The End of the Traditional Perimeter: Identity Defined Security
30 Slides3.98 MB

The End of the Traditional Perimeter: Identity Defined Security & the Future of Security From Igniting a Movement to Leaders In Action Sean Cordero CISSP, CISM,CRISC, CISA Senior Executive Director, Office of the CISO

Agenda Identity: Then to Now Shifting the Approach How Does IDS Enable Us? From Here to There Summary

Identity: Then to Now
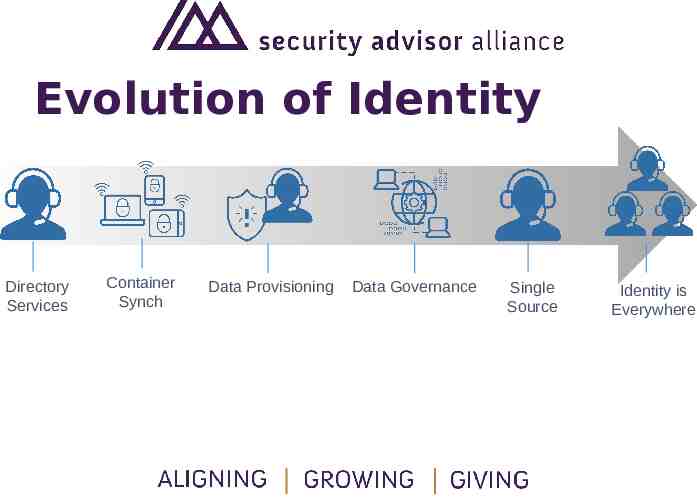
Evolution of Identity Directory Services Container Synch Data Provisioning Data Governance Single Source Identity is Everywhere
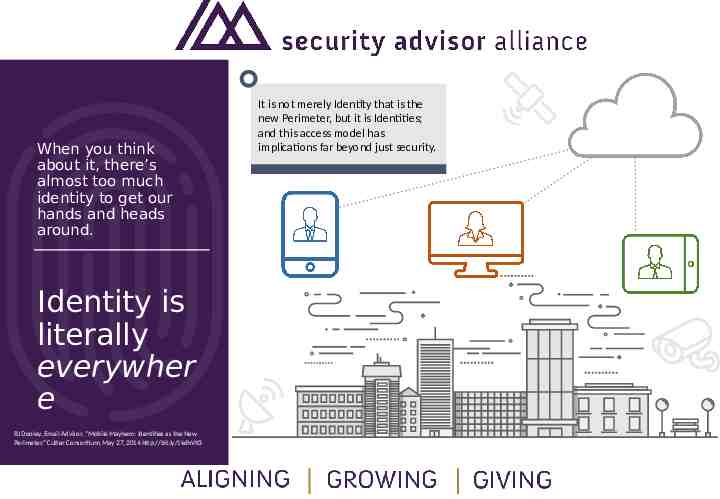
When you think about it, there’s almost too much identity to get our hands and heads around. Identity is literally everywher e BJ Dooley, Email Advisor, “Mobile Mayhem: Identities as the New Perimeter,” Cutter Consortium, May 27, 2014 http://bit.ly/1kdhVK3 It is not merely Identity that is the new Perimeter, but it is Identities; and this access model has implications far beyond just security.

