CS352H: Computer Systems Architecture Lecture 4: Instruction Set
15 Slides759.00 KB

CS352H: Computer Systems Architecture Lecture 4: Instruction Set Architectures III MIPS ALU September 10, 2008 University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell
ISA Example: IA-32 A 20-year old ISA! (30 years if you count earlier x86) Blend of RR & RM ISA Two-operand instructions Seven addressing modes Mode to indicate whether 8086, 286 or IA-32 ( 386) More than 630 instructions! Evolved to include multimedia, graphics Support operations on 8, 16 and 32-bit operands Variable-length instructions 1 – 15 bytes long (3 bytes on average) University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 2
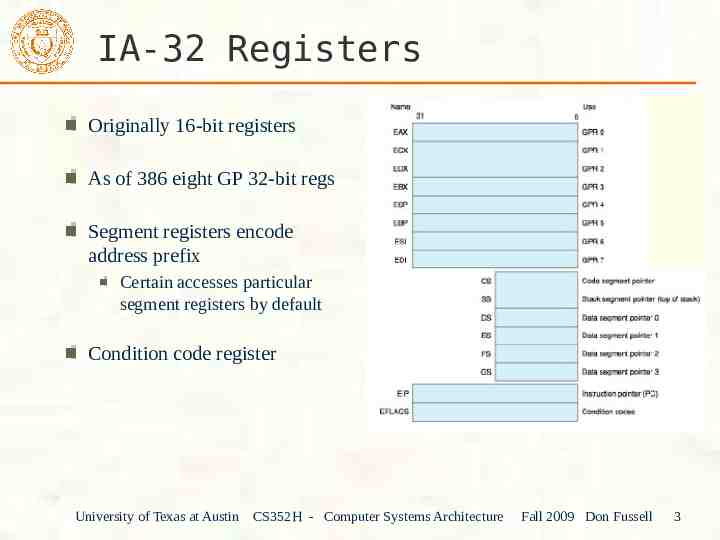
IA-32 Registers Originally 16-bit registers As of 386 eight GP 32-bit regs Segment registers encode address prefix Certain accesses particular segment registers by default Condition code register University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 3
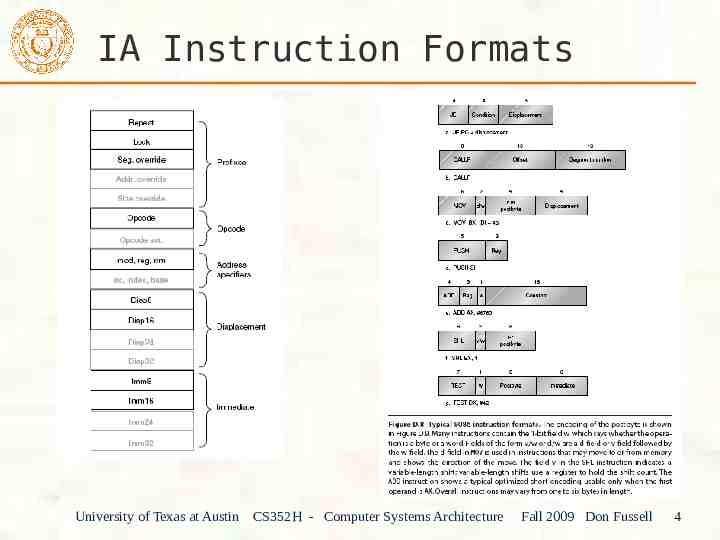
IA Instruction Formats University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 4
Principles of ISA Design KISS — Keep It Simple, Stupid (Cray) Complexity increases Logic area Pipe stage duration Development time Evolution leads to kludges Orthogonality Simple rules, few exceptions All ops on all registers in all addressing modes Frequency Make the common case fast Instructions are not born equal! University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 5
