NSF Award 1829698 CyberTraining CIP: Cyberinfrastructure Expertise on
19 Slides7.58 MB
NSF Award 1829698 CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers Hands-on Zeek (Bro) Labs The Cyber Center For Security and Analytics Elias Bou-Harb, Ph.D., CISSP

Elias BouHarb Associate Director Associate Professor Research Grants NSF OAC Core: Small: Devising Data-driven Methodologies by Employing Large-scale Empirical Data to Fingerprint, Attribute, Remediate and Analyze Internet-scale IoT Maliciousness NSF CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers Recent Publications Miranda, C., Kaddoum, G., Bou-Harb, E., Garg, S. and Kaur, K., 2020. A Collaborative Security Framework for Software-Defined Wireless Sensor Networks. IEEE Transactions on Information Forensics and Security. Expertise Operational Cyber Security Cyber Forensics Critical Infrastructure Security Data Science Digital Investigation Internet Measurements Pour, M.S., Mangino, A., Friday, K., Rathbun, M., Bou-Harb, E., Iqbal, F., Samtani, S., Crichigno, J. and Ghani, N., 2019. On Data-driven Curation, Learning, and Analysis for Inferring Evolving Internet-of-Things (IoT) Botnets in the Wild. Computers & Security, p.101707. Kaur, K., Garg, S., Kaddoum, G., Bou-Harb, E. and Choo, K.K.R., 2019. A Big Data-Enabled Consolidated Framework for Energy Efficient Software Defined Data Centers in IoT Setups. IEEE Transactions on Industrial