Chapter 2: Security Laws and Standards 1. Security Assurance 2.
98 Slides6.67 MB

Chapter 2: Security Laws and Standards 1. Security Assurance 2. Security Laws 3. IPR 4. International Standards 5. Security Audit 6. SSE-CMM / COBIT etc

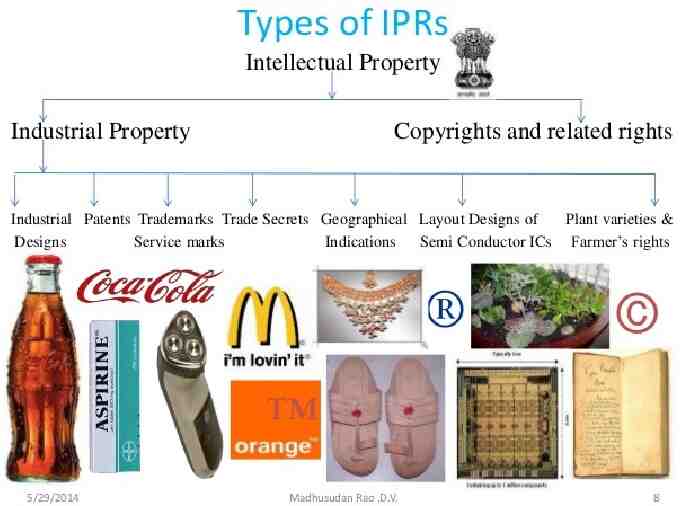
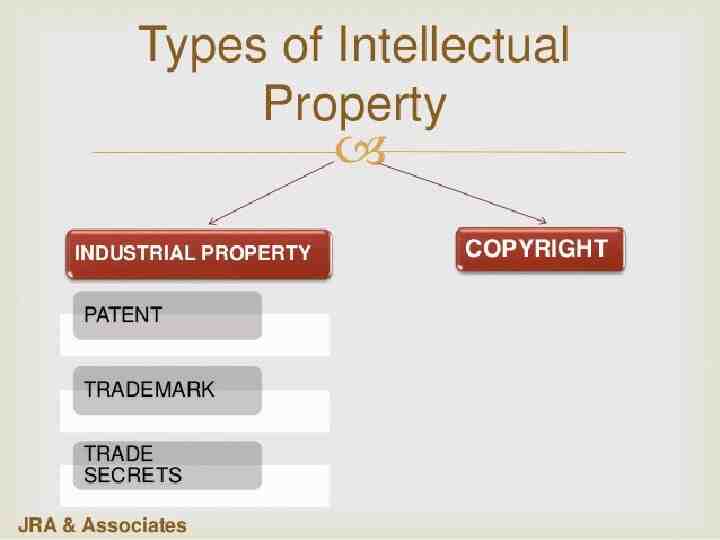
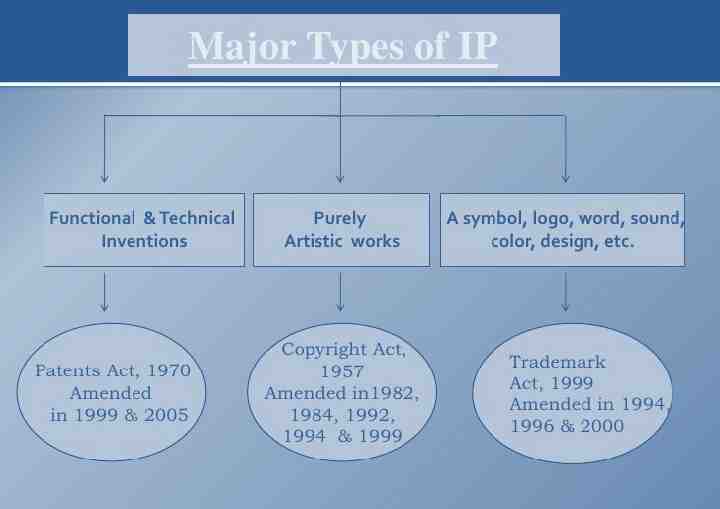
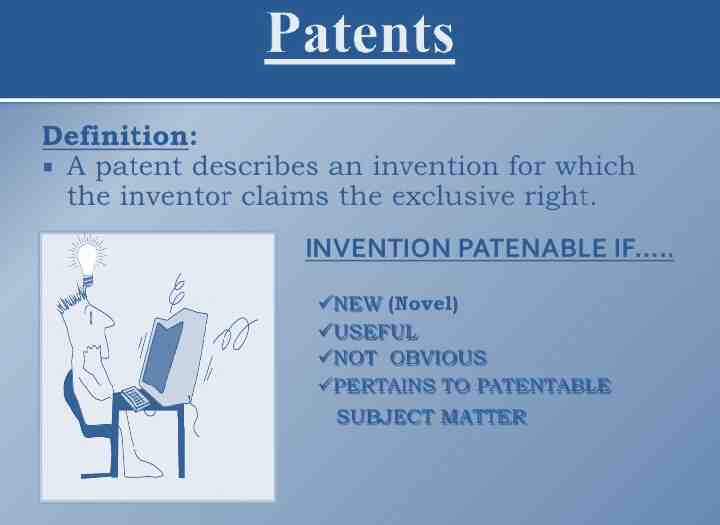
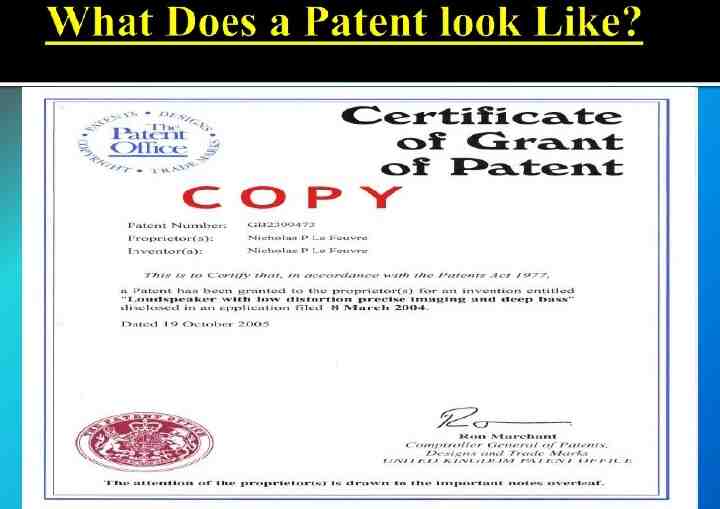
A patent is an exclusive right granted for an invention, which is a product or a process that provides a new way of doing something, or offers a new technical solution to a problem. It provides protection for the invention to the owner of the patent. The protection is granted for a limited period, i.e 20 years. Patent protection means that the invention cannot be commercially made, used, distributed or sold.

