Cyber Security Do’s & Don’ts – 2019 IMTIAZ MUNSHI, CPA – Co-founder
34 Slides1.55 MB

Cyber Security Do’s & Don’ts - 2019 IMTIAZ MUNSHI, CPA – Co-founder & CEO, Aztec Technologies Vice President, myCPE LLC President, Munshi CPA, PC LINKEDIN - https://www.linkedin.com/in/imtiaz-munshi-57725a Email - [email protected]

LEARNING OBJECTIVES Introduction to Cyber Security Identifying characteristics of best security practices Choosing the appropriate security tools / techniques Identifying Cyber Security do’s and don’t’s

CYBERSECURITY – AN INTRODUCTION Meaning and understanding Concept Importance Financial Consequences Business Perspective – for the market and business owners Approach towards Cybersecurity

FRAMING THE QUESTION AT HAND Security – a complicated necessity Need to be simple Passwords are important Assurance of security – systems approach People make policies work Right tools – Effective Results Verification is necessary to ensure trust

DATA PROTECTION & ITS RELEVANCE For Small Accounting Firms

CPA’s AS TARGETS FOR ATTACKS CPA’s have Confidential and Sensitive client Information. Lack of knowledge regarding good cybersecurity practices Weak Passwords Lack of proper IT controls; outdated hardware

DATA PROTECTION – WHY? A Healthy Business Practice Protecting the Firm’s Reputation Assistance in Risk Management Industry Requirements Regulatory Essentials Complying with Patriot Act / GDPR / AICPA’s GAPP Safeguards Intellectual Property

TECHNOLOGY FOR SMALL ACCOUNTING FIRMS Personal Computer Centric Approach Operations Based on - Windows and MS-Office Email and Data Servers Networking Infrastructure Remote Access Public Cloud Website and Private Client Portal Data Backups

Polling Question 1 Why CPA’s are easy target for Hackers ? Confidential and sensitive data of Clients. Lack of Knowledge and Weak Passwords Lack of Proper IT Security Measures. All of the above.

DATA LOCATION Storage Obvious locations – Servers, Backup Storage, PCs Not-Obvious: Email, Smartphone, Cloud, Printer etc. While Communicating E-mails Uploads/Downloads LAN & Wi-Fi Transmission Online Meetings

DATA BREACHES Unintentional – Human errors Transmitting to the wrong email-address Poor passwords Device mal-function, or lost/stolen devices Intentional Internal (rogue employees) External Malware attack Direct external breach – Less chances as not attractive targets

CONSEQUENCES OF DATA Cost to client Identity theft, IPBREACH leakage Compromised bio metrics Financial damage -1 Cost to business Confidential details leaked Revenue loss Damage to trust and reputation of brand

CONSEQUENCES OF DATA What would follow BREACH - 2 Ransom Demand Financial costs of data recovery, and notifications to protect interest of the clients Litigation Fines and Penalties

AN ENTERPRISE APPROACH TO CYBERSECURITY KEY FACETS Prevention Detection Remedy Reporting

HOW TO MITIGATE RISK? Prioritizing security when setting up systems Framework of tech policies and procedures Assuring physical security of data –staff, maintenance personnel, vendors, ex-employees Implementing hardware and software solutions – organizational buy-in Cyber Insurance
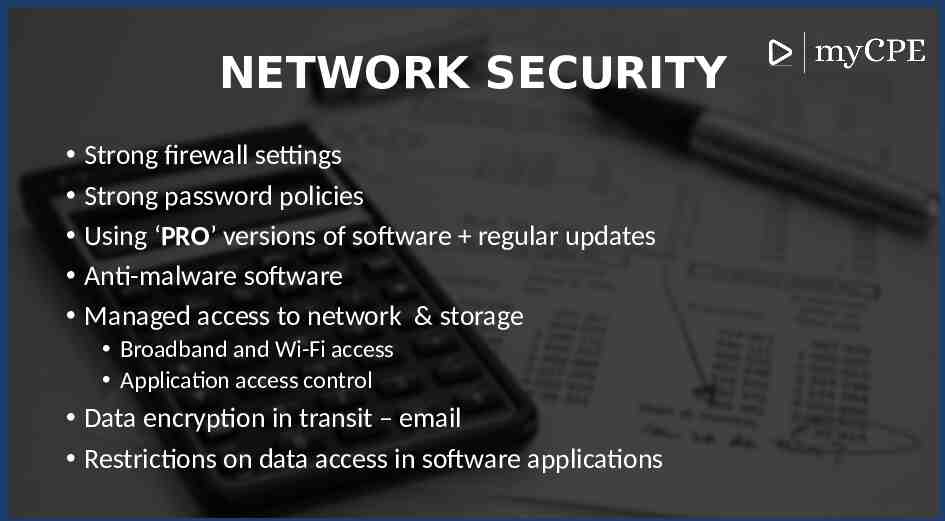
NETWORK SECURITY Strong firewall settings Strong password policies Using ‘PRO’ versions of software regular updates Anti-malware software Managed access to network & storage Broadband and Wi-Fi access Application access control Data encryption in transit – email Restrictions on data access in software applications