Informatics. Neshenko, N., Bou-Harb, E., Crichigno, J., Kaddoum, G. and Ghani, N., 2019. Demystifying IoT security: an exhaustive survey on IoT vulnerabilities and a first empirical look on internet-scale IoT exploitations. IEEE Communications Surveys & Tutorials, 21(3), pp.2702-2733. Oliveira, D., Ghani, N., Hayat, M., Crichigno, J. and Bou-Harb, E., 2018. SDN testbed for evaluation of large exo-atmospheric EMP attacks. IEEE Communications Magazine, 57(1), pp.88-97.
The Cyber Center For Security and Analytics Intro to Zeek (Bro)

The Cyber Center For Security and Analytics Network Intrusion Detection Systems Software/hardware systems that actively monitor live networks for malicious traffic, policy violations and unidentified anomalies Deployed to protect operational networks without disturbing normal/benign packet traffic flows In contrast to firewalls, NIDS are most often passive, looking for signatures or anomalies, although they can operate as NIPS as well
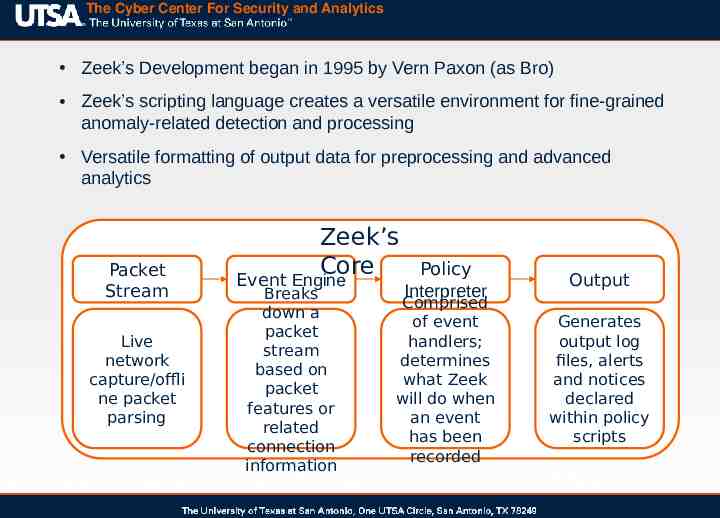
The Cyber Center For Security and Analytics Zeek’s Development began in 1995 by Vern Paxon (as Bro) Zeek’s scripting language creates a versatile environment for fine-grained anomaly-related detection and processing Versatile formatting of output data for preprocessing and advanced analytics Packet Stream Live network capture/offli ne packet parsing Zeek’s Core Event Engine Breaks down a packet stream based on packet features or related connection information Policy Interpreter Comprised of event handlers; determines what Zeek will do when an event has been recorded Output Generates output log files, alerts and notices declared within policy scripts