The Good: Why Identity Matters A mature Identity and Access Management program can have significant positive impacts on your organization Streamline authentication experience for employees, customers and partners through centralized access management Generate greater brand awareness and consumer loyalty through better customer experience Improve ability to meet compliance requirements and address audit findings through centralized reporting Gain operational efficiencies through centralized access management, user lifecycle administration and governance
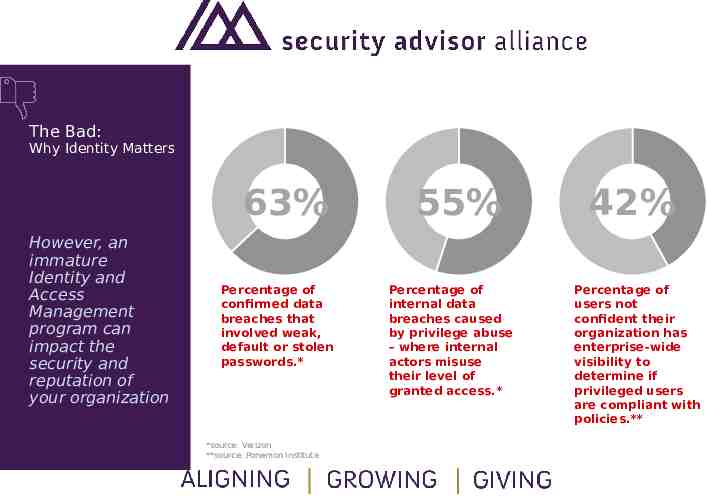
The Bad: Why Identity Matters 63% However, an immature Identity and Access Management program can impact the security and reputation of your organization Percentage of confirmed data breaches that involved weak, default or stolen passwords.* *source: Verizon **source: Ponemon Institute 55% Percentage of internal data breaches caused by privilege abuse – where internal actors misuse their level of granted access.* 42% Percentage of users not confident their organization has enterprise-wide visibility to determine if privileged users are compliant with policies.**
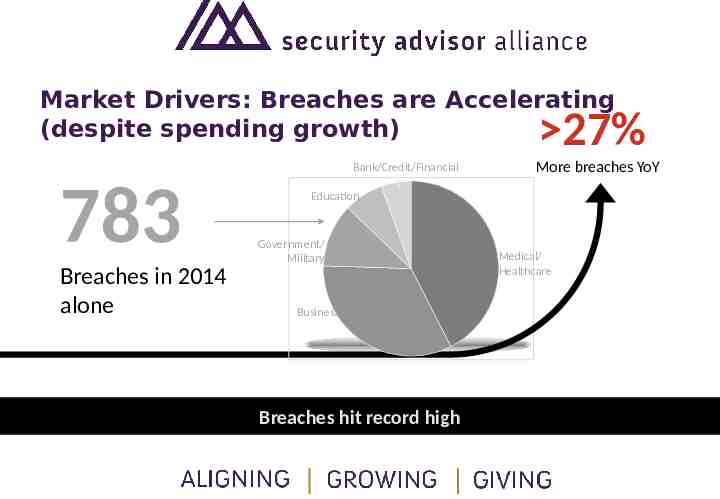
Market Drivers: Breaches are Accelerating (despite spending growth) 27% Bank/Credit/Financial 783 Breaches in 2014 alone More breaches YoY Education Government/ Military Business Breaches hit record high Medical/ Healthcare

Shifting the Approach
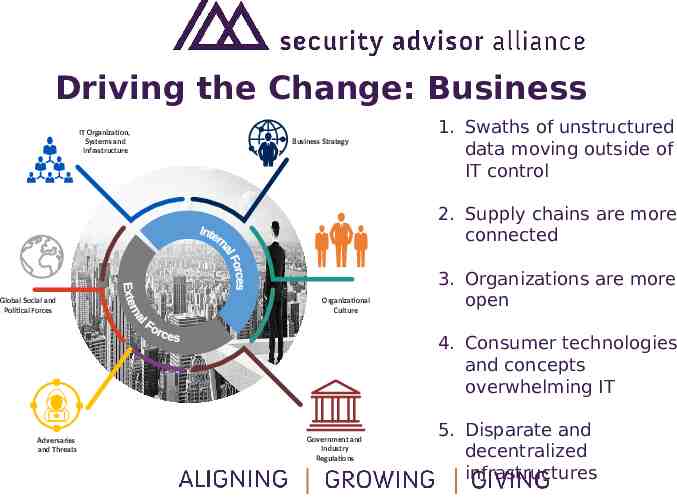
Driving the Change: Business IT Organization, Systems and Infrastructure Business Strategy 1. Swaths of unstructured data moving outside of IT control 2. Supply chains are more connected Global Social and Political Forces Organizational Culture 3. Organizations are more open 4. Consumer technologies and concepts overwhelming IT Adversaries and Threats Government and Industry Regulations 5. Disparate and decentralized infrastructures