POLLING QUESTION 2 How Data is breached ? Wrong Email Address Poor Passwords Malware Attacks All of the above
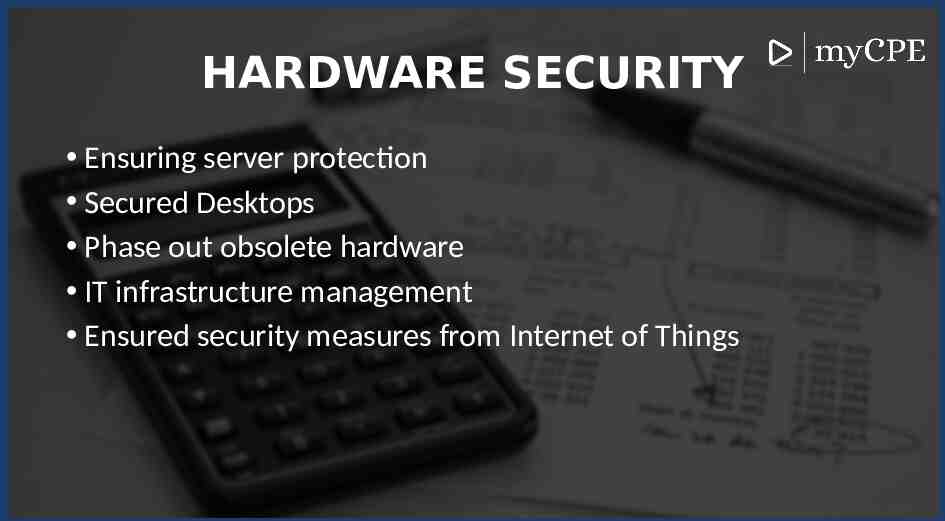
HARDWARE SECURITY Ensuring server protection Secured Desktops Phase out obsolete hardware IT infrastructure management Ensured security measures from Internet of Things

SECURITY PERSPECTIVE OF MOBILE DEVICES Mobile Devices - Smartphones, tablets, laptops, USB drives Setting up Right IT infrastructure - Company owned or BYOD Data stored in Mobile Devices (e.g. email) Mobile device management systems Rights policies and effective enforcement

REMOTE ACCESS AND CYBERSECURITY Desktop devices at homes and offices Hosted virtual desktops No DIY fixes No Starbucks Beware home Wi-Fi

CLOUD TECHNOLOGY Utilizing the cloud technology Public Private Hybrid Key points while using cloud technology Encrypt sensitive files stored in cloud Strict company policies Considerations for the Patriot Act Section 125 / European GDPR

EMAIL SECURITY Email Security Facts Security is assured only before the email is sent, beyond that it is uncertain Highly vulnerability to human errors Need for encrypting message body and attachments Modest adoption of encryption on account of complexity 38% who do encrypt use manual encryption Study: 30% of business email needs encryption Email Security Recommendations Must not interfere with workflow Must maintain file format of encrypted attachments

CYBERSECURITY STARTS WITH PASSWORD SECURITY

PASSWORD STRATEGIES Multiple Authentication Something you know – Password Something you possess – A token or a specific Smart Card Something you are – Biometrics such as thumb prints, Retina Eye verification An identification Password Screen Image Alternative authentication methods No Password Required Device access restricted within premises or Geo-Location Company policy for passwords and passphrases Password Management Tools Randomly generated passwords Add layer of authentication – Dual or multi-level security for higher sensitive data