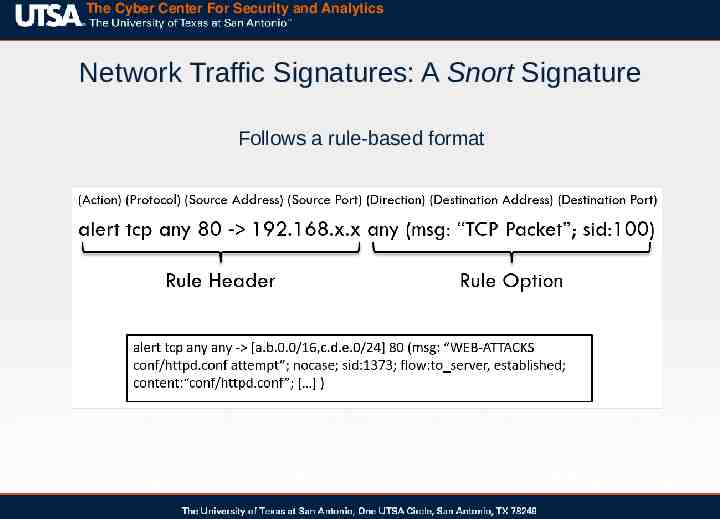
The Cyber Center For Security and Analytics Network Traffic Signatures: A Snort Signature Follows a rule-based format
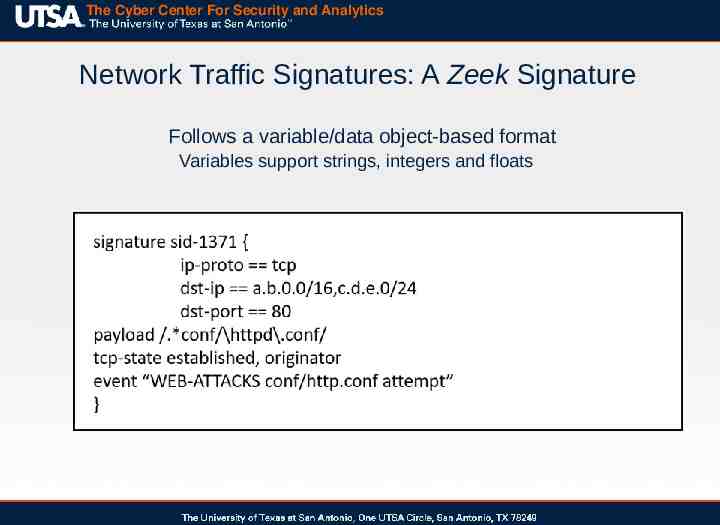
The Cyber Center For Security and Analytics Network Traffic Signatures: A Zeek Signature Follows a variable/data object-based format Variables support strings, integers and floats
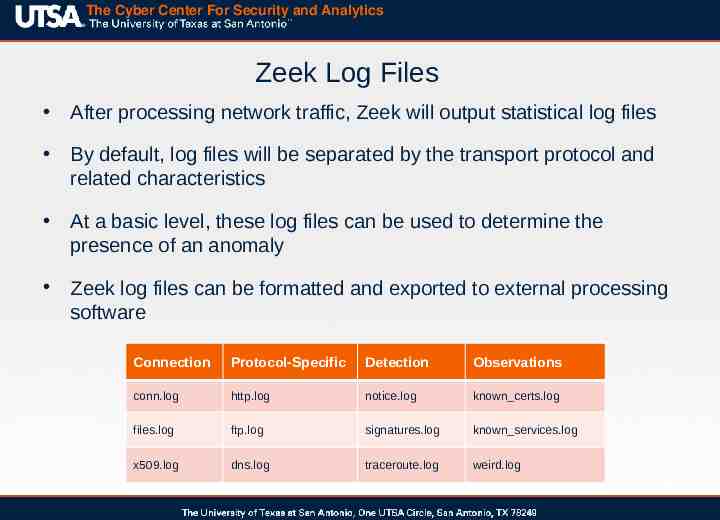
The Cyber Center For Security and Analytics Zeek Log Files After processing network traffic, Zeek will output statistical log files By default, log files will be separated by the transport protocol and related characteristics At a basic level, these log files can be used to determine the presence of an anomaly Zeek log files can be formatted and exported to external processing software Connection Protocol-Specific Detection Observations conn.log http.log notice.log known certs.log files.log ftp.log signatures.log known services.log x509.log dns.log traceroute.log weird.log

The Cyber Center For Security and Analytics Zeek Policy Scripts and Filters The Zeek scripting language is used to develop and implement filters and policies for the event-based engine Scripts can be implemented to permanently update Zeek’s event handling or