The owner no longer holds exclusive rights to the invention, which becomes available to commercial exploitation by others. All patent owners are obliged, in return for patent protection, to publicly disclose information on their invention in order to enrich the total body of technical knowledge in the world. Such an ever-increasing body of public knowledge promotes further creativity and innovation in others. In this way, patents provide not only protection for the owner but valuable information and inspiration for future generations of researchers and inventors.

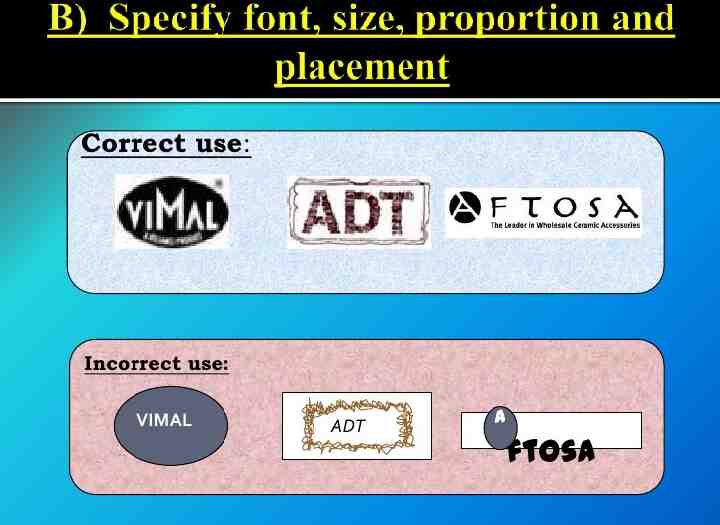
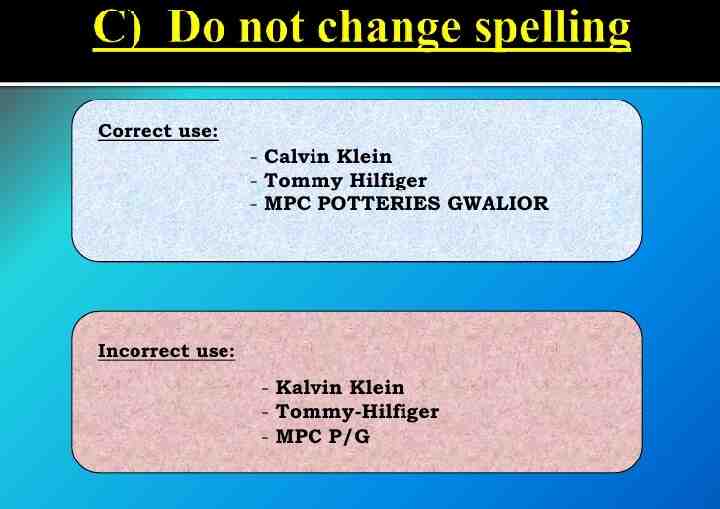
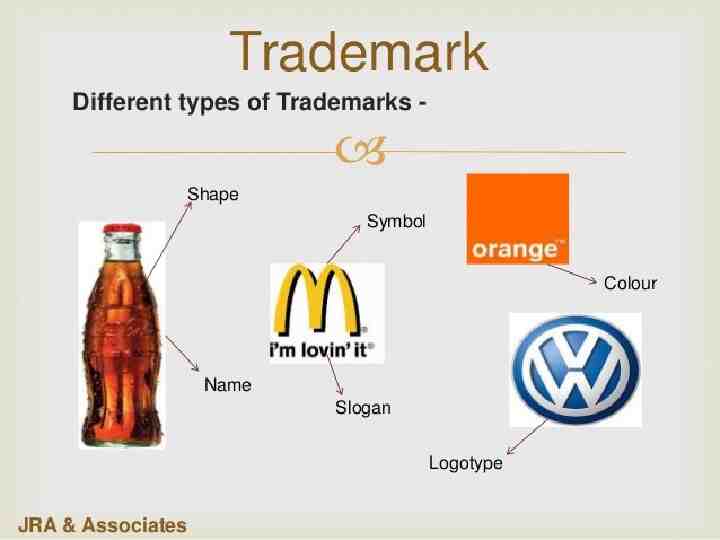
Trademarks: A trademark is a distinctive sign that identifies certain goods or services as those produced or provided by a specific person or enterprise. It may be one or a combination of words, letters, and numerals. They may consist of drawings, symbols, three- dimensional signs such as the shape and packaging of goods, audible signs such as music or vocal sounds, fragrances, or colours used as distinguishing features. It helps consumers identify and purchase a product or service because its nature and quality, indicated by its unique trademark, meets their needs. The initial term of registration is for 10 years; thereafter it may be renewed from time to time.

Trade Secrets: It may be confidential business information that provides an enterprise a competitive edge may be considered a trade secret. Usually these are manufacturing or industrial secrets and commercial secrets. These include sales methods, distribution methods, consumer profiles, advertising strategies, lists of suppliers and clients, and manufacturing processes. Contrary to patents, trade secrets are protected without registration. A trade secret can be protected for an unlimited period of time but a substantial element of secrecy must exist, so that, except by the use of improper means, there would be difficulty in acquiring the information. The Trades secret, traditional knowledge are also interlinked / associated with the geographical indications.

Geographical Indications (GI): GI are signs used on goods that have a specific geographical origin and possess qualities or a reputation that are due to that place of origin. Agricultural products typically have qualities that derive from their place of production and are influenced by specific local factors, such as climate and soil. They may also highlight specific qualities of a product, which are due to human factors that can be found in the place of origin of the products, such as specific manufacturing skills and traditions.

