Cybersecurity Threats and Countermeasures Unit 1: Basic security
14 Slides422.28 KB

Cybersecurity Threats and Countermeasures Unit 1: Basic security concepts This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Learning Objectives Upon the conclusion of this module, the student will be able to: – Identify the effect that cyber warfare and cybercrime can have on society and an organization. – Explain the trade-off between key security properties and usability. – Identify the basic concepts of threats, vulnerabilities, attack vectors, and risk. – Identify threat actors, their capabilities/techniques, motivations, risk aversion, and potential attack targets This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Cyber Warfare “Cyber warfare involves the actions by a nationstate or international organization to attack and attempt to damage another nation’s computers or information networks through, for example, computer viruses or denial-of-service attacks” (Source: Rand Corporation. Retrieved from http://www.rand.org/topics/cyber-warfare.htm) This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Cyber Warfare Targets Cyber war targets systems that are critical to maintaining a nation’s way of life, what the Department of Homeland Security identifies as “critical infrastructure” and cause widespread panic and uncertainty. These systems include financial systems, healthcare, energy (electrical grids and power plants), water (including water treatment facilities and dams), communications systems, food and agriculture, and transportation systems, all of which are now connected to the Internet. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Cybercrime Unlike cyber warfare activities, cybercrimes are malicious activities that are often financial in nature. They involve credit card theft (most often largescale), cyber extortion (ransomware attacks), theft of intellectual property (often with the intent to take stolen products to market before the developing company can do so). These crimes are often perpetrated by individuals in economically-disadvantaged countries, or hostile nation states. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Challenges Defending against these threats can be challenging, given many factors: – “Zero day” vulnerabilities – Sophistication of attack tools, requiring little knowledge or skill on the part of the attacker – System complexity – Smaller devices associated with growth of “Internet of Things” – Lack of vulnerability/patch management processes This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Security Trade-Off In addition to the security challenges previously addressed, there is always a trade-off between security and usability. As security services, such as those providing for confidentiality, integrity, and availability, are implemented, system performance and accessibility suffer. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Security Threats A security threat is the potential for an event to occur that would negatively impact security. There are three types of threats: – Natural events (also called “Acts of God”) – Human error (accidents) – Attacks – attacks require malicious intent, so must be caused by people who would circumvent or violate security. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Vulnerabilities Vulnerabilities are weaknesses, such as with insecure (buggy) software code, or misconfigurations (e.g. default or weak passwords). Vulnerabilities provide the opportunity by which threat agents/actors (the entity that would act on the threat) can cause the threat to occur. A threat action is the realization (actualization) of the threat. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Attack Vectors Attack vectors are the methods, or path, that the attacker (threat actor) will use to attack. It is the path that they will take to take advantage of a vulnerability. As an example, attackers will often use social engineering techniques, such as phishing, to attack a network. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Risk Risk is the degree to which an organization is exposed to the threat, and takes into consideration the likelihood and impact of the threat being realized. Risk assessments are processes used by an organization to calculate the amount of risk that a threat presents to an organization, often with the goal of serving to better evaluate proposed security controls for cost effectiveness. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Risk Handling Techniques Risk handling is the process of managing risk so that either the likelihood of the threat occurring is reduced, or the impact is reduced. Risk handling techniques include: – Risk Avoidance – Risk Mitigation – Risk Transference – Risk Acceptance The degree to which an organization “accepts” risk (chooses to do nothing) is based on their risk tolerance. A “risk averse” organization will be more likely to implement security controls, even if they are more costly than the event. This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org

Threat Actors Understanding who the threat actors, or attackers, are and the methods that they will use to attack a target is critical to effective cyber defense. This is categorized, using a military term, as Tactics, Techniques, and Procedures, or TTPs. Tactics refer to the art or skill in achieving the goal. Techniques are the methods that are employed that are often unique to the attacker (for example, specific “signatures” that might identify the writer of malware), and the procedures are the actions that are taken during an attack (port scans, for instance). This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org
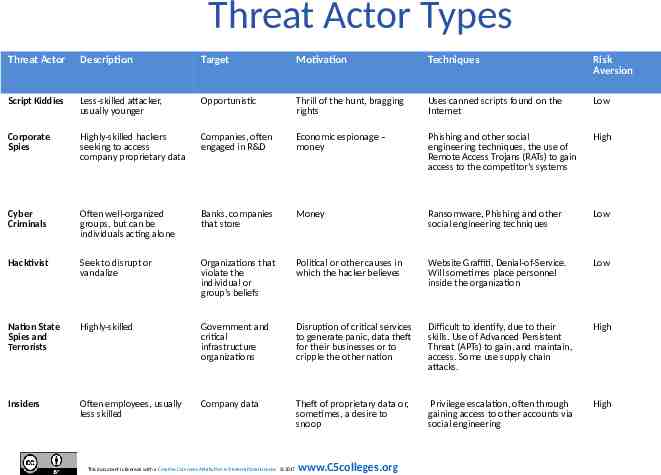
Threat Actor Types Threat Actor Description Target Motivation Techniques Risk Aversion Script Kiddies Less-skilled attacker, usually younger Opportunistic Thrill of the hunt, bragging rights Uses canned scripts found on the Internet Low Corporate Spies Highly-skilled hackers seeking to access company proprietary data Companies, often engaged in R&D Economic espionage – money Phishing and other social engineering techniques, the use of Remote Access Trojans (RATs) to gain access to the competitor’s systems High Cyber Criminals Often well-organized groups, but can be individuals acting alone Banks, companies that store Money Ransomware, Phishing and other social engineering techniques Low Hacktivist Seek to disrupt or vandalize Organizations that violate the individual or group’s beliefs Political or other causes in which the hacker believes Website Graffiti, Denial-of-Service. Will sometimes place personnel inside the organization Low Nation State Spies and Terrorists Highly-skilled Government and critical infrastructure organizations Disruption of critical services to generate panic, data theft for their businesses or to cripple the other nation Difficult to identify, due to their skills. Use of Advanced Persistent Threat (APTs) to gain, and maintain, access. Some use supply chain attacks. High Insiders Often employees, usually less skilled Company data Theft of proprietary data or, sometimes, a desire to snoop Privilege escalation, often through gaining access to other accounts via social engineering High This document is licensed with a Creative Commons Attribution 4.0 International License 2017 www.C5colleges.org






