Denial of Convenience Attack to Smartphones Using a Fake Wi-Fi Access
17 Slides7.83 MB

Denial of Convenience Attack to Smartphones Using a Fake Wi-Fi Access Point Erich Dondyk, Cliff C. Zou University of Central Florida

Background A smartphone can connect to the Internet through only one broadband channel at any particular time Cellular Channel (e.g. 3G) Wi-Fi Channel

Wi-Fi Advantages Users are encouraged to use the Wi-Fi channel when available because: 1) It is usually faster 2) Does not consume the user’s data plan 3) Does not consume the cellular provider’s bandwidth

Wi-Fi Protocol Vulnerability The following two characteristics of the Android and iPhone Wi-Fi protocol allow for exploit: 1) Wi-Fi protocol automatically connects (or asks the user to connect) to an open Wi-Fi APs 2) Wi-Fi protocol never checks if a Wi-Fi access point has a functioning Internet connection or not Could stop Internet access if the AP does not work Users have to know how to disable WiFi to

Motivation Currently, more than one third of all adults in the United States own a smartphone. Many of these users are not technologically savvy to diagnose this type of attack and/or take corrective actions. Mounting a successful Denial-of-Convinience (DoC) attack can be achieved with simple hardware device.

Attack 1: Simple Passive Wi-Fi Access Point Setup a Wi-Fi AP without an internet connection Implementations: Wireless router without an Internet connection - OR Laptop/smartphone configured as a Wi-Fi AP Fake AP Internet
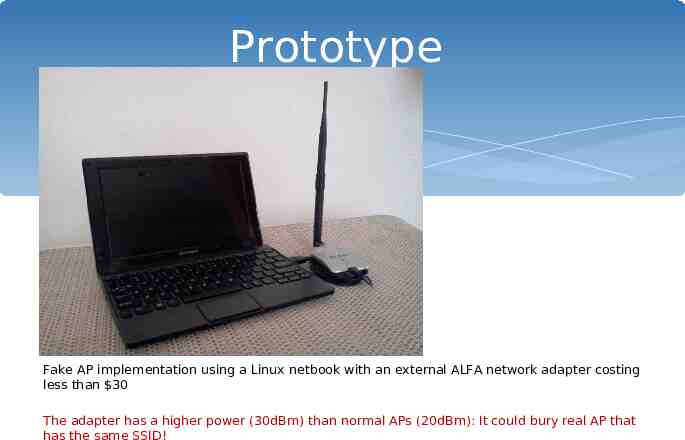
Prototype Fake AP implementation using a Linux netbook with an external ALFA network adapter costing less than 30 The adapter has a higher power (30dBm) than normal APs (20dBm): It could bury real AP that has the same SSID!
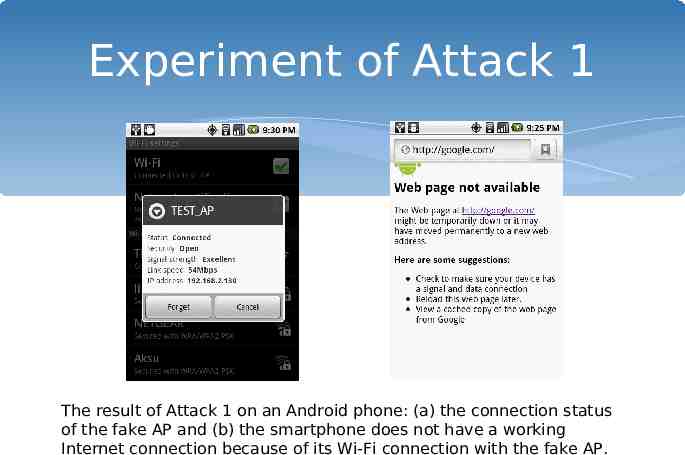
Experiment of Attack 1 The result of Attack 1 on an Android phone: (a) the connection status of the fake AP and (b) the smartphone does not have a working Internet connection because of its Wi-Fi connection with the fake AP.
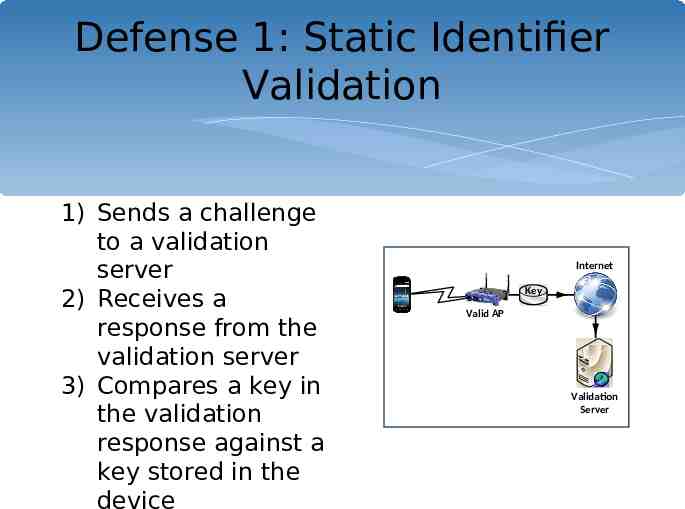