It is important that the product derives its qualities and reputation from that place. Place of origin may be a village or town, a region or a country. It is an exclusive right given to a particular community hence the benefits of its registration are shared by the all members of the community. Recently the GIs of goods like Chanderi Sarees, Kullu Shawls, Wet Grinders etc have been registered. Keeping in view the large diversity of traditional products spread all over the country, the registration under GI will be very important in future growth of the tribes / communities / skilled artisans associated in developing such products.

scope
Copyrights and related rights: Copyright is a legal term describing rights given to creators for their literary and artistic works. The kinds of works covered by copyright include: literary works such as novels, poems, plays, reference works, newspapers and computer programs; databases; films, musical compositions, and choreography; artistic works such as paintings, drawings, photographs and sculpture; architecture; and advertisements, maps and technical drawings. Copyright subsists in a work by virtue of creation; hence it’s not mandatory to register. However, registering a copyright provides evidence that copyright subsists in the work & creator is the owner of the work.

Creators often sell the rights to their works to individuals or companies best able to market the works in return for payment. These payments are often made dependent on the actual use of the work, and are then referred to as royalties. These economic rights have a time limit, (other than photographs) is for life of author plus sixty years after creator’s death

e. IndustrialDesigns: Industrial designs refer to creative activity, which result in the ornamental or formal appearance of a product, and design right refers to a novel or original design that is accorded to the proprietor of a validly registered design. Industrial designs are an element of intellectual property. Under the TRIPS Agreement, minimum standards of protection of industrial designs have been provided for. As a developing country, India has already amended its national legislation to provide for these minimal standards. The essential purpose of design law it to promote and protect the design element of industrial production. It is also intended to promote innovative activity in the field of industries. The existing legislation on industrial designs in India is contained in the New Designs Act, 2000 and this Act will serve its purpose well in the rapid changes in technology and international developments.

g. Layout Design for Integrated Circuits: Semiconductor Integrated Circuit means a product having transistors and other circuitry elements, which are inseparably formed on a semiconductor material or an insulating material or inside the semiconductor material and designed to perform an electronic circuitry function. The aim of the Semiconductor Integrated Circuits Layout-Design Act 2000 is to provide protection of Intellectual Property Right (IPR) in the area of Semiconductor Integrated Circuit Layout Designs and for matters connected therewith or incidental thereto.

The main focus of SICLD Act is to provide for routes and mechanism for protection of IPR in Chip Layout Designs created and matters related to it. The SICLD Act empowers the registered proprietor of the layoutdesign an inherent right to use the layout-design, commercially exploit it and obtain relief in respect of any infringement. The initial term of registration is for 10 years; thereafter it may be renewed from time to time.

h. Protection of New Plant Variety: The objective of this act is to recognize the role of farmers as cultivators and conservers and the contribution of traditional, rural and tribal communities to the country’s agro biodiversity by rewarding them for their contribution and to stimulate investment for R & D for the development new plant varieties to facilitate the growth of the seed industry. The Plant Variety Protection and Farmers Rights act 2001 was enacted in India to protect the New Plant Variety; the act has come into force on 30.10.2005 through Authority. Initially 12 crop species have been identified for regt. i.e. Rice, Wheat, Maize, Sorghum, Pearl millet, Chickpea, Green gram, Black gram, Lentil, Kidney bean etc. India has opted for sui- generic system instead of patents for protecting new plant variety. Department Agriculture and Cooperation is the administrative ministry looking after its registration and other matters.

