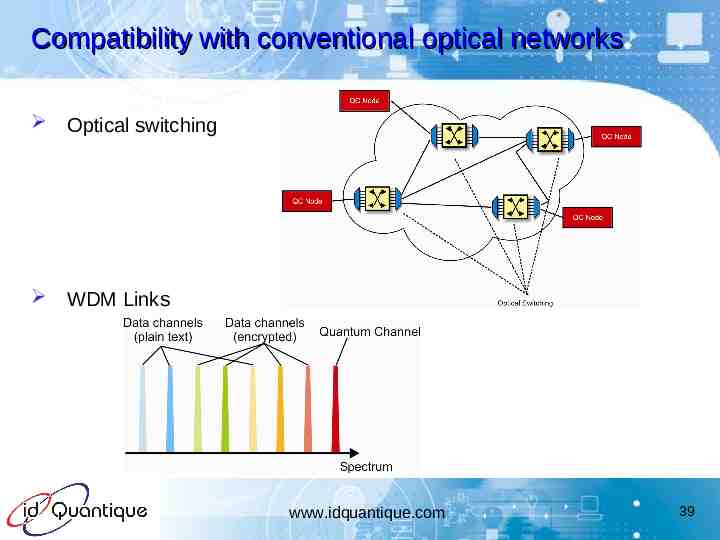
Compatibility with conventional optical networks Optical switching WDM Links www.idquantique.com 39

Thank you very much for your attention id Quantique SA Chemin de la Marbrerie, 3 CH-1227 Carouge Switzerland Ph: Fax: 41 22 301 83 71 41 22 301 83 79 [email protected] www.idquantique.com www.idquantique.com 40

Optical Taps Optical taps are cheap and simple to use « Tapping a fibre-optic cable without being detected, and making sense of the information you collect isn’t trivial but has certainly been done by intelligence agencies for the past seven or eight years. These days, it is within the range of a well funded attacker, probably even a really curious college physics major with access to a fibre optics lab and lots of time on his hands. » John Pescatore, former NSA Analyst The submarine « USS Carter » worth 4.1 bn will be able to tap and eavesdrop undersea cables. www.idquantique.com 41

Key use The key produced by a quantum cryptography system is used with conventional symmetric encryption algorithms One-time pad « unconditional security » Other symmetric algorithms (AES, Tripe-DES, etc.) enhanced security by frequent key change Why is Quantum Cryptography not used to transmit data? 1) Quantum Cryptography cannot guarantee that one particular bit will actually be received. With a random key, it is not a problem. With data, it is. 2) Quantum Cryptography does not prevent eavesdropping, but reveals it a posteriori. Sending a key and verifying its secrecy allows to prevent information leakage. www.idquantique.com 42
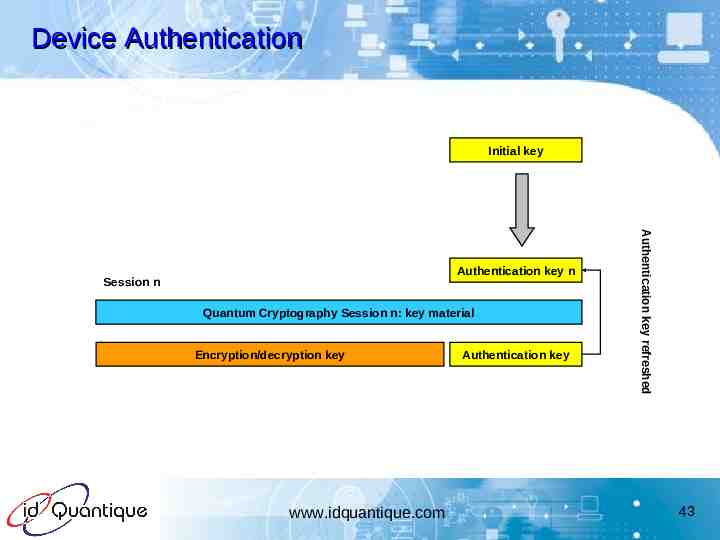
Device Authentication Initial key Quantum Cryptography Session n: key material Encryption/decryption key www.idquantique.com Authentication key Authentication key refreshed Authentication key n Session n 43