used as a non-permanent filter Script events include (but are not limited to): – Protocol-specific events – Application-level headers – Unknown/broken connection handling Packet data is accessible within the filters to be used for calculations or to be exported into separate log files
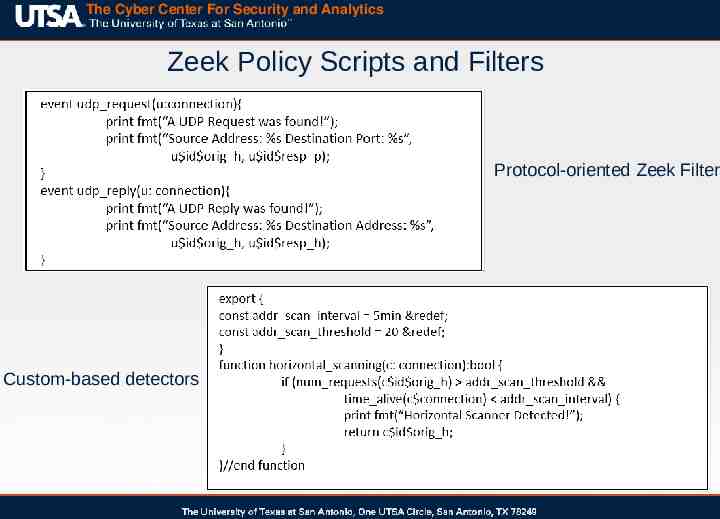
The Cyber Center For Security and Analytics Zeek Policy Scripts and Filters Protocol-oriented Zeek Filter Custom-based detectors
The Cyber Center For Security and Analytics Zeek Inferring IoT-generating Scanning The Insecurity of the IoT Paradigm
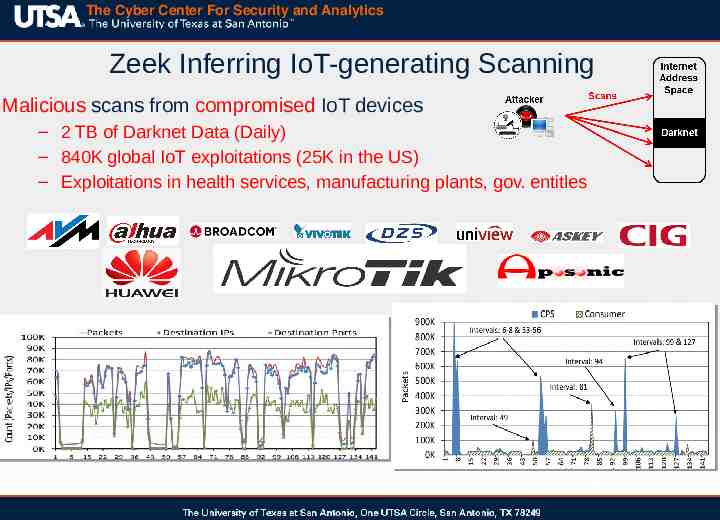
The Cyber Center For Security and Analytics Zeek Inferring IoT-generating Scanning Malicious scans from compromised IoT devices – 2 TB of Darknet Data (Daily) – 840K global IoT exploitations (25K in the US) – Exploitations in health services, manufacturing plants, gov. entitles
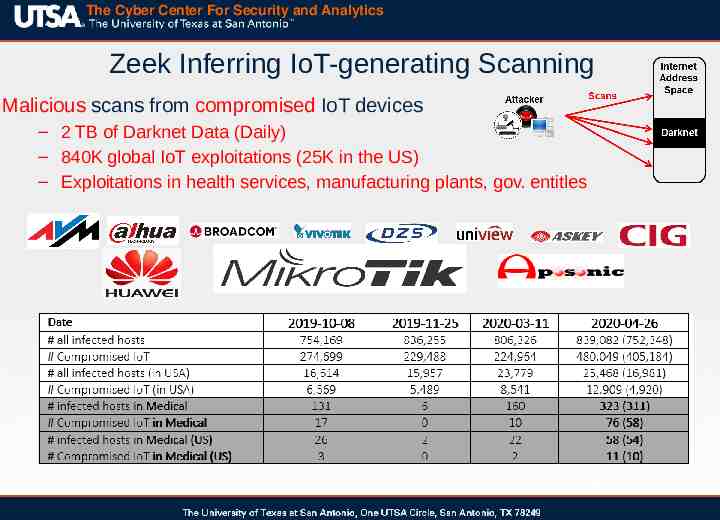
The Cyber Center For Security and Analytics Zeek Inferring IoT-generating Scanning Malicious scans from compromised IoT devices – 2 TB of Darknet Data (Daily) – 840K global IoT exploitations (25K in the US) – Exploitations in health services, manufacturing plants, gov. entitles
The Cyber Center For Security and Analytics Hands-on Zeek (Bro) Labs
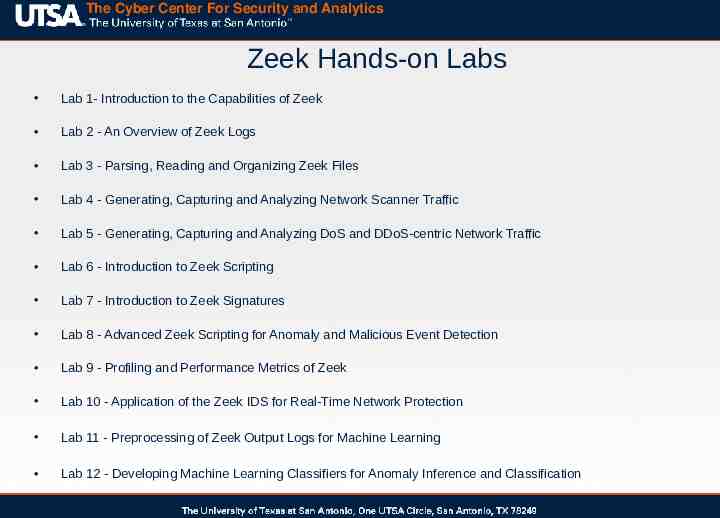