Defense 1: Static Identifier Validation 1) Sends a challenge to a validation server 2) Receives a response from the validation server 3) Compares a key in the validation response against a key stored in the device Internet Key Valid AP Validation Server
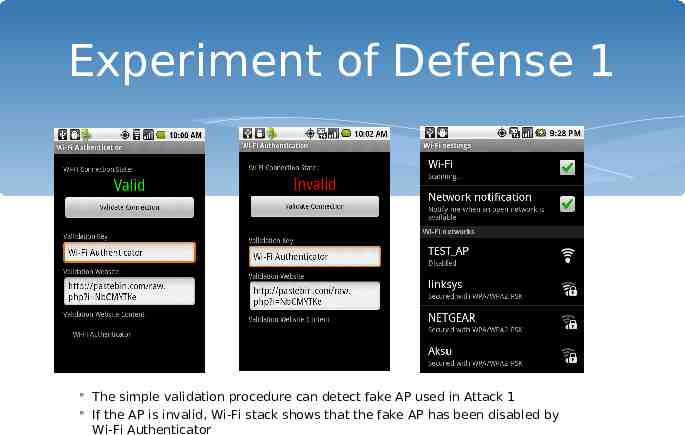
Experiment of Defense 1 The simple validation procedure can detect fake AP used in Attack 1 If the AP is invalid, Wi-Fi stack shows that the fake AP has been disabled by Wi-Fi Authenticator
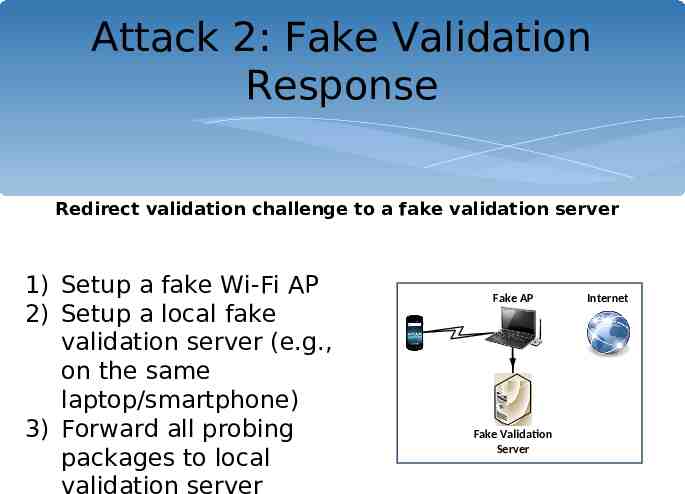
Attack 2: Fake Validation Response Redirect validation challenge to a fake validation server 1) Setup a fake Wi-Fi AP 2) Setup a local fake validation server (e.g., on the same laptop/smartphone) 3) Forward all probing packages to local validation server Fake AP Fake Validation Server Internet
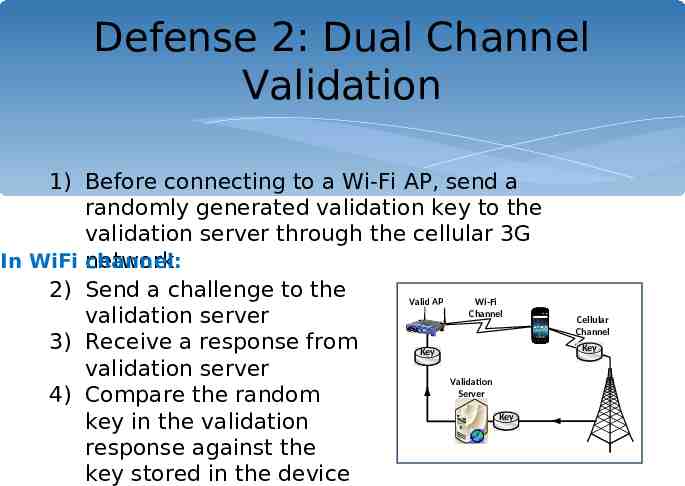
Defense 2: Dual Channel Validation 1) Before connecting to a Wi-Fi AP, send a randomly generated validation key to the validation server through the cellular 3G In WiFi network channel: 2) Send a challenge to the Valid AP Wi-Fi Channel validation server 3) Receive a response from Key validation server Validation Server 4) Compare the random Key key in the validation response against the key stored in the device Cellular Channel Key
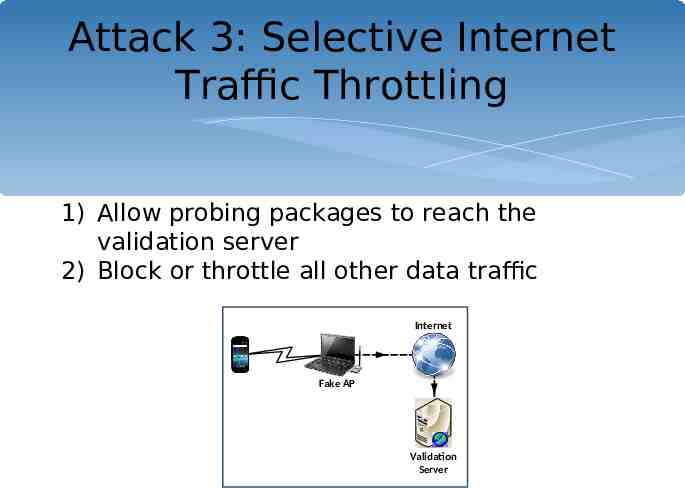
Attack 3: Selective Internet Traffic Throttling 1) Allow probing packages to reach the validation server 2) Block or throttle all other data traffic Internet Fake AP Validation Server

Defense 3: Network Performance Monitoring 1) After connecting to a Wi-Fi AP, measure the performance of the connection 2) If below a predetermine threshold, transition back automatically to the cellular network Internet Network Metrics Analyzer Valid AP

Time used for Authentication

Conclusion DoC attacks are a threat against the two most popular smartphone operating systems, Android and iOS. There are several approaches to implement a DoC attacks. Defenses can be implemented to counteract each type of DoC attack considered.

Questions?