Principles of ISA Design (cont) Generality Not all problems need the same capabilities Toaster oven vs. supercomputer Performance should be easy to predict Peter Denning: Don’t build it if you can’t model it Permit efficient implementation Today 10 years from now University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 6

CISC vs. RISC Complex Instruction Set Computer (CISC) Typically includes: Variable-length instructions RM instructions Many, complex addressing modes Complex instructions Examples: VAX, IBM 360/370, x86 Advantages Code density Legacy SW Reduced Instruction Set Computer (RISC) Typically includes: GP registers Fixed 3-address format Strict load/store conformance Few, simple addressing modes Simple instructions Examples: DEC Alpha, MIPS Advantages Good compiler target Easy to implement/pipeline In practice, other than a handful of ISAs, most contain elements of both. University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 7
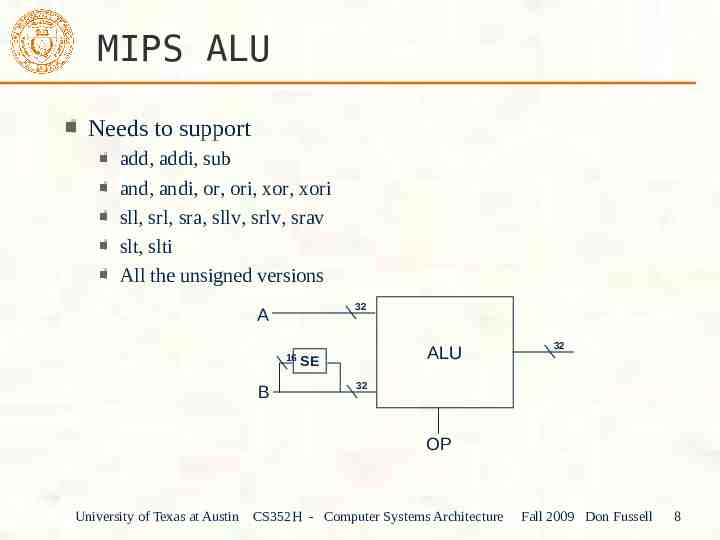
MIPS ALU Needs to support add, addi, sub and, andi, or, ori, xor, xori sll, srl, sra, sllv, srlv, srav slt, slti All the unsigned versions 32 A 16 B ALU SE 32 32 OP University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 8

Bit Slice Approach QuickTime and a decompressor are needed to see this picture. For subtraction: set invert & CarryIn to 1 (2’s complement arithmetic) How about SLT? University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 9
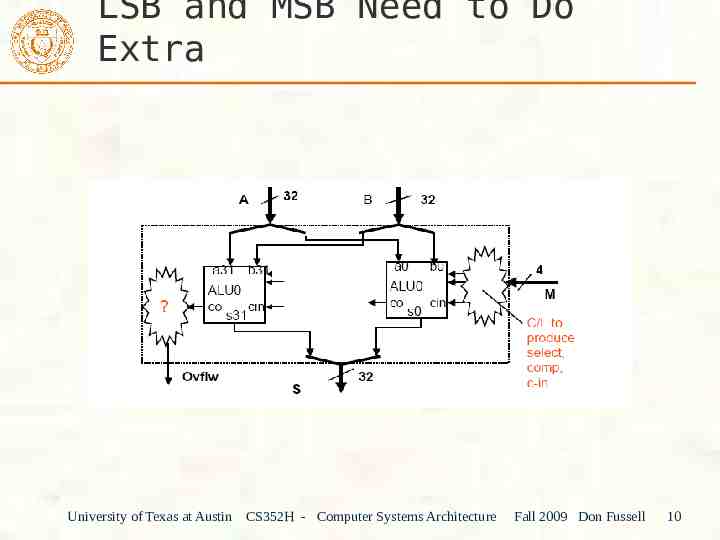