POLLING QUESTION 3 Which Password Strategy is best ? No Multiple Authentication Easy to remember passwords Biometrics

PRACTICAL TIPS FOR SMALL FIRMS QuickBooks data file transfers – “Qbox” is one solution Recover lost QuickBooks admin password https://passwordreset.quickbooks.com/app/qbdt/passwordreset Password Managers – LastPass; Dashlane Remote access software – Logmein; PCAnywhere; GoToMyPC Remote desktop connection – set up a dedicated IP address Sample Staff Technology Policy – email [email protected] Starbucks – use your phone hotspot instead of free Starbucks WiFi Email encryption - docNCRYPT

CYBER SECURITY - MUST DOs

CYBERSECURITY FOR SMALL FIRMS THE MUST DOs Educate yourself and your staff about Cybersecurity Company Tech Policy signed by all staff members Use strong logins and passwords Multiple authentication where possible Change passwords regularly Encrypt sensitive information Disk drives and folders Individual files Email Protect all devices against malware (even admin computers) Update your systems and software regularly Hire an expert Backup data daily; archive 4 weekly backups

CYBER SECURITY DON’TS
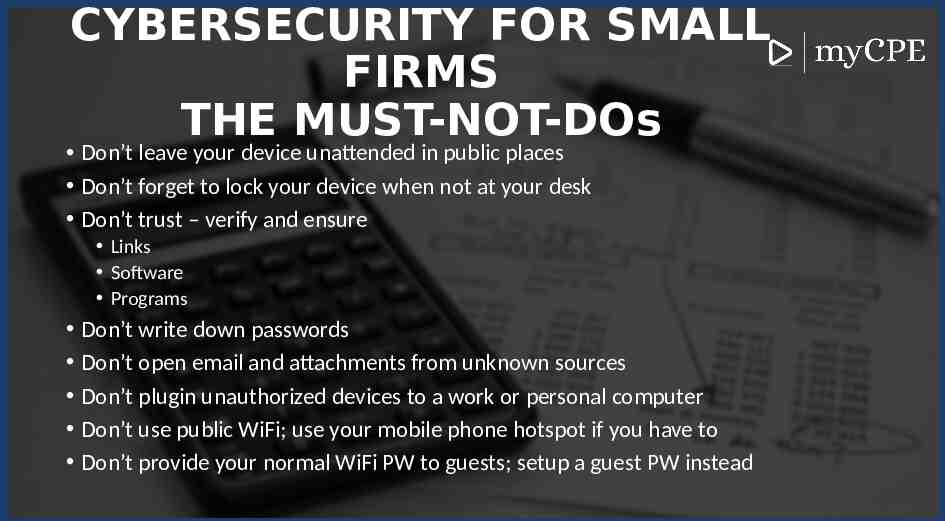
CYBERSECURITY FOR SMALL FIRMS THE MUST-NOT-DOs Don’t leave your device unattended in public places Don’t forget to lock your device when not at your desk Don’t trust – verify and ensure Links Software Programs Don’t write down passwords Don’t open email and attachments from unknown sources Don’t plugin unauthorized devices to a work or personal computer Don’t use public WiFi; use your mobile phone hotspot if you have to Don’t provide your normal WiFi PW to guests; setup a guest PW instead

‘Do It Yourself’ VS ‘IT EXPERT’ – A COMPARISON Cost Assurance Failure Risks Success ratio – Statistics for small firms Compliance Need of the changing times

PREPARING TEAM FOR THE CHALLENGE Training Testing Implementing policies Email encryption Strict policies and enforcement regarding mobile devices on premises Telephonic confirmation required for wire transfers Confirmation Text

SESSION OVERVIEW Cybersecurity – understanding and importance Data Security and relevance for Small Accounting Firms CPAs as targets Tech for small CPAs Data breach – Types and Consequences Enterprise Approach Towards Cybersecurity Framing the questions at hand Do’s and Do not’s DIY Vs. IT Expert a Comparison How to prepare your team for good cybersecurity

THANKS! DO YOU HAVE ANY QUESTIONS? REACH ME - [email protected]