ITIS 1210 Introduction to Web-Based Information Systems Chapter 51
26 Slides1.86 MB

ITIS 1210 Introduction to Web-Based Information Systems Chapter 51 How Government and Workplace Surveillance Work

Introduction Hackers aren’t the only ones who want to monitor activity Government has reason to monitor activity Law enforcement reasons Anti-terrorism reasons Businesses have reasons as well Worker productivity Hostile workplace Harassment

Introduction Civil libertarians uncomfortable See possibilities for abuse Invasion of individual’s privacy Erosion of personal freedoms Abuse by government

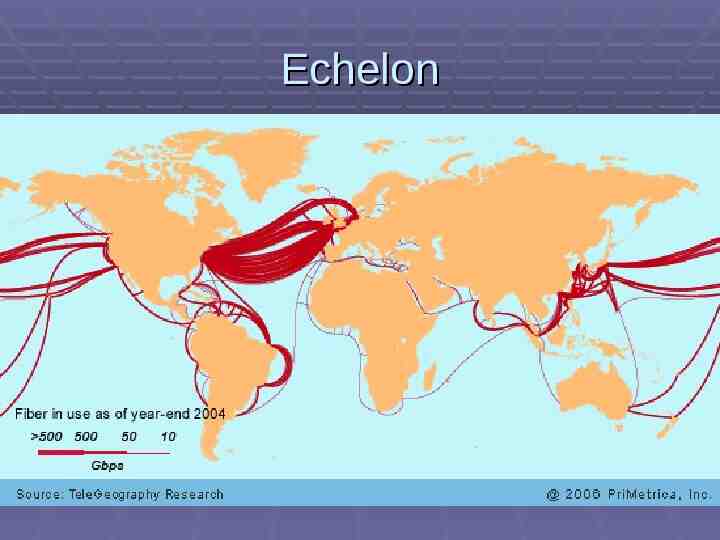
Echelon

Echelon Echelon is believed to be run by a consortium of nations including: National Security Agency (NSA) Ft. Meade, Md United Kingdom (Gov’t Communications HQ) Canada (Comm. Security Establishment) Australia (Defence Signals Directorate) New Zealand (Gov’t Comm. Security Bureau)

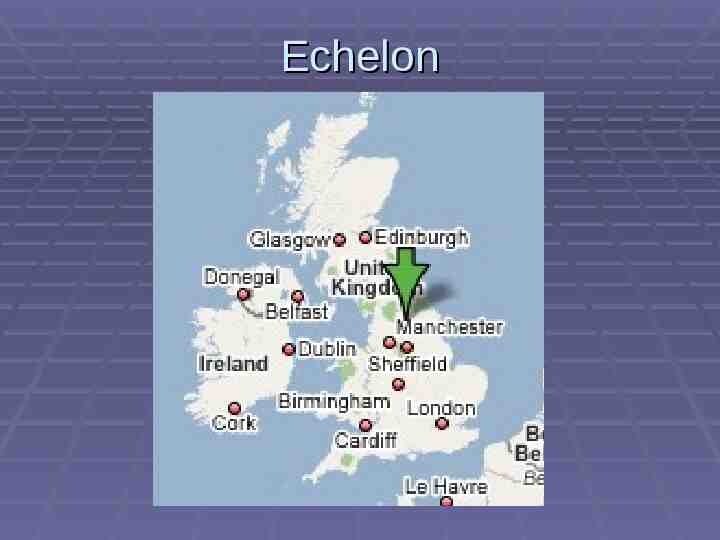
Echelon Believed to be able to monitor a large proportion of the world’s transmitted telephone, data, and fax traffic Sites in Sugar Grove, West Virginia Inbound from east Yakima, Washington Inbound from west Harrogate, Yorkshire
Echelon
Echelon

Echelon Note: There is no definitive proof of the following It is based on the author’s evaluation of some public resources This is a general outline only Listening stations worldwide point satellite dishes towards international communications satellites Used by most of the world
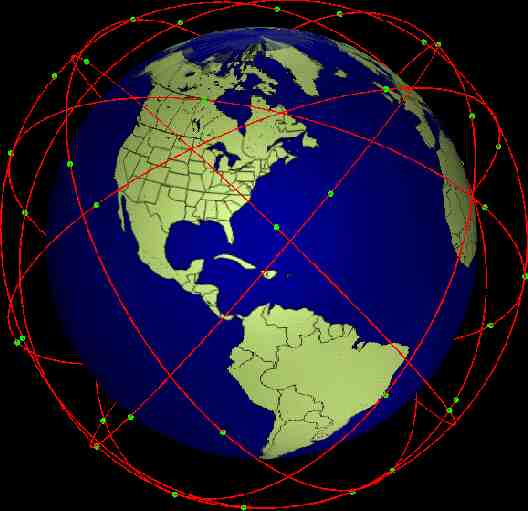
Echelon Intelsat 907 Part of the Intelsat constellation Simultaneously handles tens of thousands of Telephone Fax Emails Other digital communications