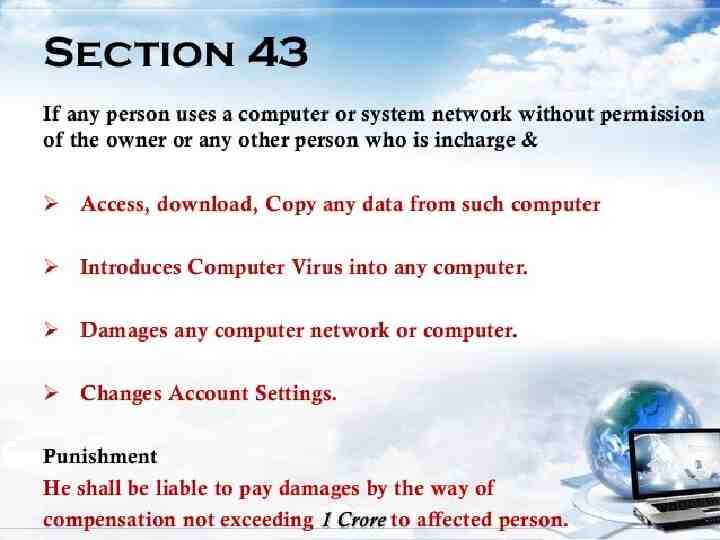
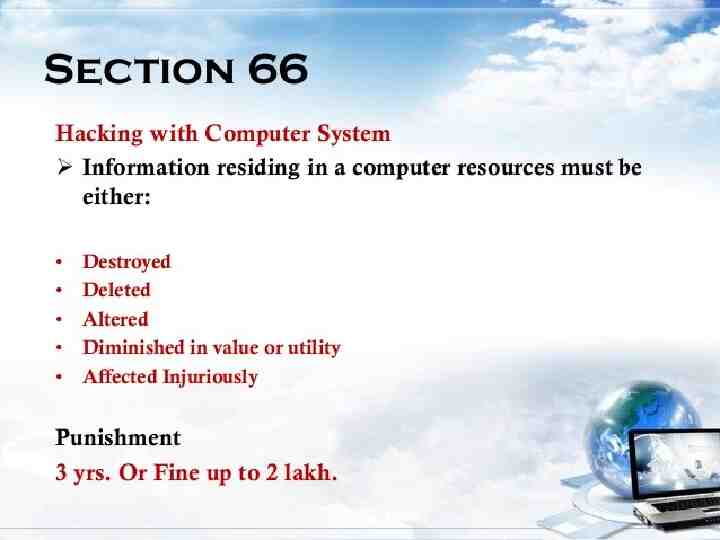
Security Laws

Law/finance
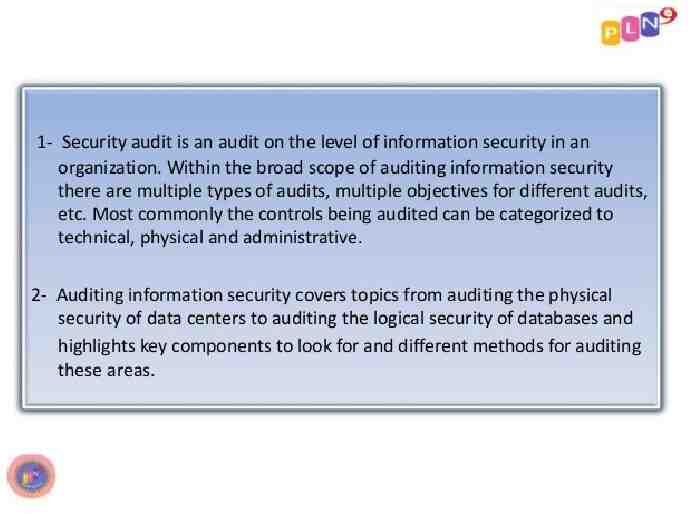
An Information security audit is an audit of information security in an organization. In auditing information security, there are multiple types of audits and multiple objectives for different audits. Most commonly, the controls being audited can be categorized to technical, physical and administrative. Auditing information security covers topics from auditing the physical security of data centers to auditing the logical security of databases. It highlights key components to look for and different methods for auditing these areas. When centered on the IT aspects of information security, it can be seen as a part of an information technology audit. It is often then referred to as an information technology security audit or a computer security audit.

Establishing audit objectives Employee procedures and responsibilities including systems and cross- functional training Appropriate back up procedures are in place to minimize downtime and prevent loss of important data The data center has sufficient physical security controls to prevent unauthorized access to the data center. sufficient environmental controls are in place to ensure equipment is protected from fire and flooding
Meet with IT management to determine possible areas of concern Review the current IT organization chart Review job descriptions of data center employees Research all operating systems, software applications and data center equipment operating within the data center Review the company’s IT policies and procedures Evaluate the company’s IT budget and systems planning documentation

Audit planning & preparation The auditor should be sufficiently educated about the company and its critical business activities before conducting a data centre review. The objective of the data centre is to align data centre activities with the goals of the business while maintaining the security and integrity of critical information and processes.

Performing the review The next step is collecting evidence to satisfy data center audit objectives. This involves travelling to the data center location and observing processes within the data center.