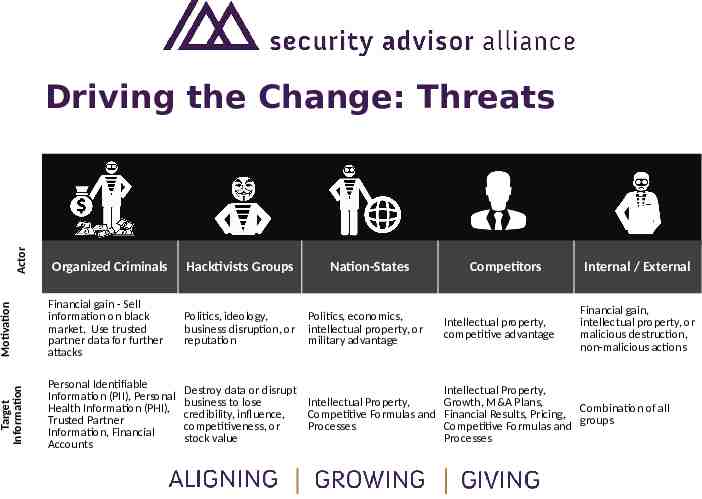
Hacktivists Groups Nation-States Motivation Organized Criminals Financial gain - Sell information on black market. Use trusted partner data for further attacks Politics, ideology, business disruption, or reputation Target Information Actor Driving the Change: Threats Personal Identifiable Information (PII), Personal Health Information (PHI), Trusted Partner Information, Financial Accounts Destroy data or disrupt business to lose Intellectual Property, credibility, influence, Competitive Formulas and competitiveness, or Processes stock value Politics, economics, intellectual property, or military advantage Competitors Intellectual property, competitive advantage Internal / External Financial gain, intellectual property, or malicious destruction, non-malicious actions Intellectual Property, Growth, M&A Plans, Combination of all Financial Results, Pricing, Competitive Formulas and groups Processes
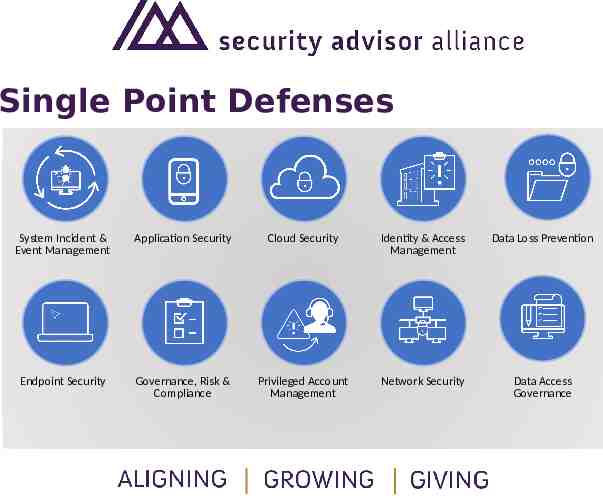
Single Point Defenses System Incident & Event Management Application Security Cloud Security Identity & Access Management Data Loss Prevention Endpoint Security Governance, Risk & Compliance Privileged Account Management Network Security Data Access Governance
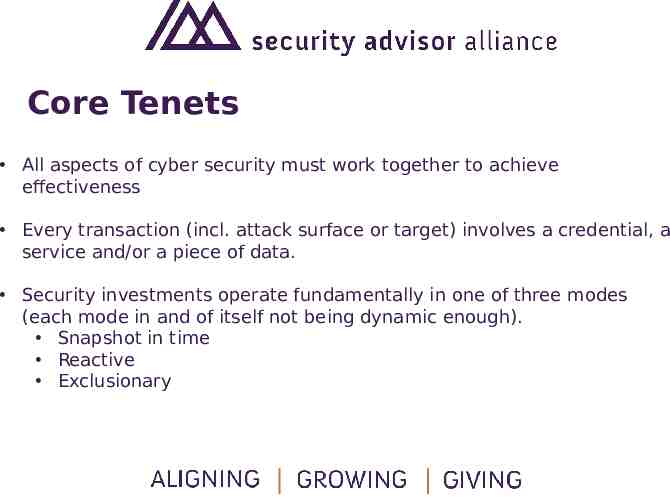
Core Tenets All aspects of cyber security must work together to achieve effectiveness Every transaction (incl. attack surface or target) involves a credential, a service and/or a piece of data. Security investments operate fundamentally in one of three modes (each mode in and of itself not being dynamic enough). Snapshot in time Reactive Exclusionary
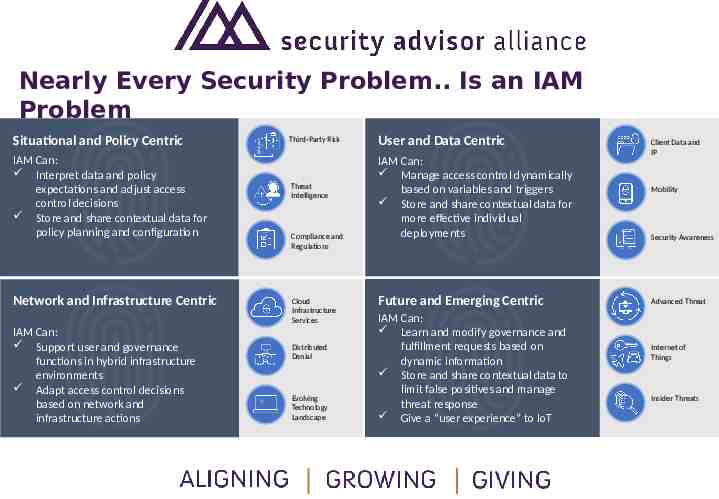