LSB and MSB Need to Do Extra University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 10
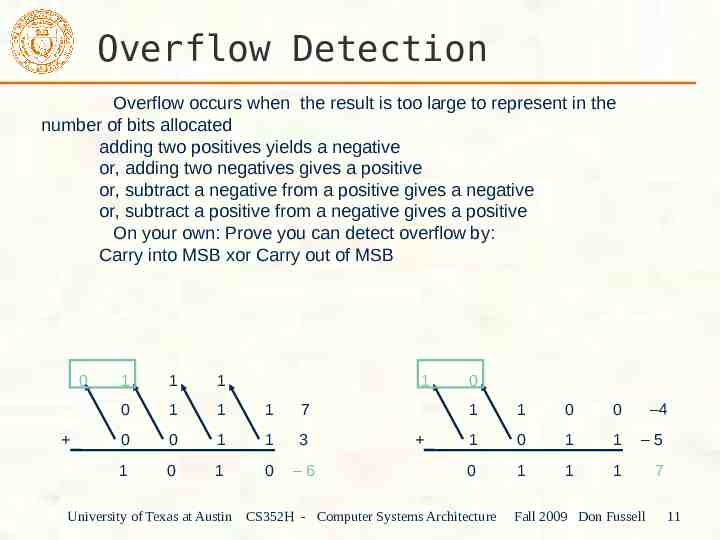
Overflow Detection Overflow occurs when the result is too large to represent in the number of bits allocated adding two positives yields a negative or, adding two negatives gives a positive or, subtract a negative from a positive gives a negative or, subtract a positive from a negative gives a positive On your own: Prove you can detect overflow by: Carry into MSB xor Carry out of MSB 0 1 1 1 1 0 1 1 1 7 0 0 1 1 3 1 0 1 0 –6 0 1 1 0 0 –4 1 0 1 1 –5 0 1 1 1 7 University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 11
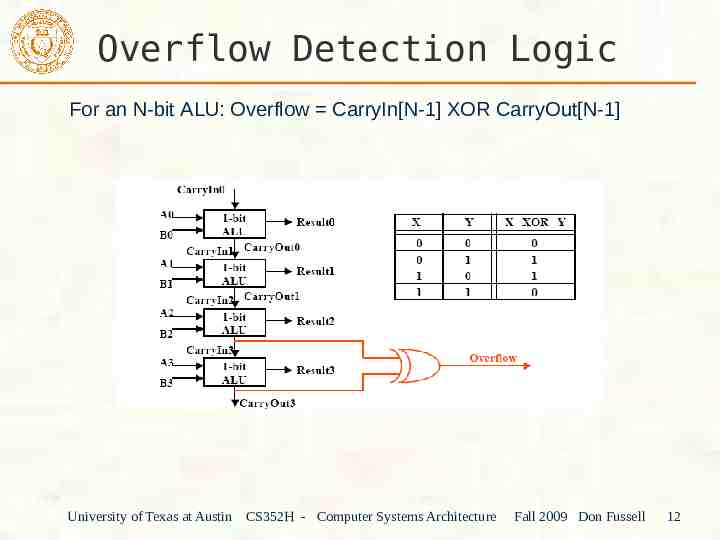
Overflow Detection Logic For an N-bit ALU: Overflow CarryIn[N-1] XOR CarryOut[N-1] University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 12
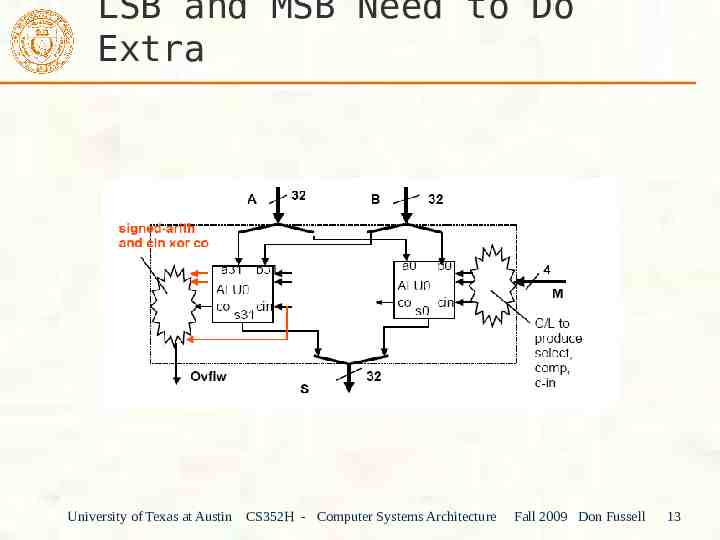
LSB and MSB Need to Do Extra University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 13
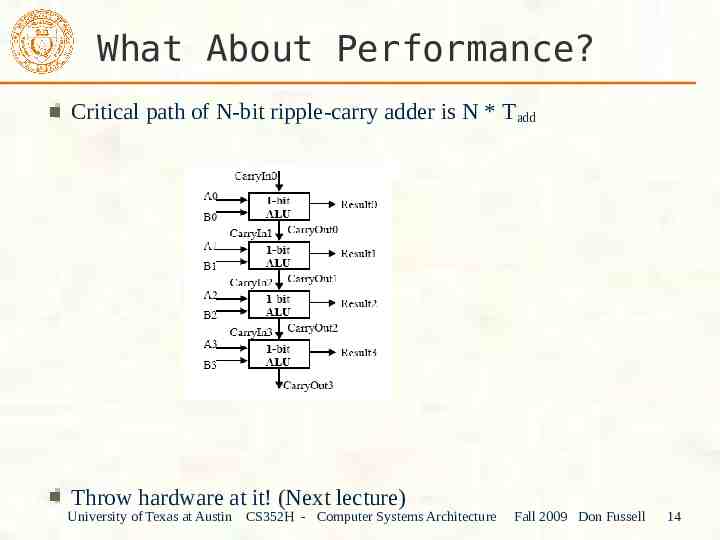
What About Performance? Critical path of N-bit ripple-carry adder is N * T add Throw hardware at it! (Next lecture) University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 14

Next Lecture Finish MIPS ALU See Appendix C (on CD) In particular, Sections C-5 & C-6 for fast adders See Chapter 3.3 & 3.4 for Multiplication & Division See Chapter 3.5 for Floating point ops University of Texas at Austin CS352H - Computer Systems Architecture Fall 2009 Don Fussell 15