The Cyber Center For Security and Analytics Zeek Hands-on Labs Lab 1- Introduction to the Capabilities of Zeek Lab 2 - An Overview of Zeek Logs Lab 3 - Parsing, Reading and Organizing Zeek Files Lab 4 - Generating, Capturing and Analyzing Network Scanner Traffic Lab 5 - Generating, Capturing and Analyzing DoS and DDoS-centric Network Traffic Lab 6 - Introduction to Zeek Scripting Lab 7 - Introduction to Zeek Signatures Lab 8 - Advanced Zeek Scripting for Anomaly and Malicious Event Detection Lab 9 - Profiling and Performance Metrics of Zeek Lab 10 - Application of the Zeek IDS for Real-Time Network Protection Lab 11 - Preprocessing of Zeek Output Logs for Machine Learning Lab 12 - Developing Machine Learning Classifiers for Anomaly Inference and Classification
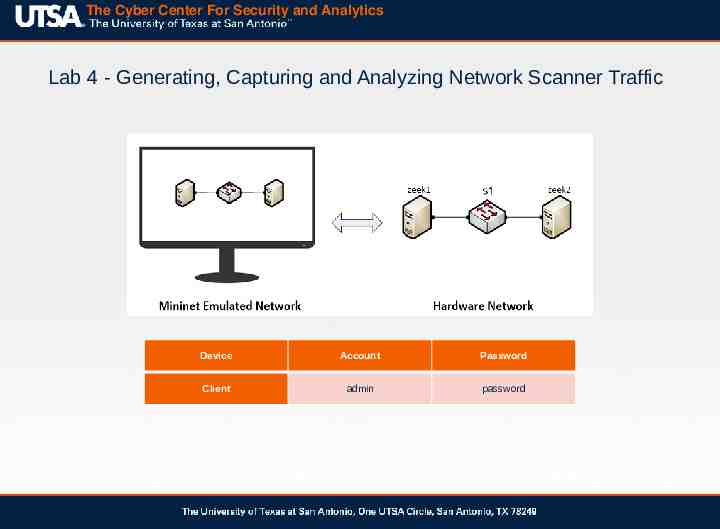
The Cyber Center For Security and Analytics Lab 4 - Generating, Capturing and Analyzing Network Scanner Traffic Device Account Password Client admin password
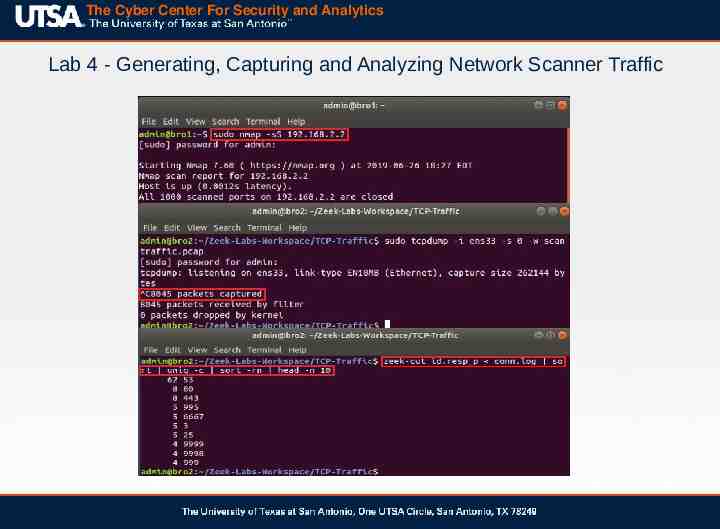
The Cyber Center For Security and Analytics Lab 4 - Generating, Capturing and Analyzing Network Scanner Traffic
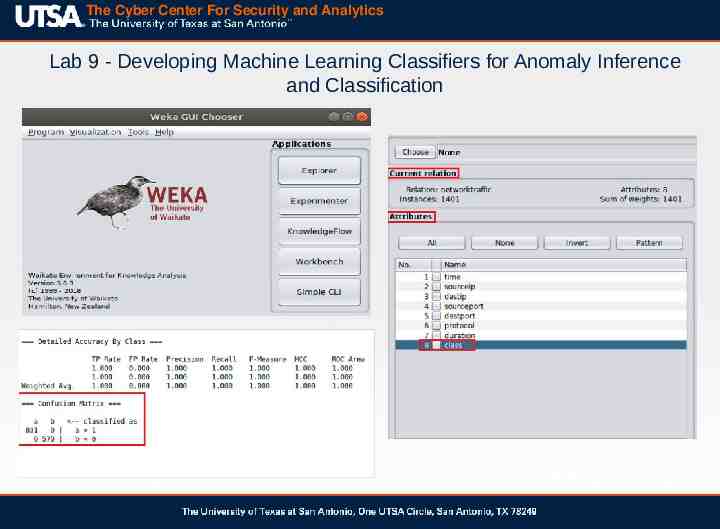
The Cyber Center For Security and Analytics Lab 9 - Developing Machine Learning Classifiers for Anomaly Inference and Classification
NSF Award 1829698 CyberTraining CIP: Cyberinfrastructure Expertise on High-throughput Networks for Big Science Data Transfers Hands-on Zeek (Bro) Labs Enjoy the Labs Thanks for the support! The Cyber Center For Security and Analytics Elias Bou-Harb, Ph.D., CISSP [email protected]