Nearly Every Security Problem. Is an IAM Problem Situational and Policy Centric IAM Can: Interpret data and policy expectations and adjust access control decisions Store and share contextual data for policy planning and configuration Network and Infrastructure Centric IAM Can: Support user and governance functions in hybrid infrastructure environments Adapt access control decisions based on network and infrastructure actions Third-Party Risk Threat Intelligence Compliance and Regulations Cloud Infrastructure Services Distributed Denial Evolving Technology Landscape User and Data Centric IAM Can: Manage access control dynamically based on variables and triggers Store and share contextual data for more effective individual deployments Future and Emerging Centric IAM Can: Learn and modify governance and fulfillment requests based on dynamic information Store and share contextual data to limit false positives and manage threat response Give a “user experience” to IoT Client Data and IP Mobility Security Awareness Advanced Threat Internet of Things Insider Threats
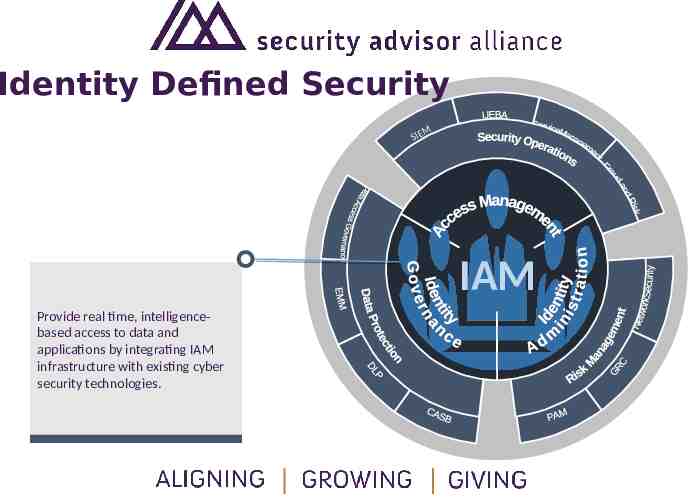
Identity Defined Security M SIE IAM Provide real time, intelligencebased access to data and applications by integrating IAM infrastructure with existing cyber security technologies.

The Future is. Identity Defined Security (IDS) Identity Defined Security is a novel term, but not necessarily a new idea. Identity has been used in the authentication process since inception but weakness in one factor or weakness in lack of data have hindered security for just as long. We need a new way of thinking about the usage of identity and defining security through identity from endto-end provides a clear alternative to denying access by default in our breach a week world of today.

How Does IDS Enable Us?