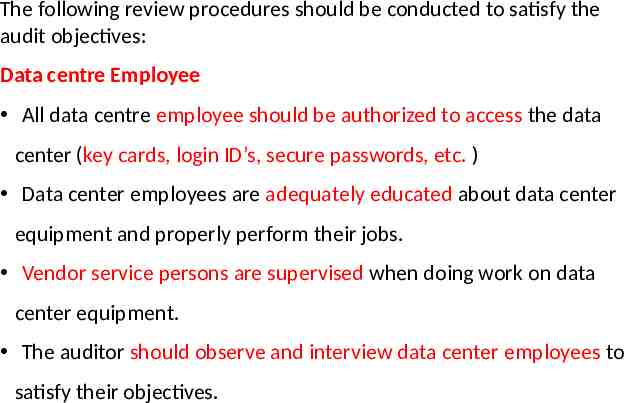
The following review procedures should be conducted to satisfy the audit objectives: Data centre Employee All data centre employee should be authorized to access the data center (key cards, login ID’s, secure passwords, etc. ) Data center employees are adequately educated about data center equipment and properly perform their jobs. Vendor service persons are supervised when doing work on data center equipment. The auditor should observe and interview data center employees to satisfy their objectives.

Equipment The auditor should verify that all data center equipment is working properly and effectively. Equipment utilization reports, equipment inspection for damage and functionality, system downtime records and equipment performance measurements all help the auditor determine the state of data center equipment. Additionally, the auditor should interview employees to determine if preventative maintenance policies are in place and performed.

Policies and Procedures All data center policies and procedures should be documented and located at the data center. Important documented procedures include: data center personnel job responsibilities, back up policies, security policies, employee termination policies, system operating procedures and an overview of operating systems.
Physical security / environmental controls The auditor should assess the security of the client’s data center. Physical security includes bodyguards, locked cages, man traps, single entrances and computer monitoring systems. Additionally, environmental controls should be in place to ensure the security of data center equipment. These include: Air conditioning units, raised floors, humidifiers and uninterruptible power supply.

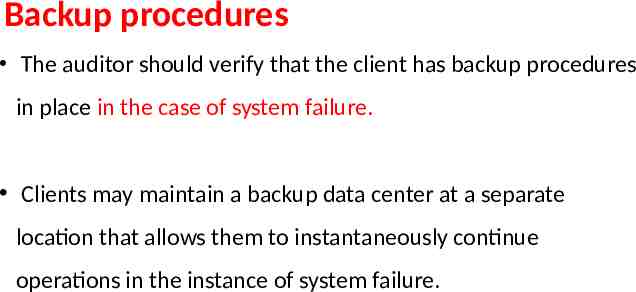
Backup procedures The auditor should verify that the client has backup procedures in place in the case of system failure. Clients may maintain a backup data center at a separate location that allows them to instantaneously continue operations in the instance of system failure.

Issuing the review report The data center review report should summarize the auditor’s findings and be similar in format to a standard review report. The review report should be dated as of the completion of the auditor's inquiry and procedures. It should state what the review entailed and explain that a review provides only "limited assurance" to third parties.
Two factor authentication(OTP)

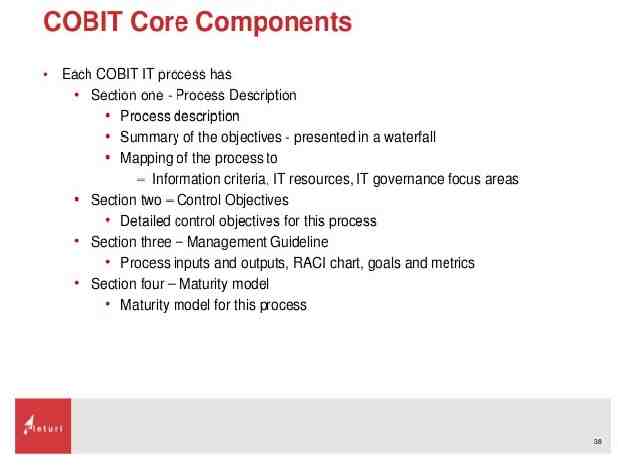
COBIT ( Control Objectives for Information and Related Technology). It is a framework created by the ISACA (Information Systems Audit and Control Association) for IT governance and management.

Thank You