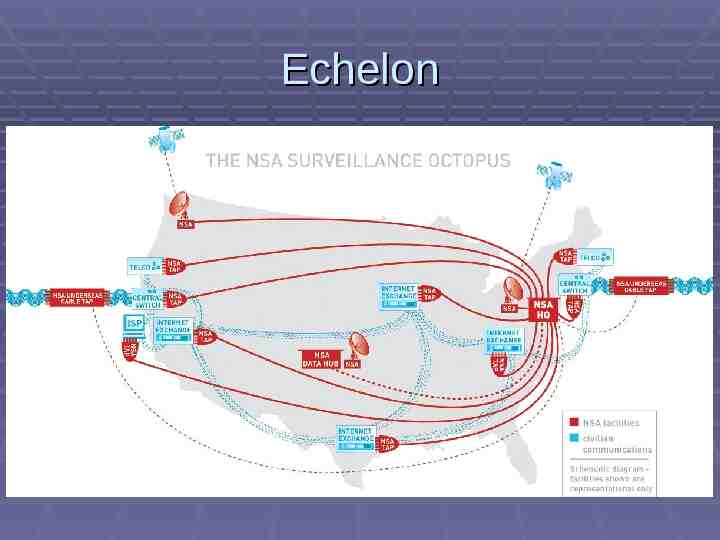
Echelon Satellites not only means of communications Undersea cables Land-based systems Microwave networks Echelon is believed to tap into each of these in different ways

Echelon

Echelon Captured data separated into two streams Encrypted Unencrypted Encrypted communications are sent to supercomputers to try to decrypt them Intercepts sent to dictionary computers at listening centers
Echelon Search for key words and phrases related to Terrorism Nuclear & biological warfare May come from foreign governments Communications with relevant keywords stored in Echelon permanently Includes name of dictionary computer that processed the data – Cowboy for example

Echelon Keyworded communications sent via secure links to regional Echelon headquarters Analyzed by communications and intelligence experts Sent to intelligence agencies both inside and outside the U.S.

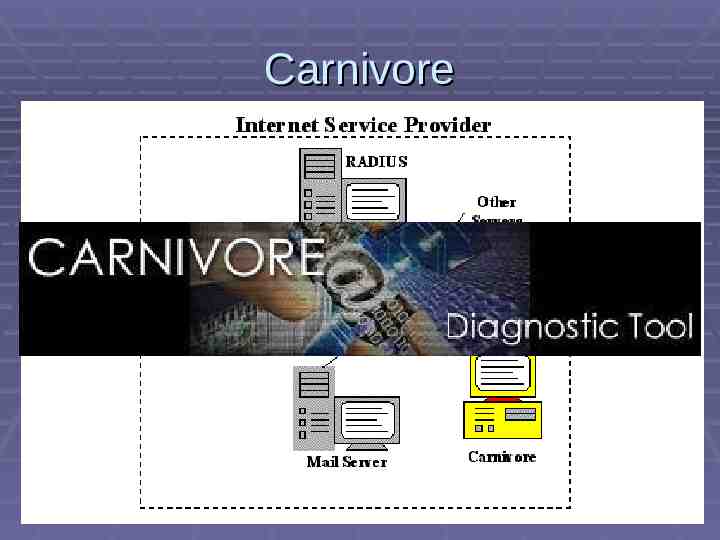
Carnivore

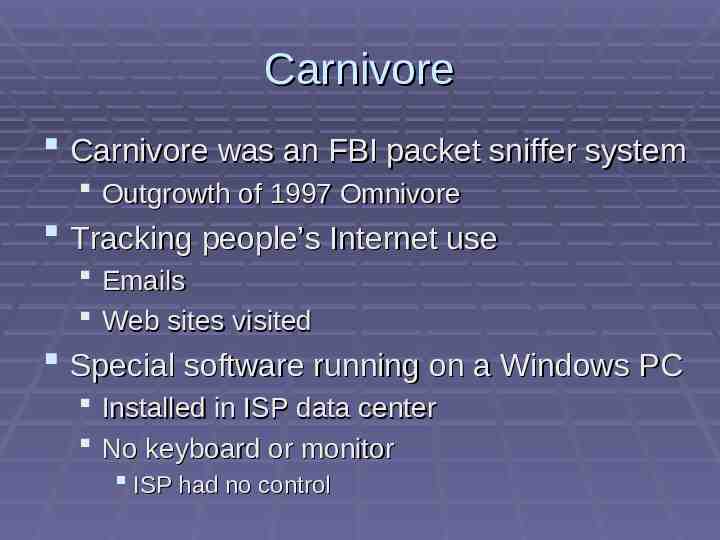
Carnivore Carnivore was an FBI packet sniffer system Outgrowth of 1997 Omnivore Tracking people’s Internet use Emails Web sites visited Special software running on a Windows PC Installed in ISP data center No keyboard or monitor ISP had no control
Carnivore Intercepts large volumes of email 6 GB per hour Scans subject lines and headers of traffic Useful data copied to 2 GB removable hard drives Controlled via secure remote access by FBI Dedicated phone line
Carnivore Installation based on a wiretap warrant Might be very restrictive (email only) Ethernet tap copied packets and forwarded to Carnivore Filters set in local box controlled access Only packets meeting certain criteria were captured Others discarded
Carnivore Removable hard drive sent to FBI periodically Data examined by Packeteer Reassembled individual packets into messages CoolMiner Analysis tool Carnivore, Packeteer, CoolMiner Known as the DragonWare Suite

Carnivore Following negative press, FBI changed designation to DCS1000 Digital Collection System FBI retired Carnivore in 2001 Commercially available software replaced it

Workplace Surveillance Employers use packet sniffers to monitor employee behavior on the Internet Unfiltered sniffers capture every packet Filtered sniffers (like Carnivore) capture only packets with special characteristics Packets saved to a log file Tech support can reconstruct employee’s Internet behavior
Workplace Surveillance Sex! Sex! Sex! No problem with Stuff.com Bicycles.org Alerts for Sex.com Kinky.com Singles.com

Workplace Surveillance Keystroke loggers also used Installed on employees computers without their knowledge Record of every keystroke available for analysis Every document Every email