IDS is Not About Building Bigger Walls Evolution is not about replicating perimeter security techniques Bad guys have become more inventive with taller ladders
IDS is About evolving and adapting more dynamic security models Build trust and confidence that creates value Enable convenient & secure (B2E, B2C and B2B) relationships Extend security beyond firewalls Seamlessly & continuous connectivity- any users, any resource, any device and any service
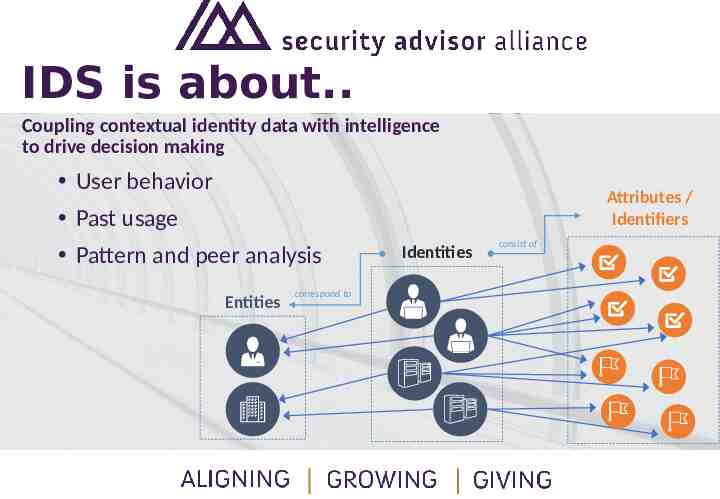
IDS is about. Coupling contextual identity data with intelligence to drive decision making User behavior Past usage Attributes / Identifiers Pattern and peer analysis Entities correspond to Identities consist of

From Here to There
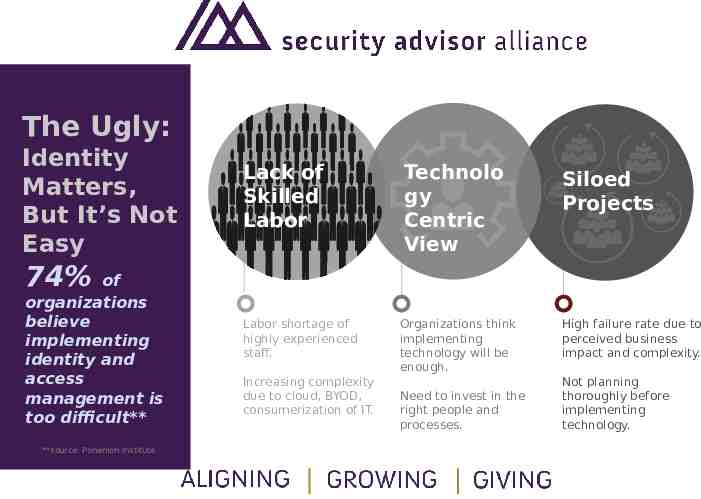
The Ugly: Identity Matters, But It’s Not Easy Lack of Skilled Labor Technolo gy Centric View Siloed Projects 74% of organizations believe implementing identity and access management is too difficult** **source: Ponemon Institute Labor shortage of highly experienced staff. Increasing complexity due to cloud, BYOD, consumerization of IT. Organizations think implementing technology will be enough. Need to invest in the right people and processes. High failure rate due to perceived business impact and complexity. Not planning thoroughly before implementing technology.
