Ethical Hacking and Network Defense NCTT Winter Workshop January
13 Slides538.00 KB

Ethical Hacking and Network Defense NCTT Winter Workshop January 11, 2006

Contact Information Sam Bowne Email: [email protected] Website: samsclass.info All materials from this talk are already on that website Download them and use them freely Hands-On Ethical Hacking and Network Defense 2
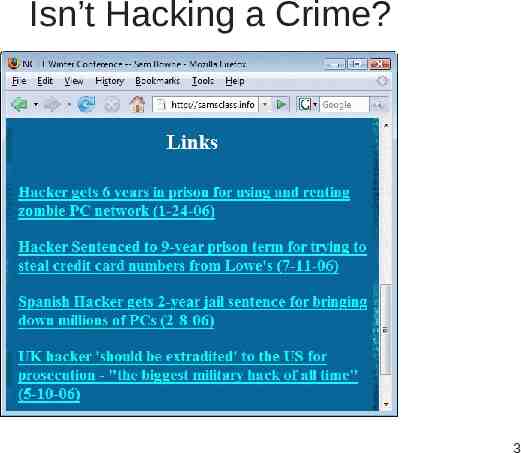
Isn’t Hacking a Crime? 3

Introduction to Ethical Hacking Ethical hackers – Employed by companies to perform penetration tests Penetration test – Legal attempt to break into a company’s network to find its weakest link – Tester only reports findings, does not harm the company 4

The Role of Security and Penetration Testers Hackers – Access computer system or network without authorization – Breaks the law; can go to prison Crackers – Break into systems to steal or destroy data – U.S. Department of Justice calls both hackers Ethical hacker – Performs most of the same activities but with owner’s permission 5

The Role of Security and Penetration Testers (continued) Script kiddies or packet monkeys – Young inexperienced hackers – Copy codes and techniques from knowledgeable hackers Experienced penetration testers use Perl, C, Assembler, or other languages to code exploits 6
Security Credentials CompTIA offers Security certification, a basic familiarity with security concepts and terms 7

OSSTMM Professional Security Tester (OPST) Designated by the Institute for Security and Open Methodologies (ISECOM) Based on the Open Source Security Testing Methodology Manual (OSSTMM) – Written by Peter Herzog 8

Certified Information Systems Security Professional (CISSP) Issued by the International Information Systems Security Certifications Consortium (ISC2) Usually more concerned with policies and procedures than technical details Web site – www.isc2.org 9

Certified Ethical Hacker (CEH) But see Run Away From The CEH Certification – Link at samsclass.info 10

What You Cannot Do Legally Accessing a computer without permission is illegal Other illegal actions – Installing worms or viruses – Denial of Service attacks – Denying users access to network resources Possession of others’ passwords can be a crime – See Password theft Link at samsclass.info 11

Get Out of Jail Free Card When doing a penetration test, have a written contract giving you permission to attack the network Using a contract is just good business Contracts may be useful in court Have an attorney read over your contract before sending or signing it 12

Projects Project 1: Using a Keylogger to record keystrokes (including passwords) Project 2: Using The Metasploit Framework to take over a vulnerable computer remotely Demonstration: Using Ophcrack to crack Windows passwords with Rainbow tables 13