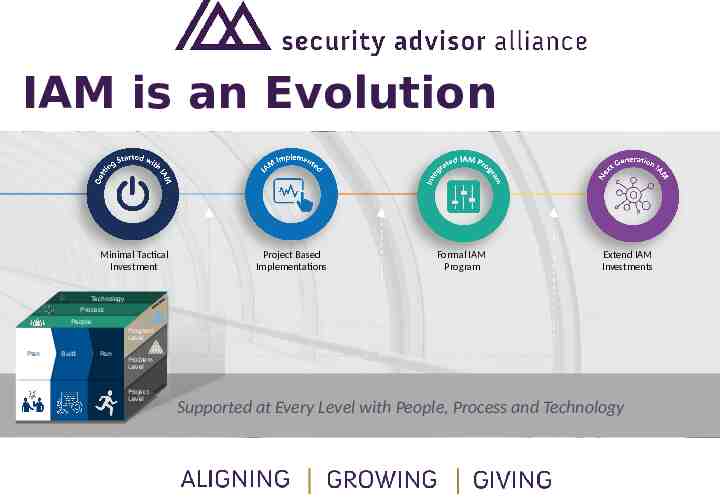
IAM is an Evolution Minimal Tactical Investment Technology Technology Process Process People People Plan Plan Build Build Run Run Project Based Implementations Formal IAM Program Extend IAM Investments Program Program Level Level Problem Problem Level Level Project Project Level Level Supported at Every Level with People, Process and Technology
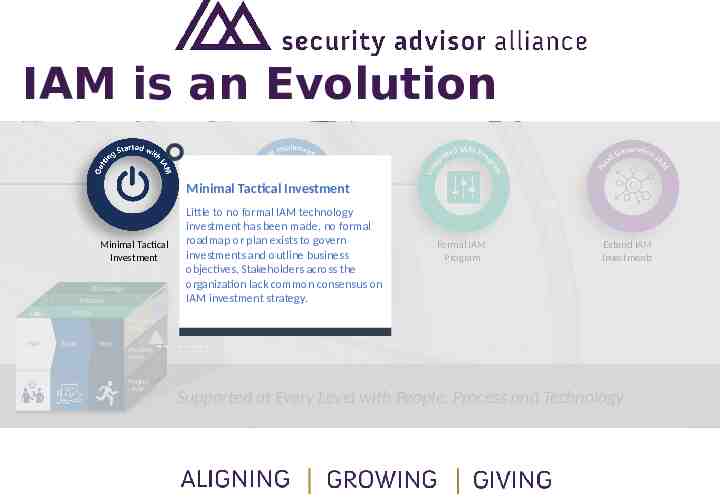
IAM is an Evolution Minimal Tactical Investment Minimal Tactical Investment Technology Technology Process Process People People Plan Plan Build Build Run Run Little to no formal IAM technology investment has been made, no formal roadmap or planProject existsBased to govern investments and outline business Implementations objectives. Stakeholders across the organization lack common consensus on IAM investment strategy. Formal IAM Program Extend IAM Investments Program Program Level Level Problem Problem Level Level Project Project Level Level Supported at Every Level with People, Process and Technology
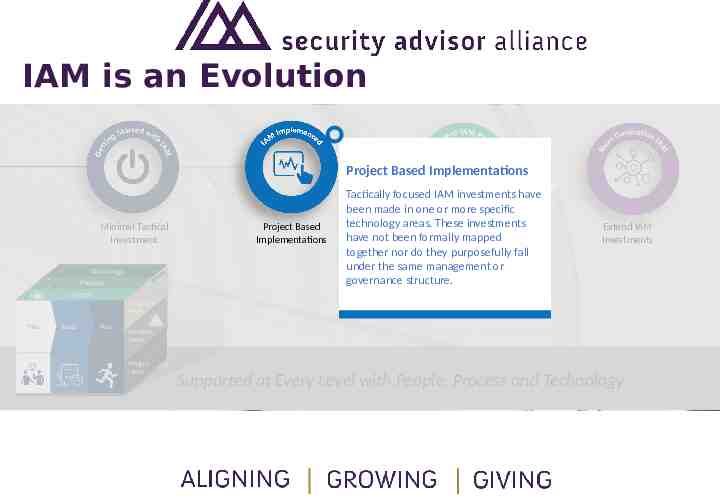
IAM is an Evolution Project Based Implementations Minimal Tactical Investment Technology Technology Process Process People People Plan Plan Build Build Run Run Project Based Implementations Tactically focused IAM investments have been made in one or more specific technology areas. These Formal investments IAM have not been formally mapped Program together nor do they purposefully fall under the same management or governance structure. Extend IAM Investments Program Program Level Level Problem Problem Level Level Project Project Level Level Supported at Every Level with People, Process and Technology
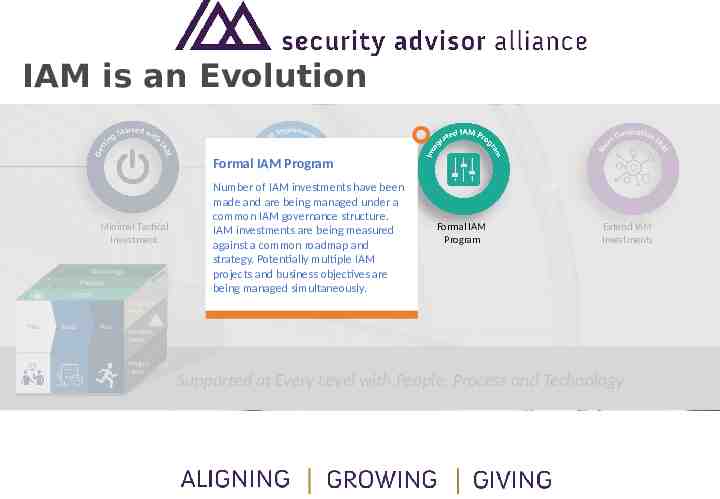
IAM is an Evolution Formal IAM Program Minimal Tactical Investment Technology Technology Process Process People People Plan Plan Build Build Run Run Number of IAM investments have been made and are being managed under a common IAM governance structure. Project Based IAM investments are being measured Implementations against a common roadmap and strategy. Potentially multiple IAM projects and business objectives are being managed simultaneously. Formal IAM Program Extend IAM Investments Program Program Level Level Problem Problem Level Level Project Project Level Level Supported at Every Level with People, Process and Technology
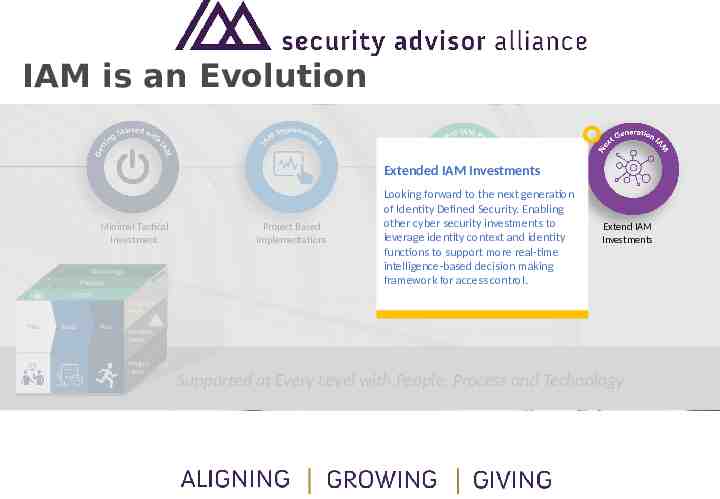
IAM is an Evolution Extended IAM Investments Minimal Tactical Investment Technology Technology Process Process People People Plan Plan Build Build Run Run Project Based Implementations Looking forward to the next generation of Identity Defined Security. Enabling other cyberFormal security IAMinvestments to leverage identity context and identity Program functions to support more real-time intelligence-based decision making framework for access control. Extend IAM Investments Program Program Level Level Problem Problem Level Level Project Project Level Level Supported at Every Level with People, Process and Technology
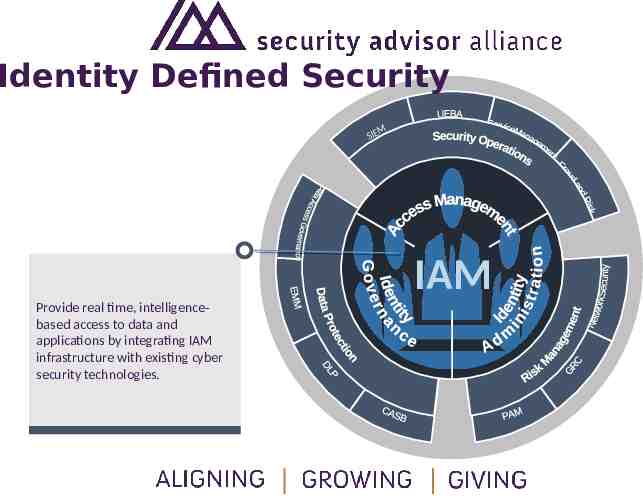
Identity Defined Security M SIE IAM Provide real time, intelligencebased access to data and applications by integrating IAM infrastructure with existing cyber security technologies.
Summary 1. All aspects of cyber security must work together to achieve effectiveness 2. Integration with IAM is no longer optional. It’s a key requiremen 3. IDS is not a silver bullet. It provides for a fighting chance.

Questions Sean Cordero Senior Executive Director, oCISO [email protected] @sean cordero